2016-07-24 - GUEST BLOG BY M. ZUBAIR RAFIQUE - MAGNITUDE EK SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
EDITOR'S NOTE:
- This blog post was submitted by M. Zubair Rafique, who was a PhD student at the University of Leuven in Belguim (KU Leuven) at the time of submission.
- This post examines a Magnitude exploit kit (EK) infection from July 2016.
- Zubair provides the full chain of events from the original referer to the malicious ad traffic to Magnitude EK.
- Click on any of the images below for a full-size view.
ASSOCIATED FILES:
- Zip archive of the pcap: 2016-07-24-Malvertising-leading-to-Magnitude-EK-sends-Cerber.pcap.zip 3.2 MB (3,240,351 bytes)
- 2016-07-24-Malvertising-leading-to-Magnitude-EK-sends-Cerber.pcap (4,533,360 bytes)
- Zip archive of the malware: 2016-07-24-samples-for-Magnitude-EK-and-Cerber-ransomware.zip 272.8 kB (272,780 bytes)
- 2016-07-24-Magnitude-EK-flash-exploit.swf (65,085 bytes)
- 2016-07-24-Magnitude-EK-flash-redirector.swf (718 bytes)
- 2016-07-24-Malvertising-leading-to-Magnitude-EK-payload-Cerber.exe (670,868 bytes)
DECEPTIVE AND COERCIVE ADVERTISING
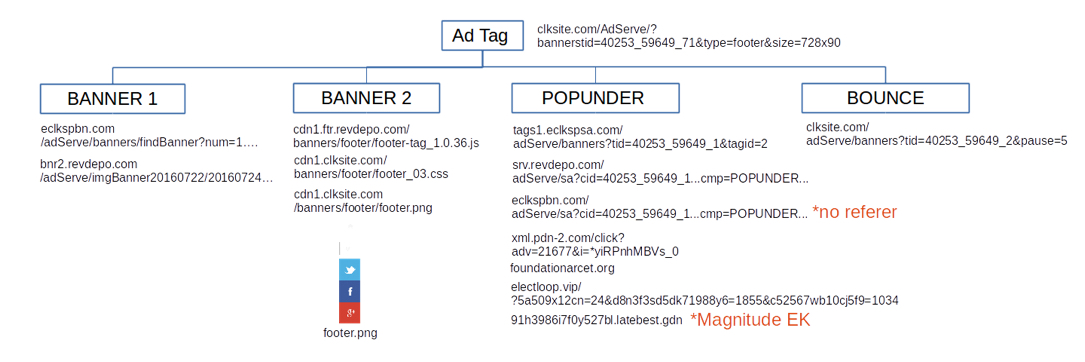
Shown above: A coercive advertisement leading to Magnitude EK.
REDIRECTION CHAIN LEADING TO MAGNITUDE EK:
- skzone[.]co[.]in - Publisher website that includes coercive advertisements
- tags1.eclkspsa[.]com - Ad network (Revenue Hits)
- srv.revdepo[.]com - Ad network (Revenue Hits) - Attach ad url to on-click event
- eclkspbn[.]com - Ad network (Revenue Hits) - Pop-under once clicked anywhere on the page
- xml.pdn-2[.]com - Ad landing page
- foundationarcet[.]org - Redirection and browser window fingerprinting
- electloop[.]vip - Gate
- 51.254.95[.]253 and 91h3986i7f0y527bl.latebest[.]gdn - Magnitude EK on 2016-07-24
FILE HASHES
FLASH REDIRECTS AND FLASH EXPLOIT:
- SHA256 hash: 0445ee20097bf09376af0b61e92805e6367445137708a1226e59fdc89b9d4bfd
File name: 2016-07-24-Magnitude-EK-flash-redirector.swf
- SHA256 hash: b95289ced424f535f91ce787202fb23fd2294c1a314c383292a259a002455611
File name: 2016-07-24-Magnitude-EK-flash-exploit.swf
MALWARE PAYLOAD:
- SHA256 hash: fd13c94d7bd6f9ec42403e1640292f97e5d69c5bb5e6e34a463981138540fbc6
File name: 2016-07-24-Malvertising-leading-to-Magnitude-EK-payload-Cerber.exe
IMAGES
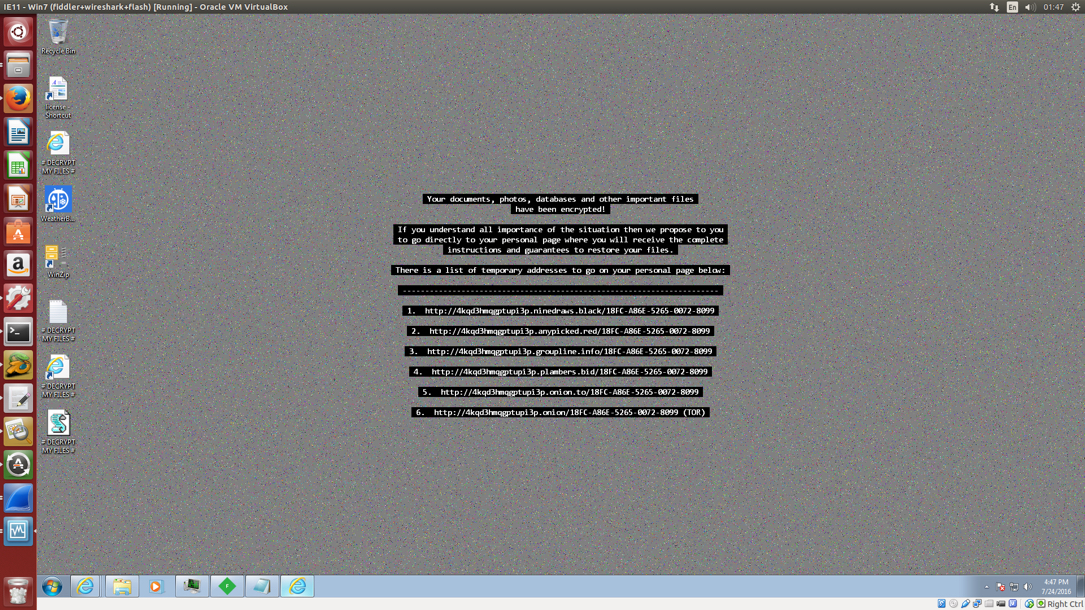
Shown above: Desktop of a Windows host infected with this Cerber ransomware sample.
Click here to return to the main page.
