2016-07-25 - MAGNITUDE EK FROM 51.254.181[.]39 SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-25-Magnitude-EK-sends-Cerber-ransomware.pcap.zip 827.6 kB (827,646 bytes)
- 2016-07-25-Magnitude-EK-sends-Cerber-ransomware.pcap (2,388,621 bytes)
- 2016-07-25-malware-and-artifacts-from-Magnitude-EK-and-Cerber-ransomware.zip 1.5 MB (1,526,171 bytes)
- 2016-07-25-Cerber-ransomware-decryption-instructions.bmp (2,825,394 bytes)
- 2016-07-25-Cerber-ransomware-decryption-instructions.html (12,171 bytes)
- 2016-07-25-Cerber-ransomware-decryption-instructions.txt (10,393 bytes)
- 2016-07-25-Magnitude-EK-flash-exploit.swf (58,683 bytes)
- 2016-07-25-Magnitude-EK-flash-redirect-file.swf (718 bytes)
- 2016-07-25-Magnitude-EK-landing-page.txt (670 bytes)
- 2016-07-25-Magnitude-EK-more-html.txt (23,011 bytes)
- 2016-07-25-Magnitude-EK-payload-Cerber-ransomware.exe (668,298 bytes)
NOTES:
- Big thanks, as always, to @malekal_morte for the Twitter posts that help me get this sort of traffic.
Shown above: Tweet from @malekal_morte on 2016-07-25.
TRAFFIC
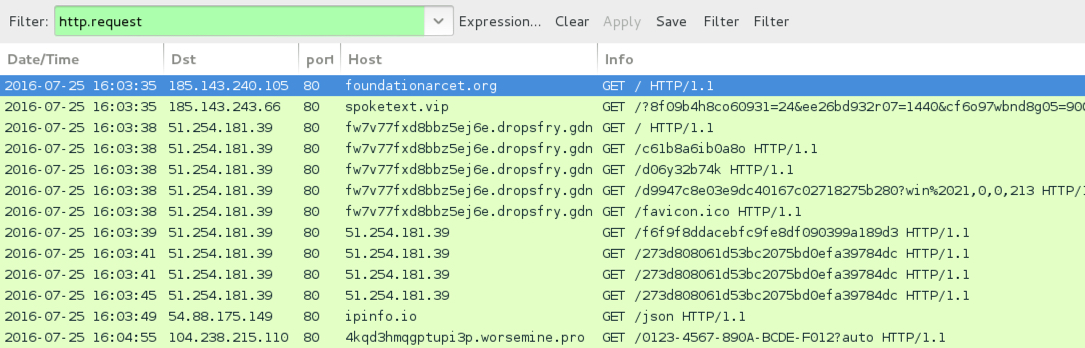
Shown above: Traffic from this infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- 185.143.240[.]105 port 80 - foundationarcet[.]org - First gate
- 185.143.243[.]66 port 80 - spoketext[.]vip - Second gate
- 51.254.181[.]39 port 80 - fw7v77fxd8bbz5ej6e.dropsfry[.]gdn - Magnitude EK
- 51.254.181[.]39 port 80 - 51.254.181[.]39 - Magnitude EK
- ipinfo[.]io - GET /json - Connectivity check by the Cerber ransomware
- 104.238.215[.]110 port 80 - 4kqd3hmqgptupi3p.worsemine[.]pro - Post-infection traffic from the infected host
- 31.184.234[.]0 - 31.184.235[.]255 (31.184.234[.]0/23) port 6892 - UDP scan from the infected host
OTHER DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- 4kqd3hmqgptupi3p.fishtotal[.]bid
- 4kqd3hmqgptupi3p.hurryball[.]asia
- 4kqd3hmqgptupi3p.innerband[.]lol
- 4kqd3hmqgptupi3p.onion[.]to
FILE HASHES
FLASH REDIRECT AND EXPLOIT:
- SHA256 hash: 12fe73f4e50d7f7ad82167ebc13121177b6c493671bd9ed18ed634226a46ebd1
File name: 2016-07-25-Magnitude-EK-flash-redirect-file.swf
- SHA256 hash: c6b2dcd7a28210fcaac6545b6ffcd4b9807c79ab2819cbecf12deb19ddd8b1b0
File name: 2016-07-25-Magnitude-EK-flash-exploit.swf
CERBER RANSOMWARE PAYLOAD:
- SHA256 hash: 8c0d32db20dcd1ec3a9ef4c036747493df85613019167b376a68b8d244d28b5b
File name: 2016-07-25-Magnitude-EK-payload-Cerber-ransomware.exe
Click here to return to the main page.