2016-09-26 - ODIN VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-26-Locky-ransomware-infection-traffic-2-pcaps.zip 340.2 kB (340,215 bytes)
- 2016-09-26-Locky-ransomware-infection-traffic-first-run.pcap.pcap (278,130 bytes)
- 2016-09-26-Locky-ransomware-infection-traffic-second-run.pcap.pcap (245,396 bytes)
- 2016-09-26-Locky-ransomware-files.zip 363.8 kB (363,813 bytes)
- 2016-09-26-1804-UTC-Locky-ransomware-email.eml (12,577 bytes)
- 2016-09-26-1804-UTC-attachment-new doc(3).zip (8,383 bytes)
- 2016-09-26-1804-UTC-downloaded-Locky-ransomware-xXINzimwQ1.dll (233,472 bytes)
- 2016-09-26-1804-UTC-extracted-file-DGWV9M4027.wsf (30,433 bytes)
- 2016-09-26-1840-UTC-Locky-ransomware-email.eml (16,001 bytes)
- 2016-09-26-1840-UTC-attachment-f2b119ce7c6.zip (11,096 bytes)
- 2016-09-26-1840-UTC-downloaded-Locky-ransomware-gkrS6IPeMxdlcQhT.dll (151,040 bytes)
- 2016-09-26-1840-UTC-extracted-file-Updated invoice pdf D32161A.wsf (64,991 bytes)
- 2016-09-26-Odin-variant-Locky-Decryptor-style.css (3,422 bytes)
- 2016-09-26-Odin-variant-Locky-Decryptor.html (5,863 bytes)
- _HOWDO_text.bmp (3,578,902 bytes)
- _HOWDO_text.html (9,459 bytes)
NOTES:
- This version of Locky ransomware uses the file extension .odin for the encrypted files.
EMAILS
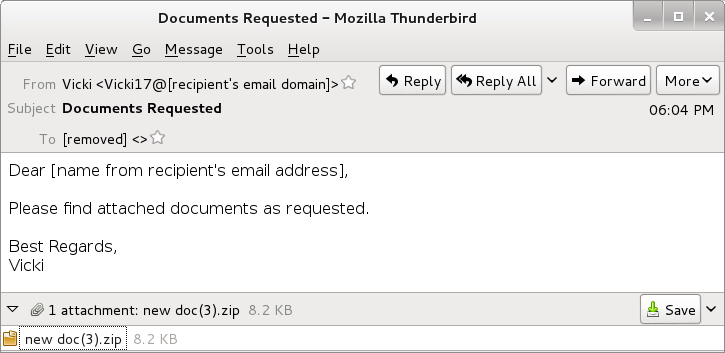
Shown above: First Locky malspam example.
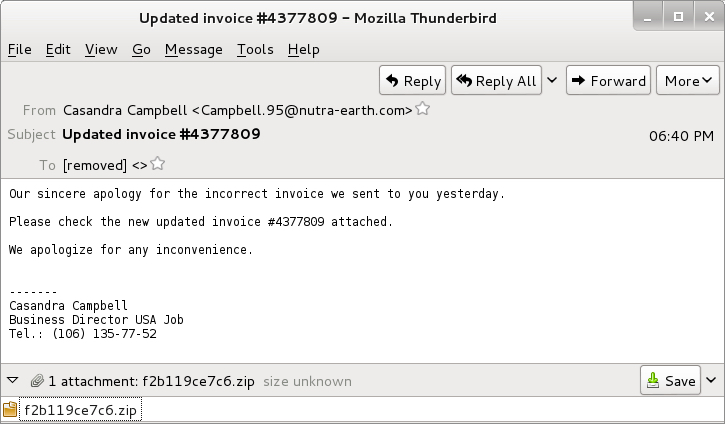
Shown above: Second Locky malspam example.
ATTACHMENTS
FIRST EMAIL:
- Date/Time: 2016-09-26 18:04 UTC
- Sender: Vicki <Vicki17@[recipient's email domain]>
- Subject: Documents Requested
- Attachment: new doc(3).zip
- Extracted file: DGWV9M4027.wsf
SECOND EMAIL:
- Date/Time: 2016-09-26 18:40 UTC
- Sender: Cassandra Campbell <Campbell.95@nutra-earth[.]com>
- Subject: Updated invoice #4377809
- Attachment: f2b119ce7c6.zip
- Extracted file: Updated invoice pdf D32161A.wsf
TRAFFIC
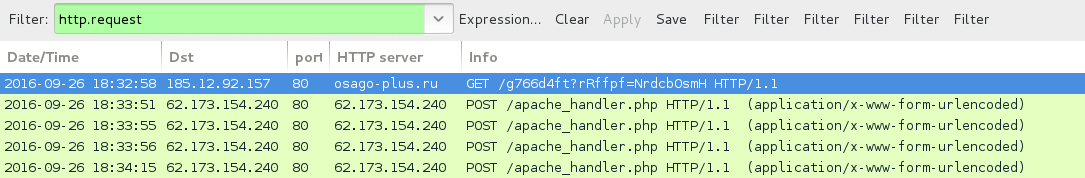
Shown above: Traffic from the first Locky ransomware example.
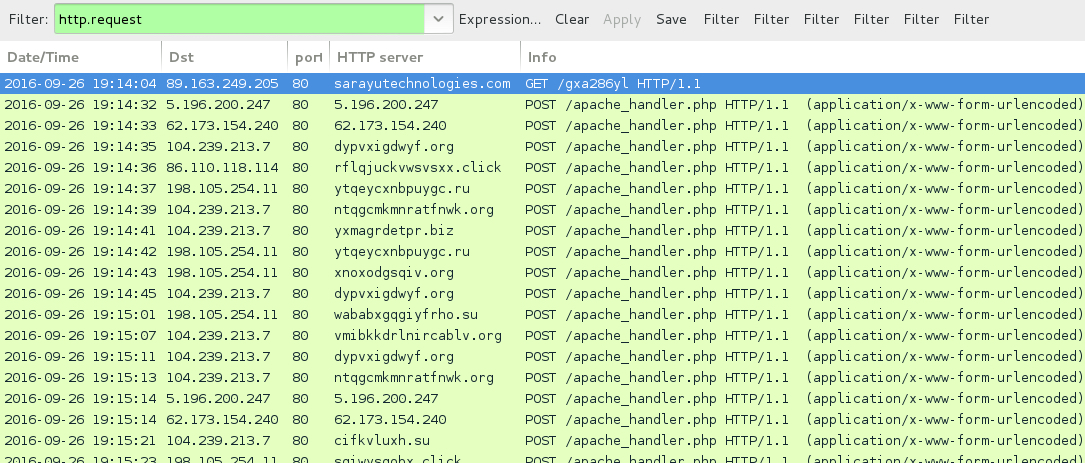
Shown above: Traffic from the second Locky ransomware example.
INFECTION FROM FIRST EMAIL ATTACHMENT:
- 185.12.92[.]157 port 80 - osago-plus[.]ru - GET /g766d4ft?rRffpf=NrdcbOsmH
- 62.173.154[.]240 port 80 - 62.173.154[.]240 - POST /apache_handler.php
INFECTION FROM SECOND EMAIL ATTACHMENT:
- 89.163.249[.]205 port 80 - sarayutechnologies[.]com - GET /gxa286yl
- 5.196.200[.]247 port 80 - 5.196.200[.]247 - POST /apache_handler.php
- 62.173.154[.]240 port 80 - 62.173.154[.]240 - POST /apache_handler.php
- 86.110.118[.]114 port 80 - rflqjuckvwsvsxx[.]click - POST /apache_handler.php
- 104.239.213[.]7 port 80 - cifkvluxh[.]su - POST /apache_handler.php
- 104.239.213[.]7 port 80 - dypvxigdwyf[.]org - POST /apache_handler.php
- 104.239.213[.]7 port 80 - ntqgcmkmnratfnwk[.]org - POST /apache_handler.php
- 104.239.213[.]7 port 80 - ocuhfpcgyg[.]pl - POST /apache_handler.php
- 104.239.213[.]7 port 80 - vmibkkdrlnircablv[.]org - POST /apache_handler.php
- 104.239.213[.]7 port 80 - yxmagrdetpr[.]biz - POST /apache_handler.php
- 198.105.254[.]11 port 80 - sqiwysgobx[.]click - POST /apache_handler.php
- 198.105.254[.]11 port 80 - wababxgqgiyfrho[.]su - POST /apache_handler.php
- 198.105.254[.]11 port 80 - xnoxodgsqiv[.]org - POST /apache_handler.php
- 198.105.254[.]11 port 80 - ytqeycxnbpuygc[.]ru - POST /apache_handler.php
DOMAINS FROM THE DECRYPTION INSTRUCTIONS:
- jhomitevd2abj3fk[.]tor2web[.]org
- jhomitevd2abj3fk[.]onion[.]to
FILE HASHES
LOCKY SAMPLES:
- SHA256 hash: 86d229d219a21ab8092839a4361d30977e56c78f0ada10b6d68363b2834dd1dc
File name: 2016-09-26-1804-UTC-downloaded-Locky-ransomware-xXINzimwQ1.dll
- SHA256 hash: 9203fe7988535d29e4808b02e403ce3399b75d344ac72b46a292bf224d51bf53
File name: 2016-09-26-1840-UTC-downloaded-Locky-ransomware-gkrS6IPeMxdlcQhT.dll
IMAGES

Shown above: Screen shot from an infected Windows desktop. Note the .odin file extension.

Shown above: Ransom payment is 1.5 bitcoin, just like I've seen from the samples of .zepto Locky variant this past week.
Click here to return to the main page.
