2016-08-16 - BOLETO CAMPAIGN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-08-16-Boleto-campaign-infection-traffic.pcap.zip 2.4 MB (2,376,541 bytes)
- 2016-08-16-Boleto-campaign-infection-traffic.pcap (3,367,311 bytes)
- 2016-08-16-Boleto-campaign-spreadsheets.zip 3.4 kB (3,438 bytes)
- 2016-08-16-Boleto-campaign-email-tracker.csv (3,827 bytes)
- 2016-08-16-Boleto-campaign-malware-and-artifacts-info.csv (3,299 bytes)
- 2016-08-16-Boleto-campaign-emails-19-examples.zip 27.2 kB (27,202 bytes)
- 2016-08-16-Boleto-campaign-email-1723-UTC.eml (1,826 bytes)
- 2016-08-16-Boleto-campaign-email-1744-UTC.eml (1,843 bytes)
- 2016-08-16-Boleto-campaign-email-1748-UTC.eml (1,834 bytes)
- 2016-08-16-Boleto-campaign-email-1804-UTC.eml (1,826 bytes)
- 2016-08-16-Boleto-campaign-email-1814-UTC.eml (1,836 bytes)
- 2016-08-16-Boleto-campaign-email-1842-UTC.eml (1,812 bytes)
- 2016-08-16-Boleto-campaign-email-1934-UTC.eml (1,791 bytes)
- 2016-08-16-Boleto-campaign-email-1939-UTC.eml (1,804 bytes)
- 2016-08-16-Boleto-campaign-email-2004-UTC.eml (1,803 bytes)
- 2016-08-16-Boleto-campaign-email-2009-UTC.eml (1,832 bytes)
- 2016-08-16-Boleto-campaign-email-2016-UTC.eml (1,811 bytes)
- 2016-08-16-Boleto-campaign-email-2043-UTC.eml (1,838 bytes)
- 2016-08-16-Boleto-campaign-email-2045-UTC.eml (1,807 bytes)
- 2016-08-16-Boleto-campaign-email-2048-UTC.eml (1,845 bytes)
- 2016-08-16-Boleto-campaign-email-2057-UTC.eml (1,807 bytes)
- 2016-08-16-Boleto-campaign-email-2059-UTC.eml (1,835 bytes)
- 2016-08-16-Boleto-campaign-email-2236-UTC.eml (1,799 bytes)
- 2016-08-16-Boleto-campaign-email-2313-UTC.eml (1,836 bytes)
- 2016-08-16-Boleto-campaign-email-2331-UTC.eml (1,828 bytes)
- 2016-08-16-Boleto-campaign-malware-and-artifacts-from-infected-host.zip 1.3 MB (1,281,704 bytes)
- 0vwy5x5w.sxp.vbs (337 bytes)
- 24ec2c3h.m0r.vbs (337 bytes)
- 301ghajh.5rb.vbs (334 bytes)
- Ionic.Zip.Reduced.dll (253,440 bytes)
- SCOOBYDOO-PC.aes (16 bytes)
- SCOOBYDOO-PC.zip (964,004 bytes)
- SYSSCOOBYDOOPC35.xml (3,220 bytes)
- VENC15082016ffmud0qJIKUpZ0wTBSLZrIg8f86C7OuY.vbs (1,088 bytes)
- ctb4jdr2.dh1.vbs (337 bytes)
- dll.dll.exe (396,480 bytes)
- dps4f3n3.nzt.vbs (336 bytes)
- edoyjk0d.h1e.vbs (333 bytes)
- gtaak3kr.0vz.vbs (337 bytes)
- h4lvi4ka.cxo.vbs (337 bytes)
- hirsngu3.dv1.vbs (337 bytes)
- jorgxg12.xni.vbs (334 bytes)
- jve5betr.n45.vbs (333 bytes)
- jvqvnoqi.2sm.vbs (337 bytes)
- mmnzj3rr.oyz.vbs (7,843 bytes)
- v33fkxhy.2m3.vbs (336 bytes)
- zezmigbh.hxq.vbs (336 bytes)
EMAILS
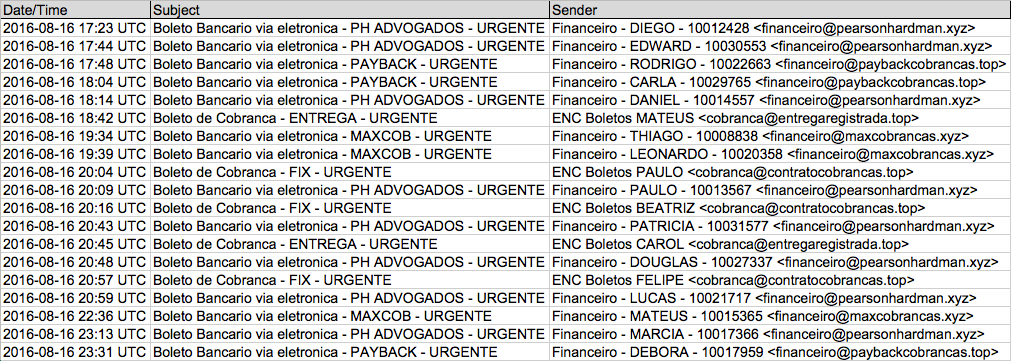
Shown above: Data from the spreadsheet (1 of 2).
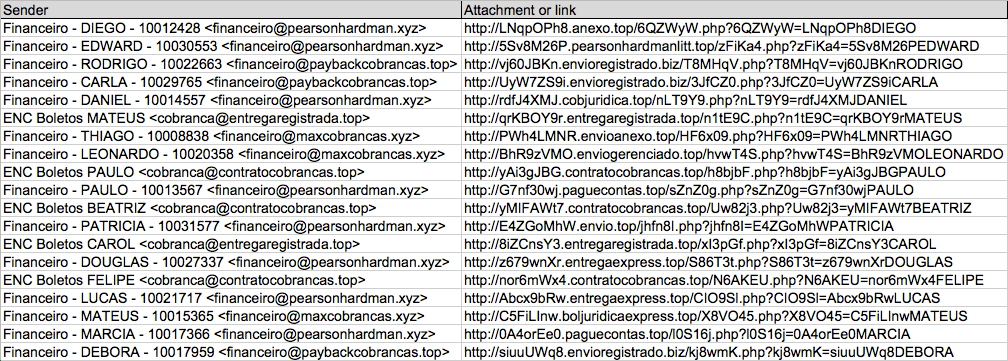
Shown above: Data from the spreadsheet (2 of 2).
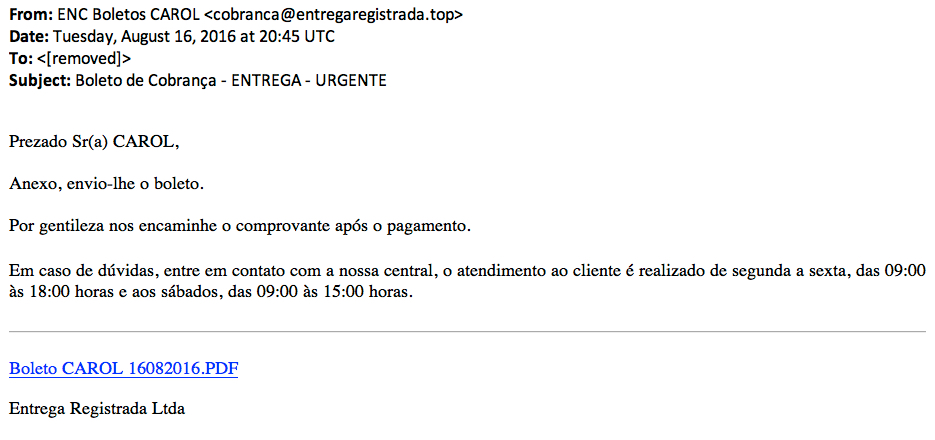
Shown above: Example of the emails.
EMAIL DETAILS
EXAMPLES OF SENDING EMAIL ADDRESSES:
- cobranca@contratocobrancas[.]top
- cobranca@entregaregistrada[.]top
- financeiro@maxcobrancas[.]xyz
- financeiro@paybackcobrancas[.]top
- financeiro@pearsonhardman[.]xyz
EXAMPLES OF SUBJECT LINES:
- Boleto Bancario via eletronica - MAXCOB - URGENTE
- Boleto Bancario via eletronica - PAYBACK - URGENTE
- Boleto Bancario via eletronica - PH ADVOGADOS - URGENTE
- Boleto de Cobranca - ENTREGA - URGENTE
- Boleto de Cobranca - FIX - URGENTE
DOMAINS FROM LINKS IN THE EMAILS:
- anexo[.]top
- boljuridicaexpress[.]top
- cobjuridica[.]top
- contratocobrancas[.]top
- entregaexpress[.]top
- entregaregistrada[.]top
- envio[.]top
- envioanexo[.]top
- enviogerenciado[.]top
- envioregistrado[.]biz
- paguecontas[.]top
- pearsonhardmanlitt[.]top
TRAFFIC
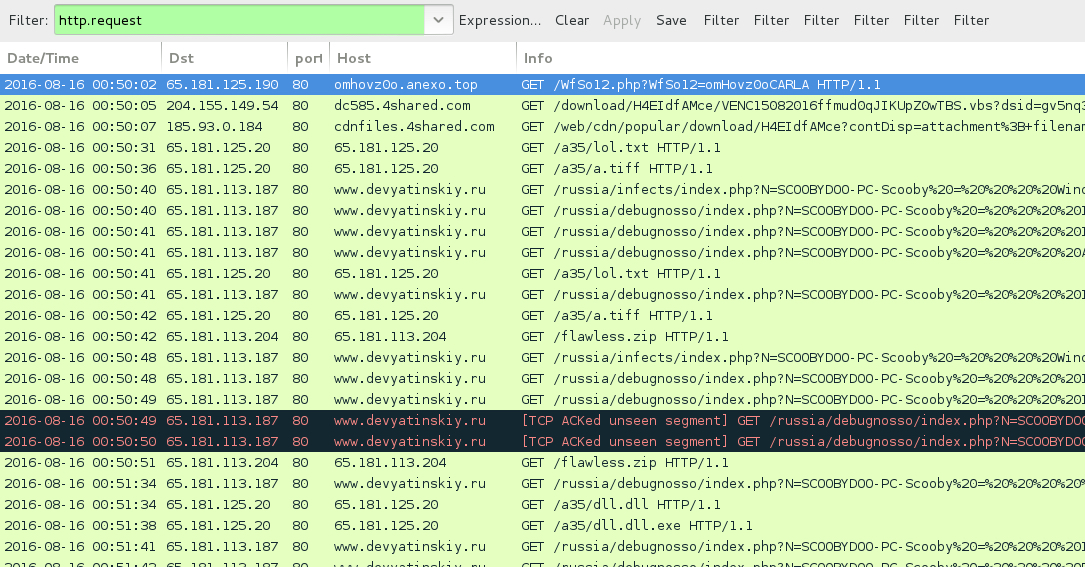
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- cdnfiles.4shared[.]com - VBS file from download link in the malspam
- 65.181.125[.]20 port 80 - 65.181.125[.]20 - GET /a35/lol.txt
- 65.181.125[.]20 port 80 - 65.181.125[.]20 - GET /a35/a.tiff
- 65.181.113[.]204 port 80 - 65.181.113[.]204 - GET /flawless.zip
- 65.181.113[.]187 port 80 - www.devyatinskiy[.]ru - HTTP callback traffic
- 65.181.125[.]20 port 80 - 65.181.125[.]20 - GET /a35/dll.dll
- 65.181.125[.]20 port 80 - 65.181.125[.]20 - GET /a35/dll.dll.exe
- 65.181.113[.]204 port 443 - ssl.houselannister[.]top - IRC traffic (botnet command and control)
- 198.105.244[.]228 port 443 - xxxxxxxxxxx.localdomain - Attempted TCP connections RST by server
- imestre.danagas[.]ru - Response 192.64.147[.]142 - no follow-up UDP or TCP connection
- imestre.noortakaful[.]top - No response
- imestre.waridtelecom[.]top - No response
- imestre.aduka[.]top - No response
- imestre.saltflowinc[.]top - No response
- imestre.moveoneinc[.]top - No response
- imestre.cheddarmcmelt[.]top - No response
- imestre.suzukiburgman[.]top - No response
- imestre.houselannister[.]top - response: 127.0.0[.]1
- xxxxxxxxxxx.localdomain - No response
Click here to return to the main page.
