2016-06-29 - EK DATA DUMP (MORE NEUTRINO EK, RIG EK)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- Got data on today's Rig EK infections from 2 tweets by @ malekal_morte. (Links are here and here.)
- @dez_ reported the Afraidgate traffic on 2016-06-27 (link) which was still active today.
- The domain realstatistics[.]info is still being used as a gate, as previously reported by @BroadAnalysis on 2016-06-23 (2025 note: the site is no longer online).
- Background on the Afraidgate campaign can be found here (Looks like it went back to Locky ransomware from CryptXXX ransomware).
- After receiving an email from Andreas, I'm including the file hashes for the malware/exploits in these blog posts.
ASSOCIATED FILES:
- 2016-06-29-EK-data-dump-4-pcaps.zip 5.8 MB (5,776,396 bytes)
- 2016-06-23-realstatistics-gate-Neutrino-EK-sends-Gootkit-after-nebularoficial_com.pcap (5,322,408 bytes)
- 2016-06-29-Rig-EK-after-gate-on-45.32.187_36.pcap (224,181 bytes)
- 2016-06-29-Rig-EK-after-glamgirltube_tk.pcap (248,972 bytes)
- 2016-06-29-afraidgate-Neutrino-EK-sends-Locky-ransomware-after-marketingguerrilla_es.pcap (389,579 bytes)
- 2016-06-29-EK-data-dump-malware-and-artifacts.zip 814.2 kB (814,207 bytes)
- 2016-06-29-Rig-EK-flash-exploit-after-gate-on-45.32.187_36.swf (24,661 bytes)
- 2016-06-29-Rig-EK-flash-exploit-after-glamgirltube_tk.swf (24,661 bytes)
- 2016-06-29-Rig-EK-landing-page-after-gate-on-45.32.187_36.txt (5,384 bytes)
- 2016-06-29-Rig-EK-landing-page-after-glamgirltube_tk.txt (5,348 bytes)
- 2016-06-29-Rig-EK-payload-after-gate-on-45.32.187_36.exe (197,120 bytes)
- 2016-06-29-Rig-EK-payload-after-glamgirltube_tk.exe (106,496 bytes)
- 2016-06-29-afraidgate-Neutrino-EK-flash-exploit-after-marketingguerrilla_es.swf (84,521 bytes)
- 2016-06-29-afraidgate-Neutrino-EK-landing-page-after-marketingguerrilla_es.txt (1,095 bytes)
- 2016-06-29-afraidgate-Neutrino-EK-payload-Locky-ransomware-after-marketingguerrilla_es.exe (240,130 bytes)
- 2016-06-29-afraidgate-redirect-from-live.keeprunning_com_br.txt (260 bytes)
- 2016-06-29-page-from-marketingguerrilla_es-with-injected-script-to-afraidgate-redirect.txt (70,443 bytes)
- 2016-06-29-page-from-nebularoficial_com-with-injected-script-pointing-to-realstatistics-gate.txt (10,475 bytes)
- 2016-06-29-realstatistics-gate-Neutrino-EK-flash-exploit-after-nebularoficial_com.swf (88,776 bytes)
- 2016-06-29-realstatistics-gate-Neutrino-EK-landing-page-after-nebularoficial_com.txt (1,083 bytes)
- 2016-06-29-realstatistics-gate-Neutrino-EK-payload-Gootkit-after-nebularoficial_com.exe (197,120 bytes)
TRAFFIC
ASSOCIATED DOMAINS:
- 93.36.35[.]39 port 80 - glamgirltube[.]tk - GET /engine/classes/js/jquery.js - file with injected script
- 193.36.35[.]39 port 80 - fijir0[.]tk - GET /linkx.php - gate
- 46.30.46[.]40 port 80 - jy.neutralarbitrations[.]com - RIG EK
- 45.32.187[.]36 port 80 - 45.32.187[.]36 - GET /jquery_1.8.9.php - gate
- 46.30.42[.]33 port 80 - gr.sagepointsolutionsgroup[.]com - RIG EK
- 59.144.17[.]122 port 80 - barbastraizand[.]com - post-infection SSL traffic over port 80 (Gootkit)
- 77.42.157[.]2 port 80 - googlesecurityhtml[.]com - post-infection SSL traffic over port 80 (Gootkit)
- 139.59.191[.]79 port 80 - live.keeprunning[.]com[.]br - GET /js/node.js - Afraidgate redirect
- 78.46.167[.]130 port 80 - wcmlqfklmn.wwmeaa[.]xyz - Neutrino EK
- 151.236.17[.]45 port 80 - 151.236.17[.]45 - POST /upload/_dispatch.php - Locky post-infection traffic
- 85.25.95[.]39 port 80 - realstatistics.info - gate pointing to Neutrino EK
- 78.46.167[.]130 port 80 - hoqthplimn.fsblim[.]xyz - Neutrino EK
- 52.67.39[.]104 port 80 - sievavower[.]com - post-infection SSL traffic over port 80 (Gootkit)
- 93.115.10[.]203 port 80 - sievavower[.]com - post-infection SSL traffic over port 80 (Gootkit)
- 52.67.39[.]104 port 80 - stogtetch[.]com - post-infection SSL traffic over port 80 (Gootkit)
- 93.115.10[.]203 port 443 - post-infection SSL traffic (Gootkit)
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: df39ef28575bf22e093531038d0951e54c6d3a7656d62da11ed4342cc5c35807
File name: 2016-06-29-Rig-EK-flash-exploit-after-gate-on-45.32.187_36.swf
File name: 2016-06-29-Rig-EK-flash-exploit-after-glamgirltube_tk.swf
- SHA256 hash: 9d8a8c9e021fcecea60f82fb2a5a8ee6ebcdc9c09f27a5136401a0ad044dcbc1
File name: 2016-06-29-afraidgate-Neutrino-EK-flash-exploit-after-marketingguerrilla_es.swf
- SHA256 hash: e30388882399a955c5457e0799fc5c6fd2e9d67ac0c02ffa57210bf6923ee7ad
File name: 2016-06-29-realstatistics-gate-Neutrino-EK-flash-exploit-after-nebularoficial_com.swf
MALWARE PAYLOADS:
- SHA256 hash: 95858bc155f71965703420efe9d7ae8154005171c8239899bb3f521040a29ef7
File name: 2016-06-29-Rig-EK-payload-after-gate-on-45.32.187_36.exe
- SHA256 hash: c850d7f22d3e8c5ef01443c06f30bc05cd07a14997a1a0bc9d8cfeedebb05f73
File name: 2016-06-29-Rig-EK-payload-after-glamgirltube_tk.exe
- SHA256 hash: ddf25ecfc1cf5125af121e53a7619183d24c1beefdb9fd19ab3eebf3b86361dd
File name: 2016-06-29-afraidgate-Neutrino-EK-payload-Locky-ransomware-after-marketingguerrilla_es.exe
- SHA256 hash: b6573cfb84ee37285ad6e84e63aca109e49096c48454a058b2c58379fde885f1
File name: 2016-06-29-realstatistics-gate-Neutrino-EK-payload-Gootkit-after-nebularoficial_com.exe
IMAGES
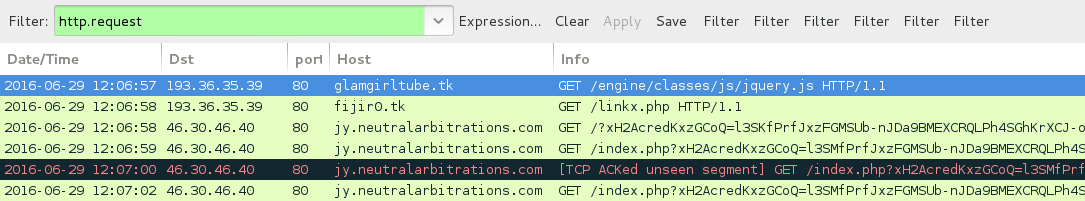
Shown above: Traffic from the first pcap filtered in Wireshark (Rig EK sends possible Gootkit, no post-infection traffic in the pcap).
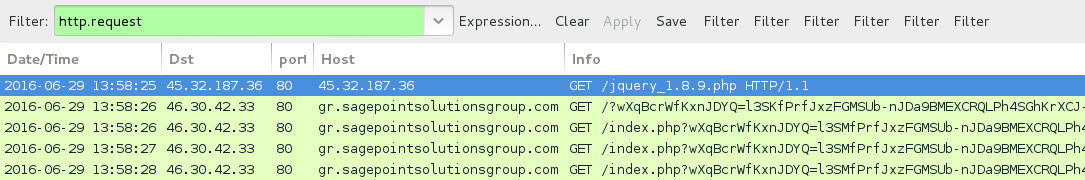
Shown above: Traffic from the second pcap filtered in Wireshark (Rig EK sends possible Gootkit, no post-infection traffic in the pcap).
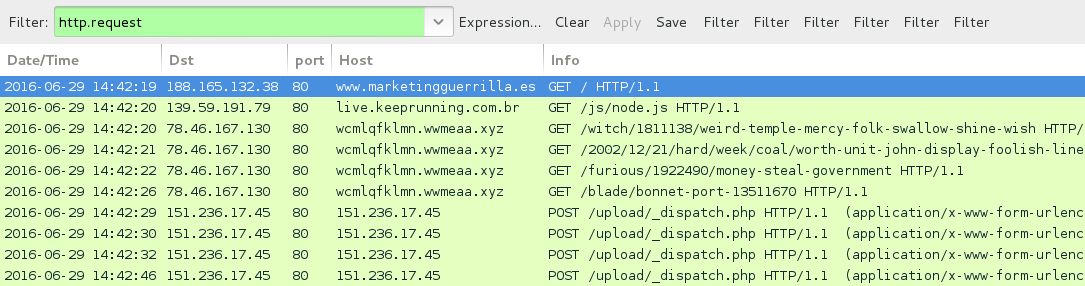
Shown above: Traffic from the third pcap filtered in Wireshark (Afraidgate Neutrino EK sends Locky ransomware).
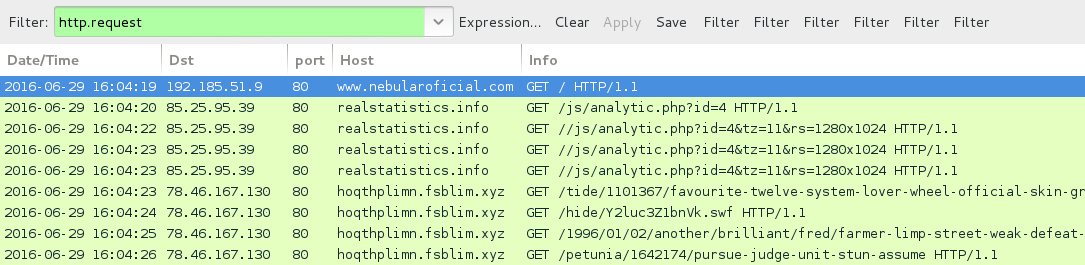
Shown above: Traffic from the fourth pcap filtered in Wireshark (realstatistics gate Neutrino EK sends Gootkit).
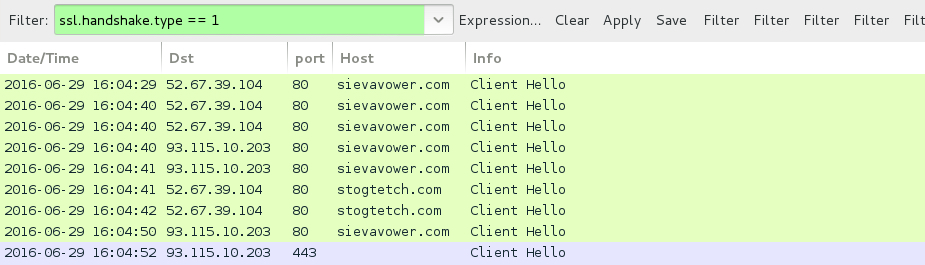
Shown above: Post-infection traffic from the fourth pcap, decoding the port 80 Gootkit traffic as SSL.
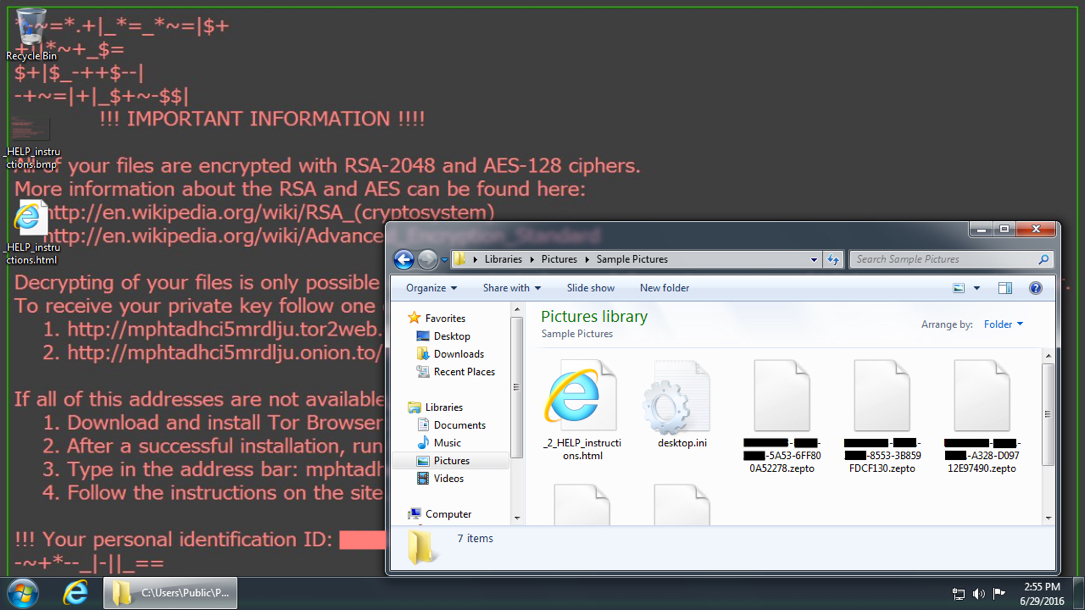
Shown above: Windows desktop after today's Locky ransomware infection.
Click here to return to the main page.
