2016-09-16 - PSEUDO-DARKLEECH RIG EK STILL FAILS AT DLL PAYLOAD - CRYPMIC RANSOMWARE SENT AS EXE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-16-pseudoDarkleech-Rig-EK-4-pcaps.zip 504.6 kB (504,578 bytes)
- 2016-09-15-pseudoDarkleech-Rig-EK-first-example.pcap (64,369 bytes)
- 2016-09-15-pseudoDarkleech-Rig-EK-second-example.pcap (71,369 bytes)
- 2016-09-16-pseudoDarkleech-Rig-EK-first-example.pcap (66,773 bytes)
- 2016-09-16-pseudoDarkleech-Rig-EK-second-example.pcap (558,458 bytes)
- 2016-09-16-pseudoDarkleech-Rig-EK-malware-and-artifacts.zip 257.8 kB (257,806 bytes)
- 2016-09-15-page-from-meinwhisky_com-with-injected-script-first-example.txt (67,513 bytes)
- 2016-09-15-pseudoDarkleech-Rig-EK-flash-exploit-both-examples.swf (25,720 bytes)
- 2016-09-15-pseudoDarkleech-Rig-EK-landing-page-first-example.txt (29,916 bytes)
- 2016-09-15-pseudoDarkleech-Rig-EK-landing-page-second-example.txt (29,952 bytes)
- 2016-09-16-CrypMIC-ransomware-decrypt-instructions.bmp (2,457,654 bytes)
- 2016-09-16-CrypMIC-ransomware-decrypt-instructions.html (1,652 bytes)
- 2016-09-16-CrypMIC-ransomware-decrypt-instructions.txt (1,652 bytes)
- 2016-09-16-page-from-meinwhisky_com-with-injected-script-first-example.txt (67,506 bytes)
- 2016-09-16-page-from-meinwhisky_com-with-injected-script-second-example.txt (68,073 bytes)
- 2016-09-16-pseudoDarkleech-Rig-EK-flash-exploit-both-examples.swf (25,720 bytes)
- 2016-09-16-pseudoDarkleech-Rig-EK-landing-page-first-example.txt (29,870 bytes)
- 2016-09-16-pseudoDarkleech-Rig-EK-landing-page-second-example.txt (29,928 bytes)
- 2016-09-16-pseudoDarkleech-Rig-EK-payload-CrypMIC-ransomware.exe (103,936 bytes)
- 2016-09-16-pseudoDarkleech-Rig-EK-payload-failed-attempt.dll (126 bytes)
NOTES:
- Thanks to Baber for informing me about today's compromised website.
- The pseudoDarkleech campaign continues to use Rig EK, which started as early as Wednesday 2016-09-14
- Just like last time, any attempt by Rig EK to send the payload as a DLL failed.
- I used an older version of Internet Explorer and other outdated applications to finally get CrypMIC ransomware payload, which was sent as an EXE.
- When Rig EK sent CrypMIC ransomware as an EXE, it was obfuscated with an encryption algorithm instead of XOR-ing an ASCII string like I've previously seen.
BACKGROUND ON THE PSEUDO-DARKLEECH CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-22 - PaloAlto Networks Unit 42 blog: Campaign Evolution: Darkleech to Pseudo-Darkleech and Beyond
- 2016-07-02 - SANS ISC diary: Change in patterns for the pseudoDarkleech campaign
BACKGROUND ON CRYPMIC RANSOMWARE:
- 2016-07-06 - SANS ISC diary: CryptXXX ransomware updated [The date I first noticed this new branch of ransomware.]
- 2016-07-14 - From the Proofpoint blog [link]: "We believe that CryptXXX is in active development and possibly split off into two branches. The original branch is now up to version 5.001 (we wrote about the upgrade to version 3.100 near the end of May), while the new branch uses a different format for versioning and will require further analysis."
- 2016-07-20 - TrendLabs Security Intelligence Blog - CrypMIC Ransomware Wants to Follow CryptXXX's Footsteps [TrendLabs analyzes the new branch and names it.]
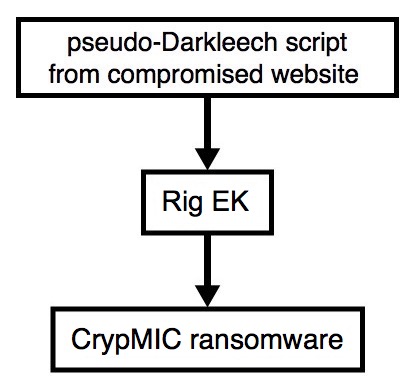
Shown above: Flowchart for this infection traffic.
TRAFFIC
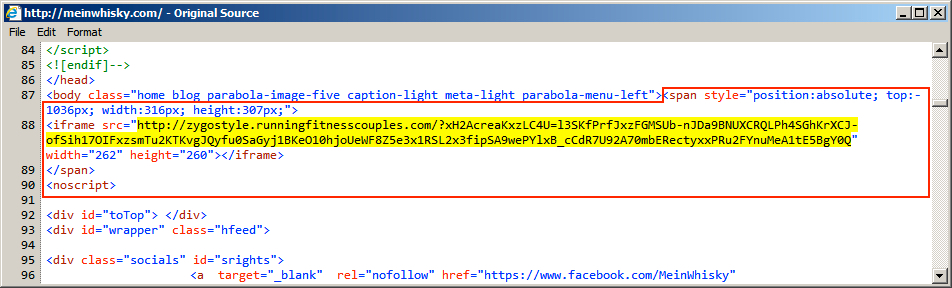
Shown above: An example of injected script in a page from the compromised website.
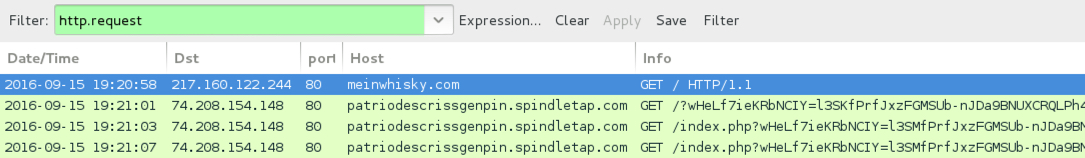
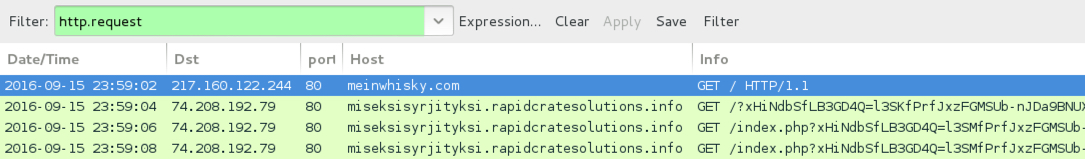
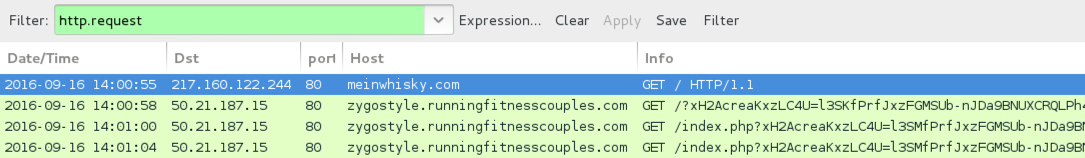
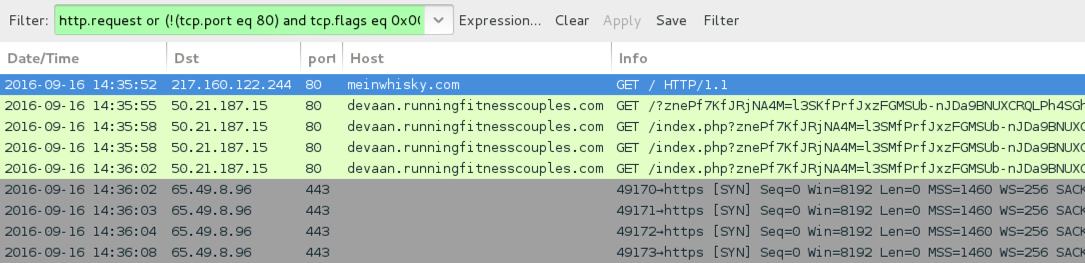
ASSOCIATED DOMAINS:
- meinwhisky[.]com - Compromised site
- 74.208.154[.]148 port 80 - patriodescrissgenpin.spindletap[.]com - Rig EK (2016-09-15 first example)
- 74.208.192[.]79 port 80 - miseksisyrjityksi.rapidcratesolutions[.]info - Rig EK (2016-09-15 second example)
- 50.21.187[.]15 port 80 - zygostyle.runningfitnesscouples[.]com - Rig EK (2016-09-16 first example)
- 50.21.187[.]15 port 80 - devaan.runningfitnesscouples[.]com - Rig EK (2016-09-16 second example)
- 65.49.8[.]96 port 443 - post-infection CrypMIC ransomware callback, custom encoded and clear text, not HTTPS/SSL/TLS (both infections)
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- xijymvzq4zkyubfe[.]onion[.]to
- xijymvzq4zkyubfe[.]onion[.]city
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: 5db51585ee1e1e4bdcca6c39050f71b6ba237bde328d610c28ee8f8659be9551
File name: 2016-09-15-pseudoDarkleech-Rig-EK-flash-exploit-both-examples.swf
File name: 2016-09-16-pseudoDarkleech-Rig-EK-flash-exploit-both-examples.swf
PAYLOAD:
- SHA256 hash: f69bb2c0fde14a3f3827ad1a4d03c54a31008fd4068e90b271d8d26b2aa5a749
File name: 2016-09-16-pseudoDarkleech-Rig-EK-payload-CrypMIC-ransomware.exe
IMAGES
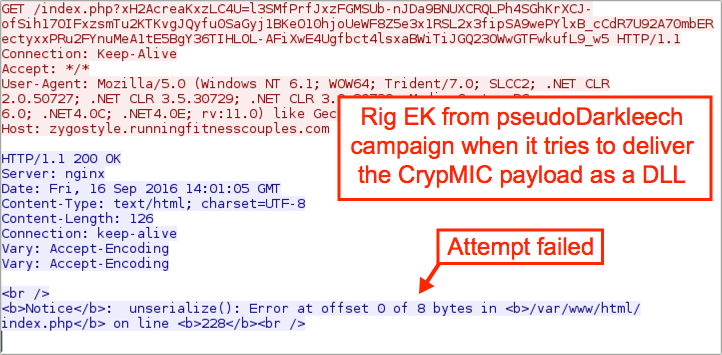
Shown above: Rig EK tries to send a DLL payload and fails.
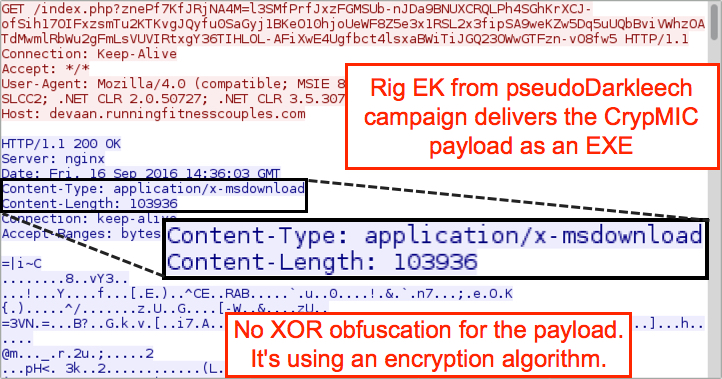
Shown above: Rig EK sends a CrypMIC ransomware payload as an EXE, and it's successful.
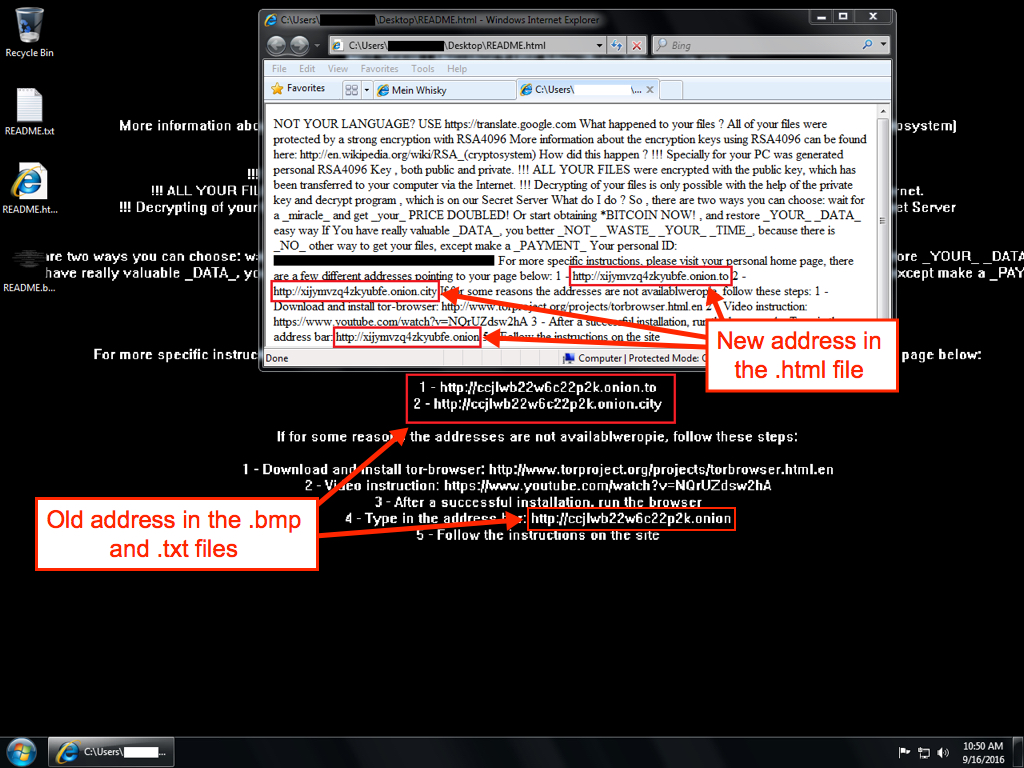
Shown above: Desktop of an infected Windows host.
Click here to return to the main page.