2016-09-22 - AFRAIDGATE NEUTRINO EK FROM 78.46.167[.]130 SENDS LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-22-Afraidgate-Neutrino-EK-sends-Locky-ransomware.pcap.zip 298.4 kB (298,445 bytes)
- 2016-09-22-Afraidgate-Neutrino-EK-sends-Locky-ransomware.pcap (320,474 bytes)
- 2016-09-22-Afraidgate-Neutrino-EK-and-Locky-ransomware-files.zip 287.5 kB (287,469 bytes)
- 2016-09-22-Afraidgate-Locky-ransomware-decrypt-instructions.bmp (4,149,158 bytes)
- 2016-09-22-Afraidgate-Locky-ransomware-decrypt-instructions.html (9,215 bytes)
- 2016-09-22-Afraidgate-Neutrino-EK-flash-exploit.swf (76,251 bytes)
- 2016-09-22-Afraidgate-Neutrino-EK-landing-page.txt (2,362 bytes)
- 2016-09-22-Afraidgate-Neutrino-EK-payload-Locky-ransomware-downloader.exe (48,128 bytes)
- 2016-09-22-Locky-ransomware.exe (174,080 bytes)
- 2016-09-22-king.bisneshotspot_com-blog.js.txt (216 bytes)
NOTES:
- Recent developments on the Afraidgate campaign can be found here.
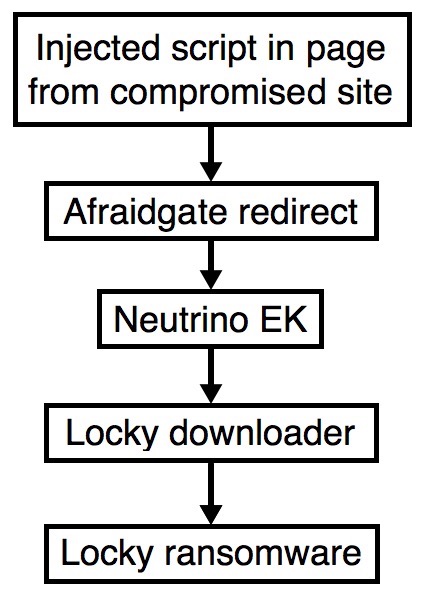
Shown above: Flowchart for this infection traffic.
TRAFFIC
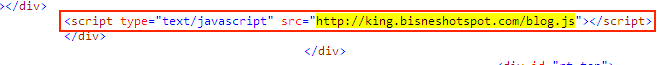
Shown above: Injected script in page from compromised site pointing to the Afraidgate URL.
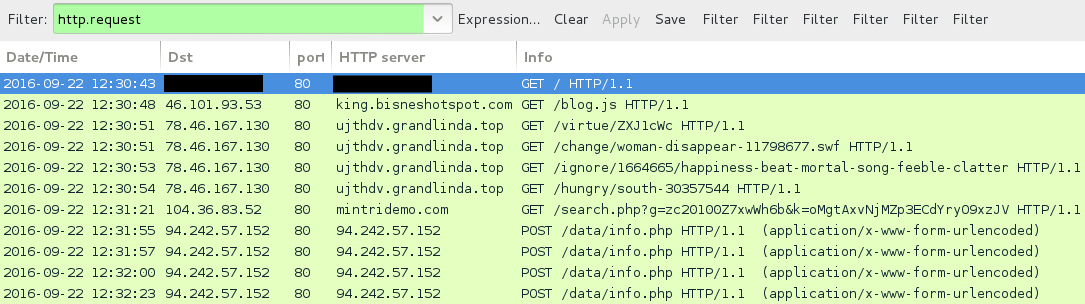
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- 46.101.93[.]53 port 80 - king.bisneshotspot[.]com - GET /blog.js - Afraidgate redirect
- 78.46.167[.]130 port 80 - ujthdv.grandlinda[.]top - Neutrino EK
- 104.36.83[.]52 port 80 - mintridemo[.]com - Domain the downloader payload retrieved Locky ransomware from
- 94.242.57[.]152 port 80 - 94.242.57[.]152 - POST /data/info.php - Locky ransomware post-infection traffic
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- f5xraa2y2ybtrefz[.]tor2web[.]org
- f5xraa2y2ybtrefz[.]onion[.]to
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: ff3889a991e7ddea35b67db40a186a1b5c99113cacfbc4e3bcce20bbfccce37f
File name: 2016-09-22-Afraidgate-Neutrino-EK-flash-exploit.swf
PAYLOAD (LOCKY RANSOMWARE DOWNLOADER):
- SHA256 hash: 22829e8f2b4f628c1a2711867669e4112e237025ba09a86299b839420903d7fc
File name: 2016-09-22-Afraidgate-Neutrino-EK-payload-Locky-ransomware-downloader.exe
FOLLOW-UP MALWARE (LOCKY RANSOMWARE):
- SHA256 hash: 433787c491e8b3534c1b477615f619fcdb1dc4881d305b5941ea965de945d5cc
File name: 2016-09-22-Locky-ransomware.exe
IMAGES
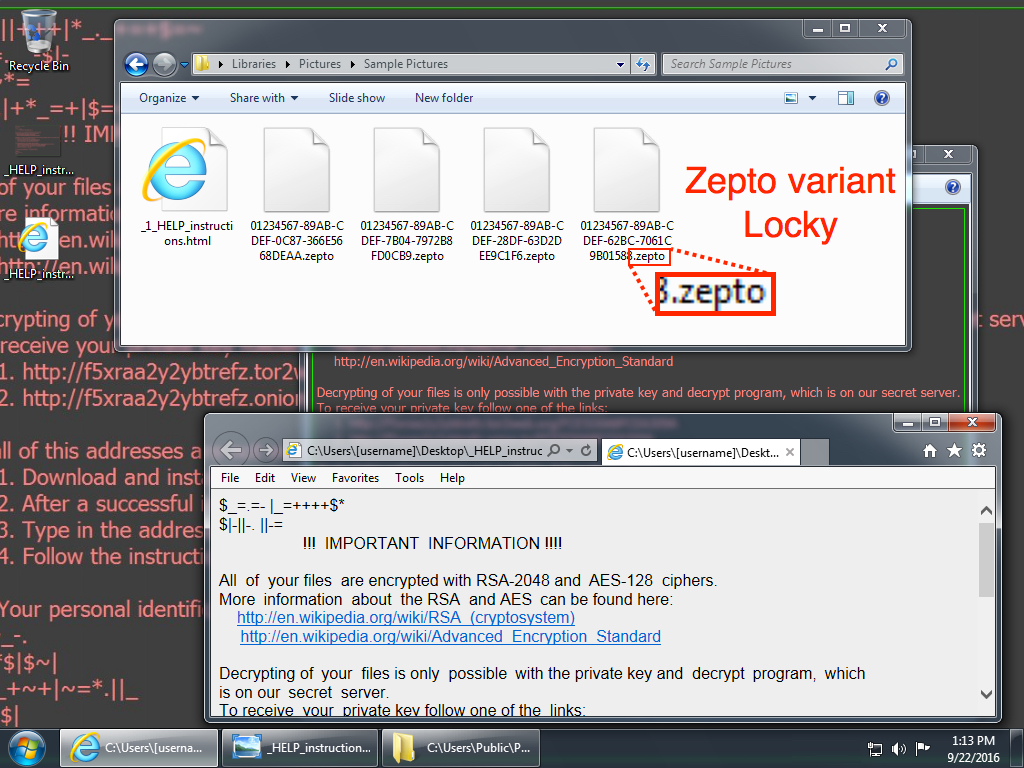
Shown above: Desktop of the infected Windows host.
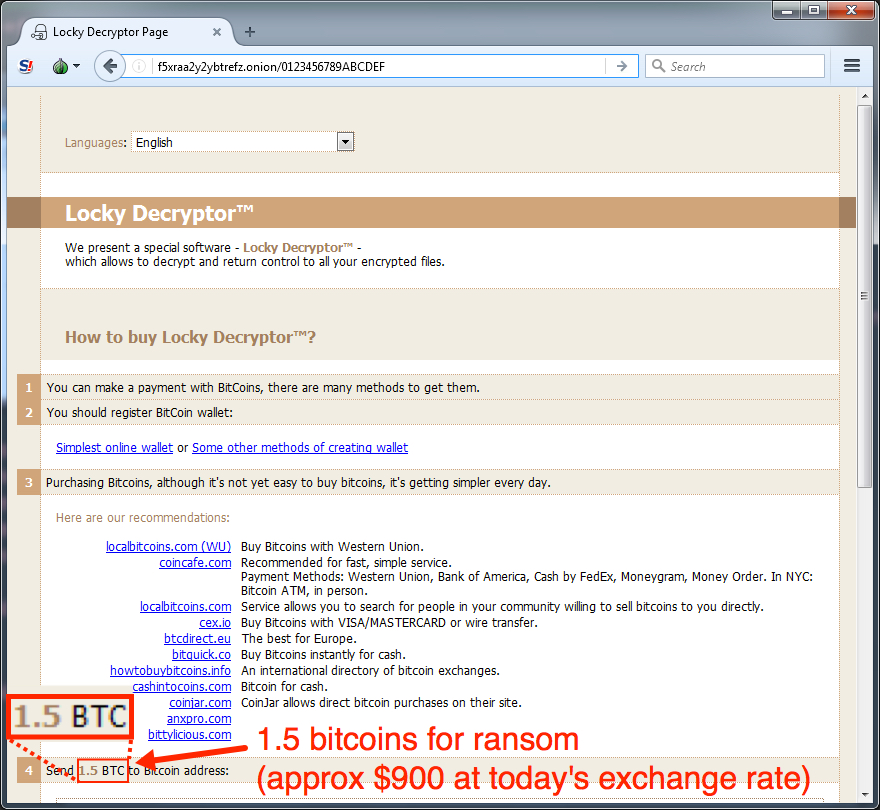
Shown above: Checking the decryption instructions link using a Tor browser.
Click here to return to the main page.