2016-08-26 - RIG EK FROM 109.234.36[.]198 SENDS GRAYBIRD MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-08-26-Rig-EK-sends-Graybird-3-pcaps.zip 1.7 MB (1,748,729 bytes)
- 2016-08-26-Rig-EK-sends-Graybird-first-run.pcap (626,054 bytes)
- 2016-08-26-Rig-EK-sends-Graybird-second-run.pcap (774,743 bytes)
- 2016-08-26-Rig-EK-sends-Graybird-third-run.pcap (595,937 bytes)
- 2016-08-26-Rig-EK-and-Graybird-malware-files.zip 253.7 kB (253,737 bytes)
- 2016-08-26-Rig-EK-flash-exploit.swf (46,058 bytes)
- 2016-08-26-Rig-EK-landing-page-first-run.txt (5,239 bytes)
- 2016-08-26-Rig-EK-landing-page-second-run.txt (5,242 bytes)
- 2016-08-26-Rig-EK-landing-page-third-run.txt (5,237 bytes)
- 2016-08-26-Rig-EK-payload-Graybird-malware.exe (221,184 bytes)
- 2016-08-26-old-Graybird-sample-and-traffic-from-previous-year.zip 1.1 MB (1,072,854 bytes)
- 2015-10-02-analysis-of-word-doc-from-hybrid-analysis_com.pcap (977,900 bytes)
- 2015-10-02-dropped-Graybird-malware.exe (273,920 bytes)
- Suspected recipient and Amount 01102015.doc [Word document, probably distributed through email] (68,096 bytes)
NOTES ON THIS CAMPAIGN:
- I last saw a campaign using this gate pattern on 2016-07-21 when it was using Neutrino EK to distribute Bandarchor ransomware.
- Now it's using Rig EK to distribute the Graybird backdoor Trojan.
NOTES ON THE MALWARE PAYLOAD:
- Graybird is a family of backdoor Trojans first discovered back in 2003.
- The associated rules from the ETPRO ruleset on today's Graybird post-infection traffic originally came out in October 2015.
- Those ETPRO rules were based on malware downloaded from a malicious Word document macro.
- The Word document appears to be an attachment from malicious spam.
- Analysis of that October 2015 Word document is available here.
- I've included copies of the previous October 2015 Word document, the October 2015 dropped Graybird exe, and the 2015 traffic in archives for this blog post.
- 2016-08-26 update: I was direct-messaged on Twitter by someone who knows this malware as Latentbot ( link ).
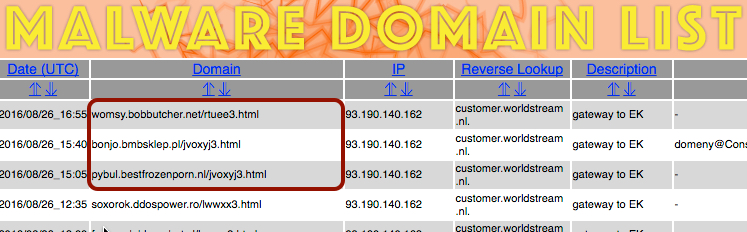
Shown above: My tipper for this traffic at malwaredomainlist.
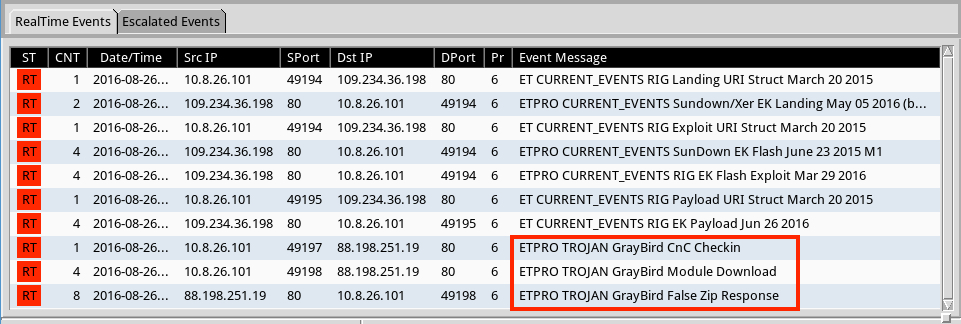
Shown above: Alerts on this traffic in Security Onion using Suricata and the ET Pro ruleset.
TRAFFIC
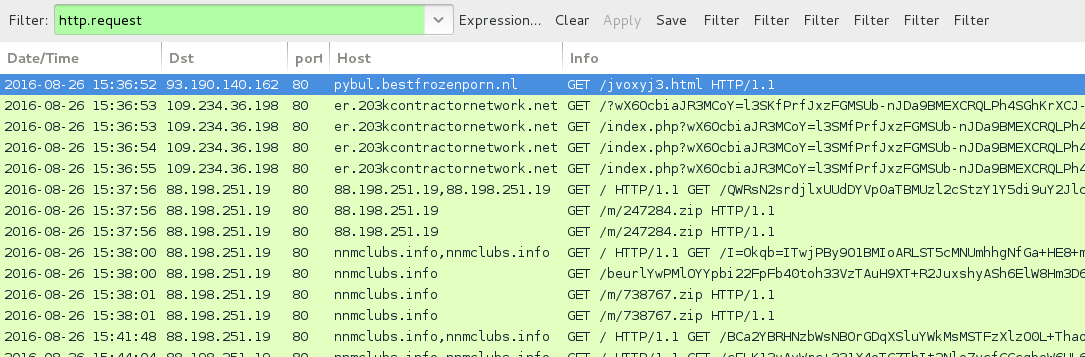
Shown above: Traffic from the first pcap filtered in Wireshark.

Shown above: Traffic from the second pcap filtered in Wireshark.
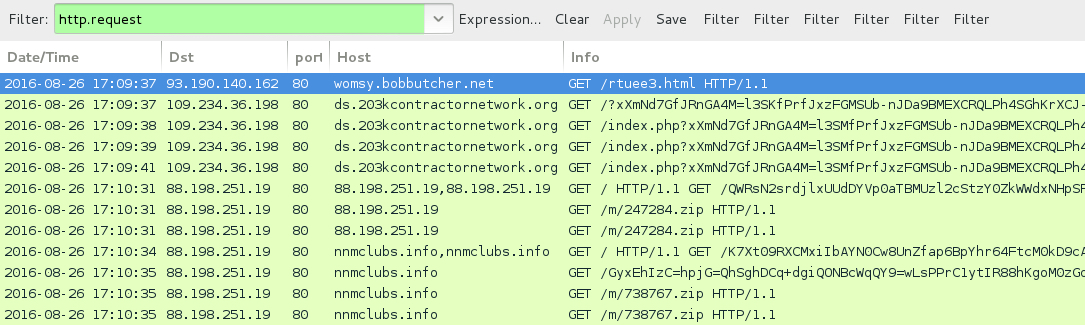
Shown above: Traffic from the third pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- 93.190.140[.]162 port 80 - pybul.bestfrozenporn[.]nl - GET /jvoxyj3.html - Gate pointing to Rig EK (first run)
- 93.190.140[.]162 port 80 - bonjo.bmbsklep[.]pl - GET /jvoxyj3.html - Gate pointing to Rig EK (second run)
- 93.190.140[.]162 port 80 - womsy.bobbutcher[.]net - GET /rtuee3.html - Gate pointing to Rig EK (third run)
- 109.234.36[.]198 port 80 - er.203kcontractornetwork[.]net - Rig EK (first run)
- 109.234.36[.]198 port 80 - ds.203kcontractornetwork[.]org - Rig EK (second and third runs)
- 88.198.251[.]19 port 80 - 88.198.251[.]19 - Various URLs for post-infection traffic
- 88.198.251[.]19 port 80 - 88.198.251[.]19 - GET /m/247284.zip
- 88.198.251[.]19 port 80 - nnmclubs[.]info - Various URLs for post-infection traffic
- 88.198.251[.]19 port 80 - nnmclubs[.]info - GET /m/738767.zip
- 88.198.251[.]19 port 8098 - 88.198.251[.]19 - Additional TCP post-infection traffic
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 1878e064d0606514a656204776e51fcaa4746666f859fda05f96656fdcf2886a
File name: 2016-08-26-Rig-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: 1005a2aaea29fffb19014ae2d76c6fd487fc26dc5f46d1f128141fc89b026e04
File name: 2016-08-26-Rig-EK-payload-Graybird-malware.exe
IMAGES
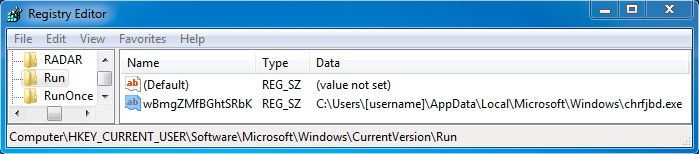
Shown above: Registry entry for persistence of the Graybird malware (first infection).
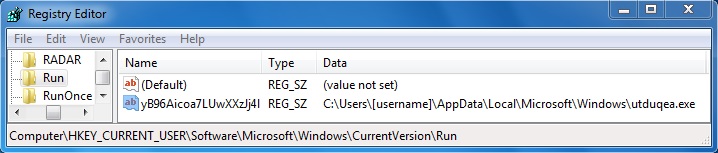
Shown above: Registry entry for persistence of the Graybird malware (second infection).
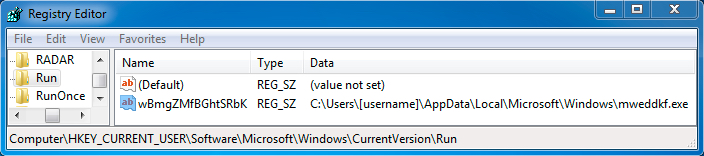
Shown above: Registry entry for persistence of the Graybird malware (third infection).
Click here to return to the main page.
