2016-08-26 - RIG EK FROM 178.32.92[.]0/24
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-08-29-Rig-EK-traffic-2-pcaps.zip 314.9 kB (314,858 bytes)
- 2016-08-29-Rig-EK-traffic-first-run.pcap (217,070 bytes)
- 2016-08-29-Rig-EK-traffic-second-run.pcap (267,577 bytes)
- 2016-08-29-Rig-EK-malware-and-artifacts.zip 140.3 kB (140,264 bytes)
- 2016-08-29-Rig-EK-flash-exploit.swf (46,081 bytes)
- 2016-08-29-Rig-EK-landing-page-first-run.txt (3,659 bytes)
- 2016-08-29-Rig-EK-landing-page-second-run.txt (3,664 bytes)
- 2016-08-29-Rig-EK-payload.exe (188,928 bytes)
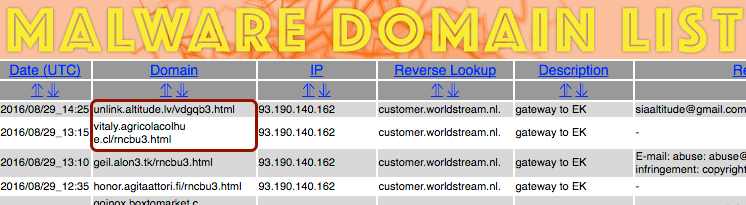
Shown above: My tipper for this traffic at malwaredomainlist.
TRAFFIC

Shown above: Traffic from the first pcap filtered in Wireshark.
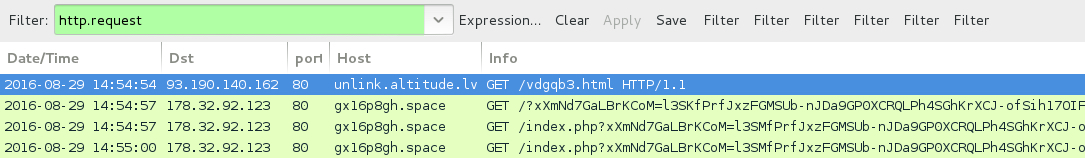
Shown above: Traffic from the second pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- 93.190.140[.]162 port 80 - vitaly.agricolacolhue[.]cl - GET /rncbu3.html - Gate URL (first run)
- 93.190.140[.]162 port 80 - unlink.altitude[.]lv - GET /vdgqb3.html - Gate URL (second run)
- 178.32.92[.]122 port 80 - l8uh5l1m[.]top - Rig EK (first run)
- 178.32.92[.]123 port 80 - gx16p8gh[.]space - Rig EK (second run)
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: a36d658b9d49b7f6e66015865db24cffd9fa0ac1e548616e03ce124b12742a88
File name: 2016-08-29-Rig-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: 9e16973b9234feb1a51c001b4338bf0929e0b967b6b877667a0d8c8f3c122eea
File name: 2016-08-29-Rig-EK-payload.exe
IMAGES
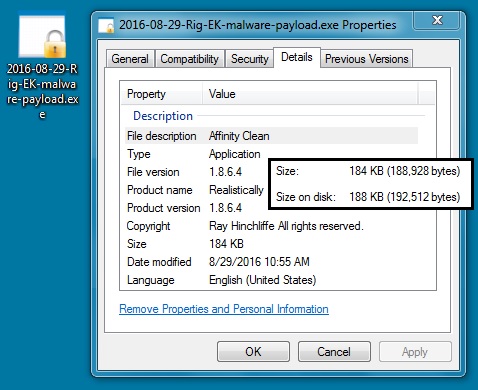
Shown above: The malware payload sent by this campaign's Rig EK.
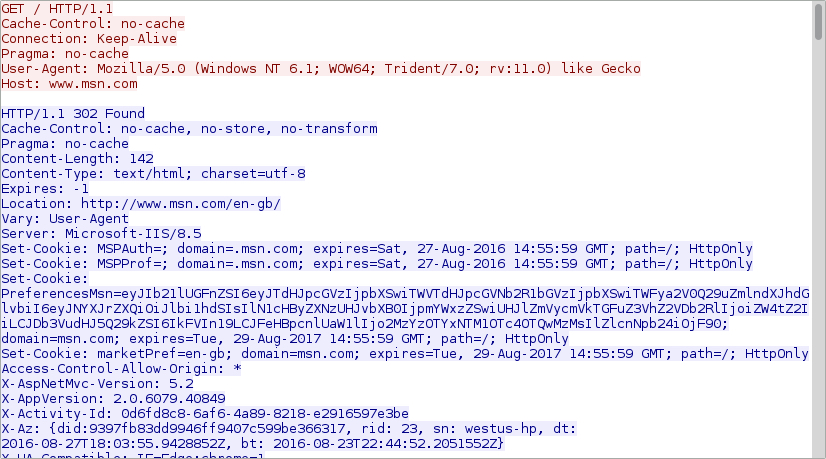
Shown above: The only post-infection traffic I saw from the malware.
Click here to return to the main page.
