2016-07-27 - AFRAIDGATE NEUTRINO EK FROM 185.140.33[.]99 SENDS LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-27-Afraidgate-Neutrino-EK-sends-Locky-ransomware-4-pcaps.zip 1.2 MB (1,196,140 bytes)
- 2016-07-26-Afraidgate-Neutrino-EK-sends-Locky-ransomware-first-run.pcap (312,623 bytes)
- 2016-07-26-Afraidgate-Neutrino-EK-sends-Locky-ransomware-second-run.pcap (329,561 bytes)
- 2016-07-27-Afraidgate-Neutrino-EK-sends-Locky-ransomware-first-run.pcap (325,181 bytes)
- 2016-07-27-Afraidgate-Neutrino-EK-sends-Locky-ransomware-second-run.pcap (314,273 bytes)
- 2016-07-27-Afraidgate-Neutrino-EK-and-Locky-ransomware-files.zip 949.0 kB (948,955 bytes)
- 2016-07-26-Afraidgate-Neutrino-EK-flash-exploit-first-run.swf (77,673 bytes)
- 2016-07-26-Afraidgate-Neutrino-EK-flash-exploit-second-run.swf (77,565 bytes)
- 2016-07-26-Afraidgate-Neutrino-EK-landing-page-first-run.txt (2,691 bytes)
- 2016-07-26-Afraidgate-Neutrino-EK-landing-page-second-run.txt (2,799 bytes)
- 2016-07-26-Afraidgate-Neutrino-EK-payload-Locky-ransomware-first-run.exe (202,240 bytes)
- 2016-07-26-Afraidgate-Neutrino-EK-payload-Locky-ransomware-second-run.exe (202,240 bytes)
- 2016-07-27-Afraidgate-Neutrino-EK-flash-exploit-first-run.swf (78,271 bytes)
- 2016-07-27-Afraidgate-Neutrino-EK-flash-exploit-second-run.swf (78,271 bytes)
- 2016-07-27-Afraidgate-Neutrino-EK-lading-page-first-run.txt (2,725 bytes)
- 2016-07-27-Afraidgate-Neutrino-EK-lading-page-second-run.txt (2,739 bytes)
- 2016-07-27-Afraidgate-Neutrino-EK-payload-Locky-ransomware-first-run.exe (203,264 bytes)
- 2016-07-27-Afraidgate-Neutrino-EK-payload-Locky-ransomware-second-run.exe (203,264 bytes)
- 2016-07-27-Locky-ransomware-decrypt-instructions.bmp (3,721,466 bytes)
- 2016-07-27-Locky-ransomware-decrypt-instructions.html (9,656 bytes)
NOTES:
- Background on the Afraidgate campaign can be found here.
- These Locky ransomware payloads are the ".zepto" variant.
- After a month or two, domains from the decryption instructions for this variant finally changed today.
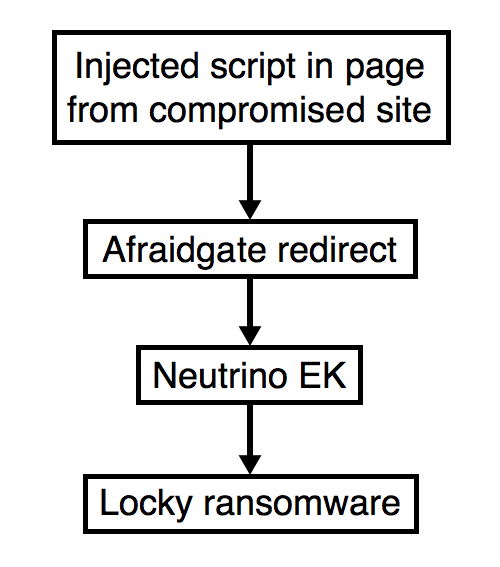
Shown above: Flowchart for this infection traffic.
TRAFFIC
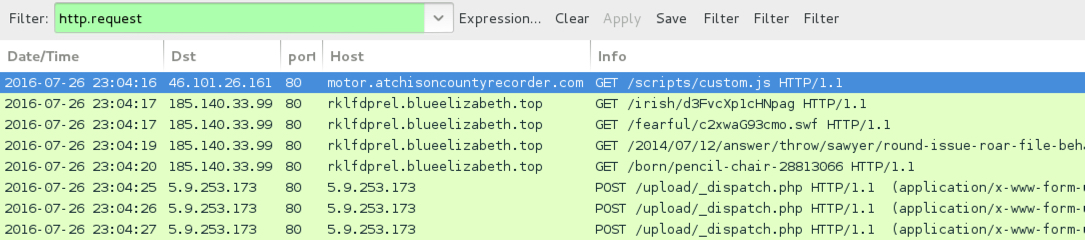
Shown above: Traffic from the first pcap filtered in Wireshark.
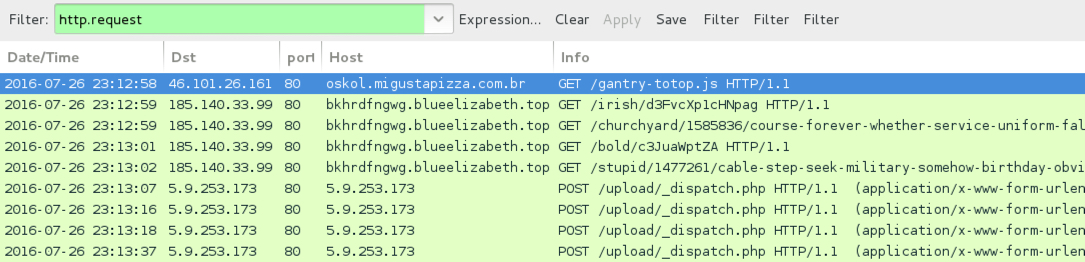
Shown above: Traffic from the second pcap filtered in Wireshark.
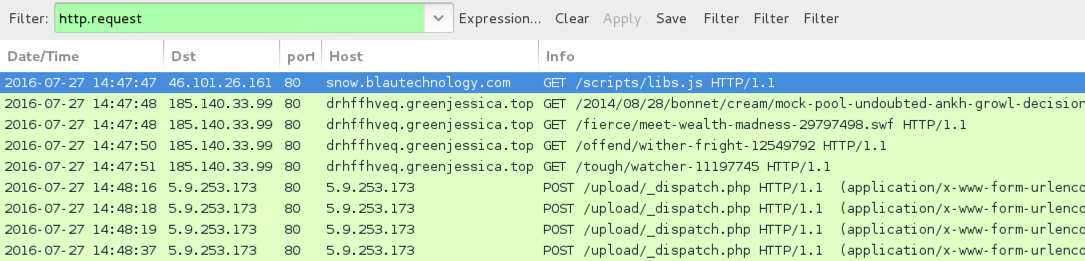
Shown above: Traffic from the third pcap filtered in Wireshark.
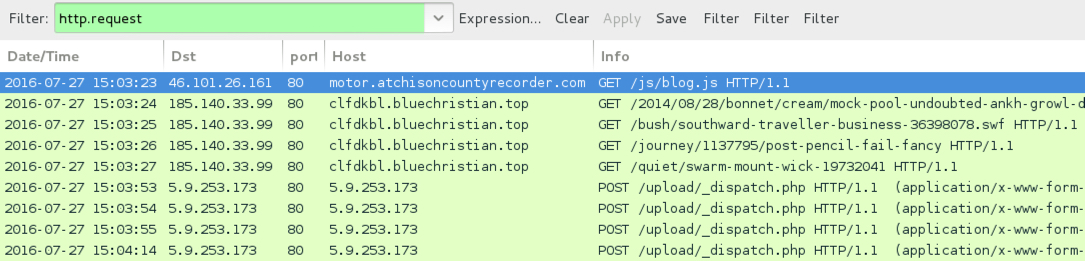
Shown above: Traffic from the 4th pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- 46.101.26[.]161 port 80 - motor.atchisoncountyrecorder[.]com - GET /scripts/custom.js - [Afriadgate redirect]
- 185.140.33[.]99 port 80 - rklfdprel.blueelizabeth[.]top - [Neutrino EK]
- 46.101.26[.]161 port 80 - oskol.migustapizza[.]com.br - GET /gantry-totop.js - [Afriadgate redirect]
- 185.140.33[.]99 port 80 - bkhrdfngwg.blueelizabeth[.]top - [Neutrino EK]
- 46.101.26[.]161 port 80 - snow.blautechnology[.]com - GET /scripts/libs.js - [Afriadgate redirect]
- 185.140.33[.]99 port 80 - drhffhveq.greenjessica[.]top - [Neutrino EK]
- 46.101.26[.]161 port 80 - motor.atchisoncountyrecorder[.]com - GET /js/blog.js - [Afriadgate redirect]
- 185.140.33[.]99 port 80 - clfdkbl.bluechristian[.]top - [Neutrino EK]
- 5.9.253[.]173 port 80 - 5.9.253[.]173 - POST /upload/_dispatch.php - [Locky ransomware post-infection traffic]
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- mphtadhci5mrdlju[.]tor2web[.]org - up through 2016-07-26
- mphtadhci5mrdlju[.]onion[.]to - up through 2016-07-26
- zjfq4lnfbs7pncr5[.]tor2web[.]org - as of 2016-07-27
- zjfq4lnfbs7pncr5[.]onion[.]to - as of 2016-07-27
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: 0fc2443a74c6ed9cfbf4dc7be68a36f91fcc2ebbade0a804d4a6ff9618bee2cf
File name: 2016-07-26-Afraidgate-Neutrino-EK-flash-exploit-first-run.swf
- SHA256 hash: 9e632302435863bd29315268b8e952c30c8e660c3a815cf7ca6872d95080178d
File name: 2016-07-26-Afraidgate-Neutrino-EK-flash-exploit-second-run.swf
- SHA256 hash: f7a345b5b68f93fd1d184e4eac1bbffb538eef05f048288751492889c10f4436
File name: 2016-07-27-Afraidgate-Neutrino-EK-flash-exploit-first-run.swf
- SHA256 hash: 2425fc0d9ef340909bd7aab7b6b3d10c3b4f99be7157f834e997d48acfff3350
File name: 2016-07-27-Afraidgate-Neutrino-EK-flash-exploit-second-run.swf
PAYLOADS:
- SHA256 hash: cab9aa5e67d41f82df7c5f14181e940b1d2757128c448c740b2bac7968faaf5f
File name: 2016-07-26-Afraidgate-Neutrino-EK-payload-Locky-rasomware-first-run.exe
- SHA256 hash: d45477fc51a1052a65c72f382e884f5236c720f7582386613403711bca5ab050
File name: 2016-07-26-Afraidgate-Neutrino-EK-payload-Locky-rasomware-second-run.exe
- SHA256 hash: 4d9333fcd3ccde1e82ba45fbf6b17fb42c7b034a84ccb56b972b62640828eb7b
File name: 2016-07-27-Afraidgate-Neutrino-EK-payload-Locky-rasomware-first-run.exe
- SHA256 hash: 1481629831dcedc7a33dfec59e591e80d8e555125cfa1532a609e80a86c6ec03
File name: 2016-07-27-Afraidgate-Neutrino-EK-payload-Locky-rasomware-second-run.exe
IMAGES
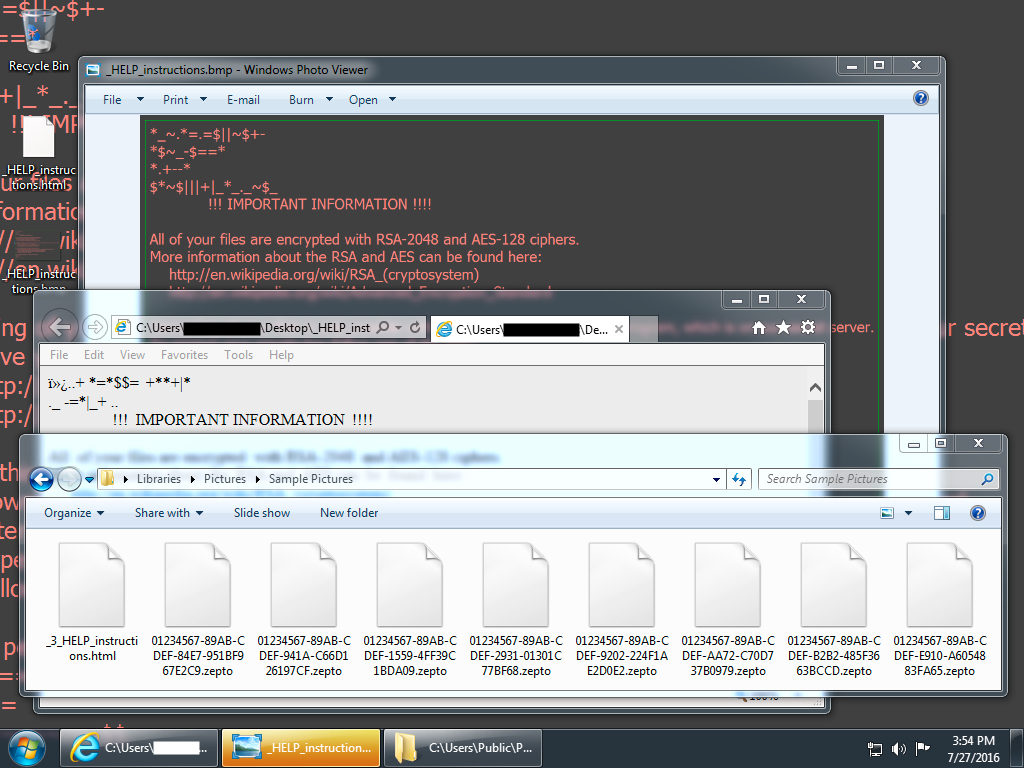
Shown above: Desktop of the infected Windows host.
Click here to return to the main page.