2016-10-25 - RIG EK DATA DUMP: REGULAR RIG VS RIG-V
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-25-Rig-EK-data-dump-6-pcaps.zip 3.0 MB (2,953,381 bytes)
- 2016-10-25-Afraidgate-RIGv-sends-Locky-ransomware.pcap (312,726 bytes)
- 2016-10-25-EITest-Rig-EK-first-run.pcap (1,932,487 bytes)
- 2016-10-25-EITest-Rig-EK-second-run.pcap (239,554 bytes)
- 2016-10-25-pseudoDarkleech-RIGv-sends-Cerber-ransomware-first-run.pcap (666,602 bytes)
- 2016-10-25-pseudoDarkleech-RIGv-sends-Cerber-ransomware-second-run.pcap (571,063 bytes)
- 2016-10-25-pseudoDarkleech-RIGv-sends-Cerber-ransomware-third-run.pcap (567,264 bytes)
- 2016-10-25-Rig-EK-data-dump-malware-and-artifacts.zip 2.5 MB (2,530,689 bytes)
- 2016-10-25-Afraidgate-RIGv-flash-exploit.swf (51,806 bytes)
- 2016-10-25-Afraidgate-RIGv-landing-page.txt (5,095 bytes)
- 2016-10-25-Afraidgate-RIGv-payload-Locky-ransomware.exe (230,912 bytes)
- 2016-10-25-Cerber-ransomware-decryption-instructions-first-run-README.hta (63,083 bytes)
- 2016-10-25-Cerber-ransomware-decryption-instructions-first-run.bmp (1,920,054 bytes)
- 2016-10-25-Cerber-ransomware-decryption-instructions-second-run-README.hta (63,083 bytes)
- 2016-10-25-Cerber-ransomware-decryption-instructions-second-run.bmp (1,920,054 bytes)
- 2016-10-25-Cerber-ransomware-decryption-instructions-third-run-README.hta (63,083 bytes)
- 2016-10-25-Cerber-ransomware-decryption-instructions-third-run.bmp (1,920,054 bytes)
- 2016-10-25-EITest-Rig-EK-flash-exploit-first-run.swf (52,571 bytes)
- 2016-10-25-EITest-Rig-EK-flash-exploit-second-run.swf (52,571 bytes)
- 2016-10-25-EITest-Rig-EK-landing-page-first-run.txt (3,287 bytes)
- 2016-10-25-EITest-Rig-EK-landing-page-second-run.txt (3,275 bytes)
- 2016-10-25-EITest-Rig-EK-payload-first-run.exe (605,696 bytes)
- 2016-10-25-EITest-Rig-EK-payload-second-run.exe (171,008 bytes)
- 2016-10-25-Locky-ransomware-decryption-instructions_WHAT_is.bmp (3,864,030 bytes)
- 2016-10-25-Locky-ransomware-decryption-instructions_WHAT_is.html (9,383 bytes)
- 2016-10-25-page-from-ardenne_org-with-injected-script.txt (20,170 bytes)
- 2016-10-25-page-from-discbinedoctor_com-with-injected-script-third-run.txt (19,826 bytes)
- 2016-10-25-page-from-joellipman_com-with-injected-script-first-run.txt (68,046 bytes)
- 2016-10-25-page-from-standardtime_com-with-injected-script-second-run.txt (9,191 bytes)
- 2016-10-25-page-from-wiki.vmug_com-with-injected-EITest-script-first-run.txt (22,656 bytes)
- 2016-10-25-page-from-xorbin_com-with-injected-EITest-script-second-run.txt (21,810 bytes)
- 2016-10-25-pseudoDarkleech-RIGv-flash-exploit-first-run.swf (51,806 bytes)
- 2016-10-25-pseudoDarkleech-RIGv-flash-exploit-second-run.swf (51,806 bytes)
- 2016-10-25-pseudoDarkleech-RIGv-flash-exploit-third-run.swf (51,806 bytes)
- 2016-10-25-pseudoDarkleech-RIGv-landing-page-first-run.txt (5,079 bytes)
- 2016-10-25-pseudoDarkleech-RIGv-landing-page-second-run.txt (5,088 bytes)
- 2016-10-25-pseudoDarkleech-RIGv-landing-page-third-run.txt (5,113 bytes)
- 2016-10-25-pseudoDarkleech-RIGv-payload-Cerber-ransomware-first-run.exe (313,605 bytes)
- 2016-10-25-pseudoDarkleech-RIGv-payload-Cerber-ransomware-second-run.exe (313,685 bytes)
- 2016-10-25-pseudoDarkleech-RIGv-payload-Cerber-ransomware-third-run.exe (327,870 bytes)
- 2016-10-25-script-returned-from-jietrdpnd.ddnsking_com-second-run.txt (379 bytes)
- 2016-10-25-script-returned-from-qsmaleump.hopto_org-third-run.txt (393 bytes)
- 2016-10-25-stowne.our1home_co_uk-xenforo.js.txt (418 bytes)
NOTES:
- There are currently at least 2 versions of Rig EK being used by different campaigns.
- One is an updated/evolving "VIP version" version of Rig EK that @kafeine has been calling RIG-v as described here.
- The other version of Rig EK is "regular Rig" that generally looks the same as it has for a while now.
- RIG-v is currently being used by the Afraidgate and pseudoDarkleech campaigns.
- Regular Rig EK is still being used by the EITest campaign.
- Today's blog has examples from all 3 campaigns: RIG-v from the Afraidgate and pseudoDarkleech campaigns. Rig EK from the EITest campaign.
TRAFFIC
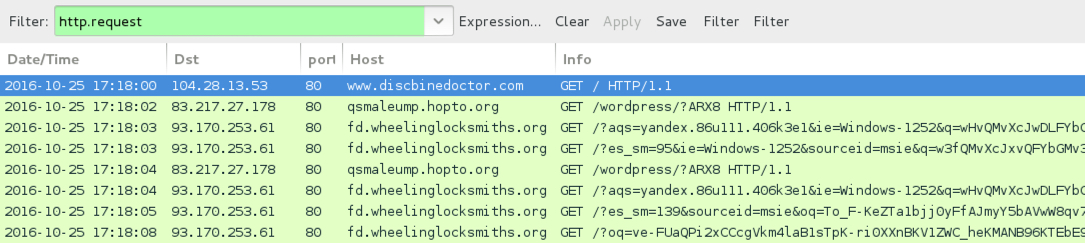
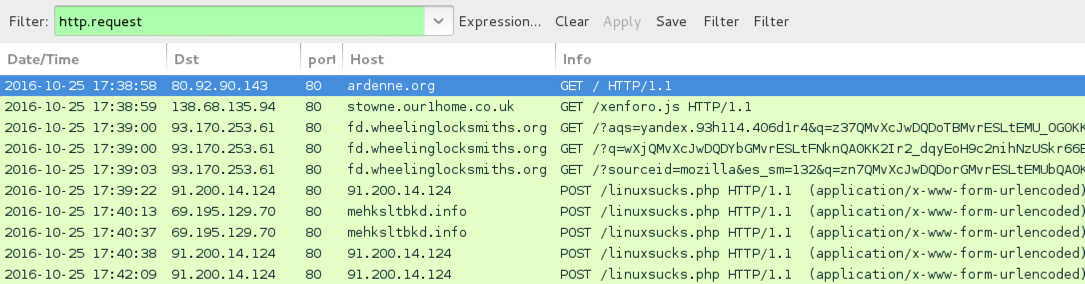
ASSOCIATED DOMAINS:
- ardenne[.]org - Compromised site (Afraidgate campaign)
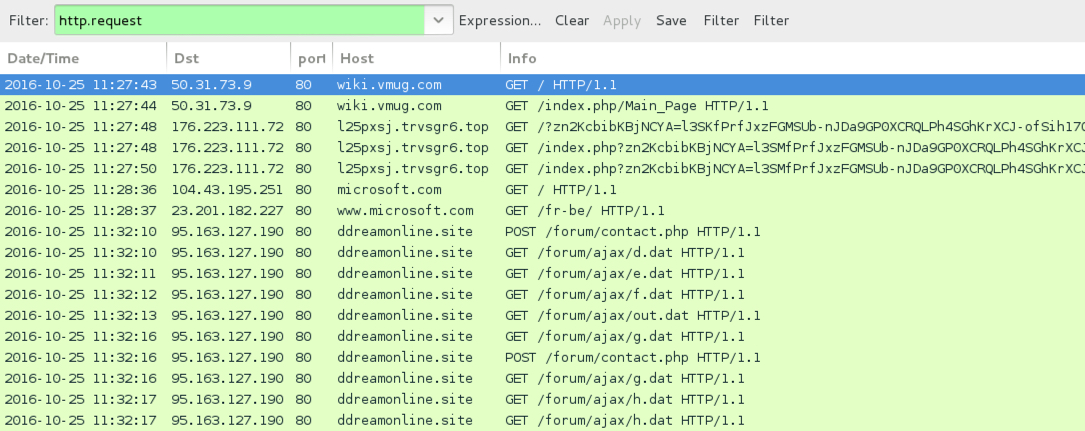
- wiki.vmug[.]com - Compromised site (EITest campaign, first run)
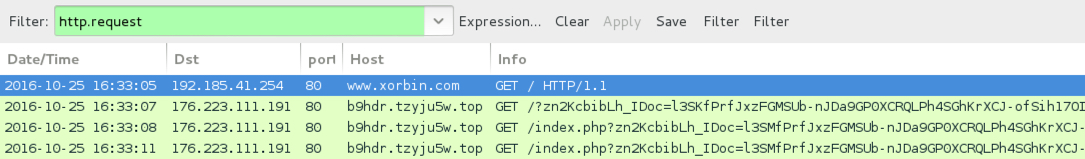
- www.xorbin[.]com - Compromised site (EITest campaign, second run)
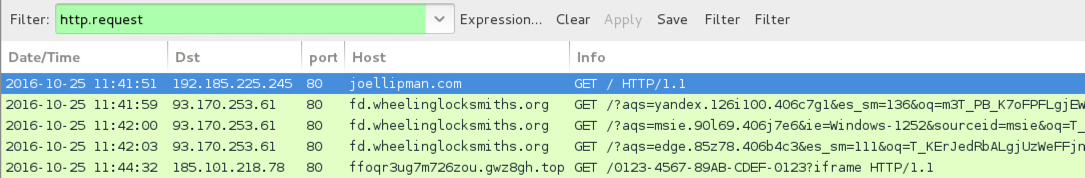
- joellipman[.]com - Compromised site (pseudoDarkleech campaign, no gate)
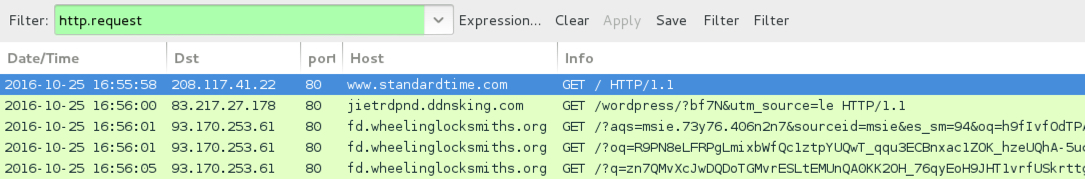
- www.standardtime[.]com - Compromised site (pseudoDarkleech campaign, "utm_source=le" gate)
- www.discbinedoctor[.]com - Compromised site (pseudoDarkleech campaign, "ARX8" gate)
- 138.68.135[.]94 port 80 - stowne.our1home[.]co[.]uk - GET /xenforo.js - Afraidgate redirect
- 83.217.27[.]178 port 80 - jietrdpnd.ddnsking[.]com - GET /wordpress/?bf7N&utm_source=le - "utm_source=le" gate for pseudoDarkleech campaign
- 83.217.27[.]178 port 80 - qsmaleump.hopto[.]org - GET /wordpress/?ARX8 - "ARX8" gate for pseudoDarkleech campaign
- 176.223.111[.]72 port 80 - l25pxsj.trvsgr6[.]top - Rig EK from the EITest campaign (first run)
- 176.223.111[.]191 port 80 - b9hdr.tzyju5w[.]top - Rig EK from the EITest campaign (second run)
- 93.170.253[.]61 port 80 - fd.wheelinglocksmiths[.]org - RIG-v from the Afraidgate campaign
- 93.170.253[.]61 port 80 - fd.wheelinglocksmiths[.]org - RIG-v from the pseudoDarkleech campaign (first run, no gate)
- 93.170.253[.]61 port 80 - fd.wheelinglocksmiths[.]org - RIG-v from the pseudoDarkleech campaign (second run, "utm_source=le" gate)
- 93.170.253[.]61 port 80 - fd.wheelinglocksmiths[.]org - RIG-v from the pseudoDarkleech campaign (third run, "ARX8" gate)
- 194.165.16[.]0 - 194.165.19[.]255 (194.165.16[.]0/22) port 6892 (UDP) - UDP traffic caused by Cerber ransomware (samples from all 3 campaigns)
- 91.200.14[.]124 port 80 - 91.200.14[.]124 - POST /linuxsucks.php - HTTP traffic caused by Locky ransomware
- 69.195.129[.]70 port 80 - mehksltbkd[.]info - POST /linuxsucks.php - HTTP traffic caused by Locky ransomware
- 95.163.127[.]190 port 80 - ddreamonline[.]site - HTTP traffic caused by malware from the first EITest campaign infection
DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- jhomitevd2abj3fk.tor2web[.]org (Locky ransomware sample from the Afraidgate campaign)
- jhomitevd2abj3fk[.]onion[.]to (Locky ransomware sample from the Afraidgate campaign)
- ffoqr3ug7m726zou.1pr9as[.]top (Cerber ransomware sample from the pseudoDarkleech campaign, no gate)
- ffoqr3ug7m726zou.umvv28[.]top (Cerber ransomware sample from the pseudoDarkleech campaign, no gate)
- ffoqr3ug7m726zou[.]onion[.]to (Cerber ransomware sample from the pseudoDarkleech campaign, no gate)
- xrhwryizf5mui7a5.1pr9as[.]top (Cerber ransomware sample from the pseudoDarkleech campaign, "utm_source=le" gate)
- xrhwryizf5mui7a5.4t6f24[.]top (Cerbe ransomwarer sample from the pseudoDarkleech campaign, "utm_source=le" gate)
- xrhwryizf5mui7a5[.]onion[.]to (Cerber ransomware sample from the pseudoDarkleech campaign, "utm_source=le" gate)
- ahuqfrqk54v3vnzj.1pr9as[.]top (Cerber ransomware sample from the pseudoDarkleech campaign, "ARX8" gate)
- ahuqfrqk54v3vnzj.9mu6vk[.]top (Cerber ransomware sample from the pseudoDarkleech campaign, "ARX8" gate)
- ahuqfrqk54v3vnzj[.]onion[.]to (Cerber ransomware sample from the pseudoDarkleech campaign, "ARX8" gate)
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: 49d5fd5a5b0058eccd888a149f6f995e7c160dd3973c0c0edebf0311365847cd
File name: 2016-10-25-EITest-Rig-EK-flash-exploit-first-run.swf (52,571 bytes)
File name: 2016-10-25-EITest-Rig-EK-flash-exploit-second-run.swf (52,571 bytes)
- SHA256 hash: 81e49d39081c0c3e1ac9ce13af6c06c7b9126743e3ed78db7e14b67a3870649e
File name: 2016-10-25-Afraidgate-RIGv-flash-exploit.swf (51,806 bytes)
File name: 2016-10-25-pseudoDarkleech-RIGv-flash-exploit-first-run.swf (51,806 bytes)
File name: 2016-10-25-pseudoDarkleech-RIGv-flash-exploit-second-run.swf (51,806 bytes)
File name: 2016-10-25-pseudoDarkleech-RIGv-flash-exploit-third-run.swf (51,806 bytes)
PAYLOAD:
- SHA256 hash: e7d865f4fe2a55f4d9a9ab286daeefbfc9e35b21994ba746d873a5412c2d176d
File name: 2016-10-25-pseudoDarkleech-RIGv-payload-Cerber-ransomware-first-run.exe (313,605 bytes)
- SHA256 hash: 47337f131c439b06f55d8f1a83d5129595697afcecf5639471da39e644802749
File name: 2016-10-25-pseudoDarkleech-RIGv-payload-Cerber-ransomware-second-run.exe (313,685 bytes)
- SHA256 hash: 426ecff4fab5b8328a756c6b1ae01123c4da6f32f148f7bfb6a66aa047bb22da
File name: 2016-10-25-pseudoDarkleech-RIGv-payload-Cerber-ransomware-third-run.exe (327,870 bytes)
- SHA256 hash: 549aa1d797be91ba3e9352d2cb4b8dc79987cb8812f7b2fd2e31d975522af708
File name: 2016-10-25-Afraidgate-RIGv-payload-Locky-ransomware.exe (230,912 bytes)
- SHA256 hash: 9f3682d34073e9b096a533eb7835d85bd77f379bac660109024602f6404a8f92
File name: 2016-10-25-EITest-Rig-EK-payload-first-run.exe (605,696 bytes)
- SHA256 hash: b1f2056295efaf74996ff92a505a34383021540a72312b99949fd83fe45ed0d8
File name: 2016-10-25-EITest-Rig-EK-payload-second-run.exe (171,008 bytes)
Click here to return to the main page.
