2016-09-21 - INFECTION FROM BOLETO CAMPAIGN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-21-Boleto-campaign-infection-traffic.pcap.zip 1.4 MB (1,380,535 bytes)
- 2016-09-21-Boleto-campaign-infection-traffic.pcap (1,874,946 bytes)
- 2016-09-21-Boleto-campaign-email-and-malware-and-artifacts.zip 1.4 MB (1,400,420 bytes)
- 1ru5a5ow.axo.vbs (7,775 bytes)
- 2016-09-21-Boleto-campaign-malware-and-artifacts-info.csv (1,977 bytes)
- 2016-09-21-Boleto-malspam-1428-UTC.eml (1,838 bytes)
- 5vieed1p.pad.vbs (338 bytes)
- DRACULA-PC.aes (16 bytes)
- DRACULA-PC.zip (1,079,293 bytes)
- Ionic.Zip.Reduced.dll (253,440 bytes)
- VCTO20097H3TOPyneOpr01jtiKs1iRdVptbVON3n7.vbs (1,084 bytes)
- aaaaaaaaaaaa.xml (3,374 bytes)
- dll.dll.exe (396,480 bytes)
- tmp42DA.tmp (11,548 bytes)
- tmp6124.tmp (0 bytes)
- tmp6124.tmpps1 (3,447 bytes)
- tmpC9B4.tmp (11,548 bytes)
EMAILS
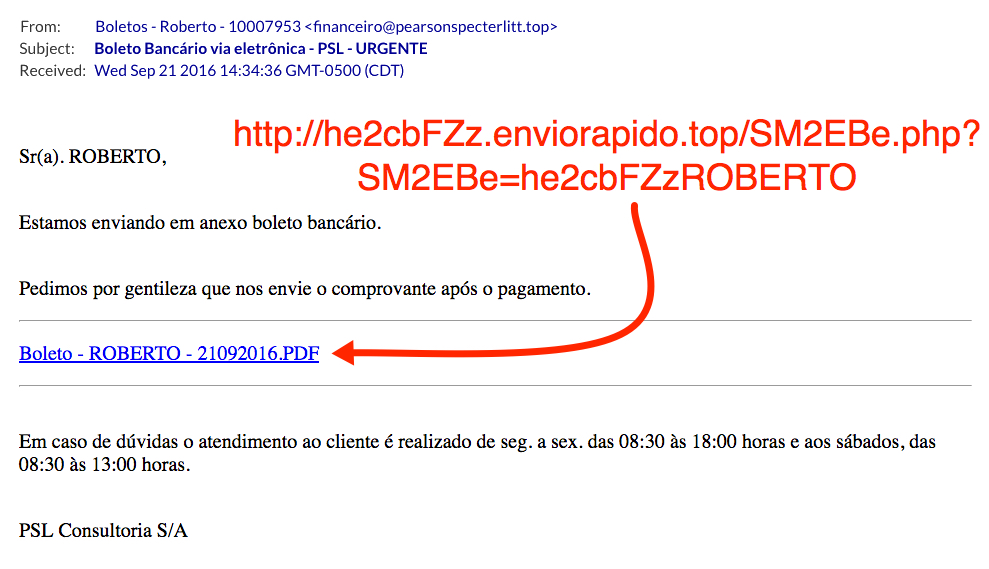
Shown above: Screen shot of the email.
TRAFFIC
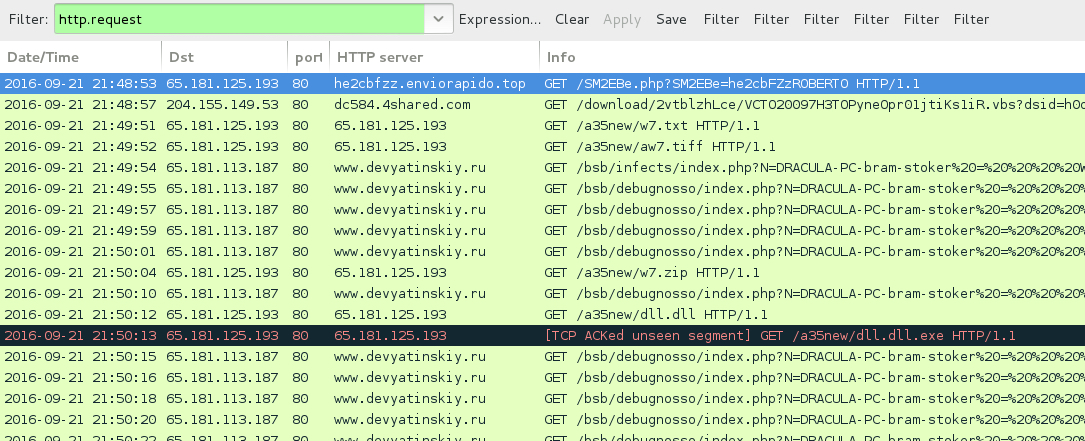
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- 4shared[.]com - VBS file from download link in the malspam
- 65.181.125[.]193 port 80 - 65.181.125[.]193 - GET /a35new/w7.txt
- 65.181.125[.]193 port 80 - 65.181.125[.]193 - GET /a35new/aw7.tiff
- 65.181.125[.]193 port 80 - 65.181.125[.]193 - GET /a35new/w7.zip
- 65.181.113[.]187 port 80 - www.devyatinskiy[.]ru - HTTP callback traffic
- 65.181.125[.]193 port 80 - 65.181.125[.]193 - GET /a35new/dll.dll
- 65.181.125[.]193 port 80 - 65.181.125[.]193 - GET /a35new/dll.dll.exe
- 65.181.113[.]204 port 443 - ssl.houselannister[.]top - IRC traffic (botnet command and control)
- imestre.danagas[.]ru - Response 192.64.147[.]142 - no follow-up UDP or TCP connection
- imestre.noortakaful[.]top - No response
- imestre.waridtelecom[.]top - No response
- imestre.aduka[.]top - No response
- imestre.saltflowinc[.]top - No response
- imestre.moveoneinc[.]top - No response
- imestre.cheddarmcmelt[.]top - No response
- imestre.suzukiburgman[.]top - No response
- imestre.houselannister[.]top - response: 127.0.0[.]1
- xxxxxxxxxxx.localdomain - No response
Click here to return to the main page.
