2016-10-06 - BANLOAD INFECTION FROM EMAIL ATTACHMENT
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-06-Banload-infection-traffic-from-email-attachment.pcap.zip 6.8 MB (6,801,853 bytes)
- 2016-10-06-Banload-infection-traffic-from-email-attachment.pcap (7,779,133 bytes)
- 2016-10-06-files-from-the-Banload-infection.zip 983.3 kB (983,271 bytes)
- 2016-10-06-email-with-malicious-attachment-1704-UTC.eml (3,950 bytes)
- FaturaVivoPendDDA-05102016.zip (489,840 bytes)
- FaturaVivoPendDDA-05102016VER.exe (813,048 bytes)
- MeuVivoFatura06102016.html (1,109 bytes)
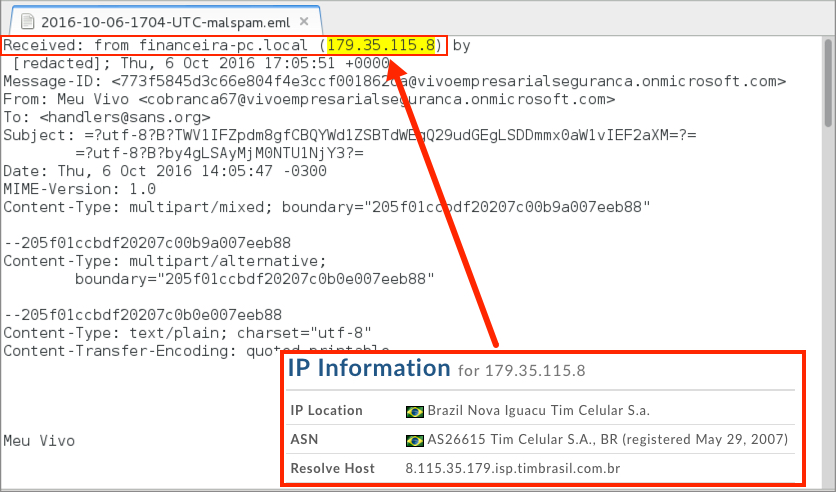
Shown above: Email headers showing where the message came from.
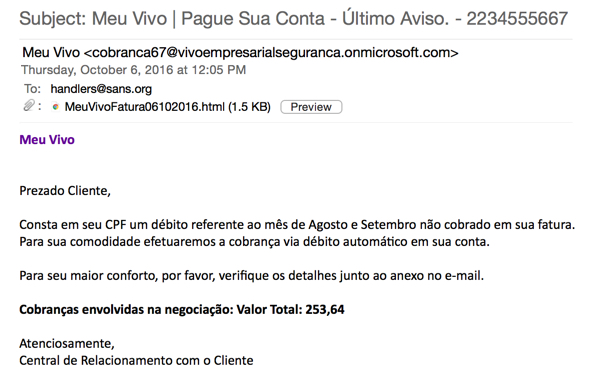
Shown above: Screenshot of the email.
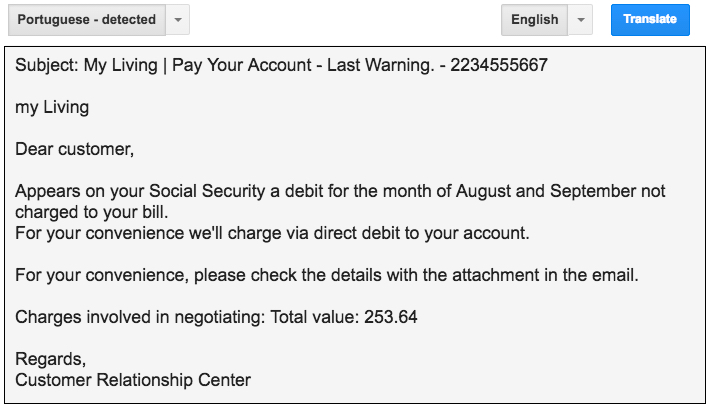
Shown above: Google translation of the email.
EMAIL TEXT:
Subject: Meu Vivo | Pague Sua Conta - Último Aviso. - 2234555667
Meu Vivo
Prezado Cliente,
Consta em seu CPF um débito referente ao mês de Agosto e Setembro não cobrado em sua fatura.
Para sua comodidade efetuaremos a cobrança via débito automático em sua conta.
Para seu maior conforto, por favor, verifique os detalhes junto ao anexo no e-mail.
Cobranças envolvidas na negociação: Valor Total: 253,64
Atenciosamente,
Central de Relacionamento com o Cliente
GOOGLE TRANSLATION:
Subject: My Living | Pay Your Account - Last Warning. - 2234555667
my Living
Dear customer,
Appears on your Social Security a debit for the month of August and September not charged to your bill.
For your convenience we'll charge via direct debit to your account.
For your convenience, please check the details with the attachment in the email.
Charges involved in negotiating: Total value: 253.64
Regards,
Customer Relationship Center
FILES
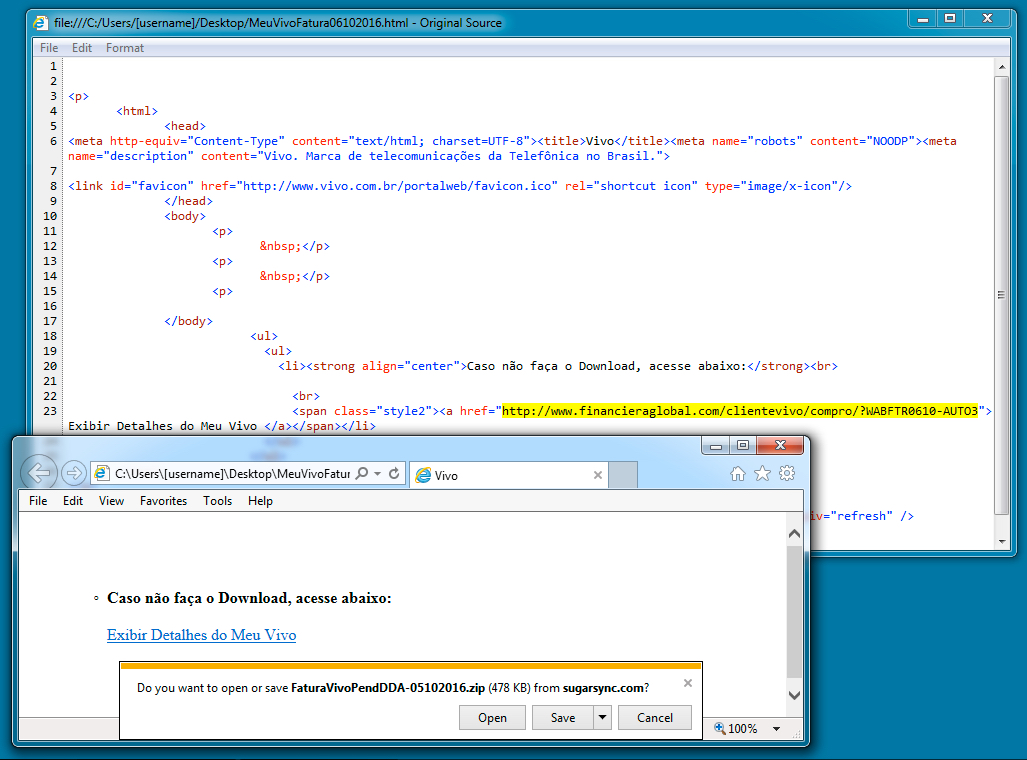
Shown above: Email attachment (an HTML file).
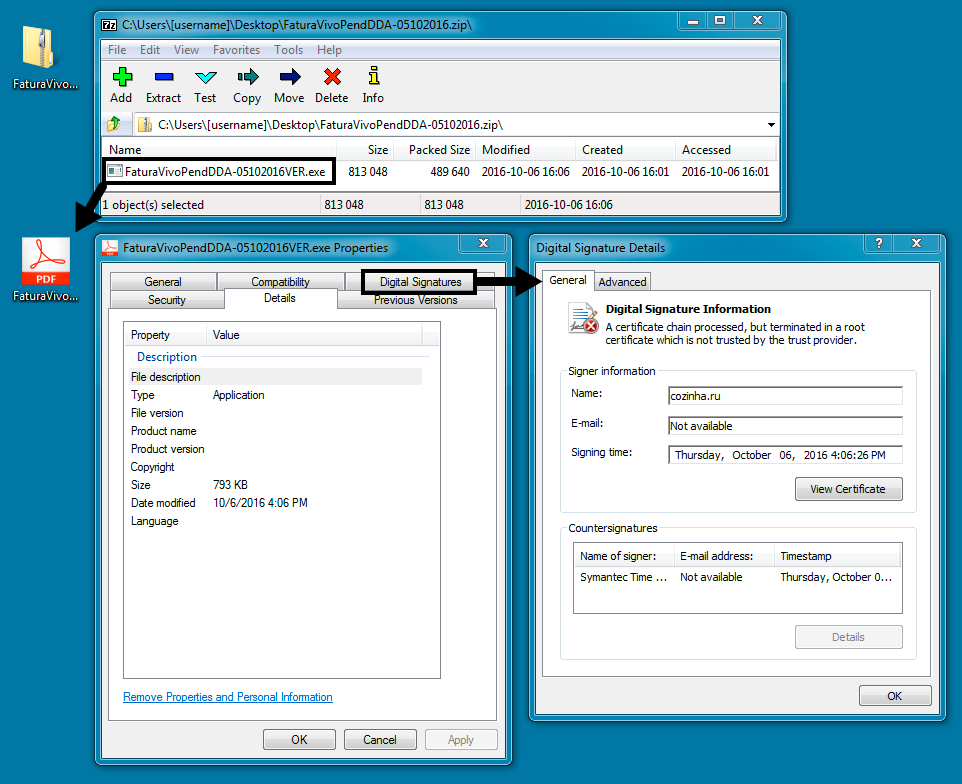
Shown above: Malware downloaded from the HTML email attachment.
ASSOCIATED FILES:
- SHA256 hash: 5bfb2bfa8cec66cd14afbc563f9c35387c7d40de2e442fc45f0b857a196438dc
File name: MeuVivoFatura06102016.html (1,109 bytes)
File description: Email attachment, an HTML file with a link to a malicious .zip archive.
- SHA256 hash: 2be5f3c8d2f41df6fa4abbc07c15d58190ecba2c01829ed60d7f9cd04276a56d
File name: FaturaVivoPendDDA-05102016.zip (489,840 bytes)
File description: Malicious .zip archive, downloaded from the HTML email attachment.
- SHA256 hash: 3fd4295e298c26813adf72f7a63d5770dbeafddda5edb5f32ed43166ac307263
File name: FaturaVivoPendDDA-05102016VER.exe (813,048 bytes)
File description: Malicious .exe file extracted from the .zip archive.
TRAFFIC
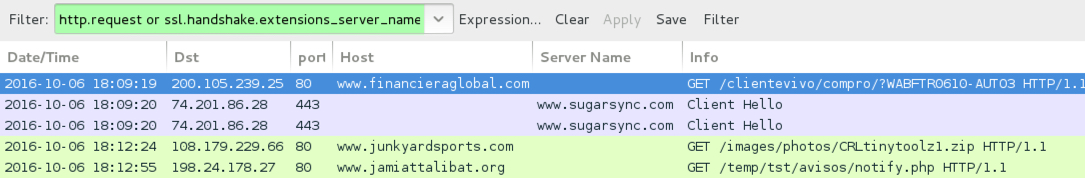
Shown above: Traffic from the pcap filtered in Wireshark.
HTTP REQUESTS:
- www.financieraglobal[.]com - GET /clientevivo/compro/?WABFTR0610-AUTO3
- www.sugarsync[.]com - GET /pf/D3213055_036_351613432?directDownload=true (HTTPS)
- www.junkyardsports[.]com - GET /images/photos/CRLtinytoolz1.zip
- www.jamiattalibat[.]org - GET /temp/tst/avisos/notify.php
ASSOCIATED DOMAINS:
- 179.35.115[.]8 - financeira-pc[.]local - Mail server IP address and possible name of infected host
- 200.105.239[.]25 port 80 - www.financieraglobal[.]com - Domain used in link from the malicious HTML attachment
- 74.201.86[.]28 port 443 - www.sugarsync[.]com - Legitimate service. It's being abused to host the zip file
- 108.179.229[.]66 port 80 - www.junkyardsports[.]com - Follow-up download caused by malware extracted from zip file
- 198.24.178[.]27 port 80 - www.jamiattalibat[.]org - Post-infection callback (Banload)
IMAGES
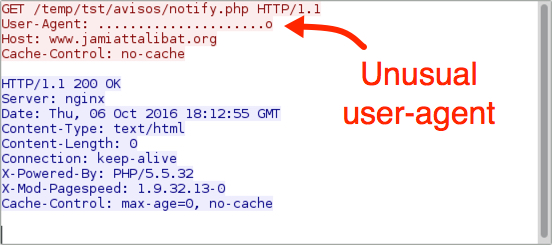
Shown above: Unusual user-agent during post-infection callback.
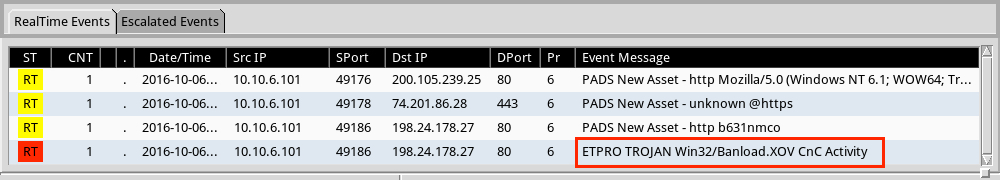
Shown above: Hits from the Emerging Threats and ETPRO rulesets using Sguil on Security Onion.
FINAL NOTES
Click here to return to the main page.
