2016-08-05 - MAGNITUDE EK FROM 185.30.232[.]65 SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-08-05-Magnitude-EK-sends-Cerber-ransomware-2-pcaps.zip 940.5 kB (940,491 bytes)
- 2016-08-03-Magnitude-EK-sends-Cerber-ransomware-from-Threatglass-post.pcap (621,587 bytes)
- 2016-08-05-Magnitude-EK-sends-Cerber-ransomware.pcap (1,284,310 bytes)
- 2016-08-05-Magnitude-EK-and-Cerber-ransomware-files.zip 603.7 kB (603,746 bytes)
- 2016-08-03-Magnitude-EK-flash-redirect.swf (697 bytes)
- 2016-08-03-Magnitude-EK-landing-page.txt (665 bytes)
- 2016-08-03-Magnitude-EK-more-html.txt (7,017 bytes)
- 2016-08-05-Cerber-ransomware-decrypt-instructions.bmp (3,145,782 bytes)
- 2016-08-05-Cerber-ransomware-decrypt-instructions.html (19,720 bytes)
- 2016-08-05-Cerber-ransomware-decrypt-instructions.txt (10,508 bytes)
- 2016-08-05-Cerber-ransomware-decrypt-instructions.vbs (246 bytes)
- 2016-08-05-Magnitude-EK-flash-exploit.swf (58,606 bytes)
- 2016-08-05-Magnitude-EK-flash-redirect.swf (700 bytes)
- 2016-08-05-Magnitude-EK-landing-page.txt (658 bytes)
- 2016-08-05-Magnitude-EK-more-html.txt (23,279 bytes)
- 2016-08-05-Magnitude-EK-payload-Cerber-ransomware.exe (315,528 bytes)
NOTES:
- Noticed Magnitude EK sending Cerber ransomware on a Threatglass post from Wednesday 2016-08-03. I filtered and sanitized that traffic, and I've included a pcap of it with this blog.
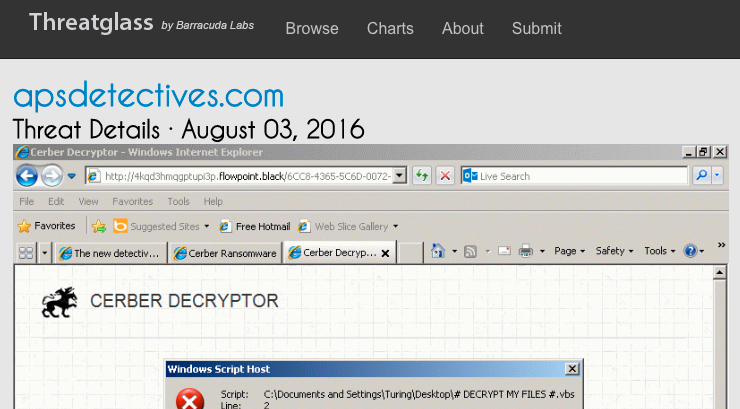
Shown above: Threatglass post with the pcap containing Magnitude EK traffic.
TRAFFIC
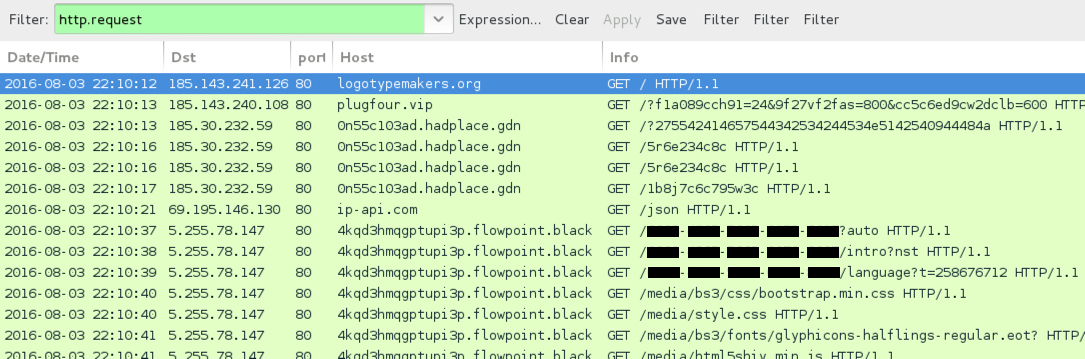
Shown above: Infection traffic from the Threatglass pcap on 2016-08-03 filtered in Wireshark.
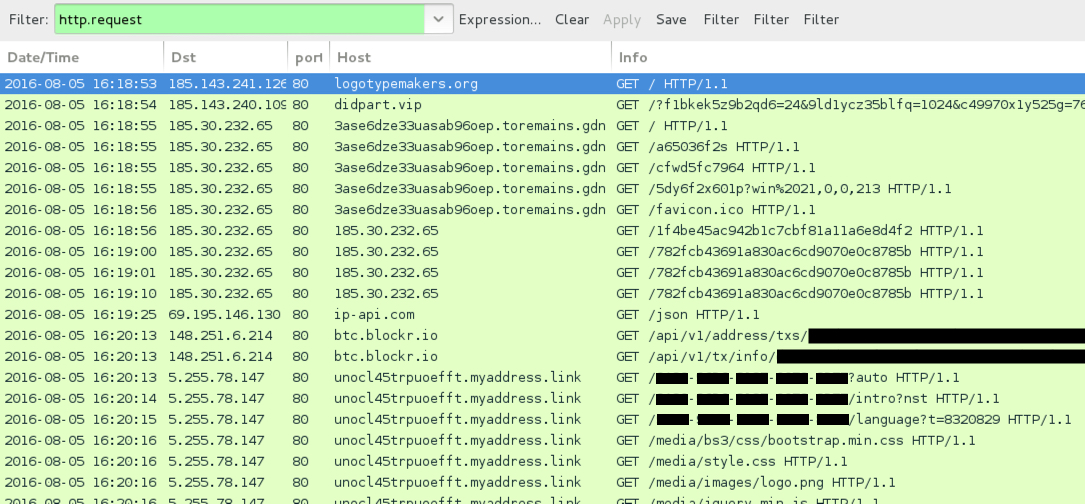
Shown above: Infection traffic from my pcap on 2016-08-05 filtered in Wireshark.
ASSOCIATED DOMAINS:
- 185.143.241[.]126 port 80 - logotypemakers[.]org - First gate
- 185.143.240[.]108 port 80 - plugfour[.]vip - Second gate on 2016-08-03
- 185.143.240[.]109 port 80 - didpart[.]vip - Second gate on 2016-08-05
- 185.30.232[.]59 port 80 - 0n55c103ad.hadplace[.]gdn - Magnitude EK on 2016-08-03
- 185.30.232[.]65 port 80 - 3ase6dze33uasab96oep.toremains[.]gdn - Magnitude EK on 2016-08-05
- ip-api[.]com - GET /json - Connectivity/IP check by the Cerber ransomware
- 5.255.78[.]147 port 80 - 4kqd3hmqgptupi3p.flowpoint[.]black - Cerber ransomware decrypt instructions on 2016-08-03
- 5.255.78[.]147 port 80 - unocl45trpuoefft.myaddress[.]link - Cerber ransomware decrypt instructions on 2016-08-05
- 31.184.234[.]0 - 31.184.235[.]255 (31.184.234[.]0/23) port 6892 - UDP scan from the host infected by Cerber ransomware
OTHER DOMAINS FROM THE CERBER RANSOMWARE DECRYPT INSTRUCTIONS:
- unocl45trpuoefft.flyingsix[.]red
- unocl45trpuoefft.aredark[.]mobi
- unocl45trpuoefft.effortany[.]win
- unocl45trpuoefft[.]onion[.]to
FILE HASHES
FLASH REDIRECTS AND FLASH EXPLOIT:
- SHA256 hash: 0b70209499644c4021382eabd5a00d8e318abcc26876019ec198e06935b610d9
File name: 2016-08-03-Magnitude-EK-flash-redirect.swf
- SHA256 hash: 4b311f4b09bed53d6bef4ed764df8a827bcc71c97067e3ef5019378819cebb87
File name: 2016-08-05-Magnitude-EK-flash-redirect.swf
- SHA256 hash: eb284501a3d39872b38f9745b38c35a0fd46d33efe78a3eda7496622adfd3b81
File name: 2016-08-05-Magnitude-EK-flash-exploit.swf
MALWARE PAYLOAD:
- SHA256 hash: 9bb24bba01d99e2d7e3e529ac1836fddd7218bb8eb54d5632f4f750655ef70db
File name: 2016-08-05-Magnitude-EK-payload-Cerber-ransomware.exe
Click here to return to the main page.