2016-07-20 - NEUTRINO EK FROM 131.72.139[.]201 SENDS BANDARCHOR RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-20-Neutrino-EK-sends-Bandarchor-ransomware.pcap.zip 211.5 kB (211,456 bytes)
- 2016-07-20-Neutrino-EK-sends-Bandarchor-ransomware.pcap (230,777 bytes)
- 22016-07-20-Neutrino-EK-and-Bandarchor-ransomware-files.zip 179.9 kB (179,880 bytes)
- 2016-07-20-Neutrino-EK-flash-exploit.swf (84,143 bytes)
- 2016-07-20-Neutrino-EK-landing-page.txt (3,805 bytes)
- 2016-07-20-Neutrino-EK-payload-Bandarchor-ransomware.exe (115,830 bytes)
NOTES:
- More information on Bandarchor ransomware can be found here and here.
- Today's Bandarchor ransomware sample didn't leave any decryption instructions.
- It just listed the email addresses in the names of the encrypted files (see below).
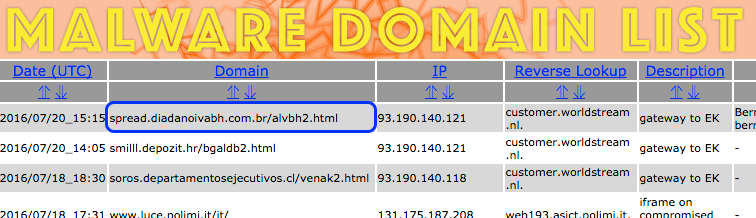
Shown above: My tipper for this traffic at Malwaredomainlist (no longer online).
TRAFFIC
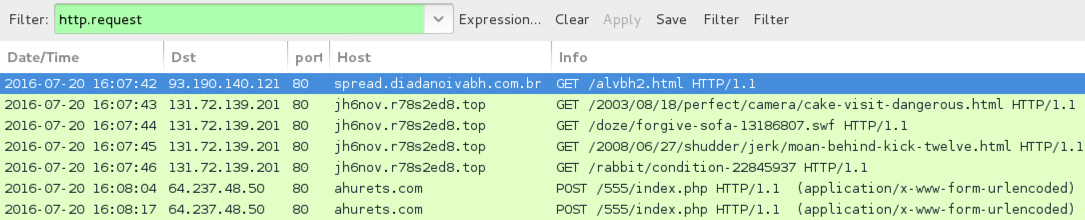
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- spread.diadanoivabh[.]com[.]br - GET /alvbh2.html - Redirect pointing to Neutrino EK
- 131.72.139[.]201 port 80 - jh6nov.r78s2ed8[.]top - Neutrino EK
- 64.237.48[.]50 port 80 - ahurets[.]com - POST /555/index.php - Post-infection traffic caused by the Bandarchor ransomware
EMAILS TO GET THE DECRYPT INSTRUCTIONS:
- aes256decoder@protonmail[.]com - First email address generated by the Bandachor ransomware
- decrypt@aesencryption[.]info - Second email address generated by the Bandachor ransomware
FILE HASHES
FLASH FILES:
- SHA256 hash: 6e045324f507802f9014451022d96a9fc3ba9b70e72637ca73ed830b1e1418de
File name: 2016-07-20-other-Neutrino-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: 042c522f7329535991ba113c46a6c766fa20bde039d71d96e0bbc06e94369443
File name: 2016-07-20-other-Neutrino-EK-payload-Bandarchor-ransomware.exe
IMAGES
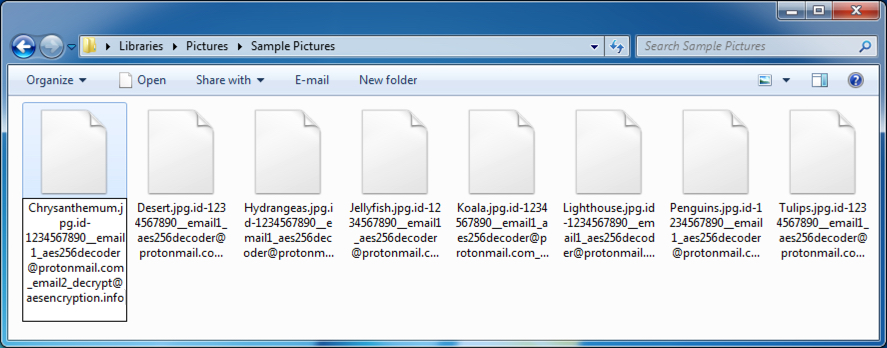
Shown above: Example of the encrypted file names from an infected host.
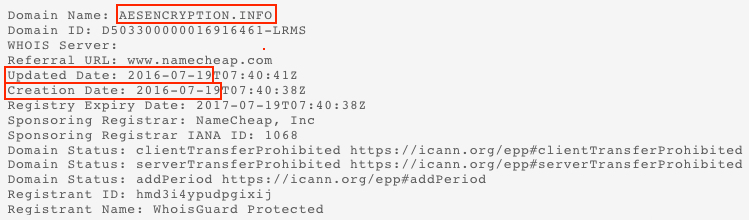
Shown above: Domain for the second email address was registered yesterday through Namecheap.
Click here to return to the main page.
