2016-07-15 - NEUTRINO EK FROM 5.2.72[.]237 SENDS GOOTKIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-15-Neutrino-EK-sends-Gootkit.pcap.zip 399.6 kB (399m636 bytes)
- 2016-07-15-Neutrino-EK-sends-Gootkit.pcap (425,124 bytes)
- 2016-07-15-Neutrino-EK-and-Gootkit-malware-files.zip 314.9 kB (314,920 bytes)
- 2016-07-15-Gootkit-task-for-persistence.txt (3,342 bytes)
- 2016-07-15-Neutrino-EK-flash-exploit.swf (82,712 bytes)
- 2016-07-15-Neutrino-EK-landing-page.txt (2,387 bytes)
- 2016-07-15-Neutrino-EK-payload-Gootkit.exe (198,144 bytes)
- csopapaxa.dll (102,912 bytes)
NOTES:

Shown above: Tweet from @malekal_morte on 2016-07-08.
- I'm assuming the payload is Gootkit. It's similar to previous malware triggering Gootkit alerts that also had SSL traffic over port 80 using a "MyCompany Ltd" certificate.
- If anyone has information this is not Gootkit, please let me know.
TRAFFIC
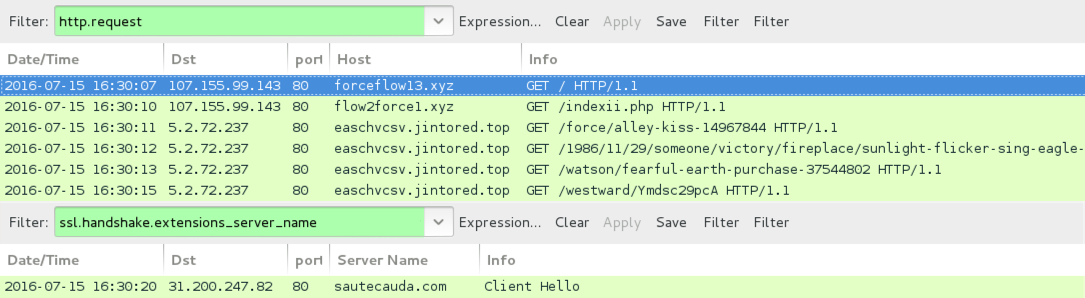
Shown above: Traffic from the first pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- 107.155.99[.]143 port 80 - forceflow13[.]xyz - Compromised site/ad traffic
- 107.155.99[.]143 port 80 - flow2force1[.]xyz - Redirect/gate
- 5.2.72[.]237 port 80 - easchvcsv.jintored[.]top - Neutrino EK
- 31.200.247[.]82 port 80 - sautecauda[.]com - SSL traffic on port 80 (Gootkit)
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 2ba6ba757ed744c76c31cff85c1a2725cc0d2eb03735816f66b927f1c0bdd4c5
File name: 2016-07-15-Neutrino-EK-flash-exploit.swf
PAYLOAD AND DROPPED MALWARE:
- SHA256 hash: 450a01b6e0278a48e7a6f3d7d95f543de6163a29d1c178c9dde054d312529984
File name: 2016-07-15-Neutrino-EK-payload-Gootkit.exe
- SHA256 hash: 927bb2c4f9c45614240c088f9f53aad5fab77598148c73b3cac63bc36b0c5fe9
File name: C:\Users\[username]\AppData\Roaming\Microsoft\Internet Explorer\csopapaxa.dll
IMAGES
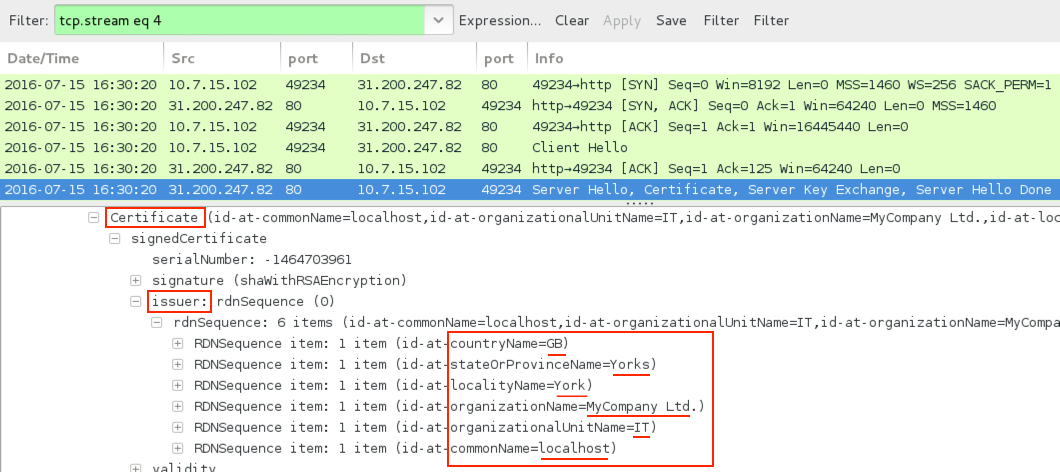
Shown above: SSL traffic over port 80 with the "MyCompany Ltd" certificate.
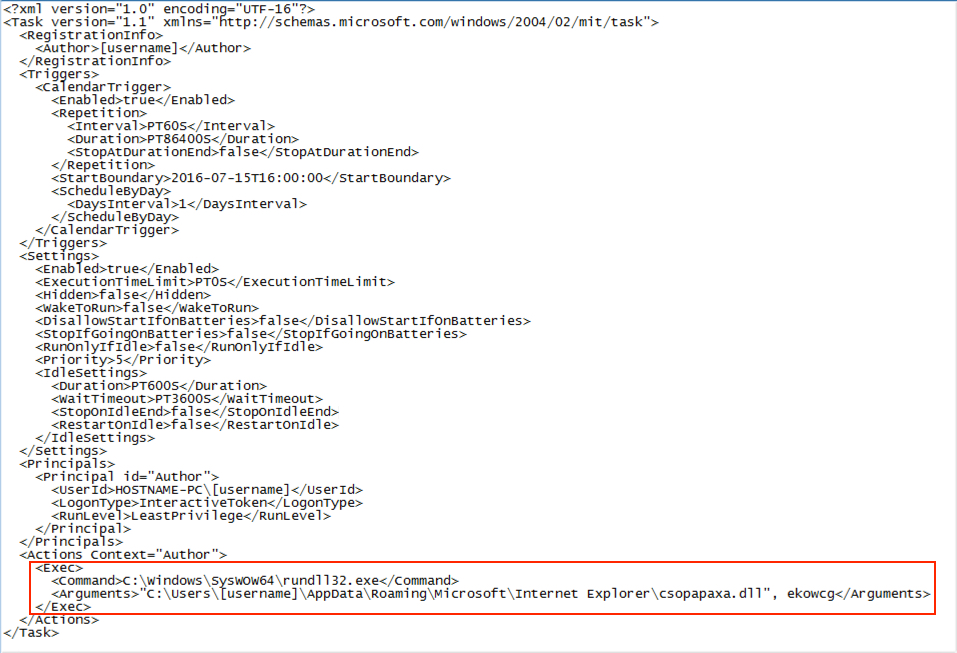
Shown above: Item from Task Scheduler that kept Gootkit persisetent on the infected Windows host.
Click here to return to the main page.
