2016-07-25 - BOLETO CAMPAIGN - SUBJECT: BOLETO DE COBRANCA - FIX - URGENTE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-25-Boleto-campaign-infection-traffic.pcap.zip 1.0 MB (1,039,843 bytes)
- 2016-07-25-Boleto-campaign-infection-traffic.pcap (1,311,600 bytes)
- 2016-07-25-Boleto-campaign-email-example-and-downloaded-VBS-file.zip 2.3 kB (2,273 bytes)
- 2016-07-25-Boleto-campaign-email-0731-UTC.eml (1,458 bytes)
- VENC25072016axZ5MUdyYrNCCIIins5Chept7INWARCL.vbs (1,104 bytes)
NOTES:
- I've seen this at least once before, so I though I'd document it.
- You'll need to run the .vbs file in a test environment or sandbox to get samples of the dropped .dll and .exe files.
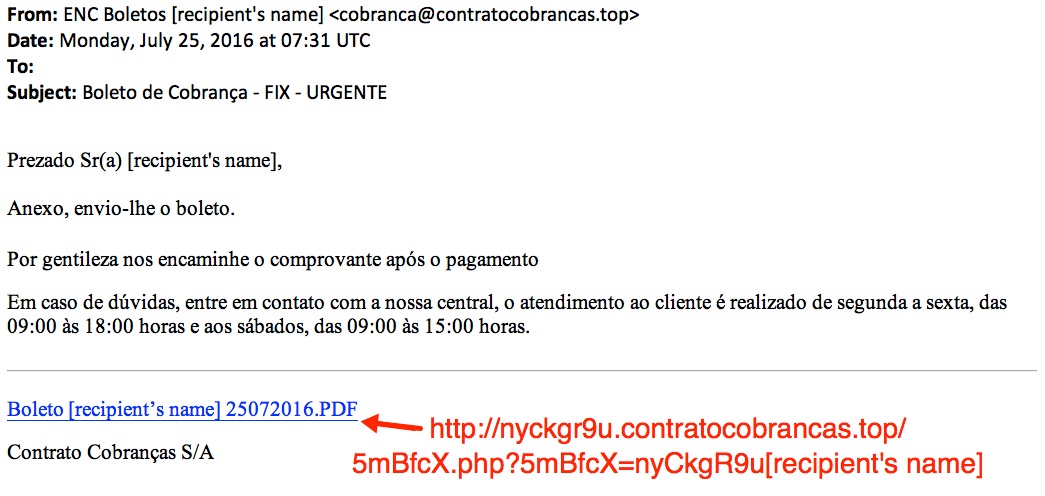
Shown above: Screenshot of the email.
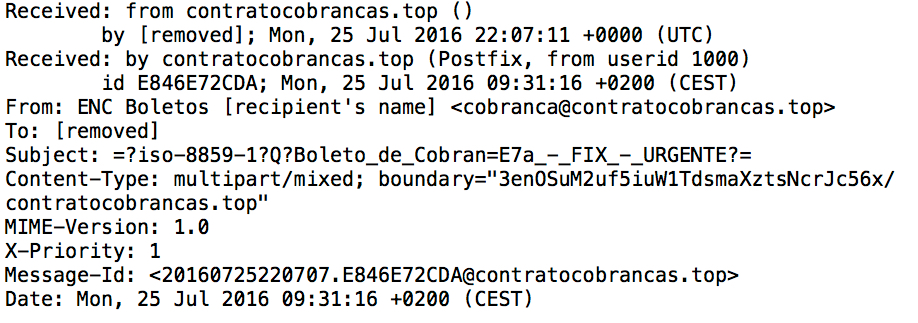
Shown above: Some headers from the email.
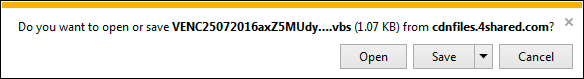
Shown above: .vbs file hosted on 4shared.com.
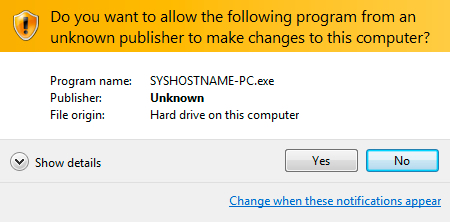
Shown above: A pop-up windows that appears at some point after running the .vbs file.
TRAFFIC
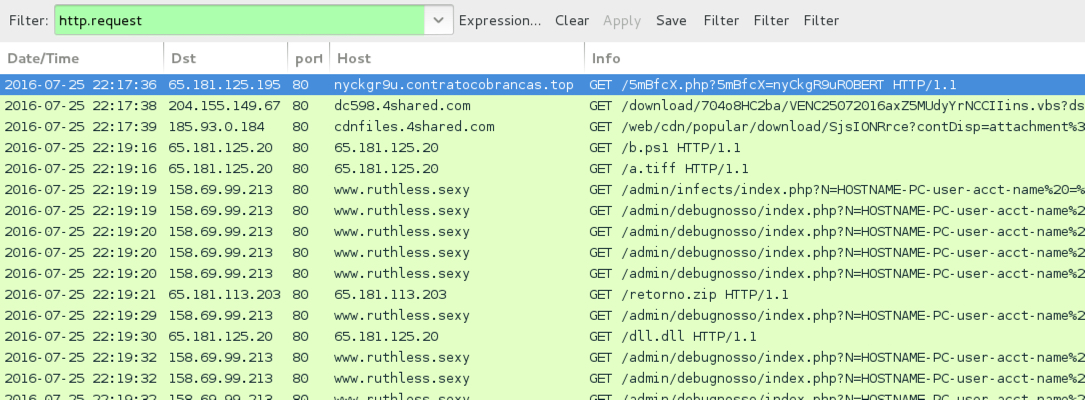

Shown above: Traffic from the second pcap filtered in Wireshark.
SOME OF THE DOMAINS:
- 65.181.125[.]195 port 80 - nyckgr9u.contratocobrancas[.]top - has URL that redirects to 4shared.com hosting .vbs file
- 65.181.125[.]20 port 80 - 65.181.125[.]20 - Follow-up malware
- 65.181.113[.]203 port 80 - 65.181.113[.]203 - Follow-up malware
- 158.69.99[.]213 port 80 - www.ruthless[.]sexy - Callback traffic from infected host
- 65.181.113[.]187 port 80 - api.devyatinskiy[.]ru - More callback traffic from the infected host
MALWARE AND ARTIFACTS ON THE INFECTED HOST
SOME MALWARE AND ARTIFACTS SEEN ON THE INFECTED HOST:
- C:\Users\[username]\AppData\Local\Temp\r1izmchi.oy2\NlsLexicons0009.dll
- C:\Users\[username]\AppData\Local\Temp\Java\Ionic.Zip.Reduced.dll
- C:\Users\[username]\AppData\Local\Temp\Java\makecert.exe
- C:\Users\[username]\AppData\Local\Temp\Java\SYSHOSTNAME-PC.exe
- C:\Users\[username]\AppData\Local\Temp\Java\HOSTNAME-PC.aes
- C:\Users\[username]\AppData\Local\Temp\Java\HOSTNAME-PC.zip
- C:\Users\[username]\AppData\Local\Temp\Java\warePlguin.txt
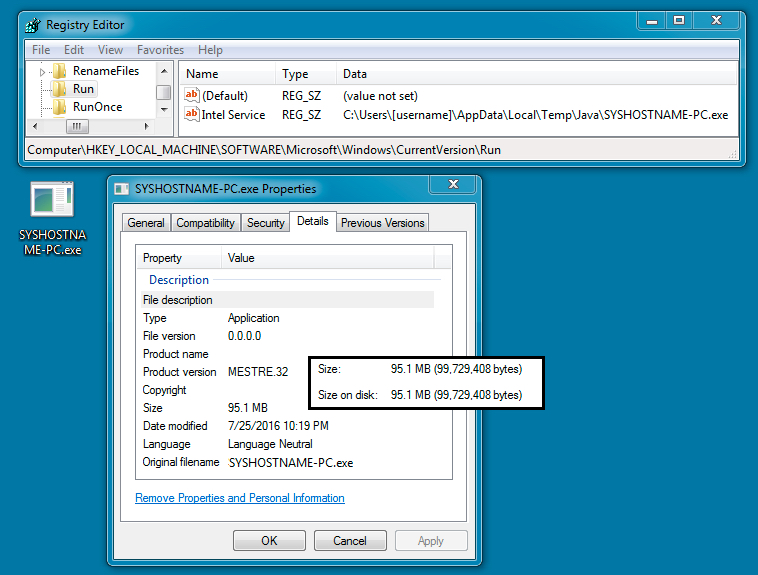
Shown above: The SYS[hostname].exe file persistent on the infected host.
Click here to return to the main page.
