2016-08-15 - ZEPTO VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-08-15-Locky-ransomware-files.zip 1.2 MB (1,175,156 bytes)
- 2016-08-15-Locky-ransomware-email-tracker.csv (1,577 bytes)
- 2016-08-15-Locky-ransomware-infection-traffic.pcap (579,729 bytes)
- files-from-an-infected-host / _HELP_instructions.html (10,328 bytes)
- files-from-an-infected-host / _HELP_instructions.bmp (4,006,594 bytes)
- files-from-an-infected-host / ferdoxs.exe (283,648 bytes)
- attachments / 3220549838967.docm (33,517 bytes)
- attachments / 76D61A7FCA46CF93B78F1288CDF232F5.docm (33,523 bytes)
- attachments / 8203439616364.docm (33,467 bytes)
- attachments / 9180520338858.docm (33,517 bytes)
- attachments / 97B1C9B8FE58680AE514FFE0EA5C0F56.docm (33,604 bytes)
- attachments / A6C5307AE24DE3CC48C00F59EE26E1E4.docm (33,603 bytes)
- emails / 2016-08-15-email-pushing-Locky-ransomware-1233-1233-UTC.eml (48,616 bytes)
- emails / 2016-08-15-email-pushing-Locky-ransomware-1233-1251-UTC.eml (48,678 bytes)
- emails / 2016-08-15-email-pushing-Locky-ransomware-1233-1254-UTC.eml (48,651 bytes)
- emails / 2016-08-15-email-pushing-Locky-ransomware-1233-1309-UTC.eml (47,602 bytes)
- emails / 2016-08-15-email-pushing-Locky-ransomware-1233-1312-UTC.eml (47,498 bytes)
- emails / 2016-08-15-email-pushing-Locky-ransomware-1233-1337-UTC.eml (47,606 bytes)
EMAILS
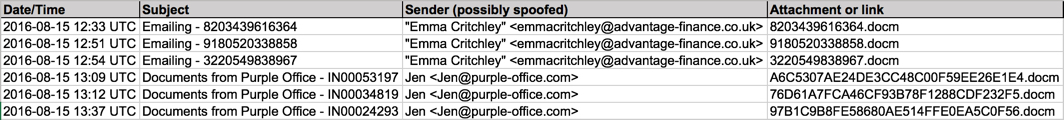
Shown above: Email data from the spreadsheet (part 1 of 2).
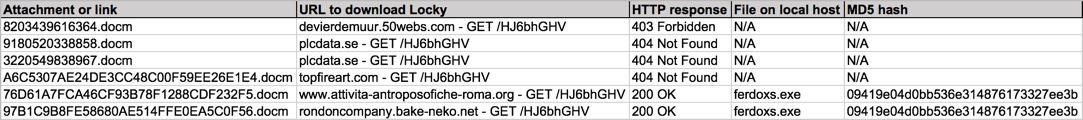
Shown above: Email data from the spreadsheet (part 2 of 2).
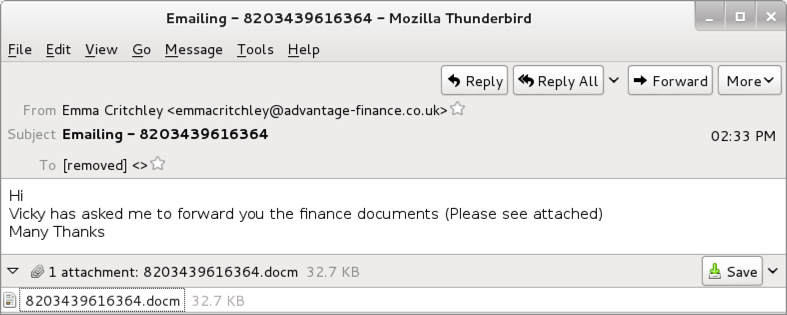
Shown above: Text of the emails (example 1 of 2).
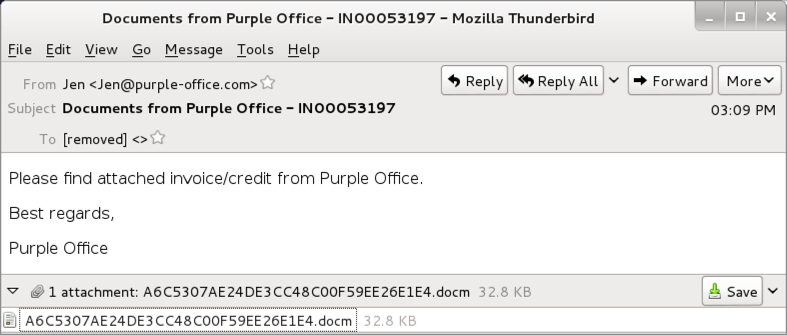
Shown above: Text of the emails (example 2 of 2).
FROM ADDRESSES / SUBJECT LINES:
- From: "Emma Critchley" <emmacritchley@advantage-finance[.]co[.]uk> - Subject: Emailing - 8203439616364
- From: "Emma Critchley" <emmacritchley@advantage-finance[.]co[.]uk> - Subject: Emailing - 9180520338858
- From: "Emma Critchley" <emmacritchley@advantage-finance[.]co[.]uk> - Subject: Emailing - 3220549838967
- From: Jen <Jen@purple-office[.]com> - Subject: Documents from Purple Office - IN00053197
- From: Jen <Jen@purple-office[.]com> - Subject: Documents from Purple Office - IN00034819
- From: Jen <Jen@purple-office[.]com> - Subject: Documents from Purple Office - IN00034819
TRAFFIC
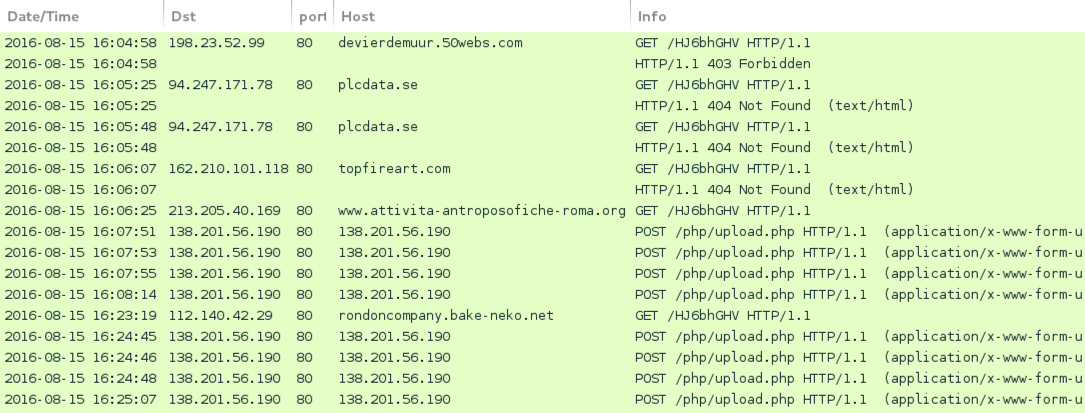
Shown above: Traffic from checking all the malspam attachments, filtered in Wireshark.
URLS FOR LOCKY RANSOMWARE DOWNLOAD BY THE MALICIOUS WORD MACROS:
- 198.23.52[.]99 port 80 - devierdemuur.50webs[.]com - GET /HJ6bhGHV [403 forbidden]
- 94.247.171[.]78 port 80 - plcdata[.]se - GET /HJ6bhGHV [404 not found]
- 162.210.101[.]118 port 80 - topfireart[.]com - GET /HJ6bhGHV [404 not found]
- 213.205.40[.]169 port 80 - www.attivita-antroposofiche-roma[.]org - GET /HJ6bhGHV
- 112.140.42[.]29 port 80 - rondoncompany.bake-neko[.]net - GET /HJ6bhGHV
POST-INFECTION TRAFFIC FROM THE LOCKY RANSOMWARE SAMPLE:
- 138.201.56[.]190 port 80 - 138.201.56[.]190 - POST /php/upload.php
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- zjfq4lnfbs7pncr5[.]tor2web[.]org
- zjfq4lnfbs7pncr5[.]onion[.]to
- NOTE: These are the same domains found in an email from a previous wave of Locky ransomware emails I blogged about on 2016-08-08.
FILE HASHES
LOCKY RANSOMWARE SAMPLE FROM THE INFECTED HOSTS:
- SHA256 hash: 945936b46faed93f1aadfa9894ece1d06f86033048c5fc07f73fbe1f23a40fe0
File name: ferdoxs.exe
IMAGES
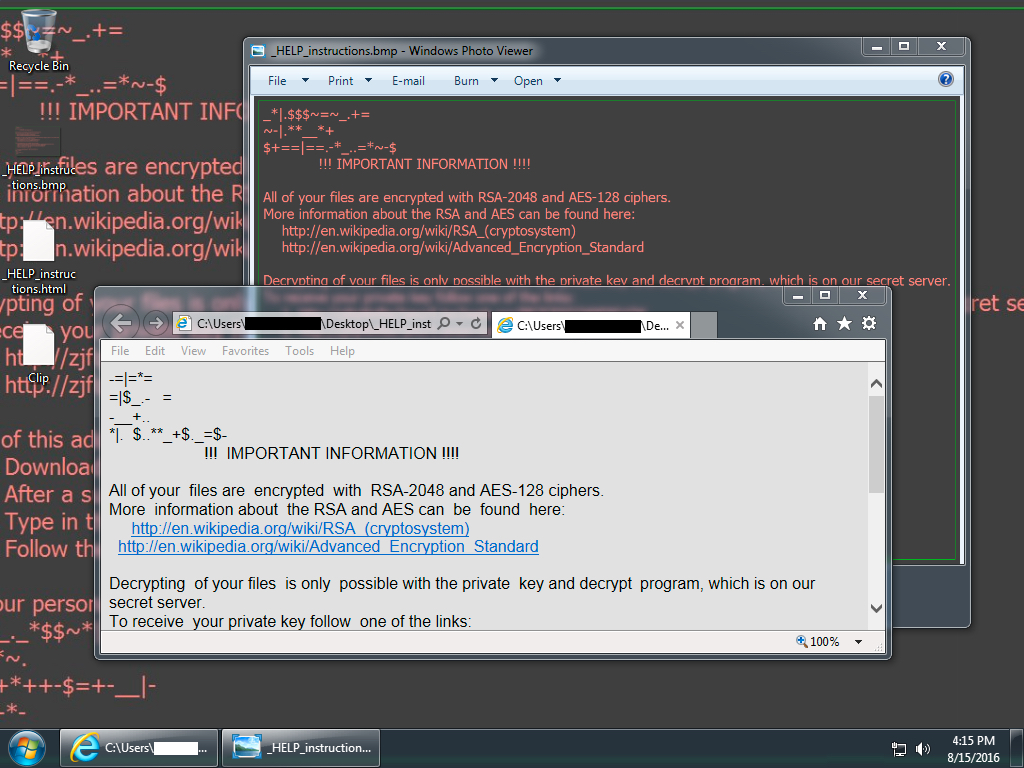
Shown above: Infected Windows desktop from one of the emails.
Shown above: This is something I haven't noticed before during a Locky ransomware infection.
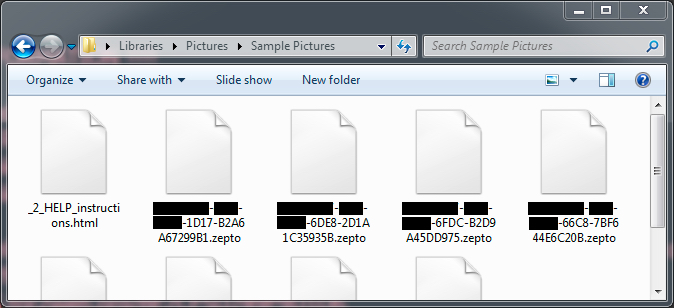
Shown above: Names of the encrypted files showing this is the Zepto variant of Locky ransomware.
Click here to return to the main page.
