2016-07-08 - EK DATA DUMP - NEUTRINO EK SENDS CRYPTXXX RANSOMWARE & GOOTKIT, RIG EK SENDS CRYPTOBIT RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-08-EK-data-dump-5-pcaps.zip 3.6 MB (3,592,006 bytes)
- 2016-07-08-EITest-Neutrino-EK-sends-CryptXXX-ransomware-after-musicmix_co.pcap (1,068,438 bytes)
- 2016-07-08-other-Neutrino-EK-sends-gootkit.pcap (451,652 bytes)
- 2016-07-08-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware-after-eielectronics_com.pcap (1,154,728 bytes)
- 2016-07-08-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware-after-toronto-annex_com.pcap (1,177,430 bytes)
- 2016-07-08-Rig-EK-sends-CryptoBit-ransomware.pcap (153,982 bytes)
- 2016-07-08-EK-data-dump-malware-and-artifacts.zip 1.4 MB (1,400,745 bytes)
- 2016-07-08-CryptoBit-ransomware-decrypt-instructions.txt (1,300 bytes)
- 2016-07-08-EITest-CryptXXX-decrypt-instructions.HTML (19,095 bytes)
- 2016-07-08-EITest-CryptXXX-ransomware-ransomware-decrypt-instructions.BMP (3,686,454 bytes)
- 2016-07-08-EITest-flash-redirector-from-fin7_tk.swf (3,070 bytes)
- 2016-07-08-EITest-Neutrino-EK-flash-exploit.swf (78,771 bytes)
- 2016-07-08-EITest-Neutrino-EK-landing-page.txt (3,179 bytes)
- 2016-07-08-EITest-Neutrino-EK-payload-CryptXXX-ransomware.dll (527,360 bytes)
- 2016-07-08-other-Neutrino-EK-flash-exploit.swf (78,158 bytes)
- 2016-07-08-other-Neutrino-EK-landing-page.txt (3,295 bytes)
- 2016-07-08-other-Neutrino-EK-malware-dropped-after-infection-svszclp.dll (102,400 bytes)
- 2016-07-08-other-Neutrino-EK-payload-Gootkit.exe (227,328 bytes)
- 2016-07-08-page-from-eielectronics_com-with-injected-script.txt (443 bytes)
- 2016-07-08-page-from-musicmix_co-with-injected-script.txt (135,261 bytes)
- 2016-07-08-page-from-toronto-annex_com-with-injected-script.txt (53,785 bytes)
- 2016-07-08-pseudoDarkleech-CryptXXX-ransomware-decrypt-instructions.BMP (3,686,454 bytes)
- 2016-07-08-pseudoDarkleech-CryptXXX-ransomware-decrypt-instructions.HTML (20,105 bytes)
- 2016-07-08-pseudoDarkleech-Neutrino-EK-flash-exploit-after-eielectronics_com.swf (78,861 bytes)
- 2016-07-08-pseudoDarkleech-Neutrino-EK-flash-exploit-after-toronto-annex_com.swf (77,708 bytes)
- 2016-07-08-pseudoDarkleech-Neutrino-EK-landing-page-after-eielectronics_com.txt (3,211 bytes)
- 2016-07-08-pseudoDarkleech-Neutrino-EK-landing-page-after-toronot-annex_com.txt (3,201 bytes)
- 2016-07-08-pseudoDarkleech-Neutrino-EK-payload.dll (512,000 bytes)
- 2016-07-08-Rig-EK-flash-exploit.swf (18,975 bytes)
- 2016-07-08-Rig-EK-landing-page.txt (5,506 bytes)
- 2016-07-08-Rig-EK-payload-CryptoBit-ransomware.exe (152,397 bytes)
GOOTKIT MALWARE NOTES:
- 2016-07-05 - Doctor Web: BackDoor.Gootkit.112—a new multi-purpose backdoor
CRYPTOBIT (CRIPTOBIT/MOBEF) RANSOMWARE NOTES:
- 2016-07-07 - Palo Alto Networks Unit 42 Blog: CryptoBit: Another Ransomware Family Gets an Update
CRYPTXXX RANSOMWARE NOTES:
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (EITest & pseudoDarkleech campaigns switch from Angler EK to Neutrino EK)
- 2016-06-11 - Malware Don't Need Coffee: Is it the end of Angler?
- 2016-07-02 - SANS ISC diary: Change in patterns for the pseudoDarkleech campaign
- 2016-07-06 - SANS ISC diary: CryptXXX ransomware updated
- 2016-07-07 - Bleeping Computer: New CryptXXX changes name to Microsoft Decryptor
- NOTE: Today CryptXXX ransomware was updated again, and it looks more like it did before the changes seen earlier this week.
- For CryptXXX ransomware, no more sending the TXT and HTML decryption instructions in the clear over TCP port 443.
- For CryptXXX ransomware, we're also back to "UltraDeCrypter" on the decryption instructions website for the ransom payment.

Shown above: Infected Windows desktop from CryptXXX ransomware samples on Friday 2016-07-08.
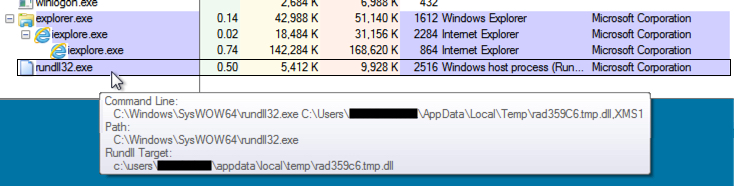
Shown above: One of the CryptXXX ransomware infections, where the ransomware is loaded by rundll32.exe.
TRAFFIC
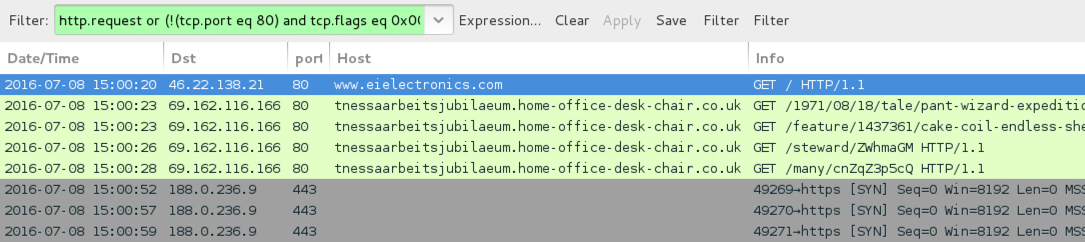
Shown above: Traffic from the first pcap filtered in Wireshark. Filter: http.request or (!(tcp.port eq 80) and tcp.flags eq 0x0002)
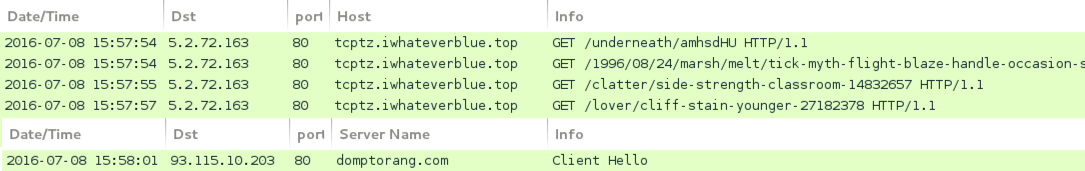
Shown above: Traffic from the second pcap filtered in Wireshark (Neutrino EK sends Gootkit).
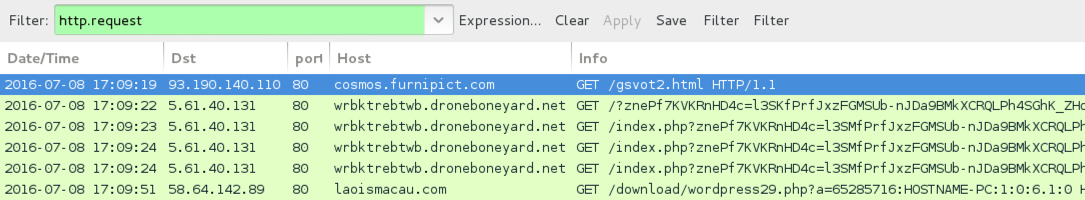
Shown above: Traffic from the third pcap filtered in Wireshark (Rig EK sends CryptoBit).
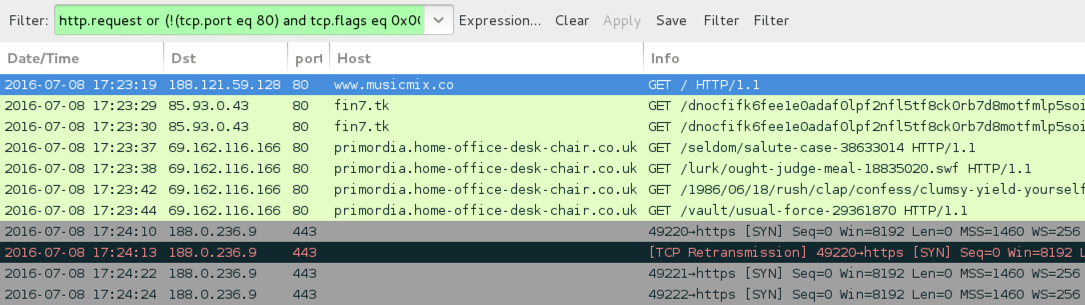
Shown above: Traffic from the 4th pcap filtered in Wireshark.
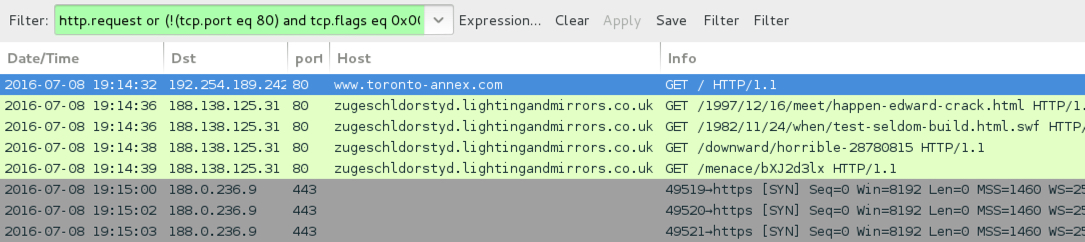
Shown above: Traffic from the 5th pcap filtered in Wireshark.
ASSOCIATED TRAFFIC:
- 85.93.0[.]43 port 80 - fin7[.]tk - EITest flash redirect
- 69.162.116[.]166 port 80 - primordia.home-office-desk-chair[.]co[.]uk - EITest Neutrino EK
- 69.162.116[.]166 port 80 - tnessaarbeitsjubilaeum.home-office-desk-chair[.]co[.]uk - pseudoDarkleech Neutrino EK
- 188.138.125[.]31 port 80 - zugeschldorstyd.lightingandmirrors[.]co[.]uk - pseudoDarkleech Neutrino EK
- 188.0.236[.]9 port 443 - CryptXXX ransomware post-infection traffic, custom encoded (not SSL)
- 5.2.72[.]163 port 80 - tcptz.iwhateverblue[.]top - Other Neutrino EK
- 93.115.10[.]203 port 80 - domptorang[.]com - SSL traffic with MyCompany Ltd cert (probable Gootkit callback)
- 93.190.140[.]110 port 80 - cosmos.furnipict[.]com - GET /gsvot2.html - Redirector from malvertising
- 5.61.40[.]131 port 80 - wrbktrebtwb.droneboneyard[.]net - Rig EK
- 58.64.142[.]89 port 80 - laoismacau[.]com - CryptoBit ransomware post-infection traffic
DOMAINS/EMAILS FROM THE DECRYPT INSTRUCTIONS:
- i5tbhsq567bemcgp[.]onion[.]to - EITest CryptXXX ransomware decrypt domain
- i5tbhsq567bemcgp[.]onion[.]cab - EITest CryptXXX ransomware decrypt domain
- i5tbhsq567bemcgp[.]onion[.]city - EITest CryptXXX ransomware decrypt domain
- lkpe6tr2yuk4f246[.]onion[.]to - pseudoDarkleech CryptXXX ransomware decrypt domain
- lkpe6tr2yuk4f246[.]onion[.]cab - pseudoDarkleech CryptXXX ransomware decrypt domain
- lkpe6tr2yuk4f246[.]onion[.]city - pseudoDarkleech CryptXXX ransomware decrypt domain
- epiclesis@protonmail[.]ch - email from CryptoBit ransomware decrypt instructions
- kyklos@scryptmail[.]com - email from CryptoBit ransomware decrypt instructions
- malakia@openmailbox[.]org - email from CryptoBit ransomware decrypt instructions
FILE HASHES
FLASH REDIRECTOR OR FLASH EXPLOITS:
-
SHA256 hash: c74757e31b335b0c668c19447733acd8ef306868ef2d0b12360c78c398bac1ce
File name: 2016-07-08-EITest-flash-redirector-from-fin7_tk.swf
-
SHA256 hash: 79762d761537af80add0e5b214990a7bfe6a1d835091e075dea0581766ff7f10
File name: 2016-07-08-EITest-Neutrino-EK-flash-exploit.swf
-
SHA256 hash: 3819f6c2a4044c4e61f8f2648aabd1f1b41fd8c77c59024ee365d7602848f6a4
File name: 2016-07-08-Rig-EK-flash-exploit.swf
-
SHA256 hash: 38ebddcf7b6b517d86f53ea8a534c985637249fe0b56f530d8155fa57e334e72
File name: 2016-07-08-other-Neutrino-EK-flash-exploit.swf
-
SHA256 hash: 2c7fbfbae04f17adfde081add27bc535412eb9ab79c54ff97c1446cab4239968
File name: 2016-07-08-pseudoDarkleech-Neutrino-EK-flash-exploit-after-eielectronics_com.swf
-
SHA256 hash: a1d83d5f5d4b67fd166b05af8c671a4fefea2091db57ec641b3bf856062ecb04
File name: 2016-07-08-pseudoDarkleech-Neutrino-EK-flash-exploit-after-toronto-annex_com.swf
MALWARE (EXE OR DLL FILES):
-
SHA256 hash: e40f89a16e44a65b53864fdfaa9dd70fc08382dcb2f3941d986056d2c50923ac
File name: 2016-07-08-EITest-Neutrino-EK-payload-CryptXXX-ransomware.dll
-
SHA256 hash: 19a60e842a5da32b4c8540ff02a51366d2b85c12e6721c80bbcf3be88478d37c
File name: 2016-07-08-other-Neutrino-EK-malware-dropped-after-infection-svszclp.dll
-
SHA256 hash: 9eb5344f51f1694eabd602a08deb0899ff187d8319ffeb6807f194d8313cf206
File name: 2016-07-08-pseudoDarkleech-Neutrino-EK-payload.dll
-
SHA256 hash: c37db7dcd15ab738517488625533fa9091b5984c5411abfaec5613b0ff205aef
File name: 2016-07-08-Rig-EK-payload-CryptoBit-ransomware.exe
-
SHA256 hash: 5777c21bcc6e2cd8ff1981544550d51c5a5e1570956a5cdee1e20a102e78b398
File name: 2016-07-08-other-Neutrino-EK-payload-Gootkit-malware.exe
OTHER IMAGES
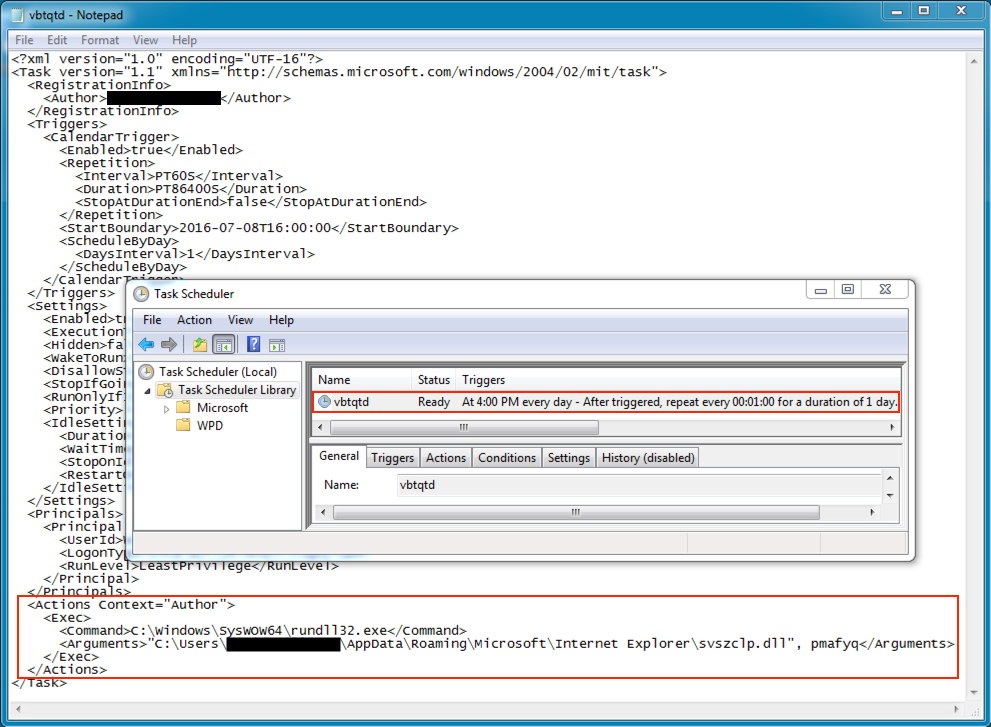
Shown above: Gootkit made persistent through a scheduled task, note the DLL file location.
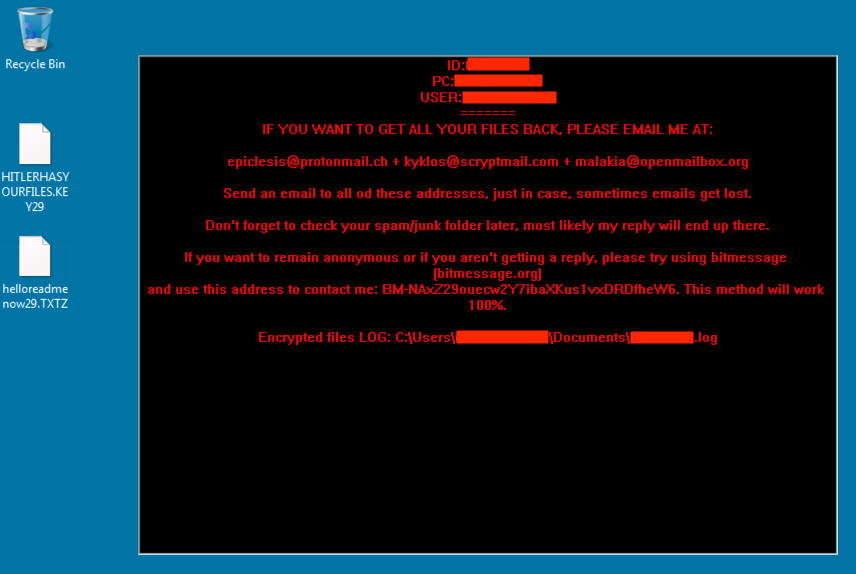
Shown above: Part of the Windows desktop after the Rig EK --> CryptoBit infection.
Click here to return to the main page.
