2016-07-12 - LOCKY RANSOMWARE ACTIVITY
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
NOTES:
- These are just 4 examples from hundreds of messages from this wave of emails pushing Locky ransomware.
ASSOCIATED FILES:
- 2016-07-12-Locky-ransomware-files.zip 1.2 MB (1,152,686 bytes)
- 2016-07-12-Locky-ransomware-email-tracker.csv (1,104 bytes)
- 2016-07-12-Locky-ransomware-infection-from-1355-UTC-email.pcap (174,188 bytes)
- 2016-07-12-Locky-ransomware-infection-from-1356-UTC-email.pcap (171,189 bytes)
- 2016-07-12-Locky-ransomware-infection-from-1402-UTC-email.pcap (162,357 bytes)
- 2016-07-12-Locky-ransomware-infection-from-1408-UTC-email.pcap (160,405 bytes)
- emails / 2016-07-12-email-pushing-Locky-ransomwware-1355-UTC.eml (12,895 bytes)
- emails / 2016-07-12-email-pushing-Locky-ransomwware-1356-UTC.eml (12,714 bytes)
- emails / 2016-07-12-email-pushing-Locky-ransomwware-1402-UTC.eml (12,808 bytes)
- emails / 2016-07-12-email-pushing-Locky-ransomwware-1408-UTC.eml (12,903 bytes)
- attachments / alan_copies_315759.zip (8,825 bytes)
- attachments / gregory_forward_937188.zip (8,850 bytes)
- attachments / robert_copies_560364.zip (8,708 bytes)
- attachments / susan_copies_104906.zip (8,782 bytes)
- extracted-files / -SWIFT-1ec2-.js (81,589 bytes)
- extracted-files / -SWIFT-43f-.js (80,760 bytes)
- extracted-files / -SWIFT-883f-.js (80,807 bytes)
- extracted-files / -SWIFT-f48e-.js (81,616 bytes)
- files-from-infected-hosts / 3VkFo0ErNhs9.exe (139,776 bytes)
- files-from-infected-hosts / OWVQ1Igf.exe (139,776 bytes)
- files-from-infected-hosts / _HELP_instructions.bmp (3,864,030 bytes)
- files-from-infected-hosts / _HELP_instructions.html (9,345 bytes)
- files-from-infected-hosts / j4NxFPY45Bz3Q.exe (139,776 bytes)
- files-from-infected-hosts / xmLXfRH8gYbB7.exe (139,776 bytes)
EMAILS
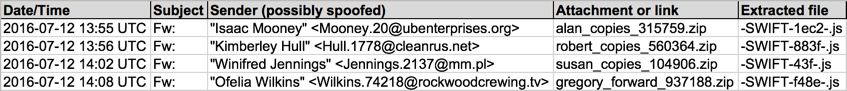
Shown above: Email data from the spreadsheet (part 1 of 2).

Shown above: Email data from the spreadsheet (part 2 of 2).
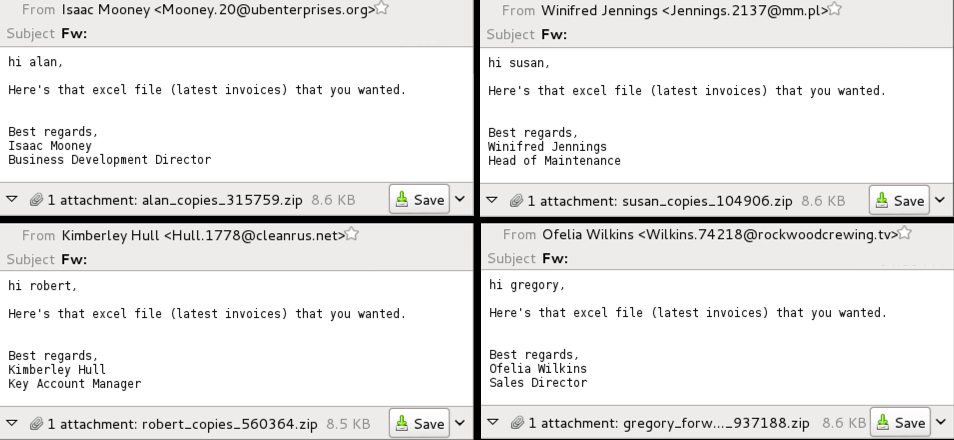
Shown above: Text of the emails.
TRAFFIC
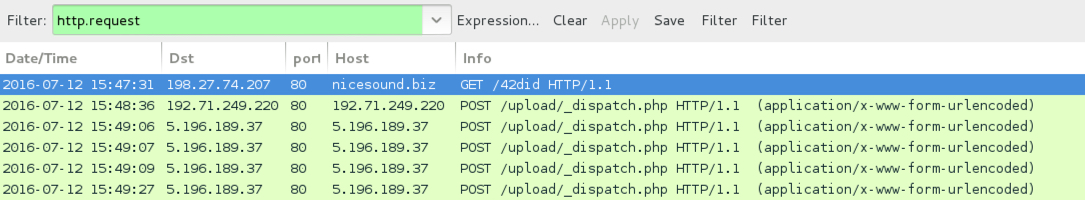
Shown above: Traffic generated from the first email.
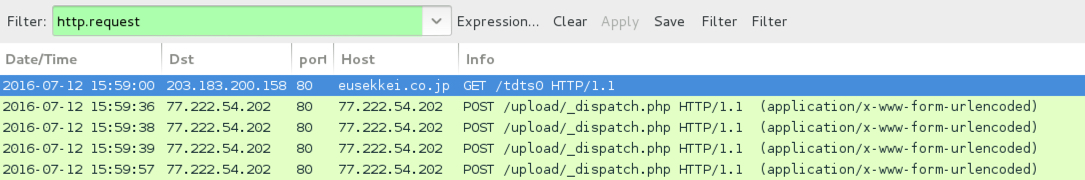
Shown above: Traffic generated from the second email.
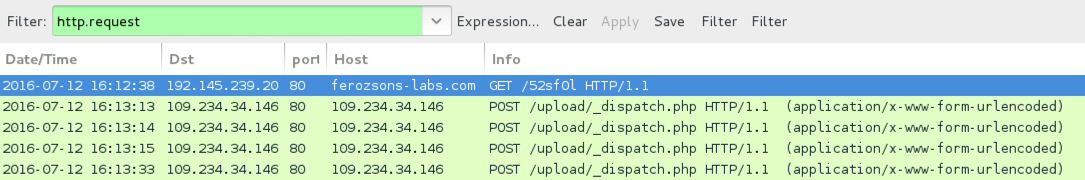
Shown above: Traffic generated from the third email.
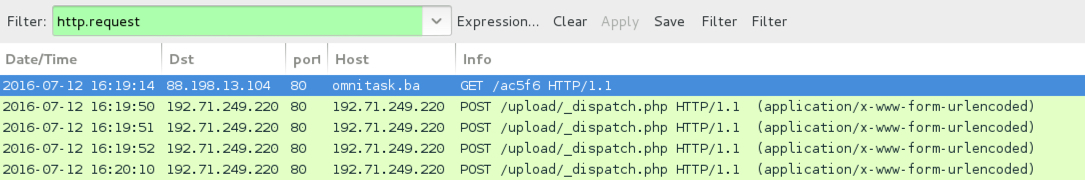
Shown above: Traffic generated from the 4th email.
ASSOCIATED URLS:
- 198.27.74[.]207 port 80 - nicesound[.]biz - GET /42did
- 192.71.249[.]220 port 80 - 192.71.249[.]220 - POST /upload/_dispatch.php
- 5.196.189[.]37 port 80 - 5.196.189[.]37 - POST /upload/_dispatch.php
- 203.183.200[.]158 port 80 - eusekkei[.]co[.]jp - GET /tdts0
- 77.222.54[.]202 port 80 - 77.222.54[.]202 - POST /upload/_dispatch.php
- 192.145.239[.]20 port 80 - ferozsons-labs[.]com - GET /52sf0l
- 109.234.34[.]146 port 80 - 109.234.34[.]146 - POST /upload/_dispatch.php
- 88.198.13[.]104 port 80 - omnitask[.]ba - GET /ac5f6
- 192.71.249[.]220 port 80 - 192.71.249[.]220 - POST /upload/_dispatch.php
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- mphtadhci5mrdlju[.]tor2web[.]org
- mphtadhci5mrdlju[.]onion[.]to
FILE HASHES
LOCKY RANSOMWARE SAMPLES FROM THE INFECTED HOSTS:
- SHA256 hash: 3f4314d12ae46f2369854fb3ac25ea40043778106362c5f1d370c14694cc777b
File name: 3VkFo0ErNhs9.exe
- SHA256 hash: 311a8c3f3a2e4f56a7e6e76a69b21f622d922f716dced83fc43d4c35aa692454
File name: OWVQ1Igf.exe
- SHA256 hash: bcc417d66308f680f163613d0debbb302e2637f6723f263babb87295b63a7fbf
File name: j4NxFPY45Bz3Q.exe
- SHA256 hash: 394dbe2e35487ba27d292a6bcc4ec5c5aa19eab88fa90c4511cfb5adea7db670
File name: xmLXfRH8gYbB7.exe
IMAGES
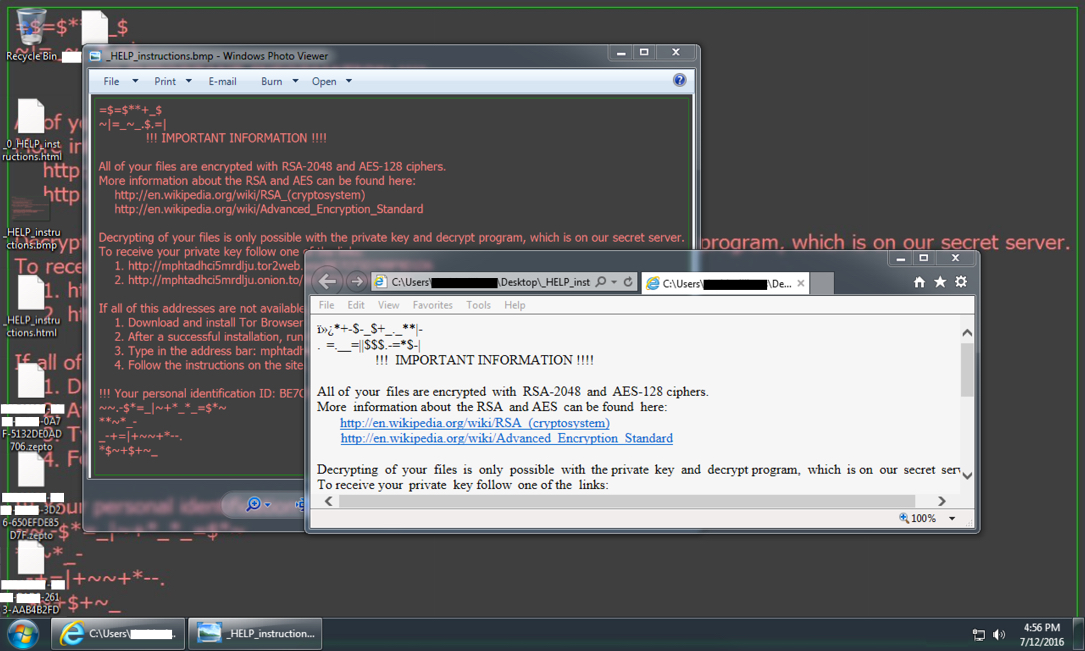
Shown above: Infected Windows desktop from one of the emails.
Click here to return to the main page.
