2016-10-31 - PSEUDO-DARKLEECH RIG-V SENDS DDOS BOTNET MALWARE
NOTICE:
- The zip archives on this page have been updated, and they now use the new password scheme. For the new password, see the "about" page of this website.
ASSOCIATED FILES:
- 2016-10-31-pseudoDarkleech-RIGv-sends-ddos-botnet-malware.pcap.zip 224.6 kB (224,558 bytes)
- 2016-10-31-pseudoDarkleech-RIGv-sends-ddos-botnet-malware.pcap (243,816 bytes)
- 2016-10-31-pseudoDarkleech-RIGv-and-ddos-botnet-malware.zip 181.2 kB (181,242 bytes)
- 2016-10-31-page-from-joellipman_com-with-injected-script.txt (68,385 bytes)
- 2016-10-31-pseudoDarkleech-RIGv-flash-exploit.swf (51,801 bytes)
- 2016-10-31-pseudoDarkleech-RIGv-landing-page.txt (4,810 bytes)
- 2016-10-31-pseudoDarkleech-RIGv-payload-ddos-botnet-malware.exe (147,456 bytes)
NOTES:
- This one's a bit weird. I saw a different URL pattern for the EK when it delivered it's payload.
- This is also a weird payload I'm not used to seeing sent by RIG-v from the pseudoDarkleech campaign.
- A short while later, the pseudoDarkleech campaign was back to using RIG-v to deliver Cerber ransomware like we normally see (link).
- There are currently at least 2 versions of Rig EK being used by different campaigns.
- One is an updated/evolving "VIP version" version of Rig EK that @kafeine has been calling RIG-v as described here.
- The other version of Rig EK is "regular Rig" that generally looks the same as it has for a while now.
- RIG-v is currently being used by the Afraidgate and pseudoDarkleech campaigns.
- Regular Rig EK is still being used by the EITest campaign.
BACKGROUND ON THE PSEUDO-DARKLEECH CAMPAIGN:
- Something I wrote on exploit kit (EK) fundamentals: link
- 2016-03-22 - PaloAlto Networks Unit 42 blog: Campaign Evolution: Darkleech to Pseudo-Darkleech and Beyond
- 2016-07-02 - SANS ISC diary: Change in patterns for the pseudoDarkleech campaign
- 2016-09-14 - Malware-traffic-analysis.net: The pseudoDarkleech campaign starts using Rig EK instead of Neutrino EK
- 2016-10-03 - Malware-traffic-analysis.net: The pseudoDarkleech campaign stops sending CryptXXX, starts sending Cerber ransomware
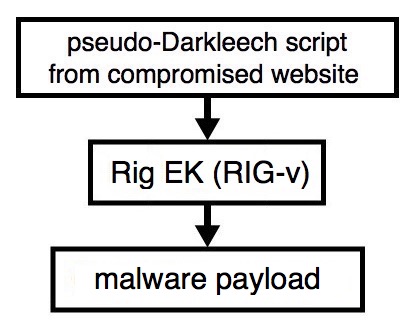
Shown above: Flowchart for this infection traffic.
TRAFFIC

Shown above: Injected script from the pseudoDarkleech campaign in a page from the compromised site.
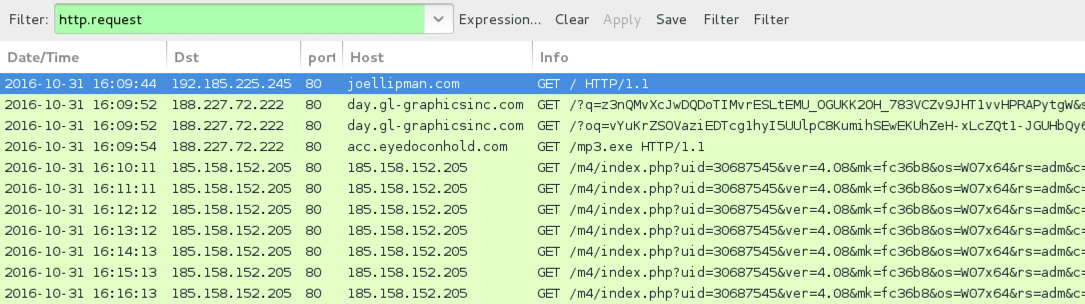
Shown above: Traffic from the infection filtered in Wireshark.
ASSOCIATED DOMAINS:
- joellipman[.]com - Compromised site
- 188.227.72[.]222 port 80 - day.gl-graphicsinc[.]com - RIGv
- 188.227.72[.]222 port 80 - acc.eyedoconhold[.]com - RIGv delivering payload
- 185.158.152[.]205 port 80 - 185.158.152[.]205 - Post-infection callback by infected host for Darkness/Madness DDoS botnet
FILE HASHES
FLASH EXPLOIT:
- SHA256 hash: c8060e6a20fa3d6ef75467c2beec1216a346cf35de863f2533260fb51ecc3cf5
File name: 2016-10-31-pseudoDarkleech-RIGv-flash-exploit.swf (51,801 bytes)
PAYLOAD (DARKNESS/MADNESS DDOS BOTNET MALWARE):
- SHA256 hash: d8fe0f4ac350b457de9de64584edc811e055a79b9179376d2189e8fbc69c4e7a
File name: C:\Users\[username]\AppData\Local\Temp\radB53A0.tmp.exe (147,456 bytes)
IMAGES
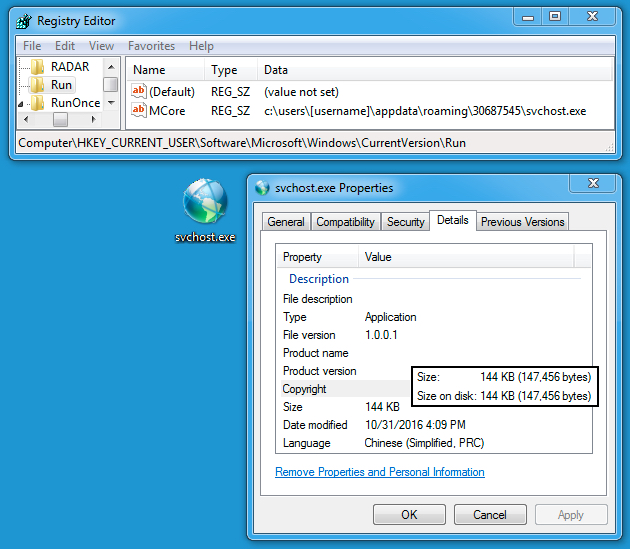
Shown above: Malware made persistent on the infected host.
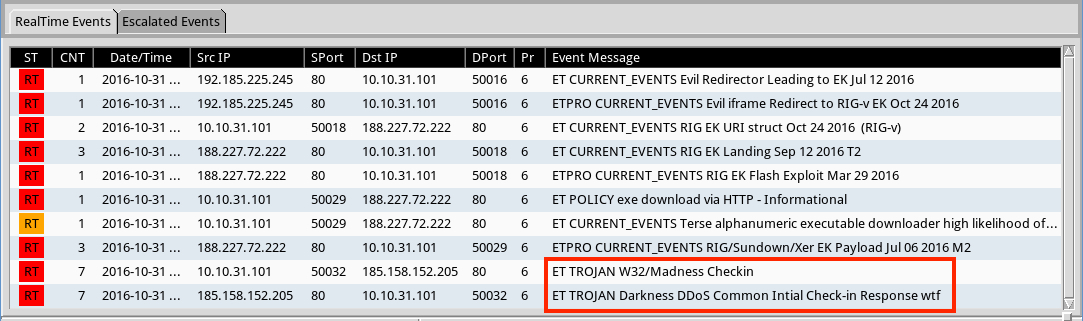
Shown above: Alerts on the pcap from the Emerging Threats Pro (ETPRO) ruleset using Sguil on Security Onion. Alerts for Darkness and Madness are noted.
Click here to return to the main page.